Manage Logs
By default, each organization's Umbrella dashboard instance logs all requests made by an identity. The level of logging for an identity's activity is set when you configure Centralized Settings > Advanced Settings. This setting is then shared with your organizations. By default, all requests are logged.
Logging options are:
- Log All Requests—For full logging, whether for content, security or otherwise
- Log Only Security Events—For security logging only, which gives your users more privacy—a good setting for people with the roaming client installed on personal devices
- Don't Log Any Requests—Disables all logging. If you select this option, most reporting for identities with this policy will not be helpful as nothing is logged to report on.
Logging to Umbrella's Data Warehouse
Each of your organizations stores their activity logs to Cisco Umbrella's data warehouse. By default, Umbrella saves event data logs to Cisco's California location; however, you can change the location of the data warehouse from North America to Europe at any time. For more information, see Change a Data Warehouse Location.
Logging to Amazon S3
The Cisco Umbrella Multi-Org console has the ability to upload, store, and archive traffic activity logs from your organizations' Umbrella dashboards to the cloud through Amazon S3. CSV formatted Umbrella logs are compressed (gzip) and uploaded every ten minutes so that there's a minimum of delay between traffic from the organization's Umbrella dashboard being logged and then being available to download from an S3 bucket.
By having your organizations' logs uploaded to an S3 bucket, you can then download logs automatically to keep in perpetuity in backup storage. Or, ingest the logs through your SIEM or another security tool to determine if any security events in your Umbrella logs coincide with events in other security tools.
Amazon S3 options:
- A self-managed bucket—You own the Amazon S3 bucket, including its configuration and management.
- A Cisco-managed bucket—Cisco owns the bucket and sets the configuration and management of it.
Advantages and Disadvantages to Configuring a Cisco-Managed Bucket
- Extremely easy to set up—it only takes a couple of minutes—and easy to manage.
- Included in the license cost for the Multi-org console, effectively making it free. Although having your own bucket is very inexpensive, the overhead of having to manage another bill can be prohibitive.
- You cannot add anything to your bucket besides log files from your organizations and the bucket cannot be used by another application.
- Some SIEM integration types may require advanced privileges for the user accessing the S3 bucket—beyond the basic Read permissions—and as such, may not work with the Amazon S3 feature.
- You cannot get support from Amazon directly for advanced configuration assistance, such as automation or help with the command line.
- Data can only be stored offline for a maximum of 30 days.
Estimate the Size of Your Logs
The size of your S3 logs depends on the number of events that occur, which is dependent on the volume of your DNS traffic. The size of each log line varies based on a number of items—for example, the length of the domain name or the number of categories. Assuming each log line is 220 bytes, a million requests would be 220 MB.
- In the Umbrella dashboard, navigate to Reporting > Activity Search.

- Under Filters, run a report for the last 24 hours and then click the Export CSV icon.
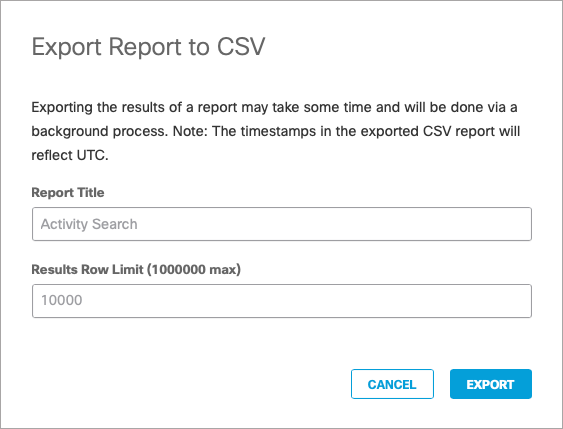
- Open the downloaded .csv file. The number of rows (minus one for the header) is the number of DNS queries per day; multiply that by 220 bytes to get the estimate for one day.
Update Billing Contact < Manage Logs > Enable Logging to Your Own S3 Bucket
Updated almost 2 years ago
