Security Activity Report
The Security Activity report highlights security events generated by your organization's identities visiting destinations flagged—but not necessarily blocked—by Umbrella security researchers as a threat. This includes security events filtered through the Intelligent Proxy and File Inspection.
Activities captured by this report might include attempts to access sites hosting malware or phishing sites, botnet activity on infected machines on your local network, attempts to download malicious files—or more. To find out about each of the individual activities and categories you can report on, see Manage Security Settings.
Table of Contents
- View Activity and Details by Filters
- View Activity and Details by Event Type or Security Category
- View an Event's Details
- Search for Security Activity
Security Events in Umbrella Packages
Not all features described here are available to all Umbrella packages. For example, Cisco AMP and Antivirus events are not available to all packages. If you encounter a feature described here that you do not have access to, contact your sales representative for more information about your current package. See also, Cisco Umbrella Packages.
View Activity and Details by Filters
The Security Activity report enables discoverability to threats by showing traffic patterns, which you can also group by event type.
- Navigate to Reporting > Core Reports > Security Activity.
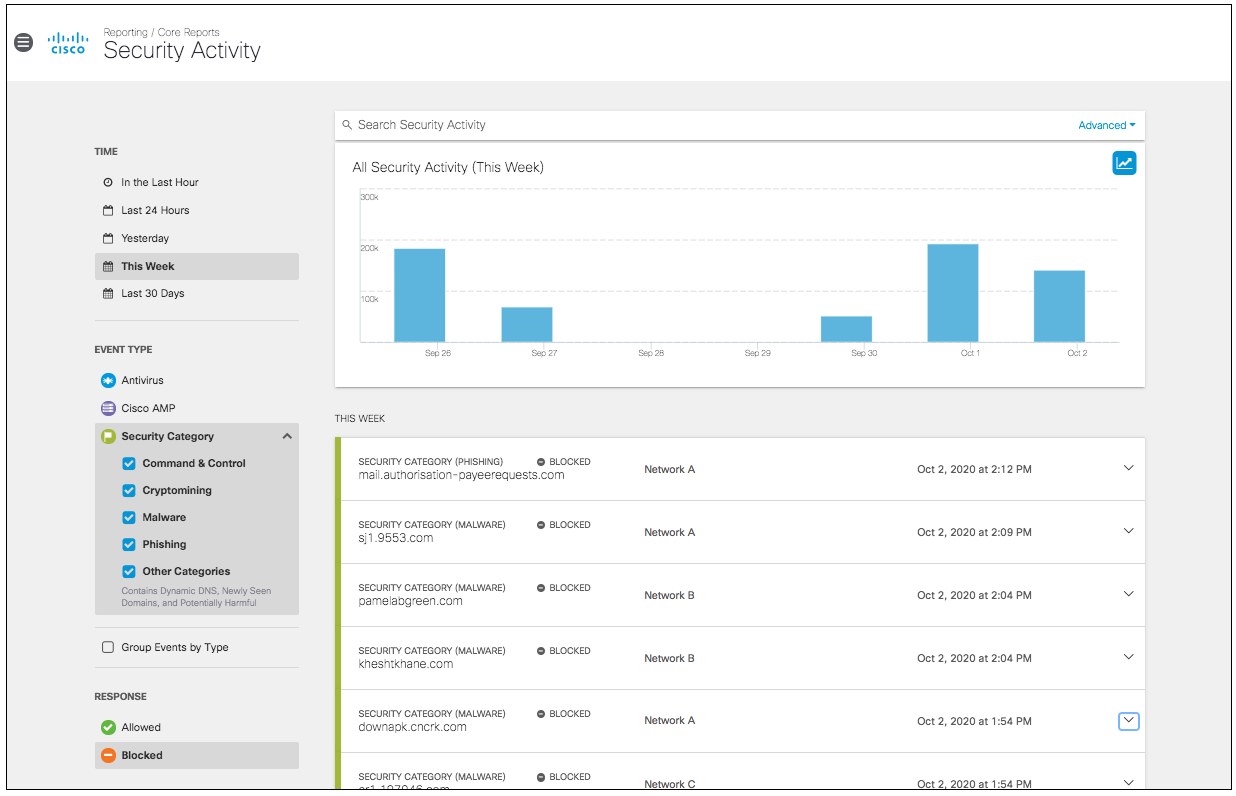
- Choose which security event types and/or categories you want to view in the report. By default, all events and categories are selected to display activity for all event types.
- Antivirus—Lists events that the Intelligent Proxy has filtered through a virus scan.
- Cisco AMP—Lists events that the Intelligent Proxy has run through Cisco Advanced Malware Protection (AMP).
- Security Category—Lists events allowed or blocked against selected security categories: Command and Control, Cryptomining, Malware, Phishing, and Other Categories (Contains Dynamic DNS, Newly Seen Domains, and Potentially Harmful categories).
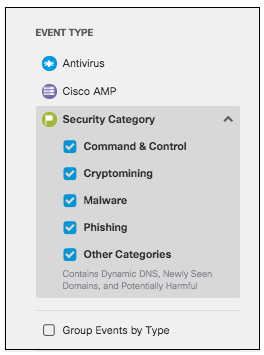
- Choose a time period of events to view. You can generate a report to document activities for the last hour, the last 24 hours, the previous calendar day (yesterday), the last seven days, and the last month.
Timezones
Most, if not all, Umbrella reports are highly time dependent. The time is UTC by default, but can be changed to a different timezone on a per-user basis. Navigate to Settings > Accounts and update your account's time setting.
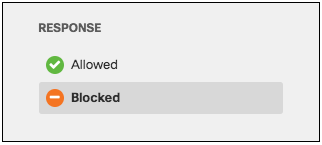
- Choose whether you want to populate all types of requests, only Blocked requests, or only Allowed requests.
Antivirus and Cisco AMP Events
If you select Antivirus or Cisco AMP as the Event Type, you cannot select Response > Allowed. Umbrella cannot allow viruses to pass through the system. These will always be blocked.
Once all filters have been selected, the activity graph and event details will reflect the chosen filters. The graph will display activities for the events selected during the selected time period. The event details cards will stack from most recent to oldest.
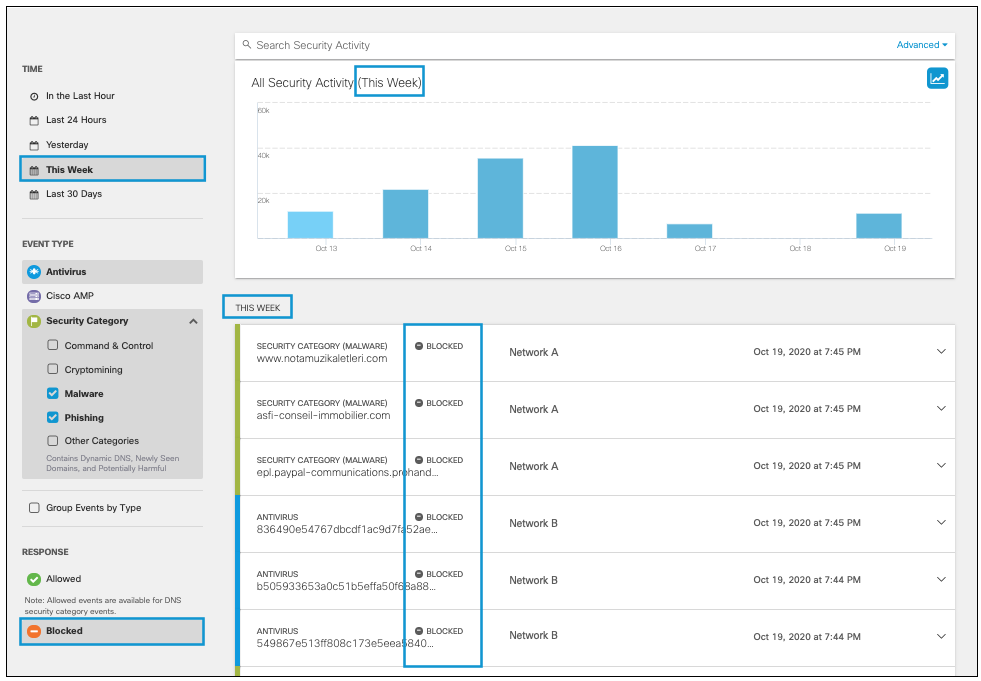
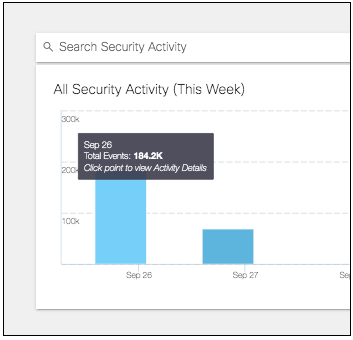
Hovering on a bar on the graph shows details for that time period (the hour or day). Clicking on the details redirects you to the Activity Search report where you can view further details for that time period filtered by Response (if only one is selected) and the security categories selected.
View Activity and Details by Event Type or Security Category
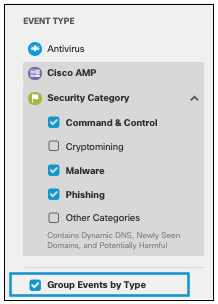
If you want to view data for individual event types or security categories in your environment to see which categories may pose more risk and at what times depending on trends, use the Group Events by Type feature.
- Navigate to Reporting > Core Reports > Security Activity.
- Choose a time period of events to view. You can generate a report to document activities for the last hour, the last 24 hours, the previous calendar day (yesterday), the last seven days, and the last month.
- Choose whether you want to populate all types of requests, only Blocked requests, or only Allowed requests.
- Choose which security event types or categories you want to view in the report. By default, all events and categories are selected to display activity for all event types.
- Check Group Events by Type.
The activity graph updates to show each selected event type so you can compare activities for each type of security risk. You can click on the event type on the graph or in the filter to view or hide the events in the graph.
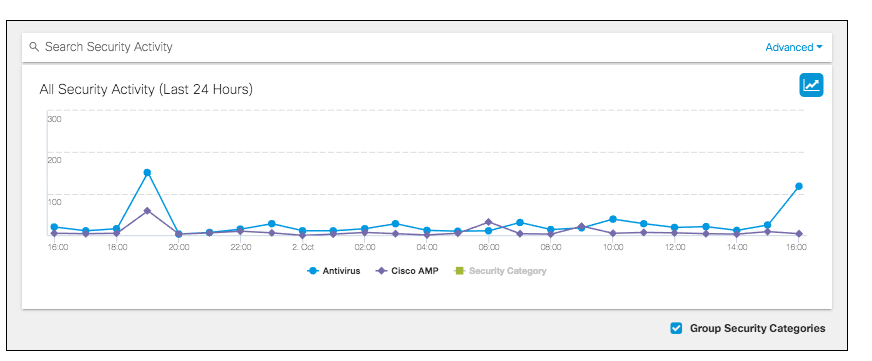
Grouping security categories also reorganizes the events' details cards by event type. By viewing event details by event type or category you can see which categories were more active and perhaps causing more risk to the environment.
Group Security Categories
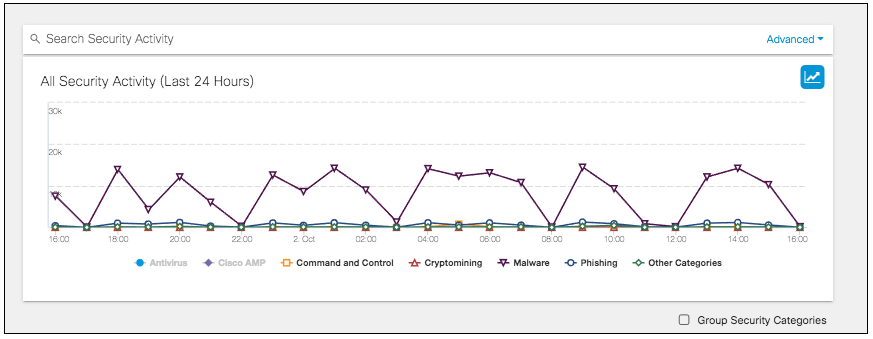
When Group Security Categories is unchecked, the selected security categories are shown individually on the Activity graph. This enables you to view which categories had more activity within the given time frame or where spikes in some categories occurred. Clicking the category name on the graph or in the Security Categories filter will show or hide that category's events on the graph.
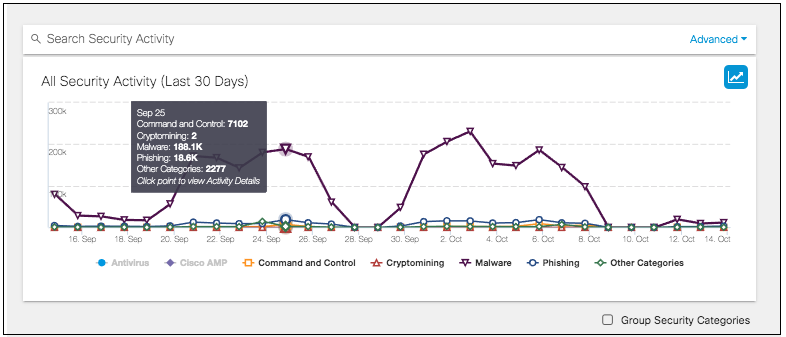
Rolling over a point on the line graph provides a summary of the security events at that time by the categories selected. Clicking the details redirects you to the Activity Search report where you can further view the activity's details.
View an Event's Details
- Navigate to Reporting > Core Reports > Security Activity.
- Choose a time period of events to view. You can generate a report to document activities for the last hour, the last 24 hours, the previous calendar day (yesterday), the last seven days, and the last month.
- Choose whether you want to populate all types of requests, only Blocked requests, or only Allowed requests.
- Choose which security event types and/or categories you want to view in the report. By default, all events and categories are selected to display activity for all event types.
The list of events' details is stacked as cards and sorted by event type (if Group Security Categories is enabled).
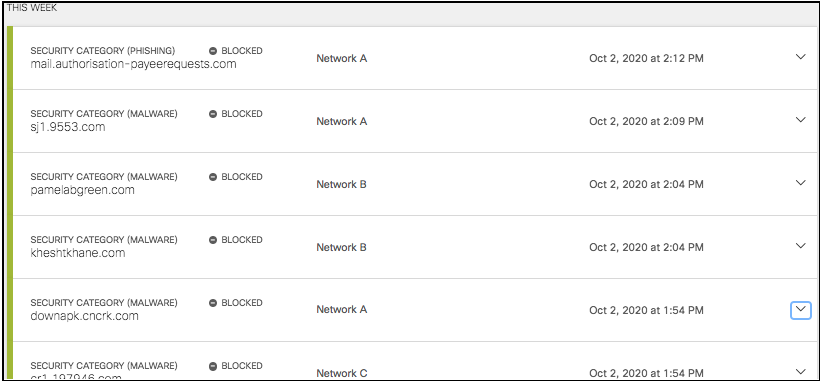
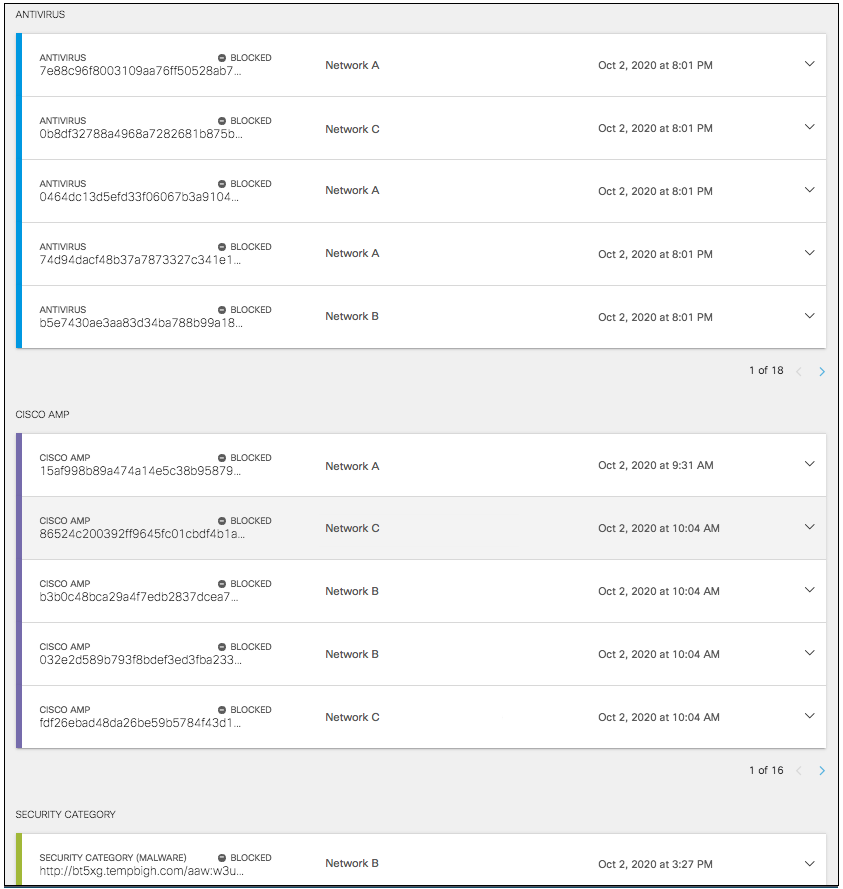
- Click an event to view its details. Each security activity card groups an event by destination and lists the details of the event including date & time, destination, identity. and the event's result (Blocked or Allowed).
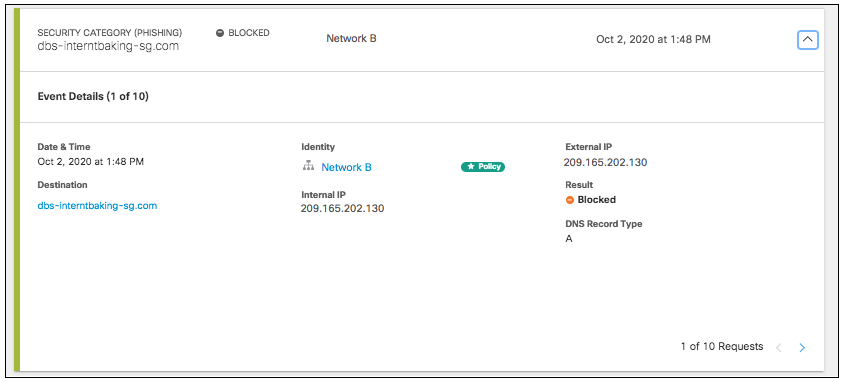
Details differ slightly between event type, but all list the destination and identity from which you can click through to the Destination Details and Identity Details.
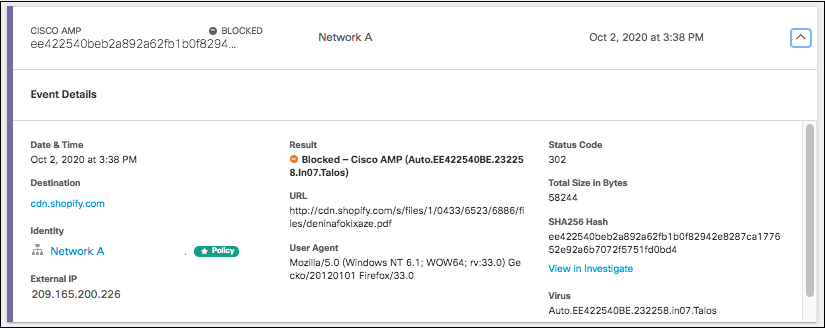
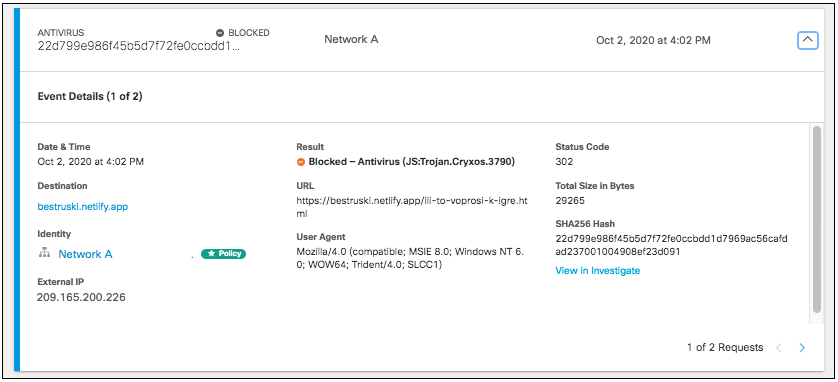
Details for AMP and Antivirus events will also include the SHA256 Hash and a link to view further details in Investigate if applicable.
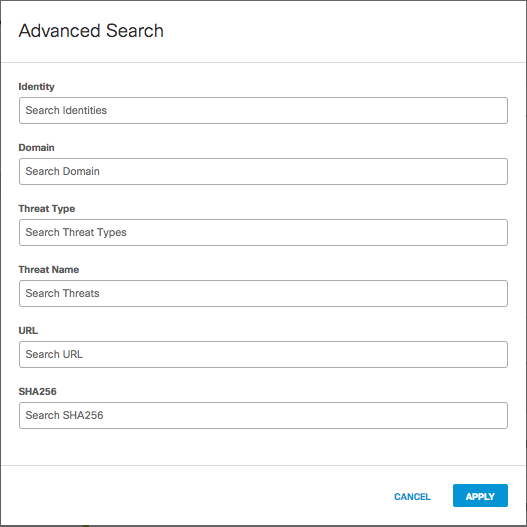
Search for Security Activity
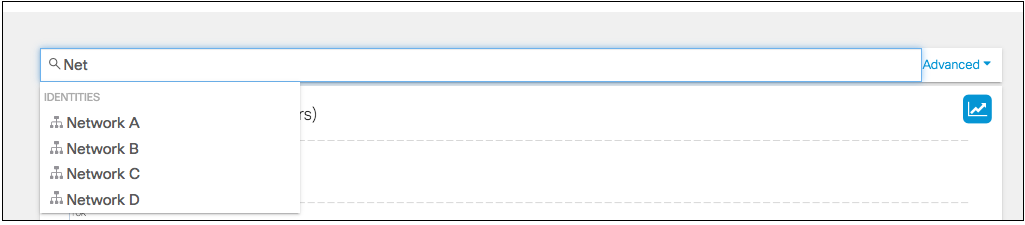
If you're interested in the security activities for a specific identity, use the search feature to filter the Activity chart and event details by identity.
- Navigate to Reporting > Core Reports > Security Activity.
- Type the identity's name in the search bar at the top of the page and press Enter. You can only filter by one identity at a time.
Advanced Search
To search security activities by more specific fields other than identity, such as domain, URL, or threat type, use the Advanced Search feature.
- Click Advanced to the right of the search bar.
- Enter the fields of your search and then click Apply. You don't have to enter information for each search field, but remember that the more information you can provide the more successful your search will be.
Overview Report < Security Activity Report > Activity Search Report
Updated over 1 year ago
