Hide Identities with De-identification
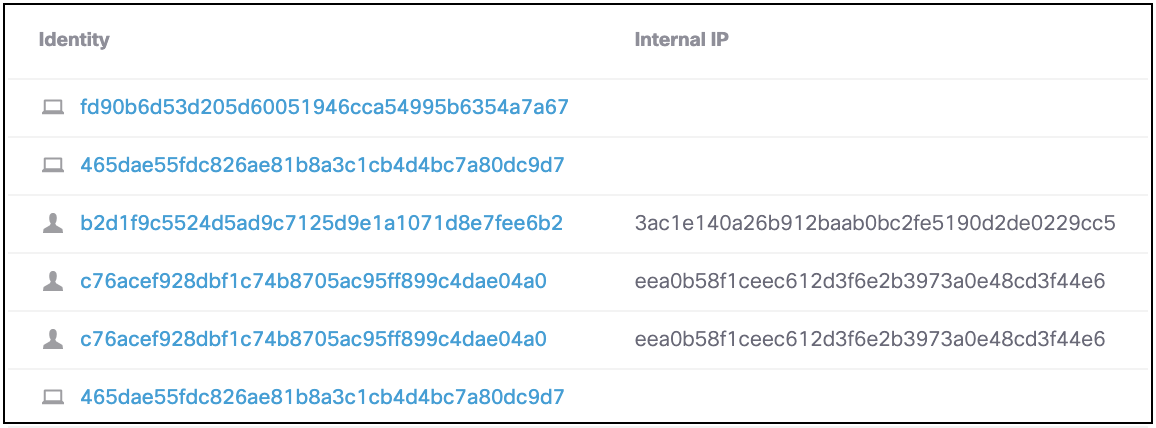
Some regions or organizations require restrictions to hide the identity of users making internet requests. To comply with these restrictions, you can hide identity names when generating a report, by enabling de-identification for a user. When enabled, a hash unique to that identity replaces the identity name.
You cannot enable or disable de-identification on your own account. At least two administrators are required to use this feature in the dashboard and any administrator can turn it on or off for another account. This is as-designed to prevent circumvention.
Table of Contents
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
Identity Types
The following identity types are de-identified:
- AD usernames
- computer/hostnames
- internal IP addresses
- Chromebook identities
- mobile identities
- GSuite users and groups
- SAML-obtained users and groups
- internal IP addresses
Enable De-Identification
- Navigate to Admin > Accounts and click an account name.
Note: You cannot enable de-identification for your own account.

- Under De-identification click Change.
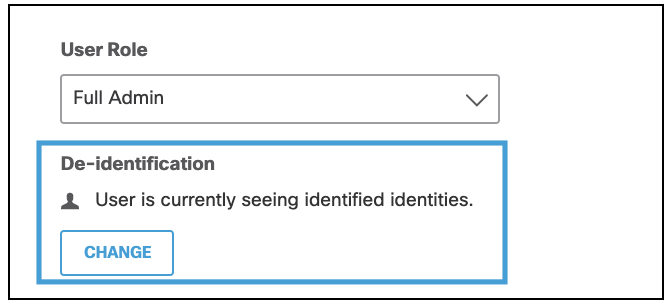
- Click Confirm.
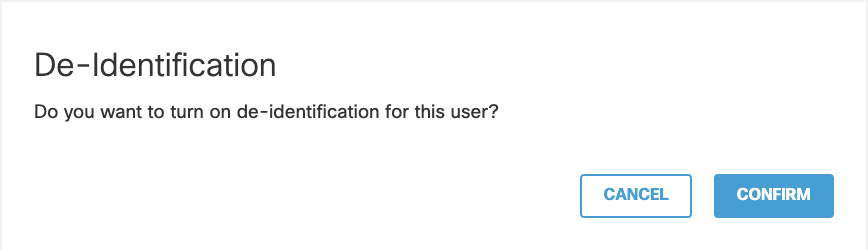
De-identification is enabled and identity names are replaced with a hash.
Disable De-Identification
- Navigate to Admin > Accounts and click an account name.
Note: You cannot enable de-identification for your own account.

- Under De-identification click Change.
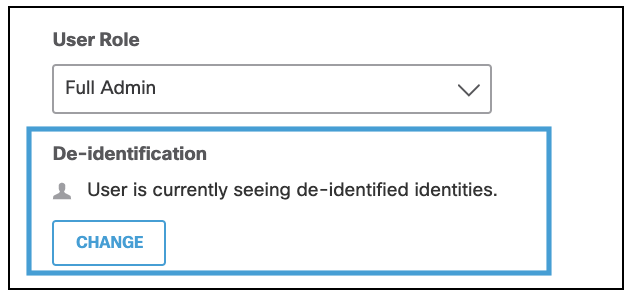
- Click Confirm.
De-identification is disabled and the account can view identity names.
Limitations
Because the purpose of de-identification is to remove the visibility of the identity names for the user, de-identification includes the following are limitations:
- Scheduling and exporting reports is not available.
- The Application Discovery report is not available.
- You cannot search by an active directory username, roaming computer name, or internal IP name.
However, you can click the hash name to view the identity's details or the Top Identities report. - There is no access to API key management and creation.
- There is no access to S3 Log Management (both self-managed and Cisco-managed).
Change Account Settings< Hide Identities with De-identification > Manage User Roles
Updated almost 2 years ago
