About the Sample View in Investigate
The Investigate Sample view displays the threat information obtained from a file hash or checksum. You can search for a domain, IP, or URL related to security threats and obtain information about file checksums, threat scores, metadata, and antivirus results.
The Investigate Sample View may include data collected within the last two years by Cisco Secure Malware Analytics. In addition, you can use the Investigate Sample View to analyze a list of checksums gathered from a third-party data feed or in-house security information and event management (SIEM) system. To learn more about Umbrella Investigate, watch New Malware Analysis Data in Umbrella Investigate.
Note: Part of the Investigate Sample View functionality is only available with both Umbrella Investigate and Cisco Secure Malware Analytics subscriptions. For more information, contact Umbrella Support. If you would like to add Cisco Secure Malware Analytics to your existing license, contact your account representative.
Table of Contents
- Prerequisites
- Get Started With Sample View
- Sample View Details
- Components of a Threat Sample
- Behavioral Indicators
- Network Connections
- Associated Samples
- Associated Artifacts (Secure Malware Analytics Integration)
Prerequisites
- A minimum of Investigate Only access to the Umbrella dashboard. See Manage the Investigate Only User Role.
Get Started With Sample View
To get started, enter a checksum or file hash in the Investigate Smart Search, or pivot to the Sample view from the Domain or IP Address view.
Note: Investigate Sample View does not contain all data collected by Cisco Secure Malware Analytics. Some of the data collected does not match the criteria that Umbrella Investigate uses to detects security incidents.
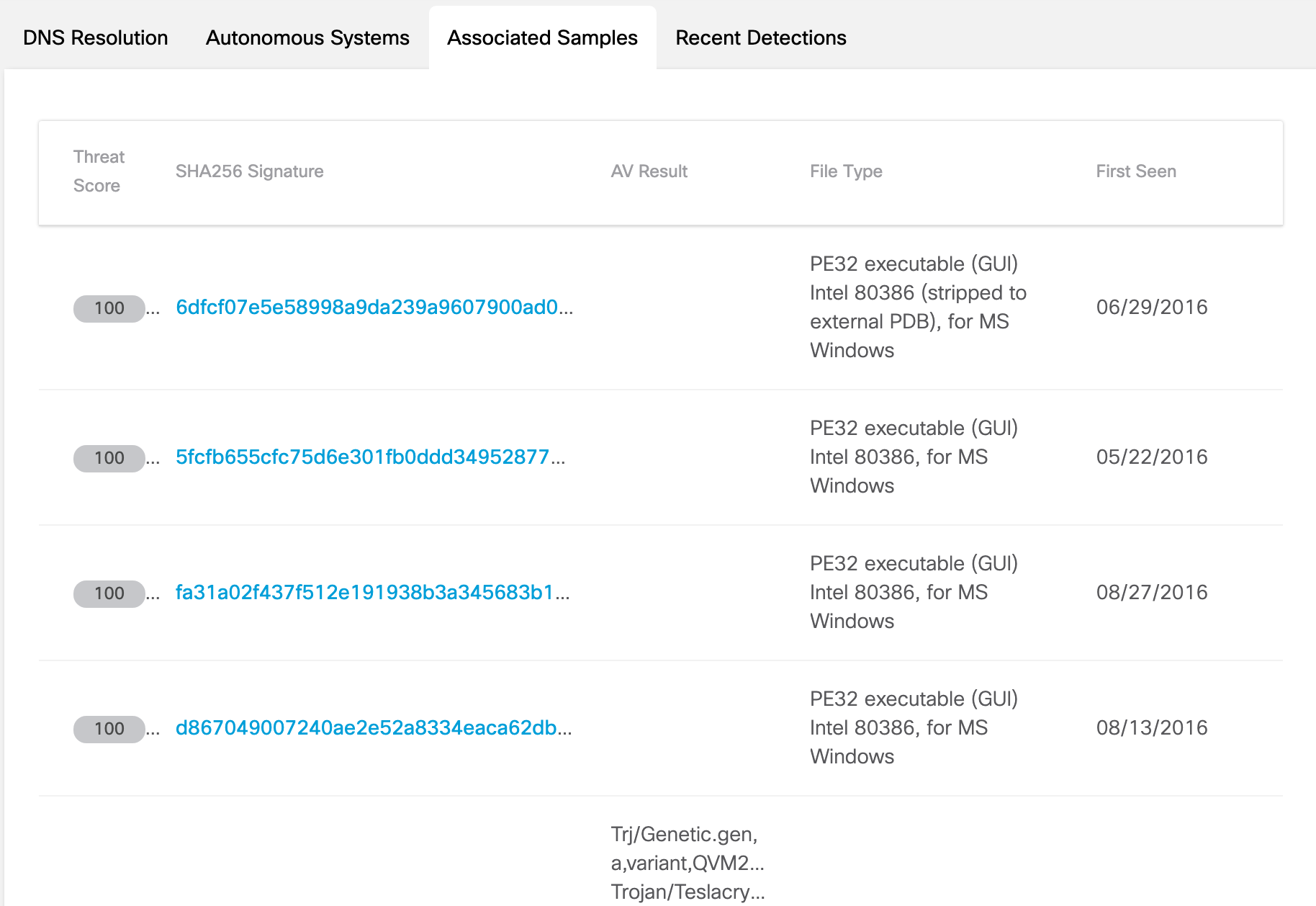
If you begin in the Domain or IP Address view, navigate to the Associated Samples tab. Click the link to a sample to display the Sample view.
Sample View Details
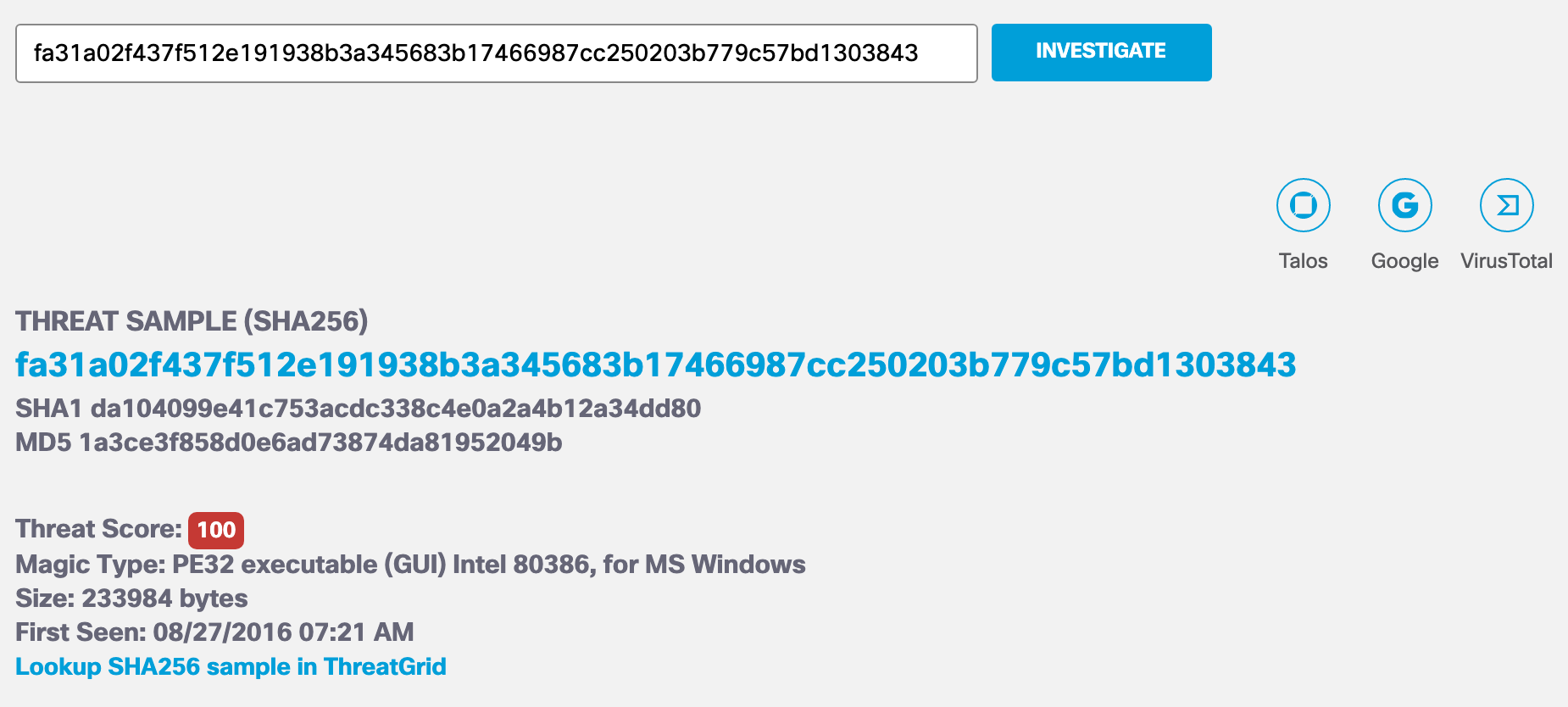
The first part of the Sample View displays information about the checksum.
Components of a Threat Sample
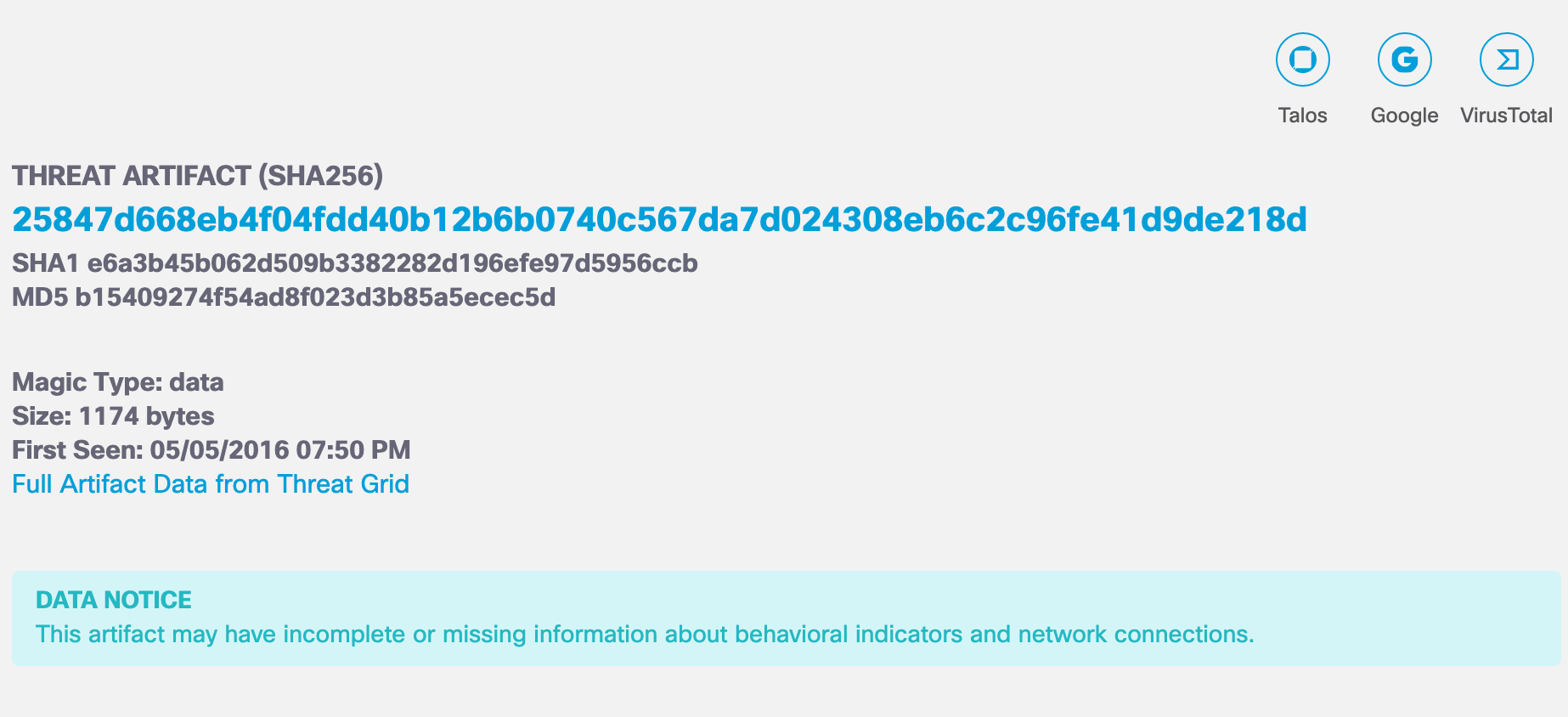
- SHA-256, SHA-1 and MD5 checksums of the sample—The hash files or checksums which help to cross-reference samples against VirusTotal and similar databases.
- Magic Type—A file type based on established file format types that allow files to be associated by the operating system and executed or loaded into memory.
- Threat Score—The score given to a particular sample based on the analysis performed by Cisco Secure Malware Analytics. A threat score is a measure of the amount of system weakening, obfuscation, persistence, modification, data exfiltration, and other behaviors which may threaten the host system’s integrity. The Threat Score is intended as an overall threat indicator or guide to a malicious system. The Threat Score is not an authoritative classification of good or bad software.
- Size—The size of the sample in bytes.
- AV Results—The Antivirus results according to ClamAV. A sample can have more than one signature if it is detected under more than one family of malware. A sample may also have no signatures associated with a virus.
- First Seen—The time stamp for when this sample was first seen by Cisco Secure Malware Analytics.
For more information, see Cisco Secure Malware Analytics.
Behavioral Indicators
The Behavioral Indicators (BI) are key traits and behaviors which may indicate malicious activity. Behavioral indicators include threat severity levels, HTTP Traffic, DNS Traffic, TCP/IP network sessions, processes, artifacts, and registry activities.
Investigate provides two key indicator scores: Severity and Confidence.
- Severity—Indicates the likely security risk posed by a given behavior, ranging from 0 to 100.
- Confidence—Indicates the likelihood of the sample exhibiting the stated behavior, ranging from 0 to 100.
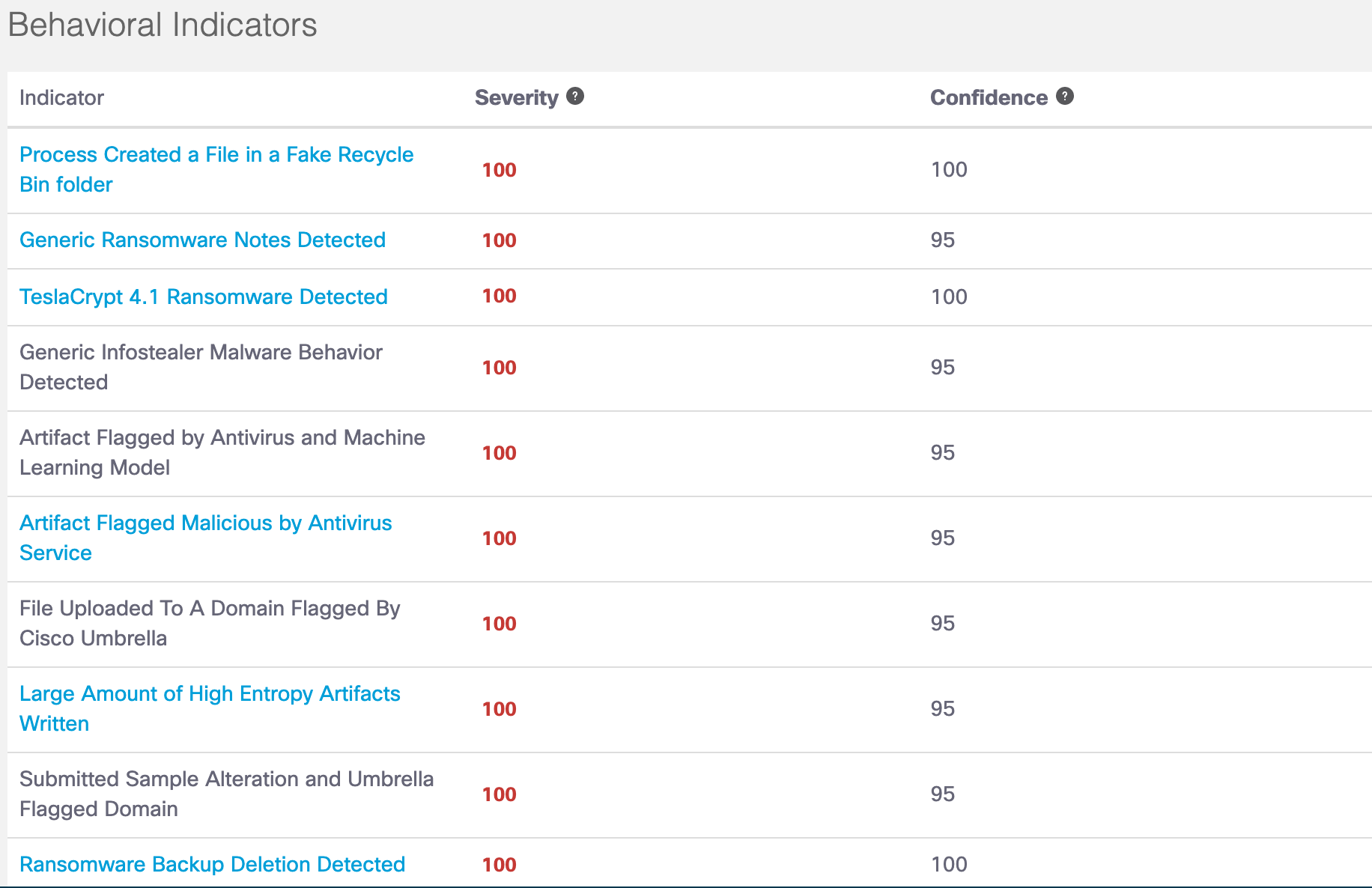
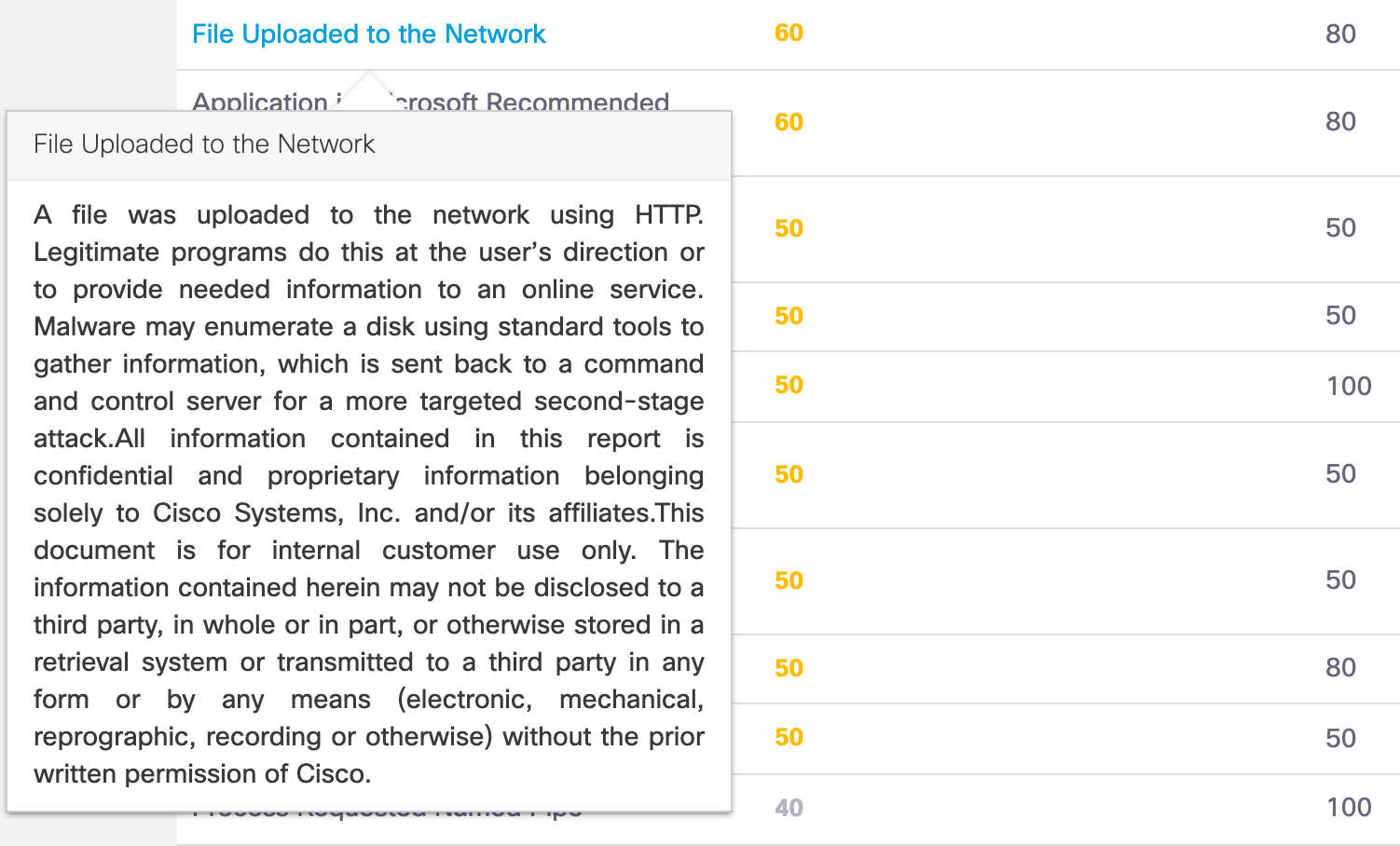
Click on the link to the behavioral indicator to view a description of the indicator.
Network Connections
A network connection is made by a certain file sample to an IP or a domain. The Network Connections section lists the destination, URLs related to the domain or IP, and security categories for the connection.
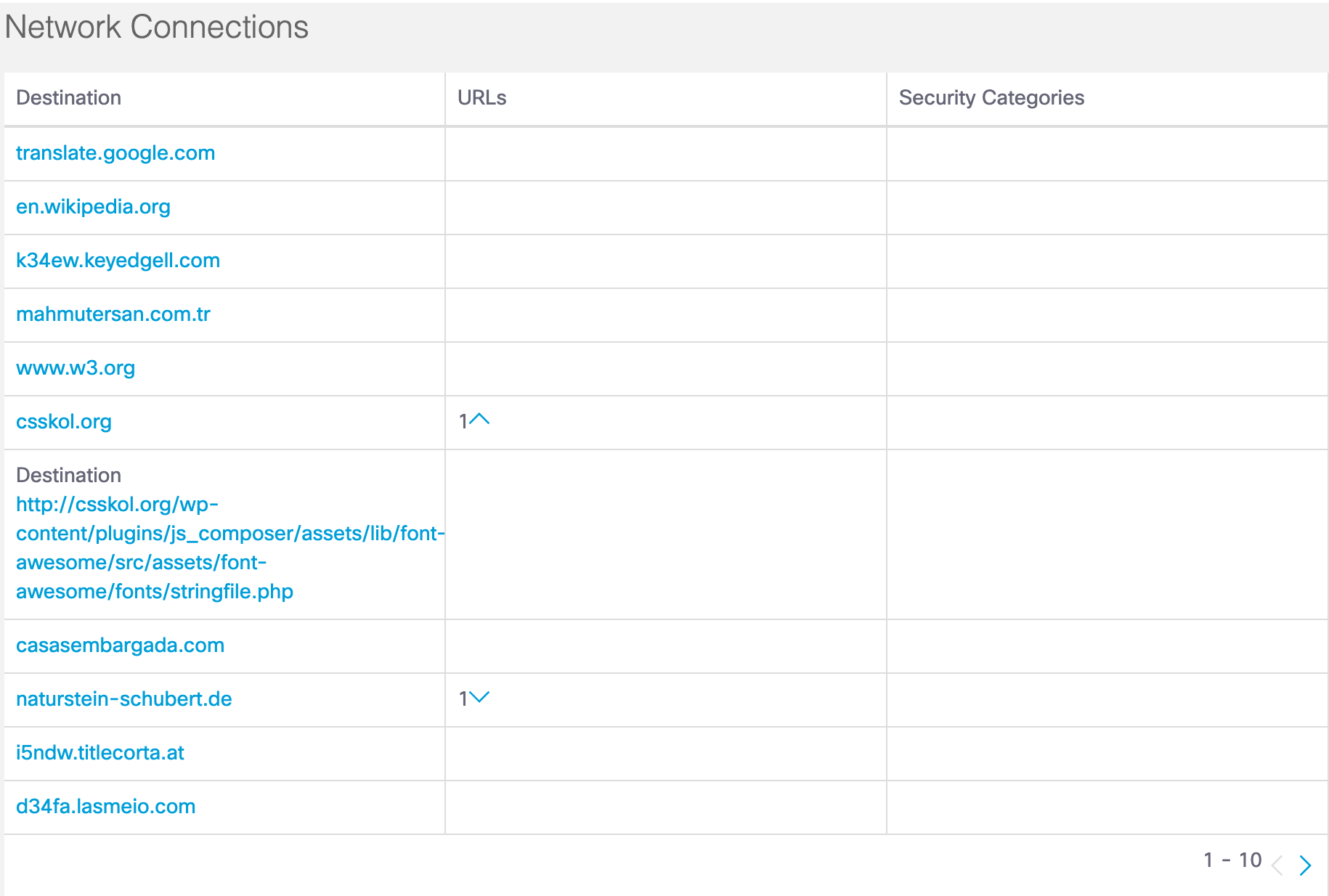
Click on a destination to display the domain or IP Address view for the destination.
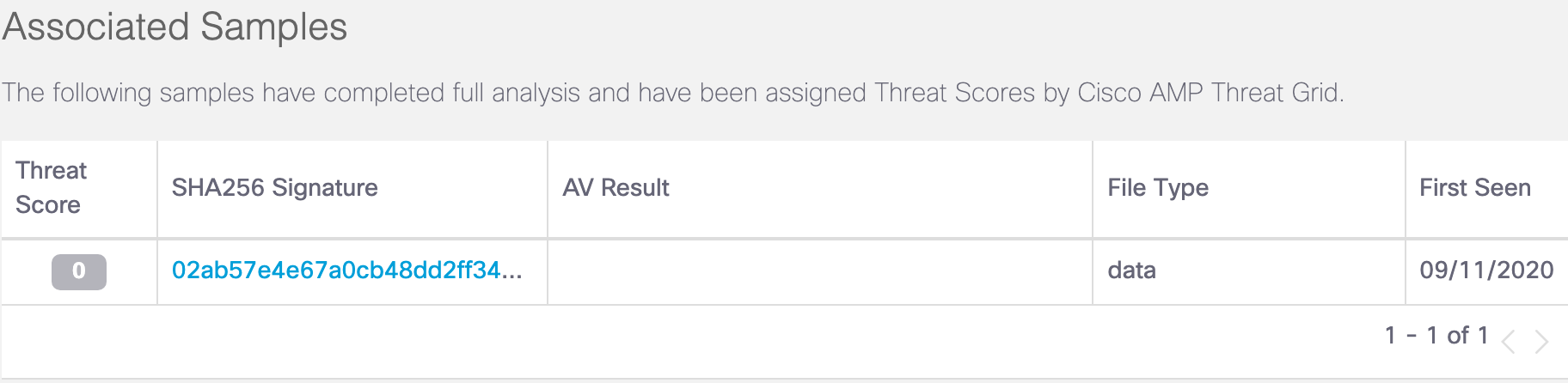
Associated Samples
A sample is a type of file, or file-like object, such as a process running in memory submitted and analyzed by Cisco Secure Malware Analytics. Associated samples are additional file samples known to be related to the main sample.
Associated Artifacts (Secure Malware Analytics Integration)
A threat artifact is a file that is created or modified during the analysis of a sample. Malware executables often download additional components and infect or modify system files, documents, and running processes. Artifacts are sometimes executables that you can analyze in Cisco Secure Malware Analytics.
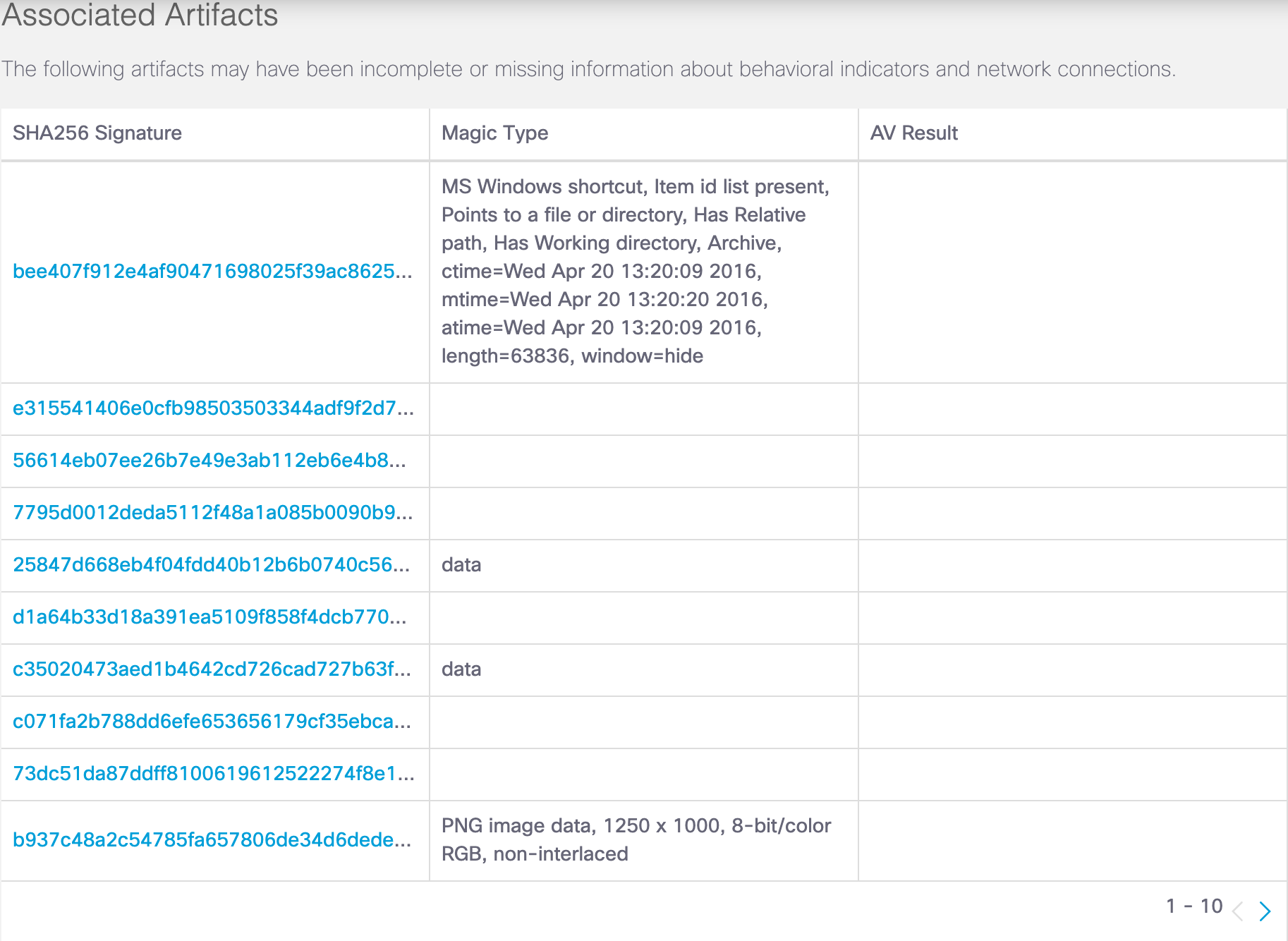
Click on the link to a signature sample to display the details of the sample threat artifact.
About the Geographic Distribution View in Investigate < About the Sample View in Investigate > About the IP Address View in Investigate
Updated over 1 year ago
