Enable Trusted Network Detection
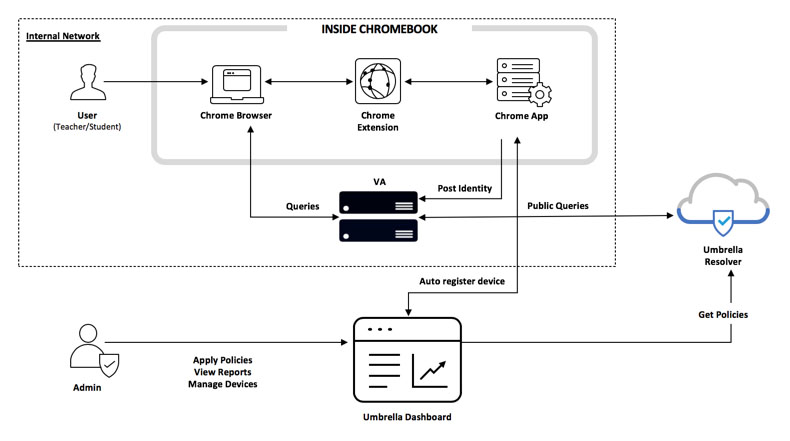
Enabling trusted network detection (TND) allows the Cisco Umbrella Chromebook client to work with Umbrella virtual appliances (VAs). The result is that a network—for example, an on-premise network—protected by VAs can be trusted by the Umbrella Chromebook client. With TND enabled, a Chromebook specific policy can take precedence over other policies by using the Chromebook user's identity.
Table of Contents
How Trusted Network Detection Works
When the Umbrella Chromebook client detects a VA in a network, it sends the Chromebook user's identity to the VA and then deactivates. The VA continues to handle requests from the Chromebook by appending the user's identity for all requests to Umbrella.
When the Umbrella Chromebook client fails to detect a VA, the Umbrella Chromebook client sends requests to Umbrella.
Prerequisites
- Umbrella Chromebook client extension version 1.2.0 or higher
- Umbrella Chromebook client app version 1.2.5 or higher
- Umbrella VA version 2.3.2 or higher
- VAs deployed to your environment. See the Virtual Appliance User Guide.
- The Cisco root certificate must be installed on all Chromebooks within your network. See Install the Cisco Umbrella Root Certificate.
This certificate can be deployed across your Chromebooks using the Google Admin console. See Set up TLS (or SSL) inspection on Chrome devices. - TCP 443 is only accessible from the clients to the VA on networks expected to have the VA configured for DNS. If the VA is accessible to the Chromebook over TCP 443, it will enter the VA state even if the VA is not configured for system level DNS. Failure to do so may result in disabled coverage.
Network Access
| Port and Protocol | Destination | Description |
|---|---|---|
| 443 (TCP) | Virtual Appliances | The Umbrella Chromebook client uses port 443 to communicate with VAs on the network. |
Note: The Umbrella Chromebook client enters trusted network mode when TCP 443 is accessible to the VAs, even if the VAs are not configured as the DNS servers. This can result in the Umbrella Chromebook client being disabled; however, identity is not persisted while not pointing DNS to the VAs. Therefore, you must ensure that the VAs are only accessible over TCP 443 from networks where the VA is configured for DNS. For example, the VAs are not publicly available on TCP 443.
Procedure
To deploy trusted network detection, follow the instructions in Deploy the Umbrella Chromebook Client with the following exception:
- Add the
vaIPsfield to the downloaded Umbrella Chromebook config file.
To use trusted network detection, your configuration file must include:
- Correctly formatted IP values in the
vaIPsfield:- Enclose each IP value in double quotes, separated by a comma.
- All VAs on your network must be added. If a client encounters a VA not configured in its profile, Umbrella can not apply the expected Chromebook-specific policy.
{
"organizationInfo": {
"Value": {
"organizationId":1234567,
"regToken":"GtTYPQfgSzQtGzYUrINmbjgTu5XriDtn"
}
},
"vaIPs": {
"Value": [
"192.168.100.10",
"192.168.100.11"
]
}
}
Add a Chromebook Specific Policy < Enable Trusted Network Detection > Filter Content with Public Session Support
Updated almost 2 years ago
