(deprecated) Notification Alerts
Deprecated Notifications
Cisco Umbrella is retiring notifications in Investigate and replacing them with the Domain Summary and Domain Risk sub-scores. For more information refer to the Domain Summary and Domain Risk Scores sections of the Domain Summary topic.
Notification alerts are intended to call your attention to information that may be useful or relevant to the domain you are researching. These notification alerts are grouped by color:
- Red—Features or attributes of a domain are highly suspicious and attributable to malicious behavior.
- Yellow—Potentially suspicious scores within Investigate's features that are worthy of attention.
- Green—Characteristics or attributes of the domain that are typical and often associated with benign domains.
- Blue—No IP data to be found for the domain, or the domain is a CNAME for another domain.
Red alerts indicate that specific features or attributes of a domain are highly suspicious and attributable to malicious behavior.
"This domain is currently in the Umbrella block list”

This alert pertains to a domain that's been found to be malicious and is currently in the Umbrella block list. The ‘block list’ is the list of known bad domains, either hosting malware, drive-by downloads, or being a command and control for botnets. A domain appearing in the block list is considered to be authoritative to all over all other scores.
Tip: This is equivalent to a -1 return value in the /domains/categorization/status result from the API.
This alert also means that this domain will be blocked in the main Umbrella product, provided that the security category for this domain is blocked by a policy and that the policy is correctly applied to the identity attempting to visit the domain.
“This domain is associated with the following named attack:”
This alert is part of Investigate's threat attribution feature. The alert appears when a domain matches the attribution features for a particular named threat. Threat attribution takes place when the Umbrella security labs teams identifies features of a domain, IP, or ASN as a part of the framework tied to emerging or known attacks. When a domain is added to the Umbrella block list, we look to see if there’s a botnet or malware network that’s been known to use the IP address, ASN or domain features associated with the domain. We can also assign automatic attribution to named attacks by noting key security features shared between hosts associated with the attack, such as shared IP space or domain name algorithms. From the context gathered from clients using Umbrella's DNS service and other related services, we can see which additional domains have already infected clients with new variants of existing threats and add the threat attribution.
A real-world example of a threat attribution is Cryptolocker, a very common form of malware utilizing command and control callbacks.
“Classifier prediction: suspicious”

When the Umbrella Investigaterisk score is a negative score, Investigate returns a classifier prediction of Suspicious and displays a red alert.
A classifier prediction is a score based on mathematical algorithms run against the other scores displayed in Investigate and is not tied to any single security feature. It is intended to be predictive and serves as an indicator that the domain may require further investigation.
It is not considered authoritative over the block list, and having a classifier of ‘suspicious’ does not mean the domain will necessarily be blocked in Umbrella under a security category.
Umbrella Investigate Risk Score

The Umbrella Investigate Risk Score is scaled from 0 to 100, with 100 being the highest risk and 0 being no risk at all. It is a computation based on the security features and scores that pertain to a domain—these scores are covered in the Security Features section.
The Umbrella Risk Score is an aggregation of the security details for a domain that you can use to quickly determine whether a site might require further investigation.
Tip
The graph score is unique to the graphical user interface and is not available in the API. The Graph Score is calculated on the fly, in real time, based on the latest information available to Umbrella.
“One or more of the IP addresses that this domain resolves to are currently blocked by Umbrella”
When querying a domain name, there are instances where the domain may resolve to several different IP addresses. The domain itself may not necessarily be blocked but one or more of the IP addresses that this domain resolved to are blocked. For more information about the IP that was blocked, scroll down to the “IP Addresses” section in the Investigate results.
“This domain has a suspicious SecureRank2”

A suspicious SecureRank2 is when the SecureRank2 value for a domain is equal to or less than -40. The SecureRank2 is the ranking of a domain based on the lookup behavior of client IP for the domain. SecureRank2 is designed to identify domain names requested by known infected clients but rarely requested by clean clients, then assuming these domains are more likely to be bad. A low score means infected clients were likely to visit this site.
Our blog has more information how we generate the score based on client behavior:
Introducing SecureRank, a large scale discovery algorithm for predictive detection
The Securerank2 score ranges from -100 (suspicious) to +100 (benign)
“This domain has a suspicious RIP score”

A suspicious RIP score is a RIP value that’s equal to or less than -50. The RIP is a score given to a domain based on the IP address(es) it resolves to and the reputation score of the IP address(es). If a domain resolves to an IP or IP range that is considered to have a poor reputation, this boosts the score. For example, a provider that is actively allowing malware or phishing sites to be hosted on their networks would trigger a high RIP score for any domain hosted on their IP space. For more information about the IP reputation, click on the IP address(es) that Investigate lists for this domain.
The RIP score ranges from -100 (suspicious) to 0 (benign).
“The domain has a suspicious ASN score”

A suspicious ASN score is an ASN score value that is less than -2. This score is similar to the RIP score: if a domain resolves to an ASN that has a poor reputation, the score will be more suspicious. Information about the ASN reputation can be found by clicking the AS number listed in the Features section for this domain.
The ASN score ranges from -100 (suspicious) to 0 (benign).
“This domain has a suspicious prefix score”

A suspicious prefix score is when the prefix score value that is less than -10. This score is similar in context to the RIP and ASN scores. Prefix score ranks domains given their IP prefixes (An IP prefix is the first three octets in an IP address) and the reputation of these prefixes in regard to hosting malware or botnets.
The prefix score ranges from -100 (suspicious) to 0 (benign).
“This domain might be a fast flux”

The value for ‘fast flux’ security is set to true, and the domain name looks like a candidate for fast flux. Fast flux is a DNS trick used by criminals to hide phishing and malware delivery sites behind a high number of IP addresses that are constantly changing. This alert is to let you know the IP address that this FQDN resolves to have been changing rapidly.
###Yellow Warning Notifications
The yellow alerts are ones meant to warn you about potentially suspicious scores within the Investigate's features that are worthy of attention.
“Some users have explicitly blocked this domain”

The warning indicates that, in some cases, the Umbrella DNS resolvers have returned a block page for this site. This warning is literal: some users of the Umbrella DNS resolvers have explicitly requested that this domain be blocked on their networks. In some cases, this means that the domain was made for reasons such as a user thinking this was bad, but it may in fact not be.
“This domain has appeared in the Umbrella block list”
This warning is to let you know that this domain is blocked as part of the Umbrella block list.
“Geo distance between hosts serving this domain is fairly high”
Geo-distance between hosts is a mathematical algorithm scoring the relative distances—in kilometers—between hosts serving the domain data. This reflects unusually high scores for the Mean Geo-distance and Sum Geo-distance in the domain features. The alert will appear when the mean distance between hosts serving the site is over 3000 kilometers.
In our research, we've found that hosts serving a non-malicious domain tend to be geographically close, whereas a domain serving malware can be served by hosts spread all around the globe. Our blog provides more information on how we use distance between domains to determine the maliciousness of certain domains:
The role of country code top-level domains (CCTLDS) in malware classification
“Authoritative servers for this domain are unstable”

This alert occurs when DNS request for the IP of this domain returns a SERVFAIL more than once. The SERVFAIL implies that the authoritative server may belong to a network provider that is not able to provide reliable DNS service because it is part of the botnet activity, or simply an untrustworthy network provider. To read more about how authoritative servers can help determine whether a domain is, read this blog post:
Discovery of new malicious domains using authoritative name server traffic
“This domain may have been created using a domain generation algorithm (DGA)”

This alert occurs when the DGA (Domain Generation Algorithm) score is -25 or lower. The DGA for a domain name is a score that correlates highly with the domain being randomly generated by a computerized algorithm as part of a botnet attack. A randomly generated name is used in order to stay ahead of static block lists of known bad domains. To read more, see Finding the Patterns in a Mysterious New DGA.
This score ranges from -100 (suspicious) to 0 (benign). A score below -25 is generally suspicious if the domain is unknown.
“This domain has very low TTLs”

This alert occurs when the median TTL is equal to or below five. A domain with a low TTL is likely to have an IP change. TTL is normally lowered in advance of a normal migration of a domain from one IP to another, but it is also lowered when a domain is being used to mask multiple IP addresses hosting malicious content.
Green alerts indicate that there are characteristics or attributes of the domain that are typical and often associated with benign domains.
"Classifier prediction: benign"

The Classifier prediction of benign is reflective of a positive Umbrella score. This indicates a domain is already known to be good and is not worthy of further investigation.
For example:

Tip
This notification is not necessarily the equivalent of the domains/categorization endpoint from the API returning a score value of +1.
The Umbrella score is calculated separately from the classifier prediction of benign, but a site will only be considered benign when the Umbrella score is greater than zero. The benign categorization is not a static allow list but a dynamic categorization based on the Umbrella score.
“This domain has a fairly good SecureRank2”

This alert is shown when the Securerank2 security feature has a value equal to or greater than 40.
The SecureRank2 is the ranking of a domain based on the lookup behavior of client IP for the domain. SecureRank2 is designed to identify domain names requested by known infected clients but never requested by clean clients, then assuming these domains are more likely to be bad. A fairly good score means that very few infected clients were visiting this domain.
Our blog has more information on how SecureRank is determined:
Introducing SecureRank, a large-scale discovery algorithm for predictive detection
“This domain is very popular”

This alert is shown when the popularity security feature has a value equal to 100. The popularity is a relative weight score comparing this domain to the rest of the internet and very popular domains are highly unlikely to be worthy of investigation. Typically, a site receiving a note about being 'very popular' is within the Alexa 500 although there times when unusual sites can rate as ‘very popular’, such as advertising hosts or content delivery networks.
“According to the requester geo distribution, this domain is very likely to be benign”

This alert is shown when the geo-distribution for the domain is small, meaning that the hosts serving the domain are all within the same geographical area. In our research, we have found domains with hosts in the same geographic region are less likely to host malware. For more information on this research, please read this blog:
The role of Country Code Top Level Domains (CCTLDs) in malware classification
###Blue Informational Notifications
Blue bars indicate there's no IP data to be found about the domain, or the domain is a CNAME for another domain.
“No IP addresses have recently been seen for this domain name”

If a domain has had no traffic to it recently from any clients, then you can expect to see this alert appear, as we’ve not had to resolve the domain to an IP address.
In that case, the DNS Queries graph may display that there’s no been any query information in recent days.
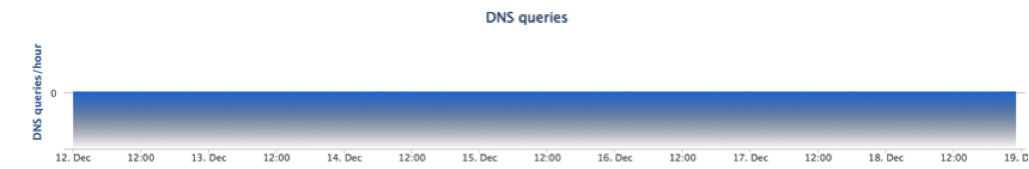
On your network, if you are seeing requests to a domain that’s not had any IP addresses seen for it, it is possible the machine making the request is infected and trying to contact command and control botnet hosts that don’t yet exist.
Alternately, the domains that the infected client is trying to contact could be ‘sinkholed’ and no longer present on the internet. This is an example of traffic to a Conficker domain that is still receiving requests, although it is no longer present on the internet:
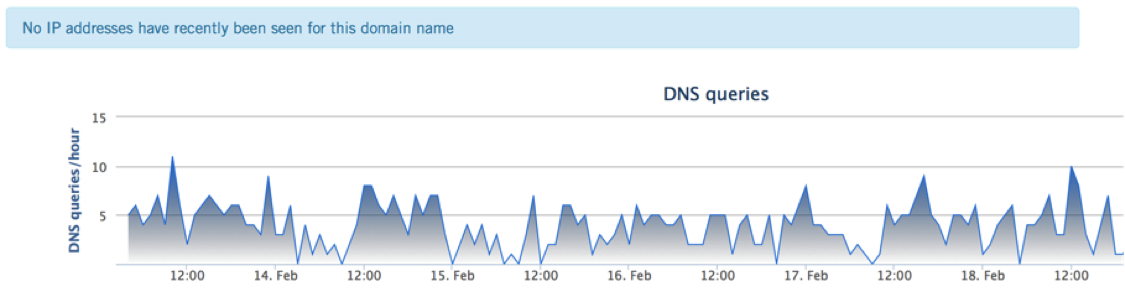
However, this can also happen with domains that generating a very high volume of queries. These domains will have intentionally been removed from Investigate as not to skew events by their sheer magnitude. An example of this is spamhaus.org.
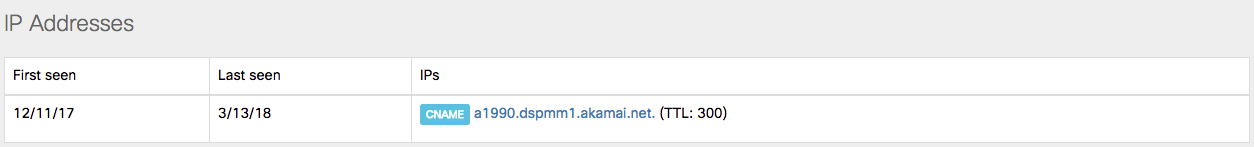
“This record is a CNAME”
Another common blue bar that's displayed is when is when the domain you've looked up is a CNAME.

In this case, there's little information on the domain itself as requests are directed to the CNAME. We recommend you follow the link in the IP Address section of the Investigate interface to see information on the site that this domain is a CNAME for.
Domain Details < Notification Alerts > Timeline
Updated almost 2 years ago
