File Inspection Reports
A file that's been inspected and blocked appears in your security logs like any other network event that passes through Umbrella. Both the activity search and the security activity report show file inspection events, but greater detail is found in the security activity report.
Files that were inspected and allowed through because they are safe to appear as allowed events in the activity search report without any information about scan results because there is nothing to report.
In the earlier test with eicar.com, if the test worked as expected you should have a result in your security activity report for the identity that matched when doing a test. This result can be seen in one of two ways.
Table of Contents
Security Activity Report for File Inspection
- Navigate to Reporting > Core Reports > Security Activity and using the built-in filters, search for the threat name, which in this example is "EICAR."
- Click Advanced Search and filter for threat, then type 'eicar':
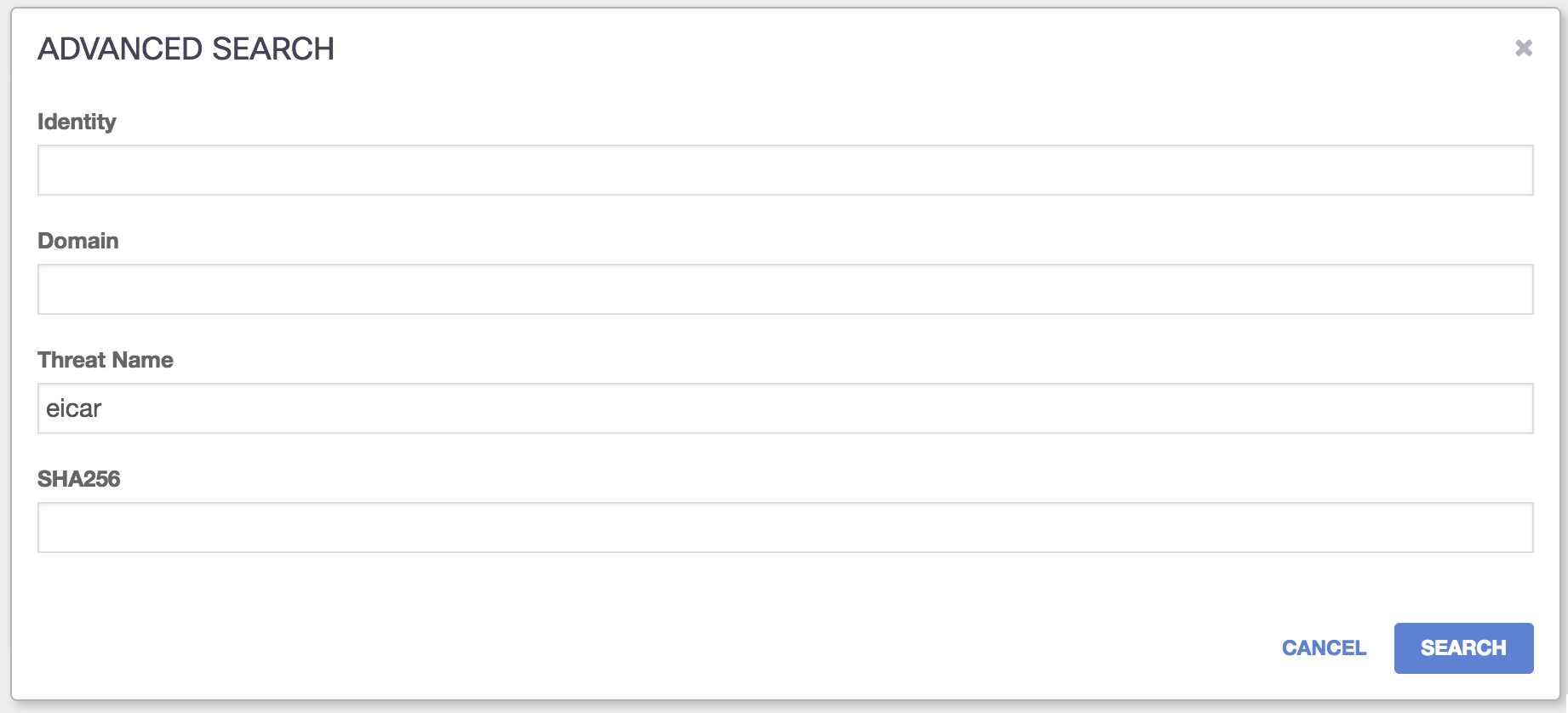
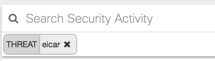
The result will appear compressed in a card.

Click the card to expand it and review data. Because every sample of malware is different, each result will vary based on the malware, the identity triggered and which engine detected it as malicious, but the majority of these fields are consistent between various blocks of files that have been inspected.
The SHA-256 hash is especially helpful in cross-referencing between other security data platforms, or even VirusTotal.
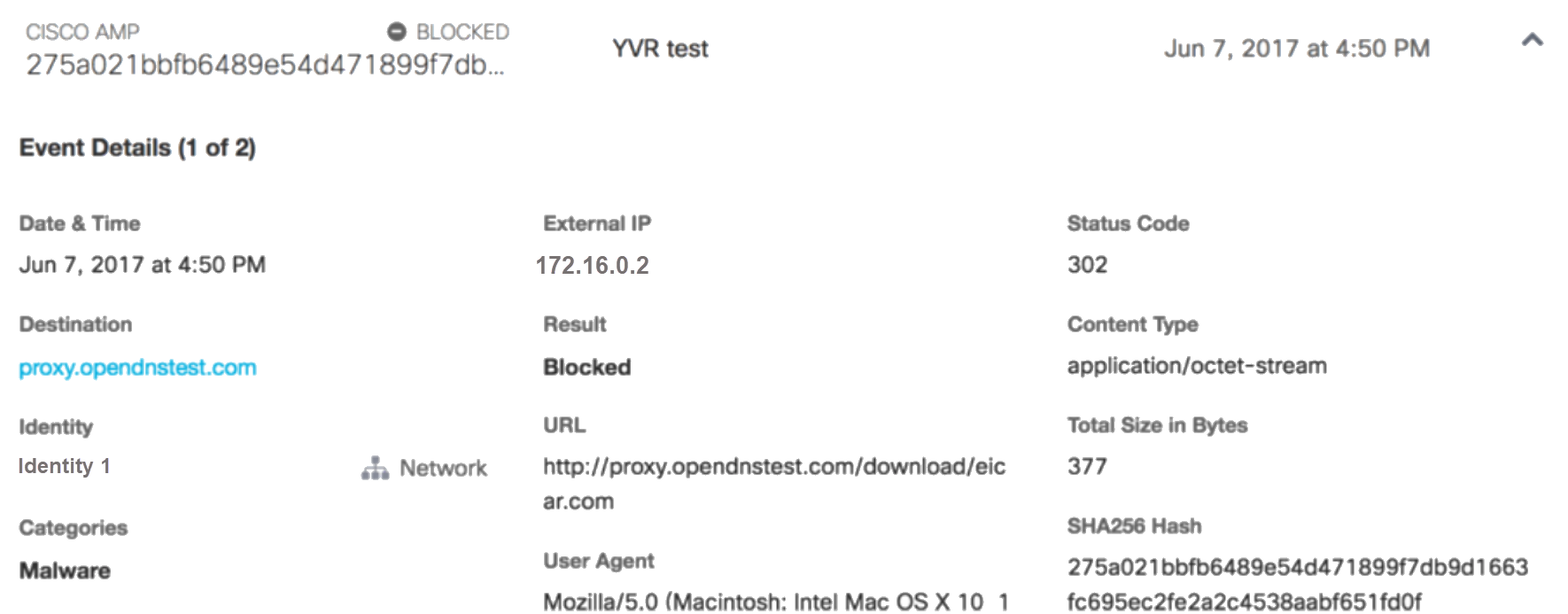
Note: The eicar test virus is scanned by both the antivirus engine and the Cisco AMP engine and detected by both. All files are scanned by both engines and can be detected by both, one or neither. If a sample is detected by both engines, the Cisco AMP detection takes precedence in the reports.
| Field | Value |
|---|---|
| Destination | which domain or IP hosted the suspicious file |
| URL | the URL at which the suspicious file was found at, if available. Usually the same domain as the destination. |
| Date & Time | when the suspicious file was downloaded by the user and scanned |
| Categories | which security categories matched against this event. It is possible for a file to be malicious or suspicious as per the antivirus scanner and Cisco AMP but not be categorized. |
| Result | either blocked or allowed |
| User Agent | the user agent of the browser with which the request was made (http://www.useragentstring.com/pages/useragentstring.php?typ=Browser) |
| Content Type | the MIME type of the data stream (https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/MIME_types) |
| SHA-256 Hash | checksum of the file, if available. Typically for Cisco AMP; this is also included in the summary. |
| Status code | the HTTP code returned from the query (typically 300 or 400) |
| Virus | the name found by the antivirus scanner, where applicable |
| Referrer | the referrer URL where available/applicable |
Security Activity Report for Activity Search
The Activity Search shows files that were allowed through and files that were blocked. Any page on any website could count as a file—files likes .HTML or .CSS are common. In the earlier test to download the eicar.com test file from proxy.opendnstest.com, other page elements were downloaded but allowed.
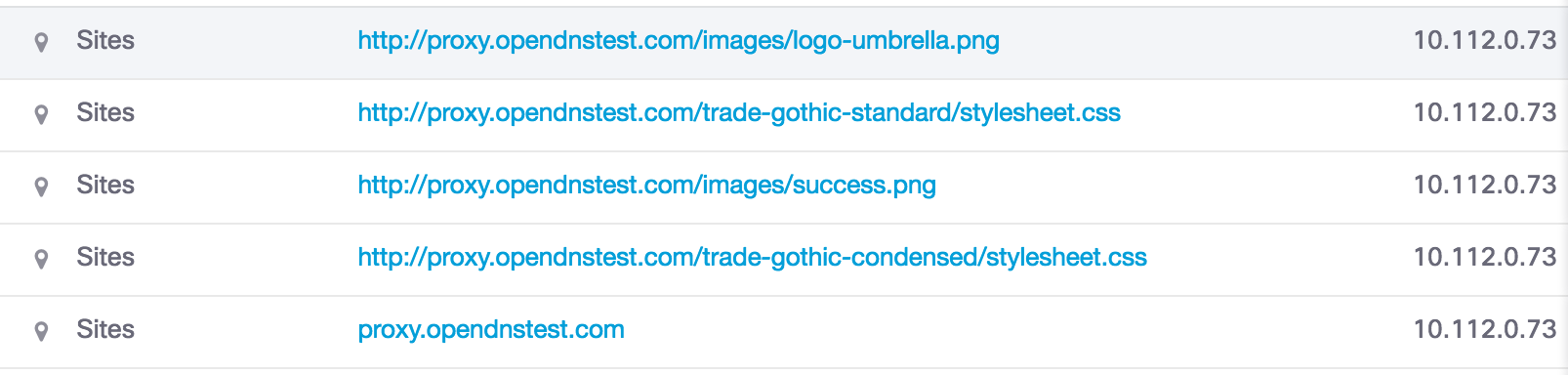
On the far right-hand side, the ellipsis icon can be expanded for more information. In this instance, the file was allowed.
Click See Full Details to view details.
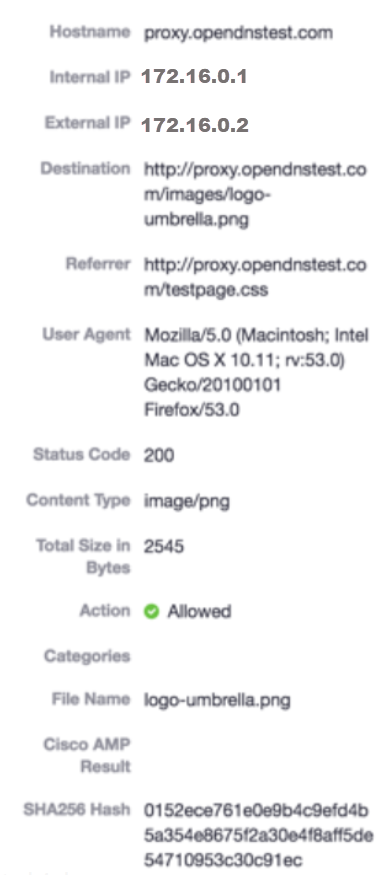
The results for Cisco AMP are blank, as the file was allowed.
You can also use the filters for the columns in the activity search to show the 'file name' and make it more apparent. First, select "Columns" and expose the 'File Name' which is hidden by default.
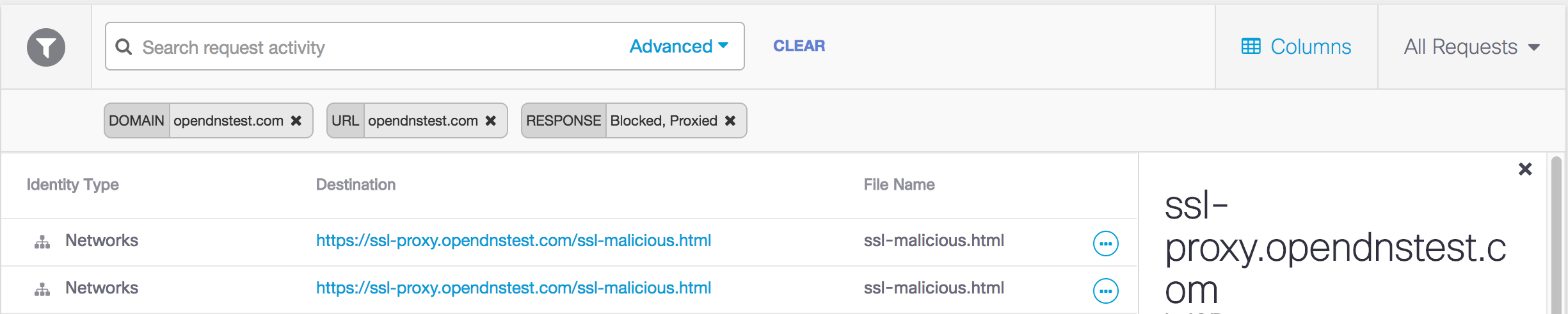
Run the report for the last 24 hours and you'll see the results, including the file name that was proxied.
Troubleshooting < File Inspection Reports > Manage the Cisco Umbrella Root Certificate
Updated 3 months ago
