Configure Protected Networks for Roaming Computers
The Umbrella DNS redirection setting for roaming computers manages and protects the traffic from the Umbrella roaming client or the AnyConnect Umbrella Roaming Security module when the roaming computer is on a protected network or located off the protected network.
Roaming Computers on a Protected Network
- Roaming computers are protected by an organization's on-network policy's settings.
- The traffic sent from the roaming computer is identified by the network identity in the Activity Search report.
- The Umbrella roaming client or the AnyConnect roaming security module is managed by Umbrella and is disabled. DNS settings revert to the DNS server configured for the network.
- DNS traffic from the roaming computer is not encrypted.
Roaming Computers Off-Network
- Roaming computers are protected by an organization's off-network policy's settings.
- The traffic sent from the roaming computer is identified by the roaming computer identity in the Activity Search report.
- The Umbrella roaming client or the AnyConnect roaming security module is managed by Umbrella and is enabled.
- DNS traffic from the roaming computer is encrypted.
Table of Contents
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
Before You Begin
- Configure and add your networks in Umbrella. For more information, see Add a Network Identity.
- Install and configure the Umbrella roaming client or AnyConnect Umbrella roaming security module on your roaming computers. For more information see Roaming Client User Guide and The AnyConnect Plugin: Umbrella Roaming Security.
- Configure the general settings for the roaming computers in your organization. For more information, see Roaming Computer Settings.
Configure Your DNS for Local Network
To enable DNS redirection for a roaming computer on a protected network, you must configure DNS for the local network and add a network to Umbrella. For more information, see Point Your DNS to Cisco Umbrella.
- Configure the local DNS servers to use Umbrella as the only DNS forwarders.
- Configure the DHCP scope to provide the IPs of the internal DNS servers.
- The local network must allow direct access to either 53/UDP or 443/UDP with a destination of 208.67.222.222.
- The workstation's egress IP must match the configured local DNS server's egress IP's registered network.
Test Your Configured DNS
Run the following commands and confirm that the output contains the same value of the originId.
nslookup -type=txt debug.opendns.com 208.67.222.222
nslookup -type=txt debug.opendns.com [local DNS server IP]
Add Policies
You must add at least two policies that are configured to manage the roaming computers in your organization on-network and off-network.
- Add a policy for roaming computers that send traffic from a protected network.
- Add a policy where the roaming computers are located off the protected network.
- Give the protected network policies higher priority than the off-network policies.
Step 1: Add Networks to On-Network Policies
Add your configured networks to an existing policy or create a new policy and include the network. For more information, see Add a Policy. The on-network policy does not need to enforce content filtering or configure logging. Security filtering is enabled by default.
Step 2: Add Roaming Computers to Off-Network Policies
Add your configured roaming computers to an existing policy or create a new policy and include the roaming computer. For more information, see Add a Policy.
Step 3: Order Your Policies
The order of your policies is important. Make the on-network policies have higher precedence than your off-network policies. Give your on-network policies that only contain network identities the highest priority. The on-network policies appear first or before the other policies in your organization.
- On-Network—When the roaming computer is on the protected network, the on-network policy takes precedence. The traffic is visible only for the network in the Activity Search report.
- Off-Network—When the roaming computer is located off the protected network, Umbrella applies the off-network policy. The Umbrella roaming client or the AnyConnect roaming security module provides visibility into the traffic sent from the roaming computer and Umbrella logs the roaming computer traffic in the Activity Search report.
Procedure
Configure the protected network settings for the roaming computers in your organization. For more information, see Roaming Computer Settings.
- Navigate to Deployments > Core Identities > Roaming Computers and click Settings.
- Select the Cisco Secure Roaming Client tab.
- For Traffic Forwarding on Umbrella Protected Networks, check Disable DNS redirection while on an Umbrella Protected Network and click Save.

Traffic Forwarding on Umbrella Protected Networks—Disables the DNS-based protection applied by the Umbrella roaming client, AnyConnect Umbrella roaming security, and web-based protection applied by AnyConnect Umbrella roaming security while on a network protected by Umbrella. This includes the intelligent proxy as it is a DNS-based redirect. Relies on the protection of the network for all features. To trigger this setting, network registration and the network must be the higher policy (not same, but higher) and the local DNS server egress network must be the same network registration as straight out from the computer to 208.67.222.222. Having the network in the same organization will not trigger the disabling of traffic redirection. Currently, DNS and web traffic forwarding can only be disabled together.
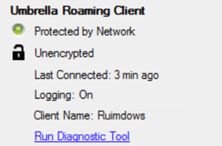
- After DNS redirection is enabled, the roaming client or AnyConnect Umbrella roaming security module receives an update from Umbrella. On your roaming computer, view the status of the Umbrella roaming client or AnyConnect Umbrella roaming security module. After the update is completed, the roaming client's tray icon status displays Protected by Network. The client update may take ten minutes.
Domain Management < Configure Protected Networks for Roaming Computers > Roaming Computer Settings
Updated over 1 year ago
