Chromebook-specific DNS Policy
Add a Chromebook-specific DNS policy to Umbrella and protect all Chromebook devices connected to your network. Once added, place this Chromebook-specific DNS policy at the top of your policies list so that it is evaluated first. This ensures that this Chromebook-specific DNS policy is applied to your Chromebooks before any other DNS policy is evaluated. For more information about adding a DNS policy, see Add a DNS Policy.
Note: To maintain end-user privacy when Chromebooks are connected at remote locations, you can also disable Content Logging and include only security-related events in your reporting.
Table of Contents
Prerequisites
- Cisco Security for Chromebook client must be deployed. For more information, see Deploy the Chromebook Client.
- Cisco Umbrella root certificate must be installed. To avoid certificate errors when accessing an Umbrella block page, you must install the Cisco Umbrella root certificate on all Chromebook devices. See Install the Cisco Umbrella Root Certificate.
- You must have full admin access to the Umbrella dashboard. See Manage User Roles.
Procedure
- Navigate to Policies > Management > All Policies and click Add.
The DNS Policy wizard opens.

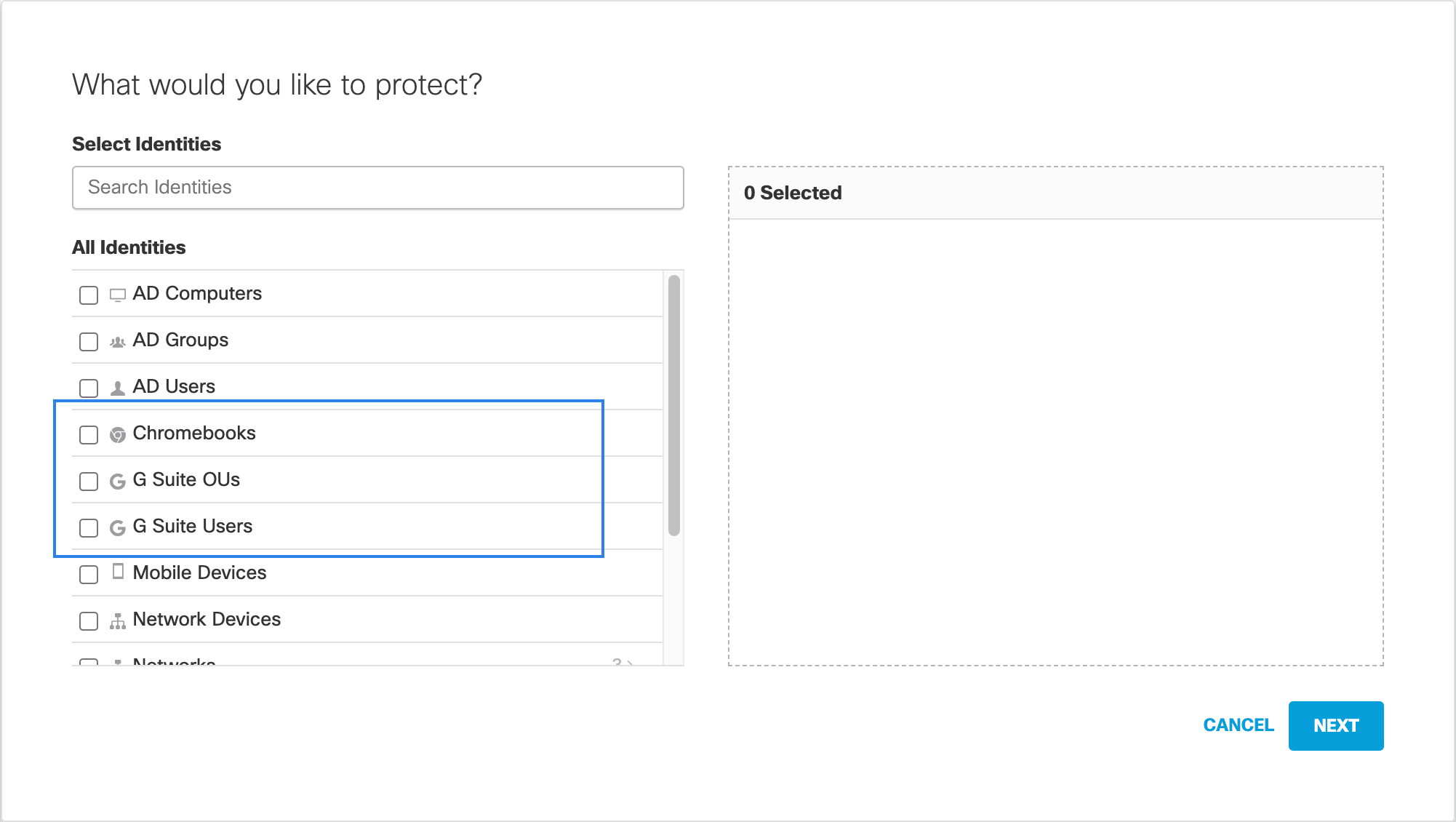
- Select the Policy wizard components you'd like enabled and determine how Umbrella will block threats.
The options you choose here determine the steps of the Policy wizard that become available for configuration and how this policy protects your identities. - Select G Suite OUs, G Suite Users, and Chromebooks identities as required:
- G Suite OUs — To apply a DNS policy to one or more G Suite Organizational Units.
- G Suite Users — To apply a DNS policy to one or more Chromebook users.
- Chromebooks — To apply a DNS policy to one or more Chromebook devices.
- Click Next and continue through the DNS policy wizard until you are prompted to save it. For more information, see Add a DNS Policy.
Note: The Custom block page, Bypass Users, and Bypass Codes features are not supported by the Chromebook client. Currently, the user is allowed to visit a site that should be blocked, and the result is that, in some cases, the site is erroneously shown in Reports as blocked.
- Give your DNS policy a meaningful name and click Save.
Your policy is automatically applied to Chromebooks.
Note: Cisco recommends that you place the Chromebook specific DNS policy at the top of the list of policies.
Protection Status > Chromebook-specific DNS Policy > Chromebook Client FAQs
Updated almost 2 years ago
