Prerequisites
Table of Contents
Virtual Appliance Requirements
- Two virtual appliances (VAs) per Umbrella site—VAs must be deployed in pairs to ensure redundancy at the DNS level and to allow for updates without downtime.
- VA Specifications—At a minimum, each VA requires the following allocated resources:
- Two virtual CPUs
- Minimum 2GB of RAM
- 7 GB of disk space.
Each VA is able to process millions of DNS requests per day using these specifications. If you believe your network will exceed this number, see Sizing Guide.
Important
High-traffic site VAs should use two virtual CPUs and 2048MB of RAM per VA.
A high-traffic site is one that has more than 500 DNS queries per second coming from the overall network.
- Correct Date/Time—Ensure your hypervisor host has the correct date and time. The incorrect date or time can cause update or sync issues with the VAs. The VA syncs time independently and is always set to UTC by default.
VMware Requirements
- VMware ESXi (supported versions as per VMware)
For more information, see VWware documentation. - VMware Cloud on AWS
Microsoft Hyper-V Requirements
One of the following Windows Server operating systems:
- Windows Server 2012, SP1, or R2 (Standard or Data center), 2016 or 2019 with Hyper-V role
- Hyper-V Server 2012, 2012 R2, 2016 or 2019
Note: Deploying the virtual appliance through System Center Virtual Machine Manager (SCVMM) has not been qualified and is not officially supported.
Networking Requirements
Once VAs are deployed and ready to be utilized, endpoint clients must exclusively resolve DNS through the VAs and not your local DNS forwarders. This is usually accomplished through the network's DHCP configuration. For more information, see Local DNS Forwarding.
The following firewall/ACL requirements ensure VAs can communicate with the Umbrella cloud services and local DNS forwarders/servers. These requirements apply to each platform to which the VA is deployed.
| Port and Protocol | Source | Destination | Note |
|---|---|---|---|
| 53 TCP + UDP | Virtual Appliance | Local DNS servers | Standard DNS traffic for internal domains. |
| 53 TCP + UDP 443 TCP + UDP 5353 TCP + UDP | Virtual Appliance | Umbrella for Government resolvers Alternate resolvers if you have configured the VA to use other Umbrella for Government resolvers: | Standard and encrypted DNS queries to Umbrella for Government resolvers. Port 443 is used as failover if your firewall does not allow DNSCrypt on port 53. Port 5353 is used as failover if DNSCrypt is not allowed on port 53 and port 443. |
| 443 TCP | Virtual Appliance | api.umbrellagov.com | HTTPS—Used for registration, health checks, and updates from Umbrella. |
| 80 TCP | Virtual Appliance | ocsp.digicert.com crl3.digicert.com * crl4.digicert.com | HTTP—Used for fetching the SSL revocation list to initiate the HTTPS connection. ocsp.digicert.com, crl3.digicert.com, and crl4.digicert.com Note: The Digicert domains resolve to various IP addresses based on a CDN and are subject to change. |
| 443 TCP | Virtual Appliance | disthost.umbrellagov.com | Updates to the VA |
| 123 UDP | Virtual Appliance | NTP servers If you have configured custom NTP servers on the VA, use those IPs instead. | NTP—Protocol to synchronize time. |
| 443 TCP | Chromebook client | Virtual Appliance(s) | Required for Chromebook client trusted network feature. |
| 443 TCP | Umbrella Active Directory Connector | Virtual Appliance(s) | Used to send user/IP mapping (one-way) from the Active Directory (AD) connector to the VA. |
Networking: Additional Considerations
Intrusion Protection Systems (IPS) and Deep Packet Inspection (DPI)—If utilizing an IPS or DPI, ensure that traffic on port 53 TCP/UDP to and from the VAs is excluded from packet inspection, as Umbrella's DNS encryption methods might be flagged and dropped. If the VAs cannot successfully send and receive encrypted DNS packets, Umbrella displays a warning in the dashboard.
Network Address Translation (NAT)—If a routing device running a separate NAT is placed between endpoints and VAs, an endpoint's IP address will show as the NAT device's IP address in the dashboard. The endpoints must reach the VAs without being subjected to a separate NAT. If you are unable to remove a routing device with a separate NAT, you may have to run a separate set of VAs within that NAT. If you have any questions regarding this matter, contact Support.
HTTP Proxies / Content Filtering—Most solutions attempting to locally proxy, cache, or filter HTTP/HTTPS traffic between an endpoint and the internet require additional configuration in order to work in unison with VAs. Failure to adjust the configuration of these solutions before employing the VAs may result in the complete ineffectiveness of the VAs and Umbrella. For more information, see Using Umbrella with an HTTP Proxy. Solutions include:
- Transparent HTTP/HTTPS Proxy
- Standard/Caching HTTP/HTTPS Proxy
- Content Filtering via a hardware appliance
VA-ADC Deployment Procedure
Prerequisites
When deploying the VA-ADC for the first time, generate the Admin API keys.
To generate the Admin API keys:
- Go to the Umbrella Dashboard.
- Select all areas so that the key has the permission to manage all the areas.
- Provide the Expiry Date.
- Select Create Key.
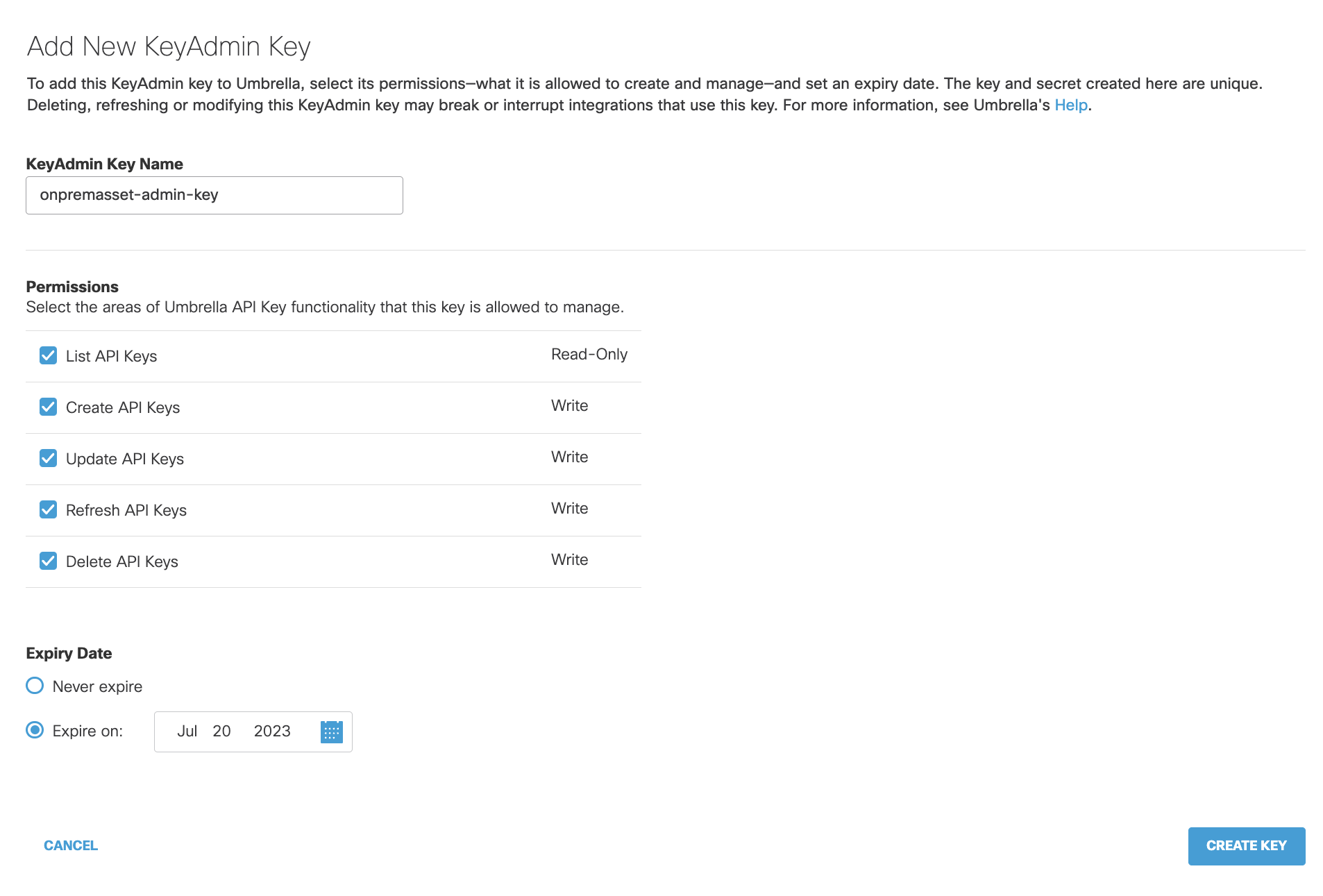
- Copy the KeyAdmin Key and KeyAdmin Secret.
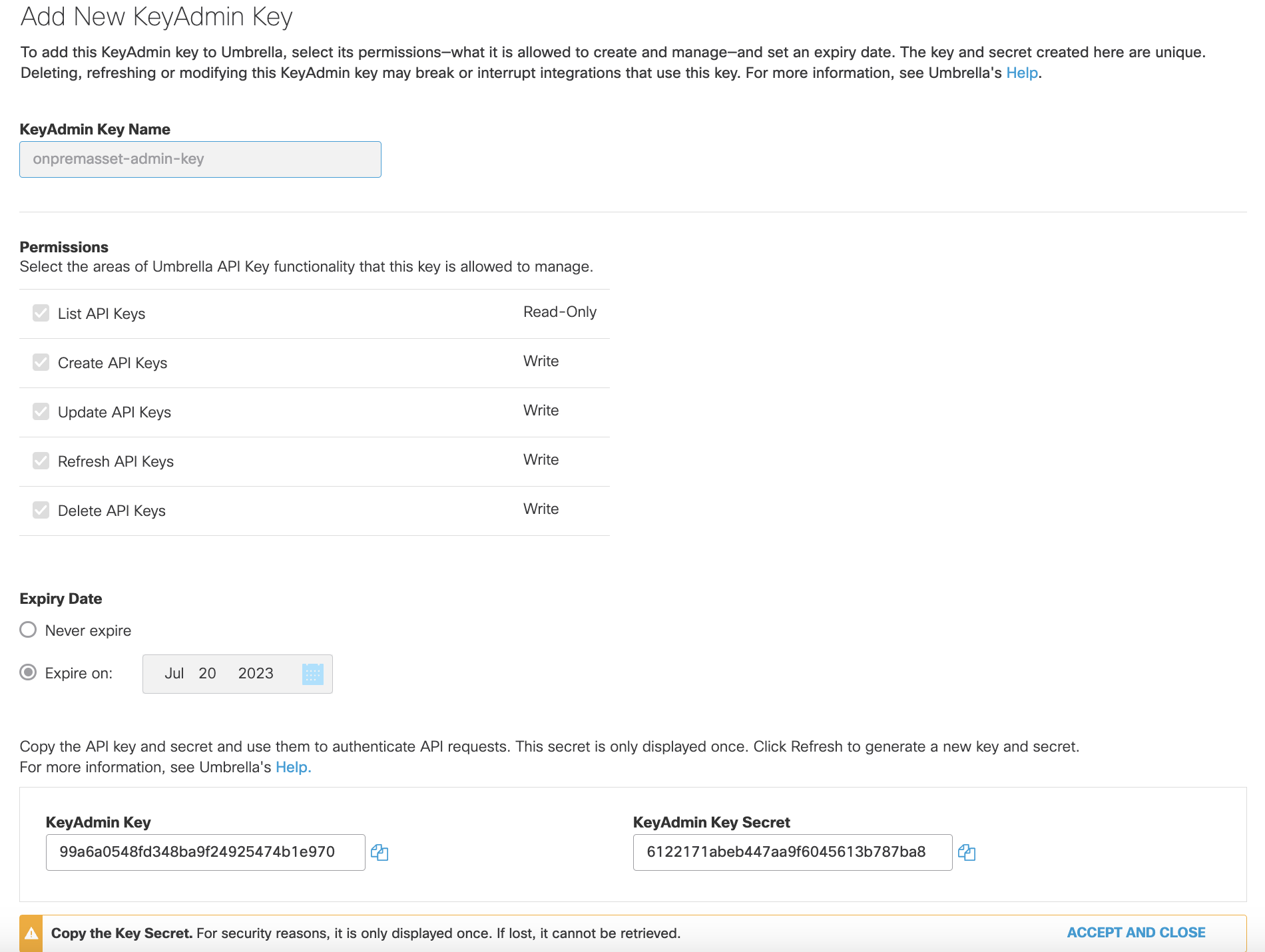
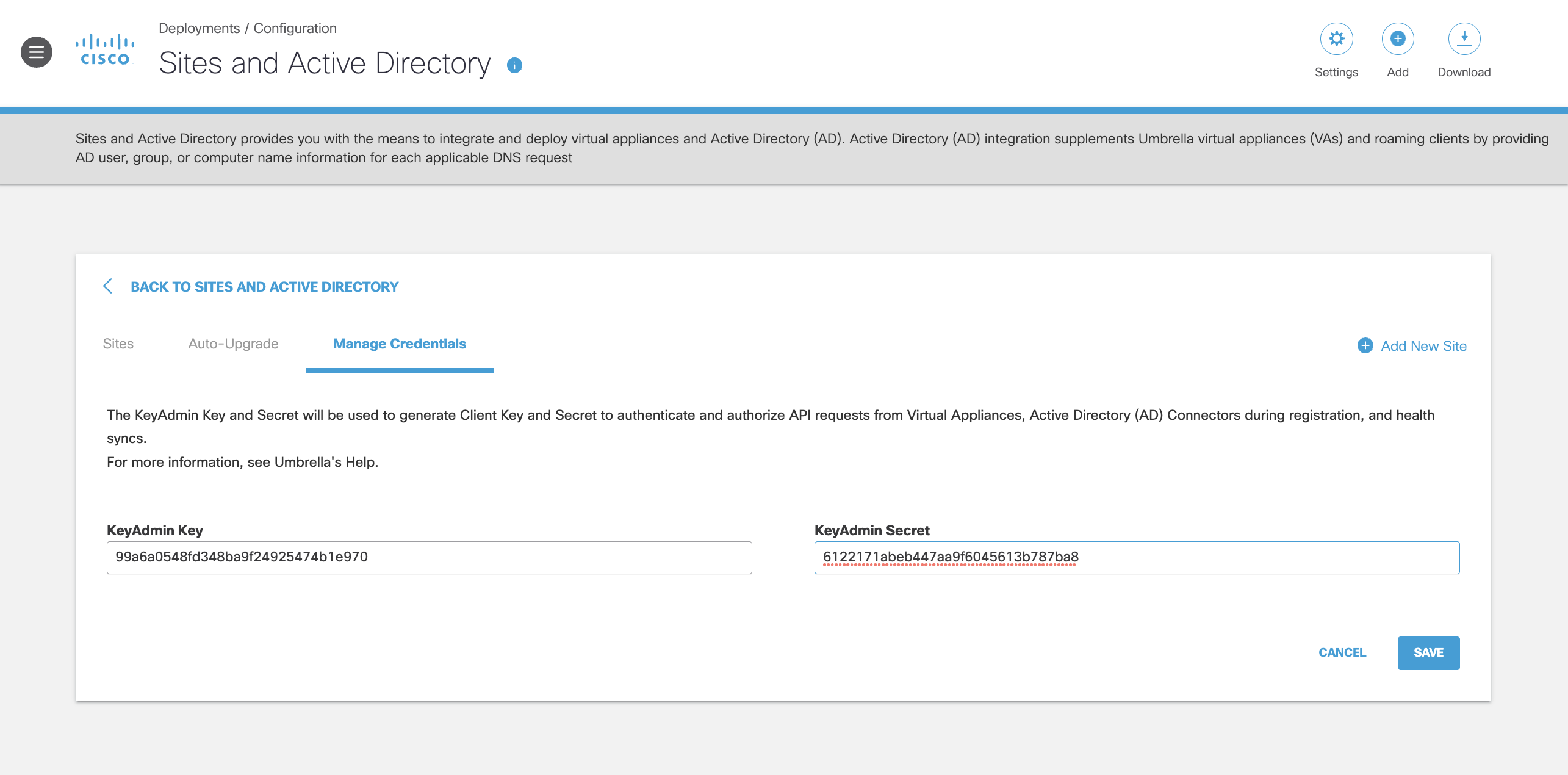
- Navigate to the Umbrella Dashboard > Sites and Active Directory > Manage Credentials.
- Paste the KeyAdmin Key and KeyAdmin Secret generated in the API Keys page.
- Select Save. Client credentials are generated.
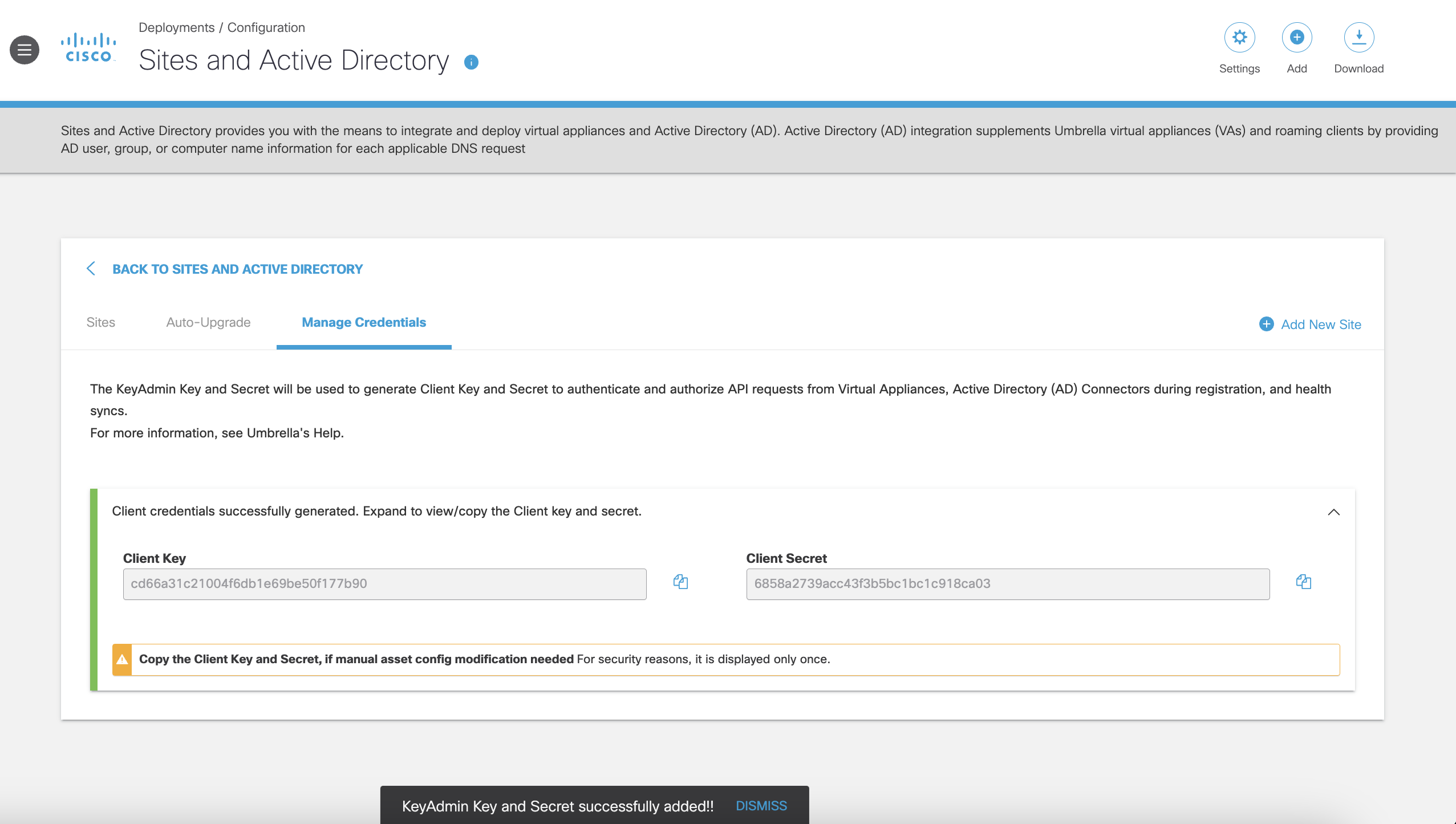
Introduction < Prerequisites > Deployment Guidelines
Updated 10 months ago
