Deploy Umbrella for Cisco Secure Client
Deploying the Cisco Secure Client can be accomplished in three ways: SecureX Connected Deployment (Recommended), Standard Deployment and VPN head-end-based Deployment. This guide will walk you through all the methods. To start, select the steps for your chosen deployment method.
Table of Contents
Standard Installation
You can download the Cisco Secure Client from the Dashboard and deploy the client using the standard installation.
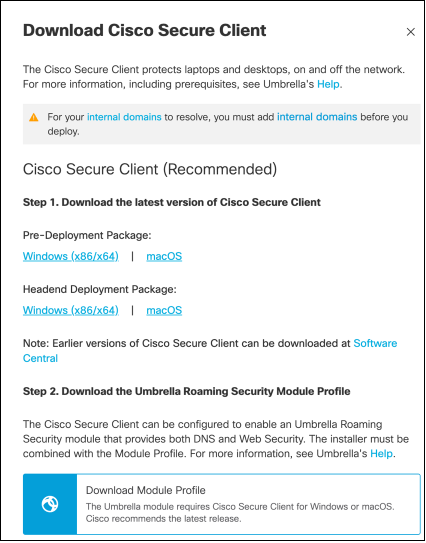
Download
Select and download the Cisco Secure Client deployment packages that meet the operating system requirements of the devices in your organization. To begin, download the prerequisite software:
- Download a copy of the configuration profile from the Umbrella Dashboard.
- Depending on your system, drop or push the file into the following directory:
- Windows: %ProgramData%\Cisco\Cisco Secure Client\Umbrella
- macOS: /opt/cisco/secureclient/umbrella/
The client activates the Umbrella module once installed and OrgInfo.json is present in the Umbrella directory.
Deployment
Standard deployment for Windows consists of manual or mass installing of the client with the module MSI installer or with the wrapping setup EXE installer contained in the client download ZIP file. For macOS, a PKG file is used for installation.
Authentication
Once OrgInfo.json is pushed to the client, it authenticates before registration with Umbrella. A popup displays the IdP authentication window.
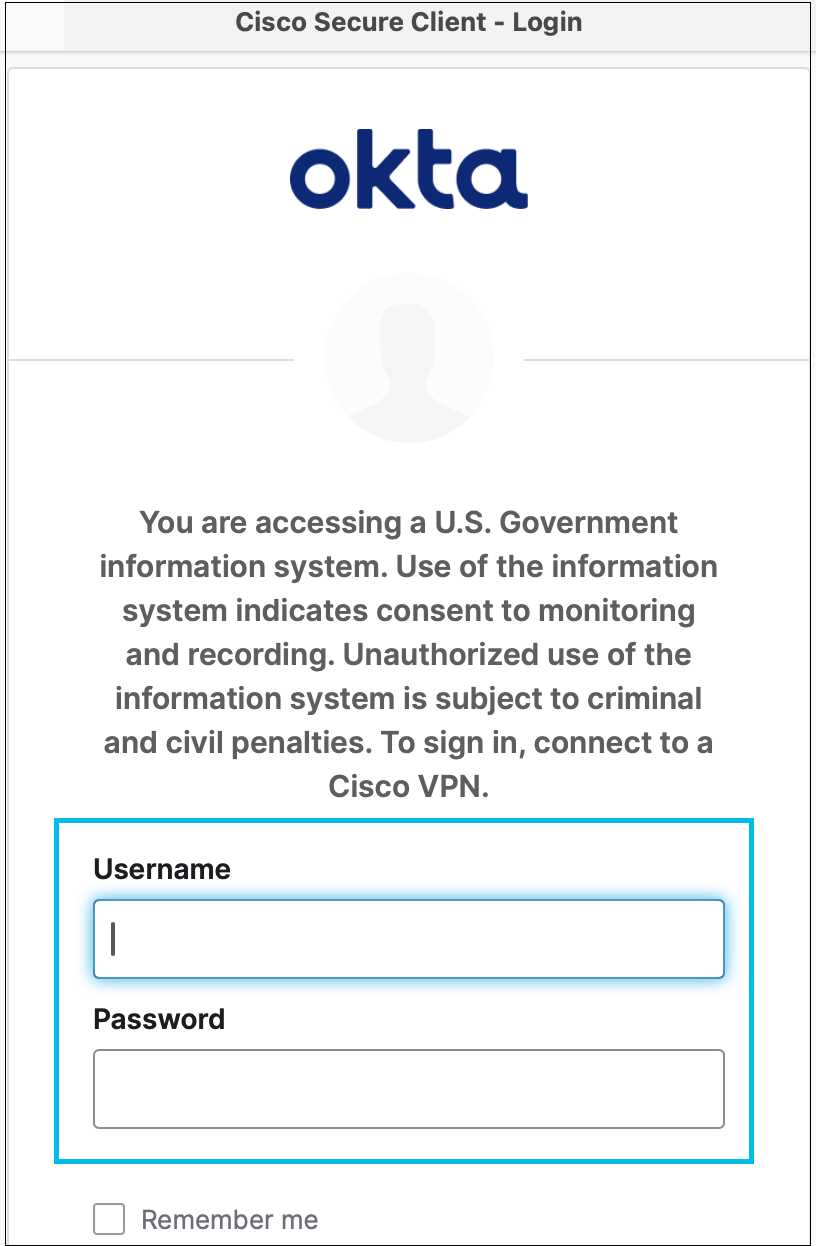
The registration proceeds after authentication. As part of the registration the client obtains a TTL (Time to Live) value that is configured with the IdP. Once the token expires, you will have to reauthenticate. The TTL time interval is specified by the IdP admin.
Note: You could see a blank authentication window, if the IdP is not reachable, or if the root certificate is not properly installed.
Manual Installation (Most Common for Evaluation)
- Initial deployments for evaluation occur when an admin downloads a copy of the Cisco Secure Client (formerly AnyConnect) and manually installs it on the system.
- At install, the client prompts the required modules. For Umbrella-only, check Umbrella and DART, and install. For VPN as well, check Core/VPN, DART, and Umbrella.
Standard Installation (Most Common)
-
Standard deployment consists of manual or mass installing the client with the module MSI installer or with the wrapping setup EXE installer contained in the client download ZIP file. To begin, download the prerequisite software:
-
Download a copy of the Cisco Secure Client from software.cisco.com. Cisco Secure Client is licensed for Umbrella use for all current Umbrella packages but may require linking your contract ID to your Cisco account. For more information, see Standalone Roaming Client vs AnyConnect Roaming Module.
-
Download a copy of the configuration profile from the Umbrella Dashboard. See Quick Start Guide.
-
Depending on your system, drop or push the file into the following directory:
- Windows: %ProgramData%\Cisco\Cisco Secure Client\Umbrella
or - macOS: /opt/cisco/secureclient/umbrella/
- Windows: %ProgramData%\Cisco\Cisco Secure Client\Umbrella
Note:
- If deploying after installing Cisco Secure Client, the folder structure will already be in place.
- If deploying the OrgInfo.json before installing Cisco Secure Client, you will need to create the folder before placing the file.
The client activates the Umbrella module once installed and OrgInfo.json is present in the Umbrella directory.
Important
When you deploy the OrgInfo.json file for the first time, it is copied to the data subdirectory (/umbrella/data), where several other registration files are also created. Therefore, if you need to deploy a replacement OrgInfo.json file, the data subdirectory must be deleted. Alternatively, you can uninstall the Umbrella Roaming Security module (which deletes the data subdirectory) and reinstall it with the new OrgInfo.json file.
The OrgInfo.json has specific information about your Umbrella dashboard instance that lets the Roaming Security module know where to report to and which policies to enforce. If you use another OrgInfo.json file from a different dashboard to install the Roaming Security module, the client computer appears in that dashboard instead.
VPN Head-end Pushed Installation
Cisco Secure Client may also be deployed from a Cisco Secure VPN head end such as an ASA. Head end deployment is not available on Meraki MX devices for Umbrella profiles.
Deploy the Module
To add the Umbrella module to your VPN profile, add “Umbrella” from ASDM or with the following CLI command:
webvpn
anyconnect modules value umbrella
Deploy the Umbrella Profile
After configuring the module installation, the profile must be deployed as well. Please refer to your deployment vector of choice:
ASA CLI
- Upload the OrgInfo.json that you obtained from the Umbrella dashboard to the ASA file system.
- Run the following commands, adjusting the group-policy name as appropriate for your configuration.
Note
The file name on the ASA is case sensitive. If you upload a file named OrgInfo.json, you must maintain the case of the filename.
In the following example, you can configure the default group policy by setting <Group_Policy_Name> to
DfltGrpPolicy.
webvpn
anyconnect profiles orginfo disk0:/OrgInfo.json
group-policy <Group_Policy_Name> attribute
webvpn
anyconnect profiles value orginfo type umbrella
group-policy <Group_Policy_Name> attributes
webvpn
anyconnect modules value umbrella
ASDM GUI
Note
ASDM 7.6.2 is required to configure the Roaming Security module through the GUI.
- Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile.
- Choose Add.
- Give the profile a name.
- Choose the Umbrella Security Roaming Client type from the Profile Usage drop-down list. The OrgInfo.json file populates in the Profile Location field.
- Click Upload and browse to the location of the OrgInfo.json file downloaded from the dashboard.
- Associate it with the DfltGrpPolicy at the Group Policy drop-down list or the policy of your choice. For more information about how to specify the new module name in the group-policy,
see Enable Additional AnyConnect Modules.
ISE
- Upload the OrgInfo.json from the Umbrella dashboard.
- Rename the file OrgInfo.xml.
- Follow the steps in Configure ISE to Deploy AnyConnect.
Before You Begin< Deploy Umbrella for Cisco Secure Client > Meraki Systems Manager (SM) Deployment
Updated 12 months ago
