Deploy the Chromebook Client
The Cisco Security for Chromebook client allows you to enable DNS layer protection for Chromebook users.
Table of Contents
DNS Layer Protection
For DNS layer protection, DoH (DNS over HTTPS) is used to send DNS queries to Umbrella for Government resolvers. These DNS queries are sent using DoH templates, which capture the Chromebook identities. The Chromebook identities are hashed using a Salt value that you configure. Once the Salt is configured on the Umbrella console, you can copy the DoH templates, configure the Enterprise Policy on Google Admin Console and propagate the DoH templates to the Chromebooks.
Deploy Cisco Security for Chromebook Client
The Cisco Security for Chromebook client is deployed using the Umbrella dashboard and the Google Admin Console. Use the Umbrella Dashboard to configure the Salt value, get the URL for the DoH templates, and download the JSON file. Use the Google Admin Console to deploy the Cisco Security for Chromebook client. The configuration and deployment procedures take, approximately, 30 minutes.
Umbrella Dashboard
- Navigate to Deployments > Core Identities > Chromebook Users and click Configure.

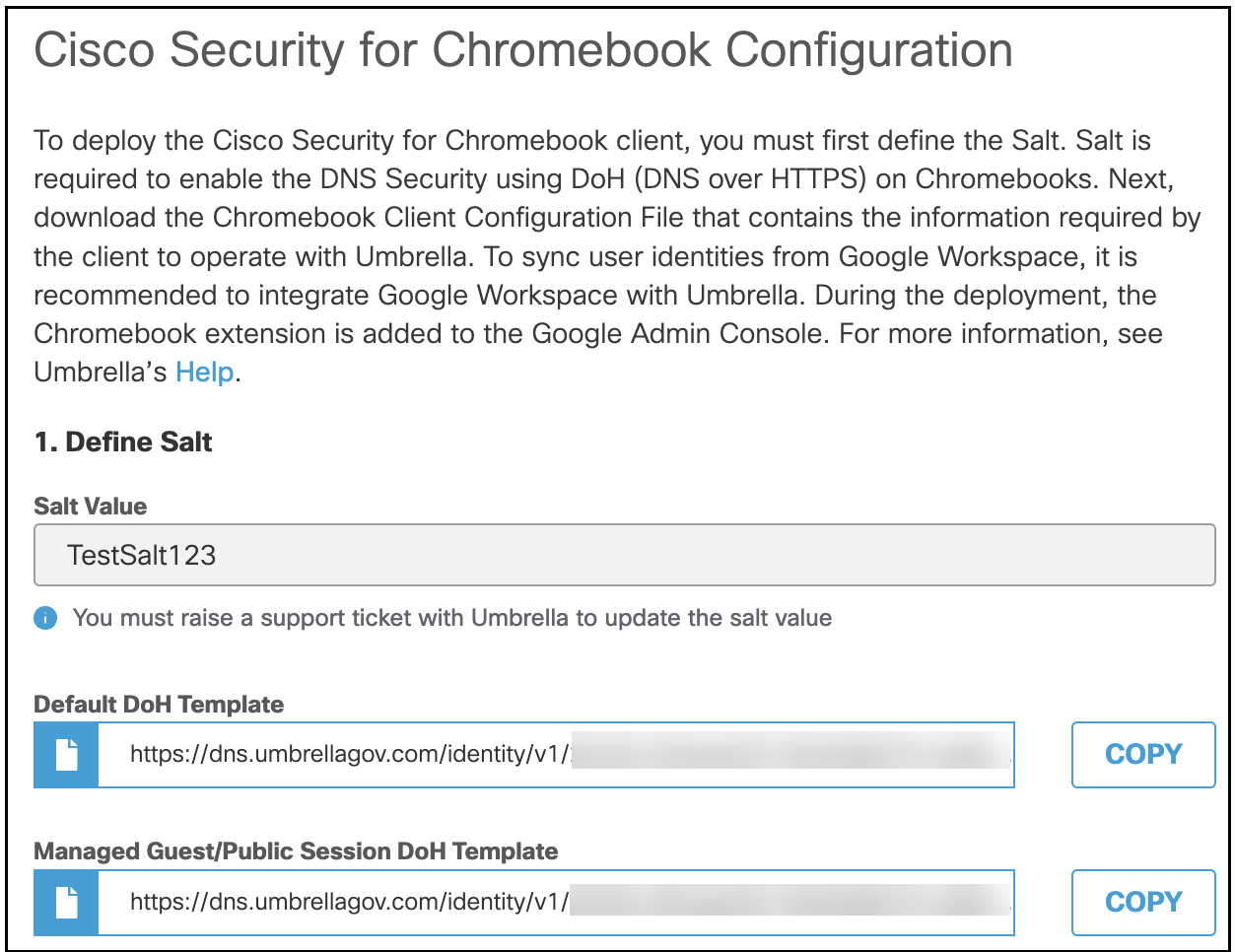
- To enable DoH protection you need to configure the Salt value. To configure the Salt value, click Configure in the Define Salt row.
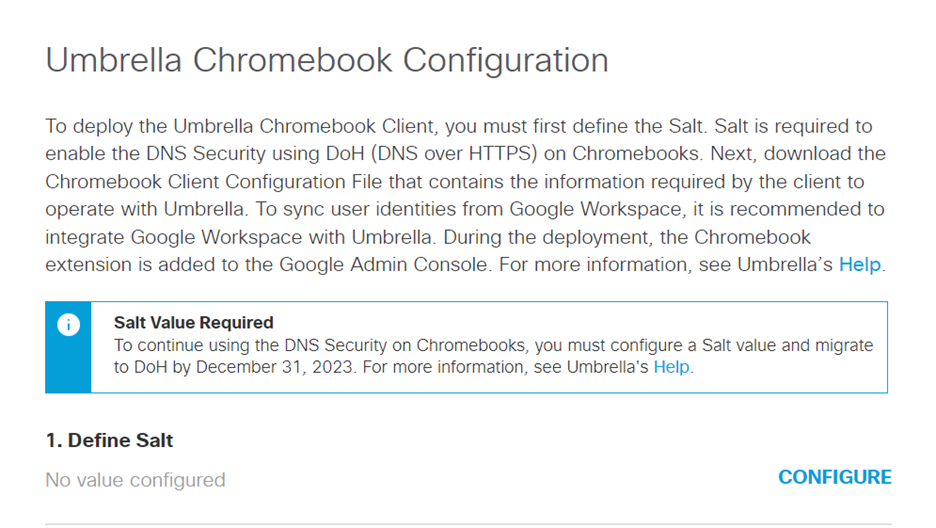
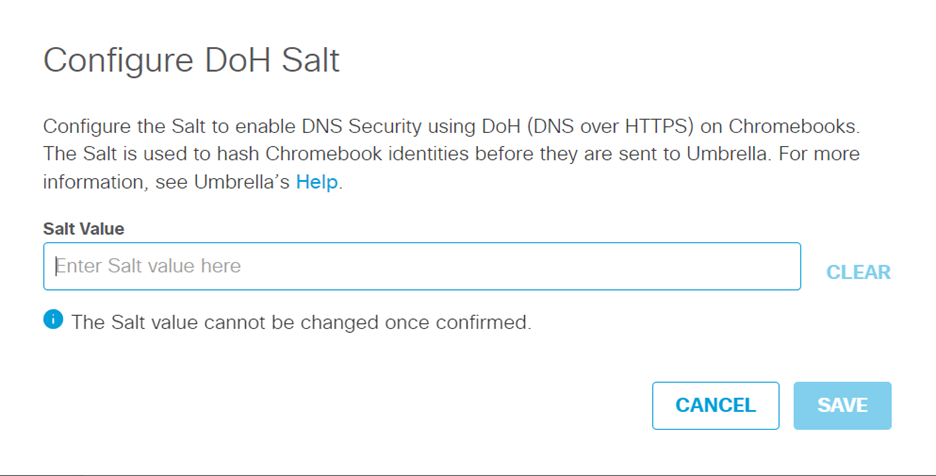
- Enter the Salt value. The Salt value can be between 8 and 32 characters and can be a combination of letters and/or numbers. Special characters are not allowed.
Note
The Salt value cannot be changed once it is saved and confirmed. You will need to raise a support ticket with Umbrella to change the Salt value.
- Once the Salt value is configured, two DoH templates are created. The first template is the default template, which is used for all Managed Chromebooks. The second template is the Managed guest session template, which is used only for Managed guest session devices. Copy and save the configured Salt value and the DoH template URLs. They will be required later when deploying the Cisco Security for Chromebook client from the Google Admin console.
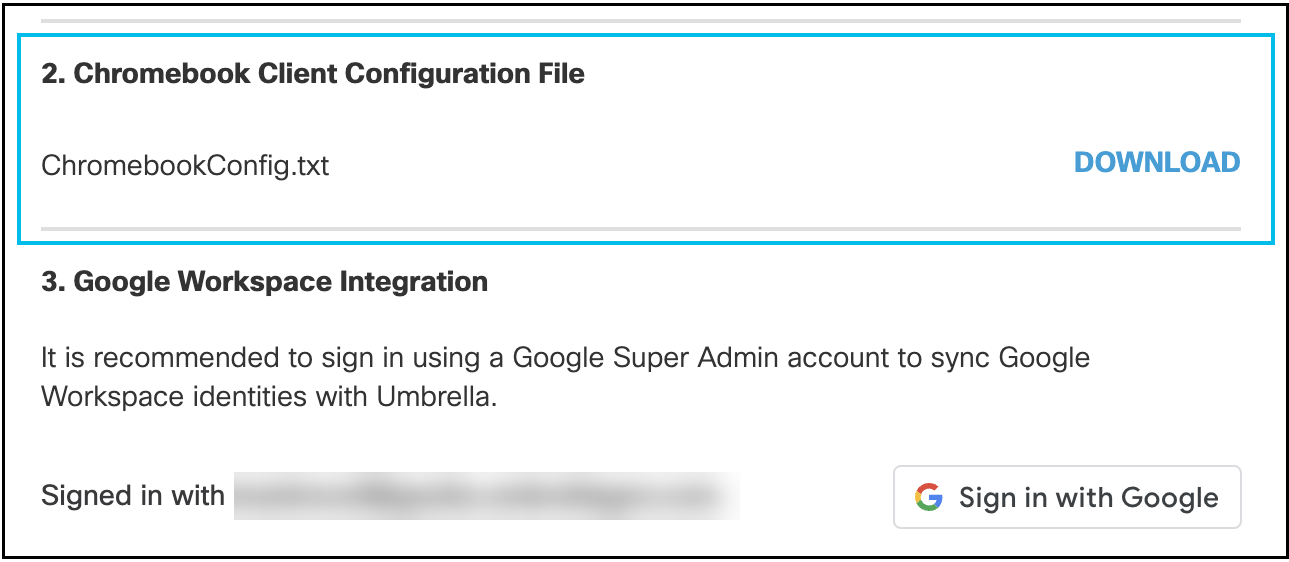
- Click Configure and download the Chromebook Client Configuration JSON file. Save this file to a known location.
Google Admin Console
You can configure the default and the managed guest session DoH templates using the Google Admin console.
Configure Default Template
- Log into the Google Admin console.
- Navigate to Devices > Chrome > Settings > Users & browser settings.
- Filter settings for DNS. The DNS settings are displayed.
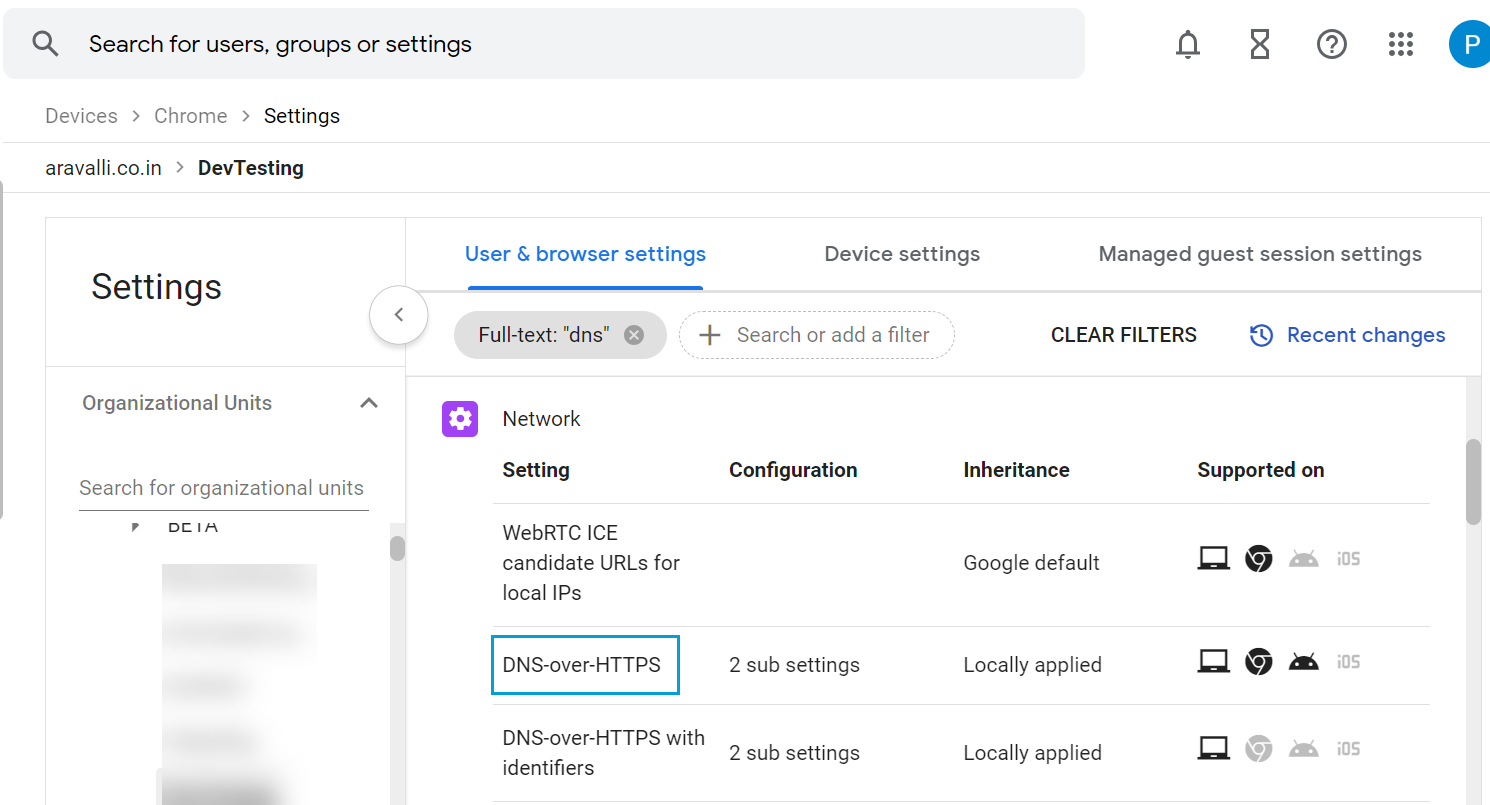
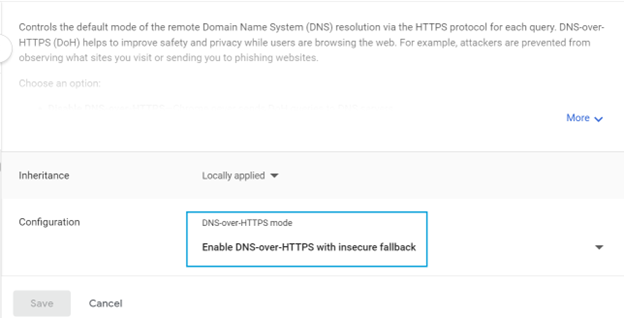
- Select DNS-over-HTTPS and configure it to Enable DNS-over-HTTPS with insecure fallback.
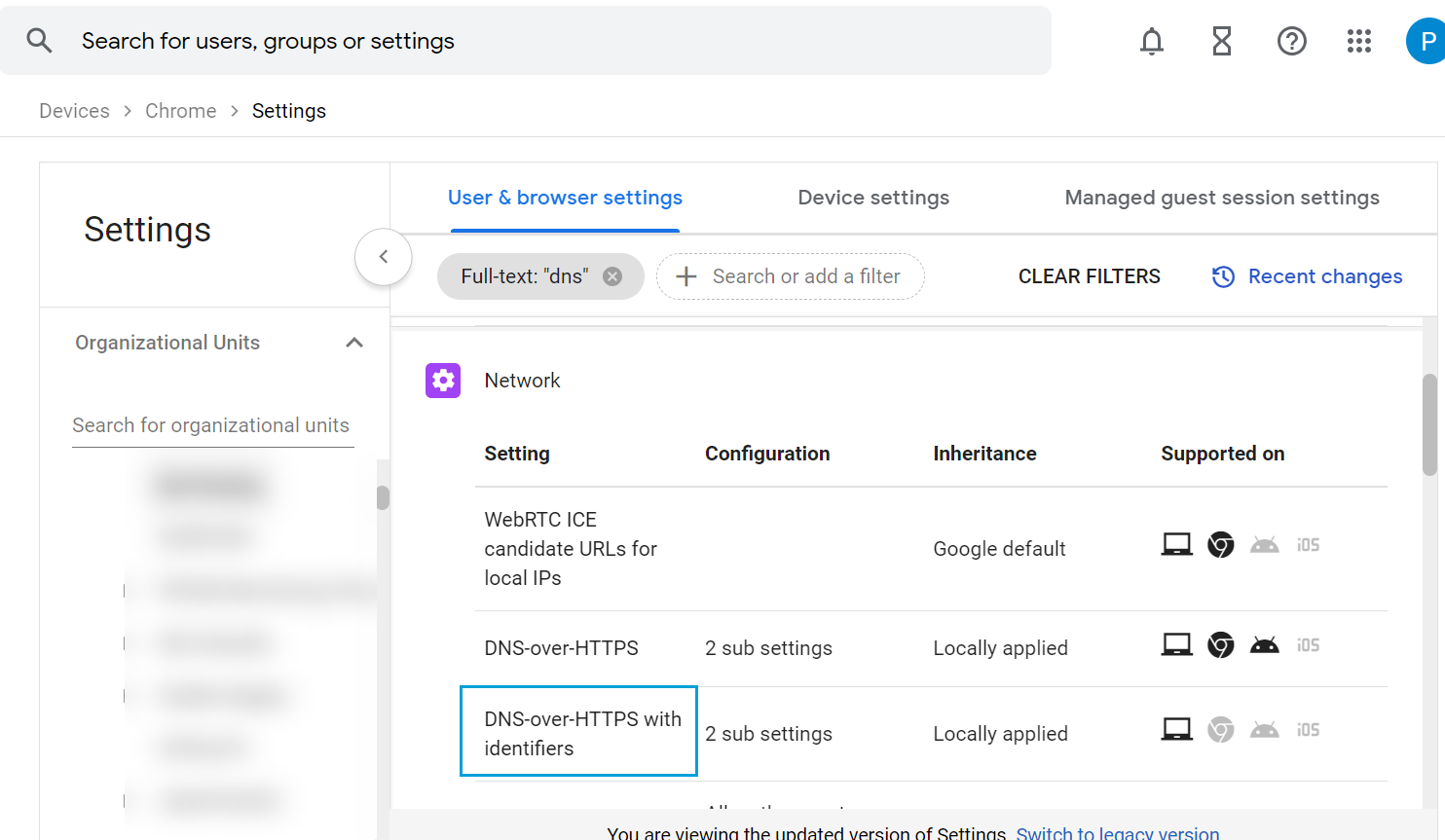
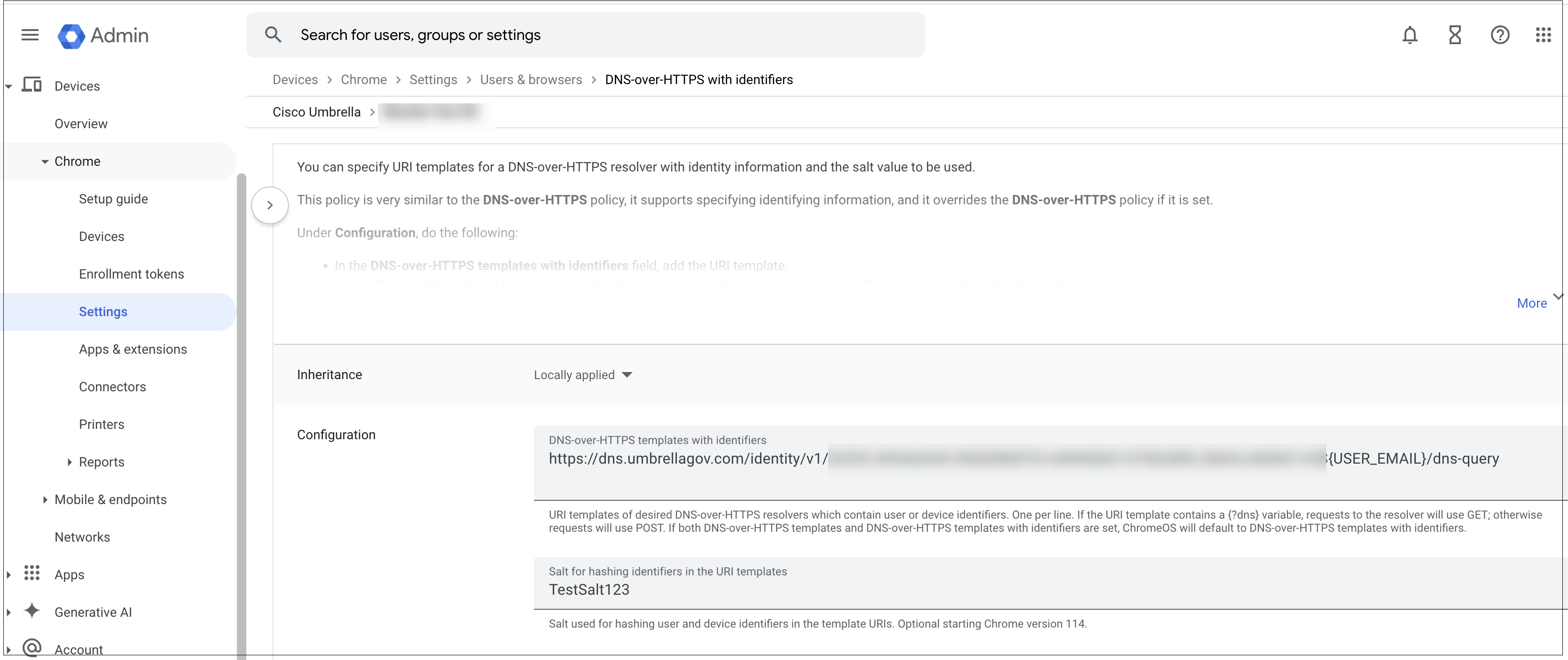
- Return to the Users & Browser Settings page. Select DNS-over-HTTPS with Identifiers.
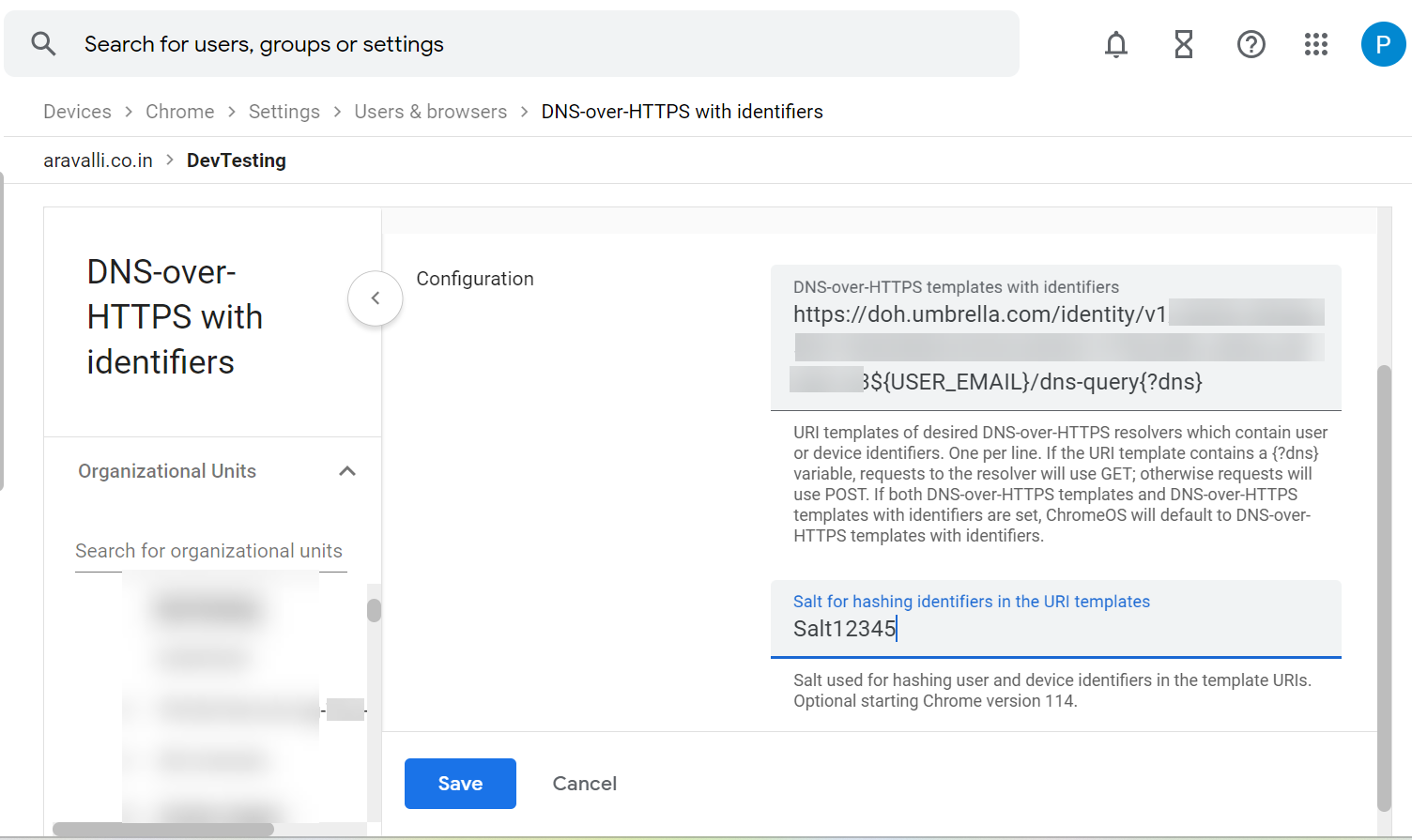
- Enter the URL of the Default DoH template and the Salt value copied from the Umbrella Dashboard in the earlier steps. Click Save.
Note
The Salt value entered here should be the same as the Salt value entered in the Umbrella dashboard.
- From Apps & Extensions, navigate to Users & browsers > Organizational Units.
- Expand Organizational Units and choose the organization into which you want to deploy the Cisco Umbrella Unified Chromebook client.
- Click the + (Expand) icon and choose Add from Chrome Web Store.
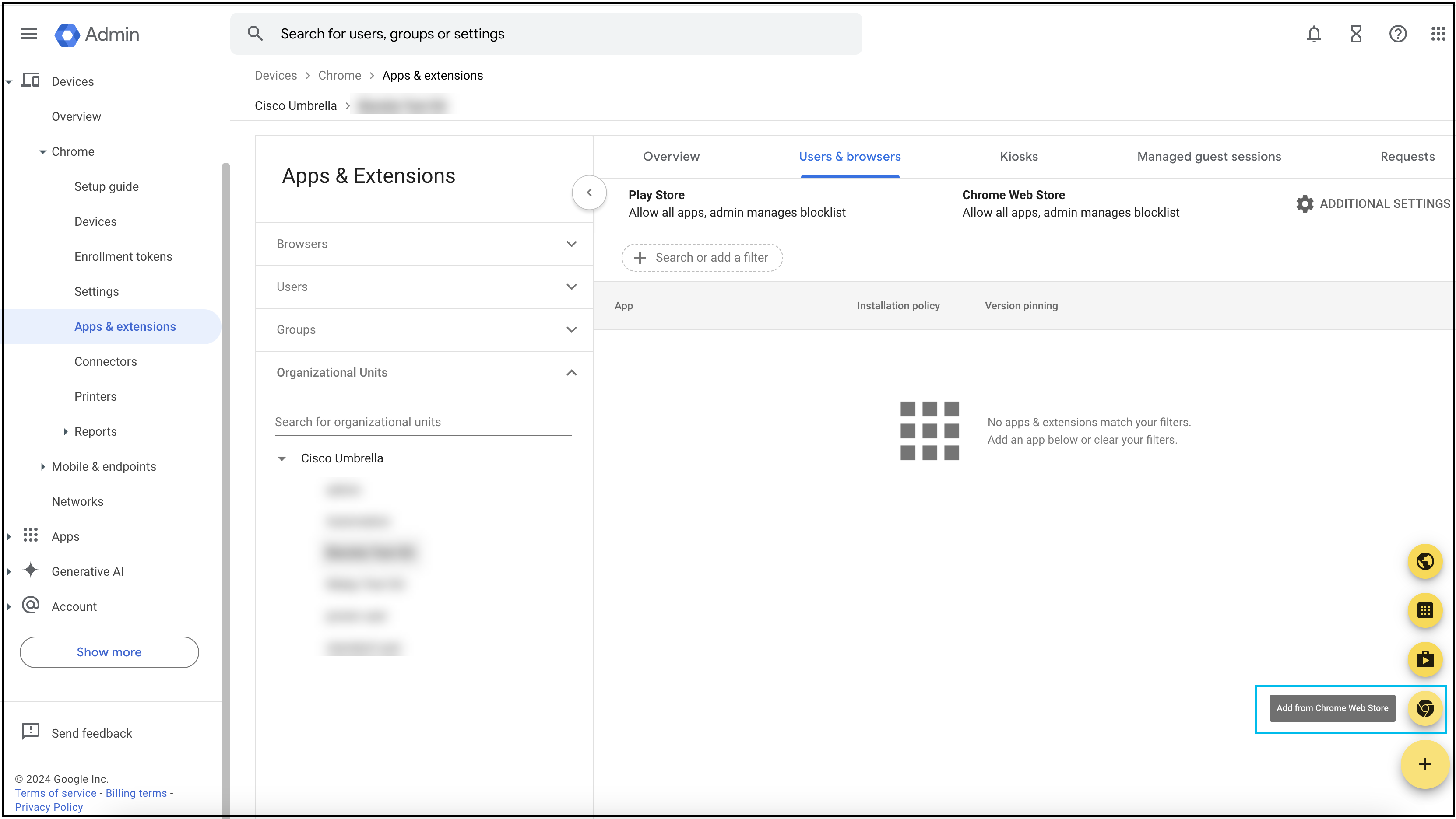
- In the Chrome Web Store, navigate to Extensions and search for the Cisco Umbrella Chromebook client extension using the ID aiaoiippnjfkanmgamnpphpjffaijicm.
Note: When copying and pasting the extension ID into the search field, ensure there are no spaces before or after it. This will help you locate the Cisco Security for Chromebook client extension.
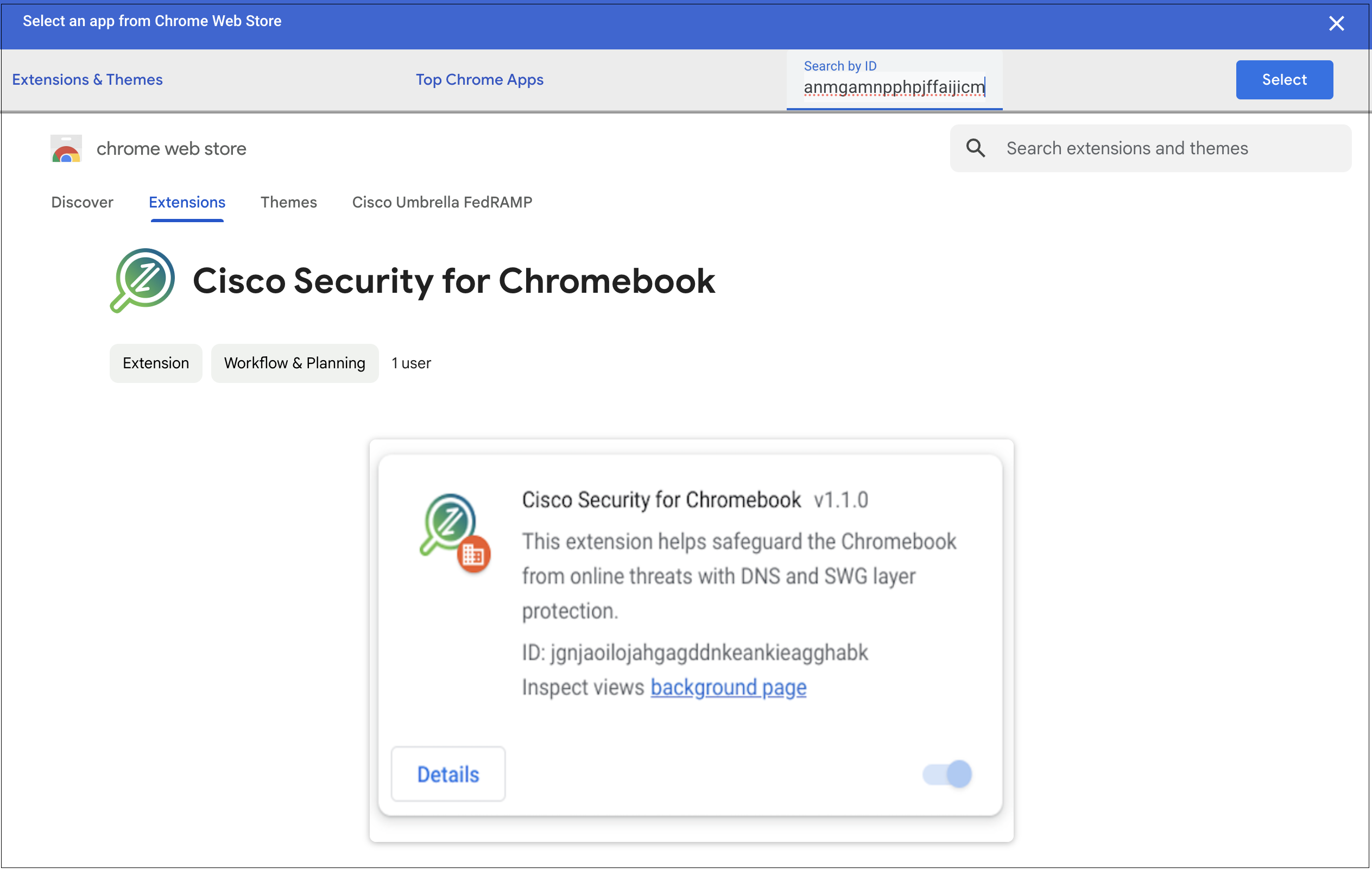
- Click Select. The extension is added to the selected organization unit.
- Copy the JSON file that you downloaded and paste it into the Policy for Extensions section.
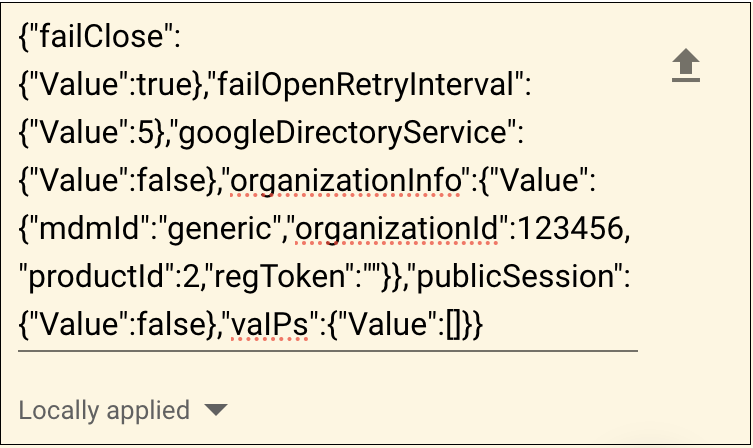
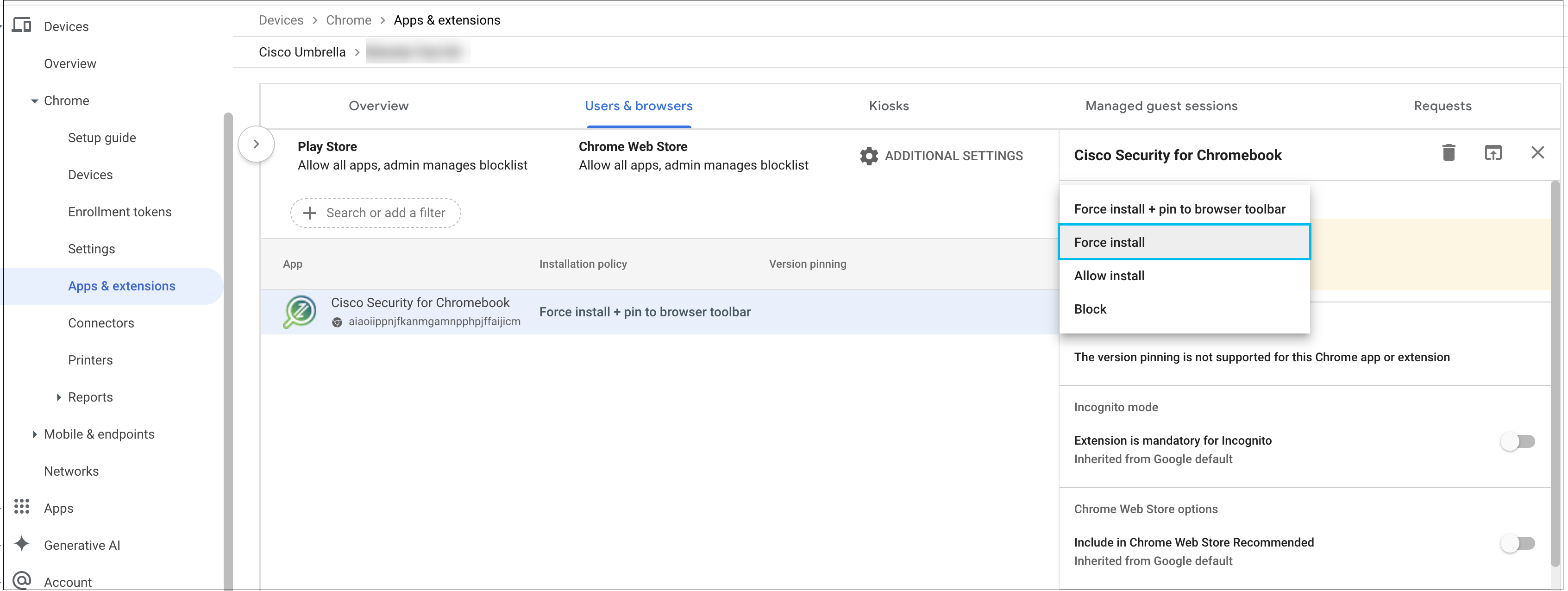
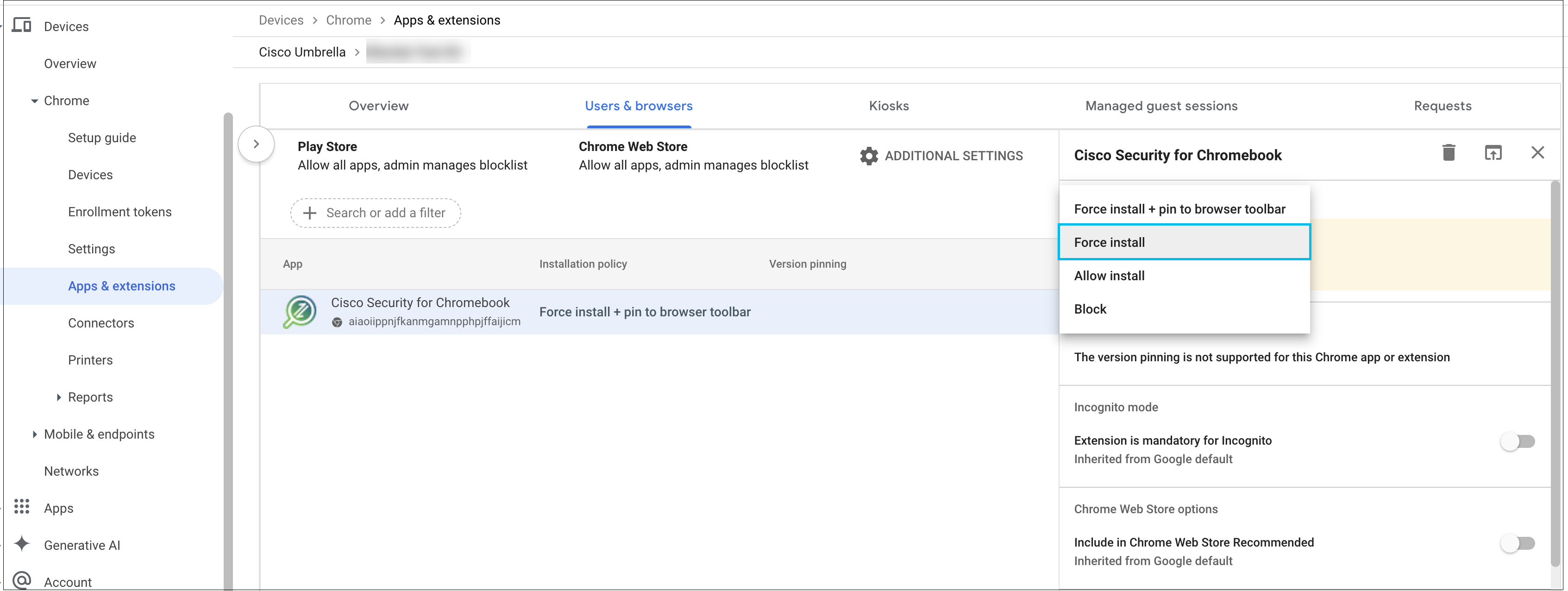
- Choose Force Install and then click Save.
The Cisco Security for Chromebook client extension is installed. Force Install ensures that Chromebook users in the selected Organization Unit cannot remove or disable the extension.
Important
Once the configuration is done and pushed to the device, the user will be prompted with a SAML pop-up window to authenticate based on the integrated IDP. For more information, see SAML Configuration. On successful authentication, the device will be registered and protected by Umbrella. If the user fails to authenticate, the prompt will repeat until correct credentials are provided. The user will need to re-authenticate after the IDP authentication expiry limit is reached.
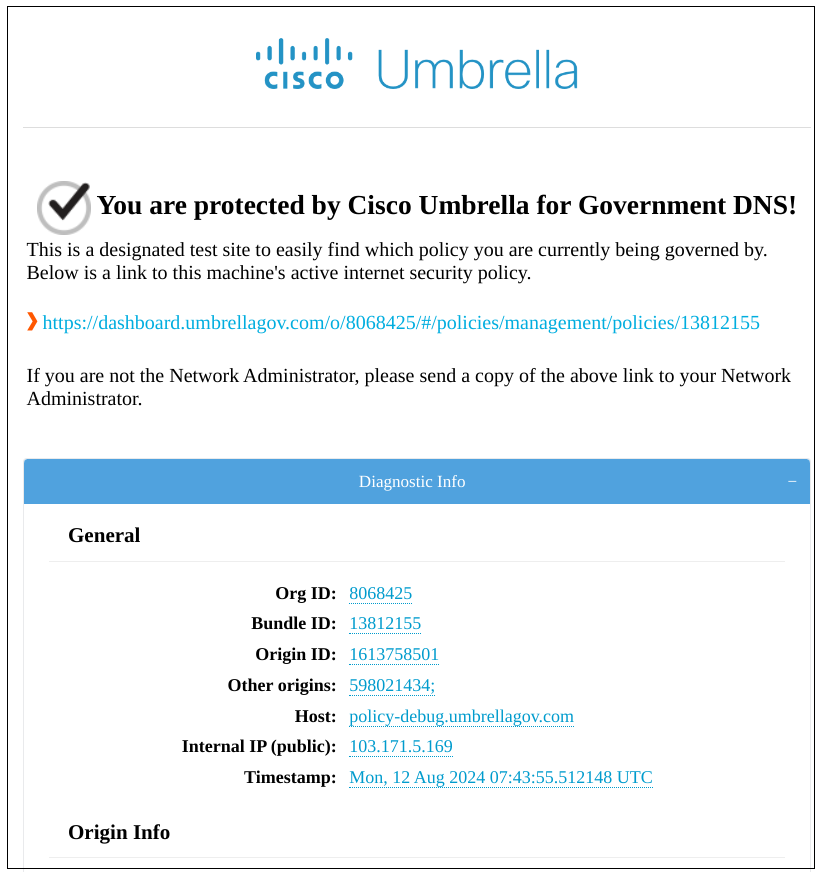
- Open the URL https://policy-debug.umbrellagov.com and verify if the device is being protected by Umbrella. For DNS customers, the message displayed is “You are protected by Cisco Umbrella DNS!”
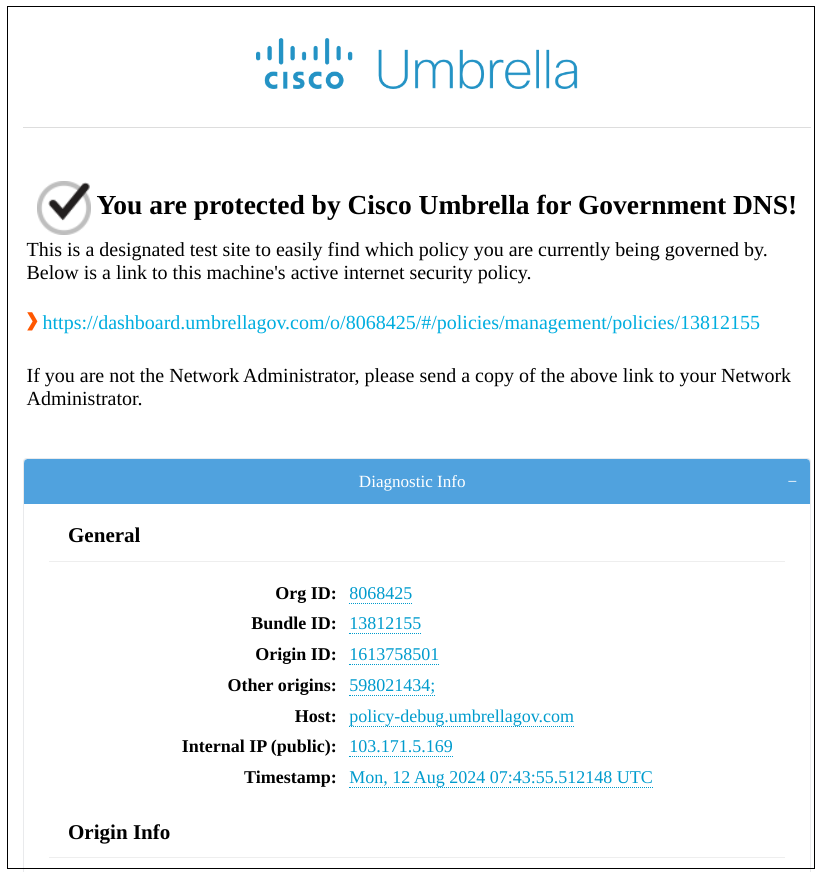
It may take Google up to eight hours to push the Chrome extension to all your Chromebooks. After the client is installed in a Chromebook, allow a few hours for Chromebook traffic to begin appearing in your Umbrella dashboard.
Note
Chromebooks must be connected and logged in.
Configure Managed Guest Session Template
- Log into the Google Admin console.
- Navigate to Devices > Chrome > Settings > Managed guest session settings.
- Filter settings for DNS. The DNS settings are displayed.
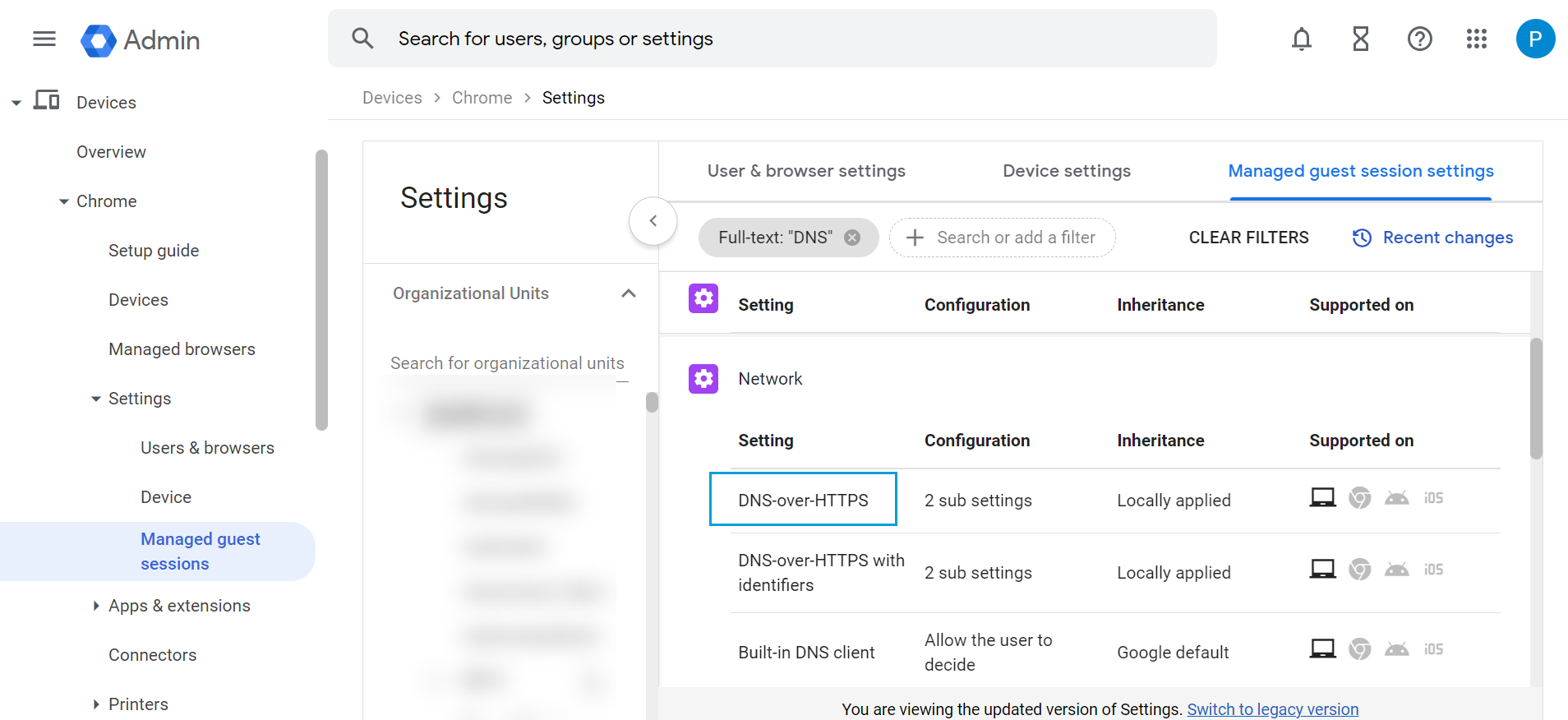
- Select DNS-over-HTTPS and configure it to Enable DNS-over-HTTPS with insecure fallback.
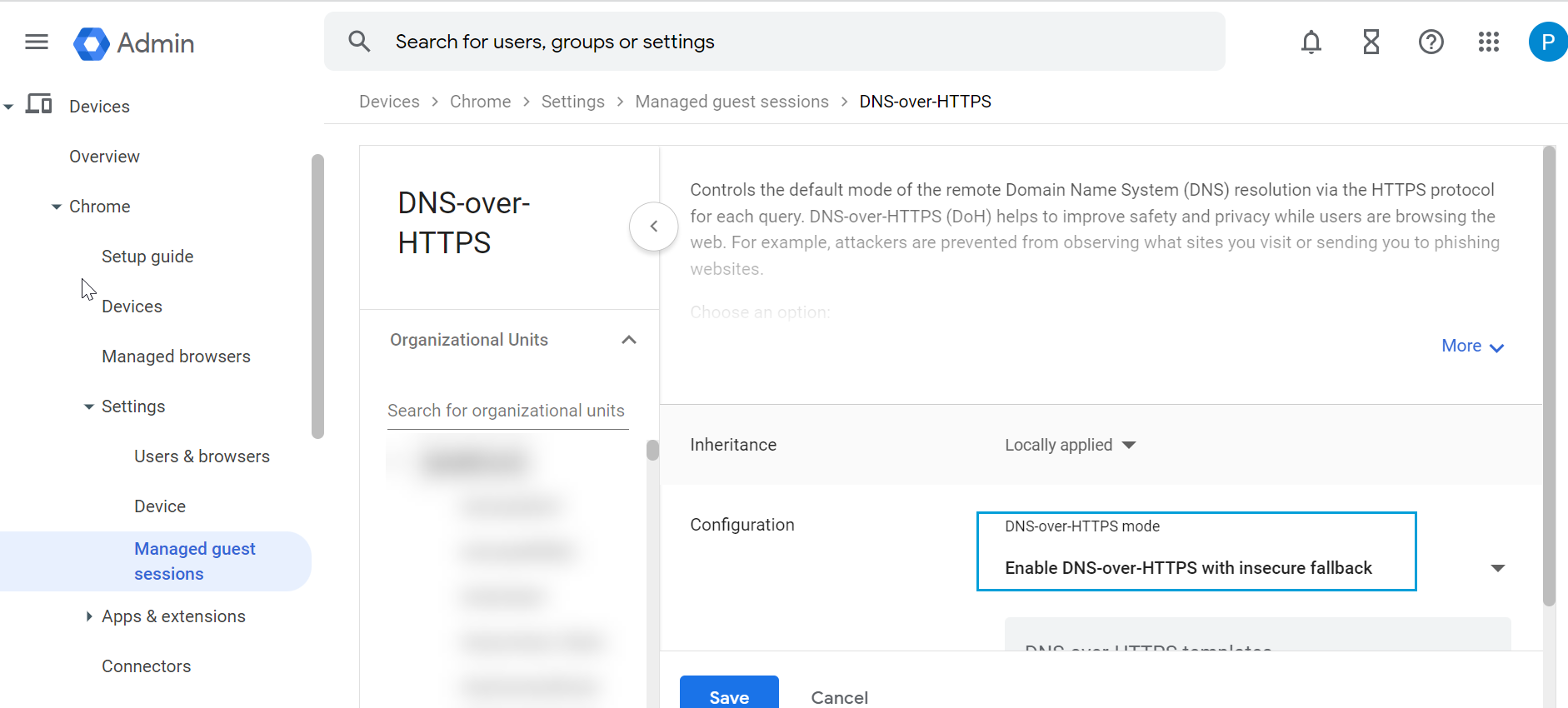
- Return to the Managed guest session settings. Select DNS-over-HTTPS with Identifiers.
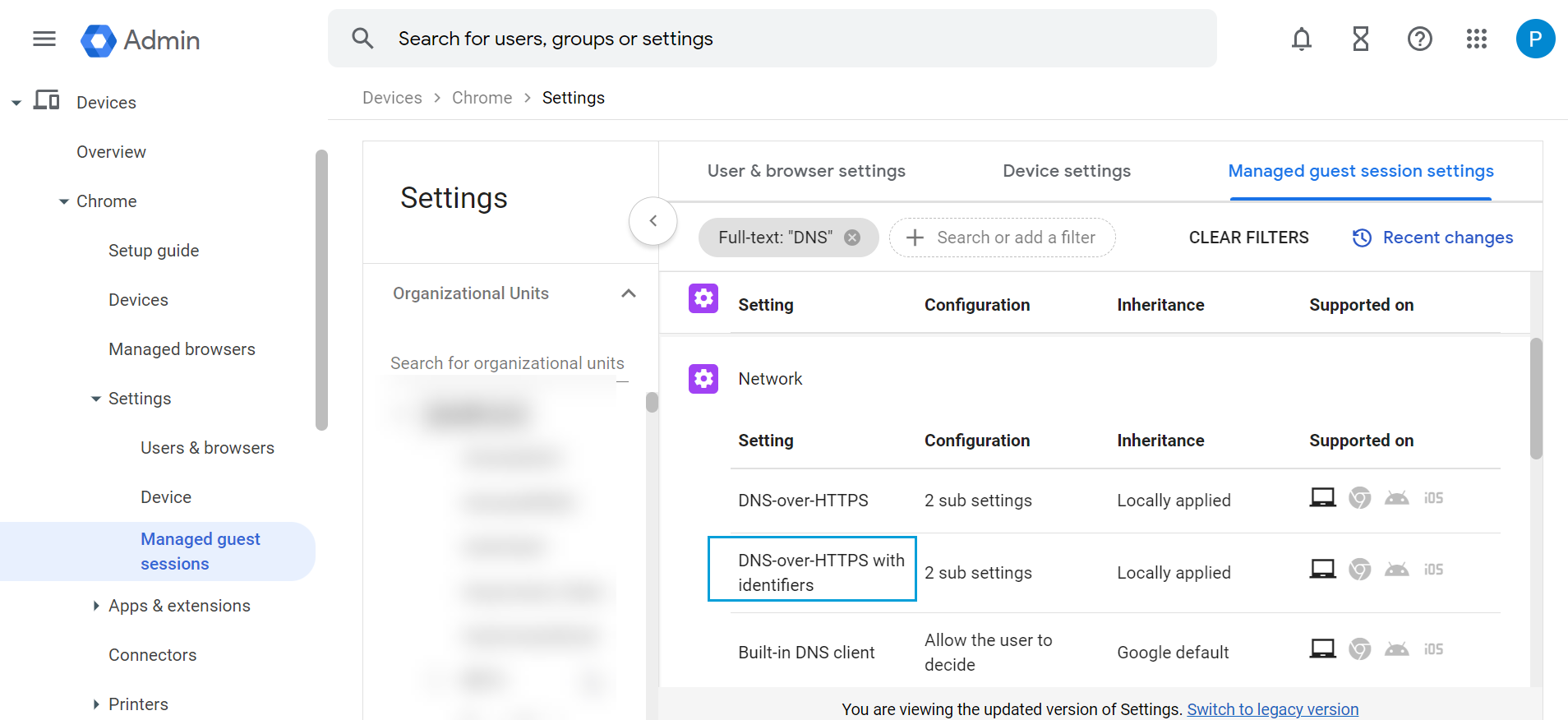
- Enter the URL of the Managed Guest Session DoH template and the Salt value copied from the Umbrella Dashboard. Click Save.
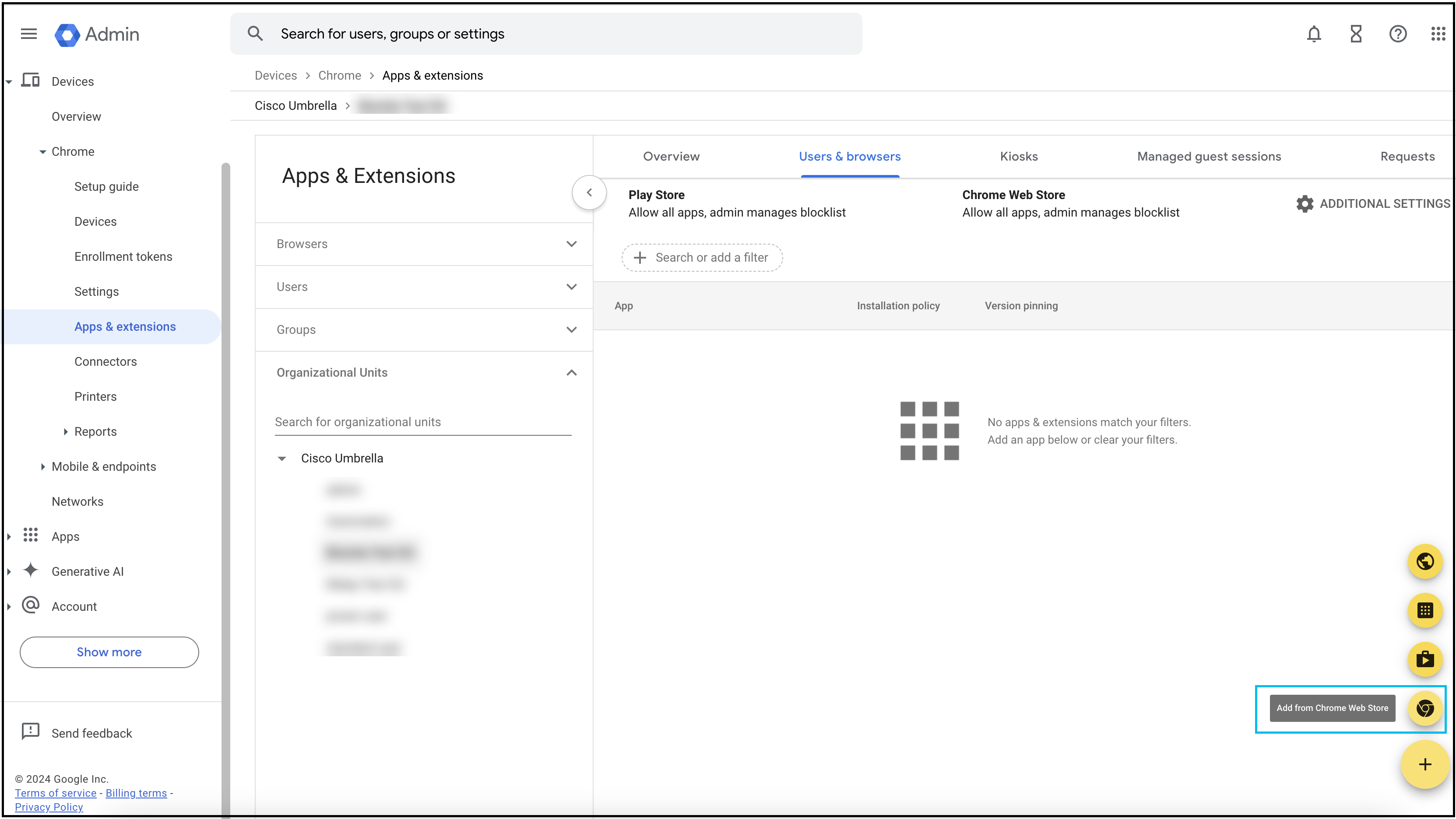
- From Apps & Extensions navigate to Managed Guest Session > Organizational Units.
- Expand Organizational Units and choose the organization into which you want to deploy the Cisco Security for Chromebook client.
- Click the + (Expand) icon and choose Add from Chrome Web Store.
- In the Chrome Web Store, navigate to Extensions and search for the Cisco Security for Chromebook client extension using the ID aiaoiippnjfkanmgamnpphpjffaijicm.
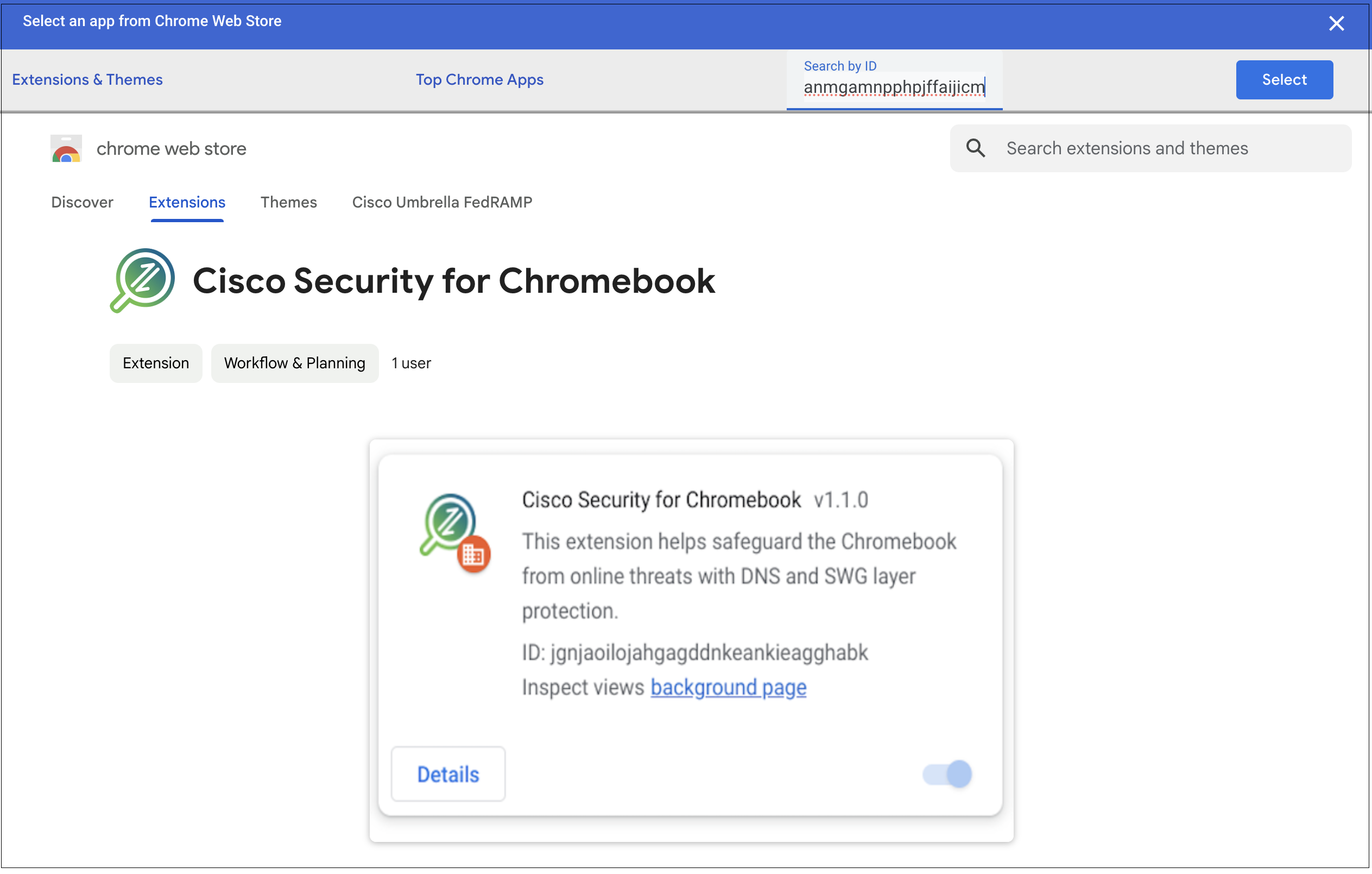
- Click Select. The extension is added to the selected organization unit.
- Copy the JSON file that you downloaded and paste it into the Policy for Extensions section.
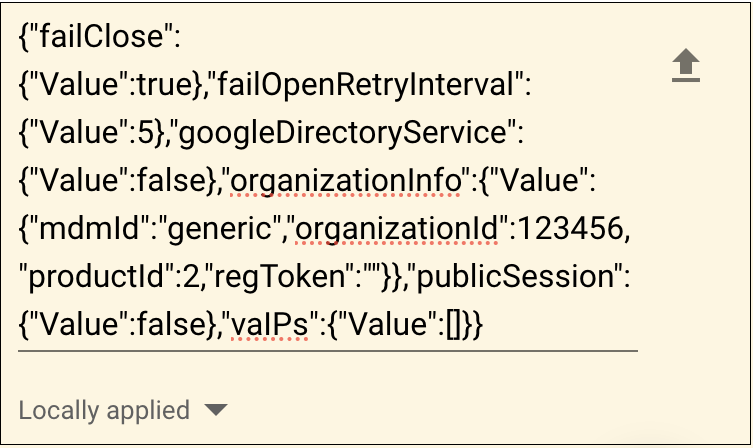
- Choose Force Install and then click Save.
The Cisco Security for Chromebook client extension is installed. Force Install ensures that Chromebook users in the selected Organization Unit cannot remove or disable the extension.
Once the configuration is done and pushed to the device, the user will be prompted with a SAML pop-up window to authenticate based on the integrated IDP. For more information, see SAML Configuration. On successful authentication, the device will be registered and protected by Umbrella. If the user fails to authenticate, the prompt will repeat until correct credentials are provided. The user will need to re-authenticate after the IDP authentication expiry limit is reached.
- Open the URL https://policy-debug.umbrellagov.com and verify if the device is being protected by Umbrella. For DNS customers, the message displayed is “You are protected by Cisco Umbrella DNS!”
It may take Google up to eight hours to push the Chrome extension to all your Chromebooks. After the client is installed in a Chromebook, allow a few hours for Chromebook traffic to begin appearing in your Umbrella dashboard.
Note
Chromebooks must be connected and logged in.
Verification Steps
-
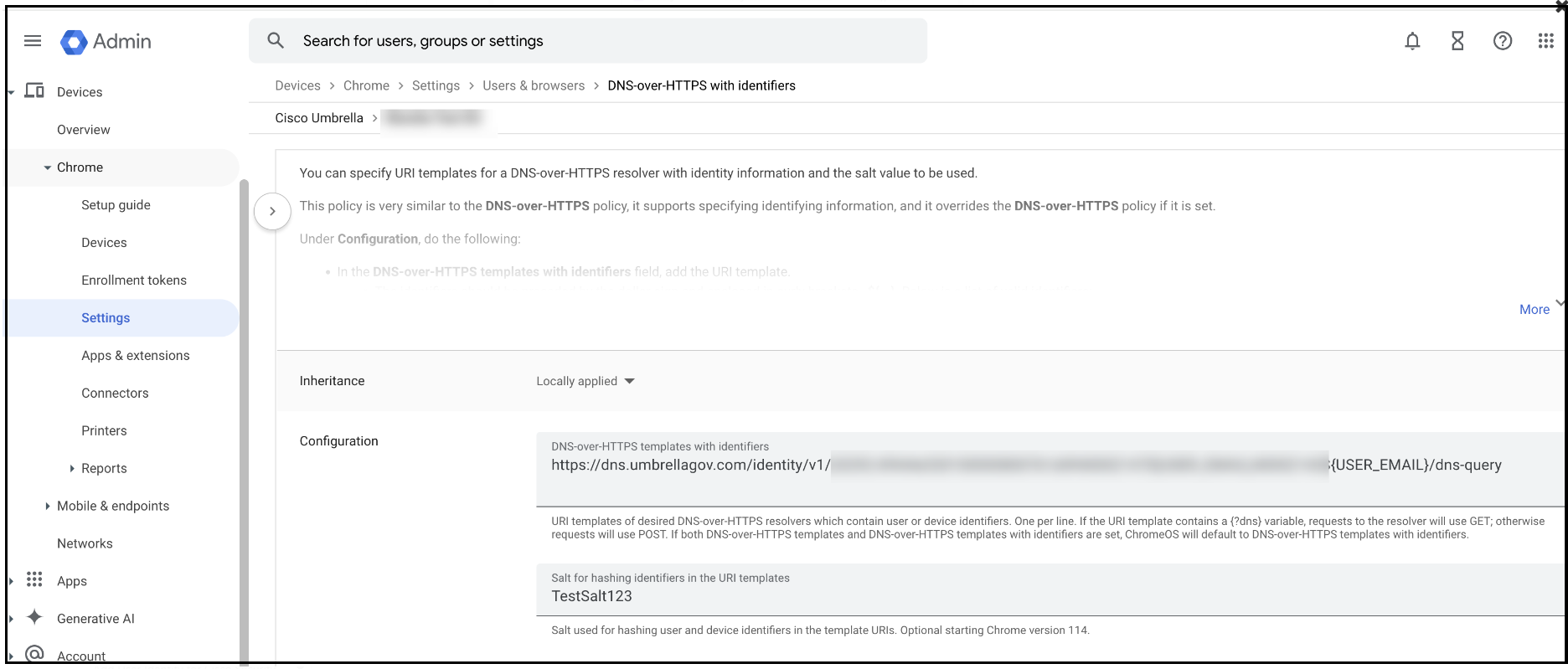
Verify if the DoH Template and Salt configured on Google Admin Console are propagated to the device. For this:
- Ensure that the user is in the same organizational unit as the one in which the salt value and the DoH templates are configured.
- From the Chrome browser on the Chromebook device, go to chrome://policy.
- Search for DNS and check the values of properties: DnsOverHttpsSalt and DnsWithHttpsTemplatesWithIdentifiers.
-
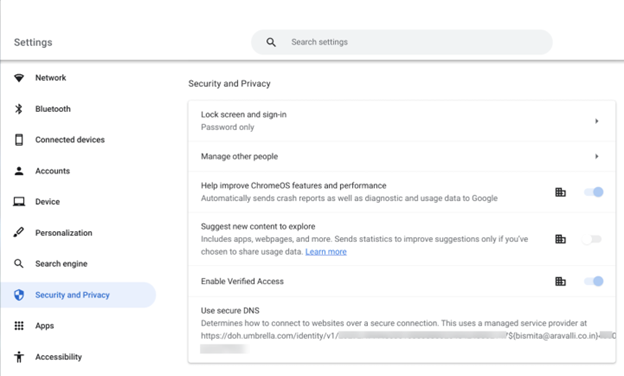
Verify if the DoH Template resolution with the Email id or Serial number is as configured on the DoH Template:
-
Go to Chromebook Setting > Security and Privacy > Use Secure DNS.
- Verify if malicious websites are getting blocked. Go to https://internetbadguys.com and check if it is blocked.
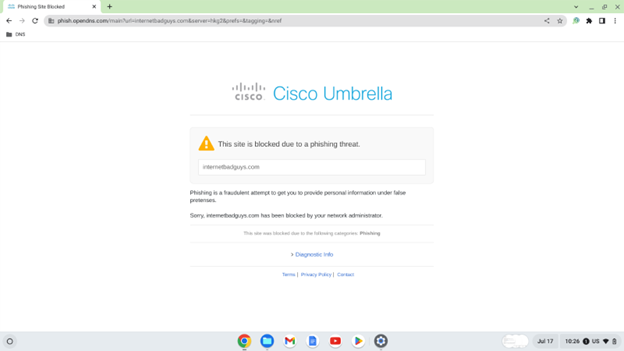
- For Debugging, enable “Always allow built-in developer tools” from Google Admin Console.
- Third-party Web filtering/Web proxy solutions may interfere with SWG proxy setup of the Umbrella Chromebook Client. It is suggested that these solutions be removed before installing Umbrella Chromebook Client.
Integrate Google Workspace Identities> Deploy the Chromebook Client > Bypass Internal Domains from DNS-over-HTTPS (DoH)
Updated 9 months ago
