Provision Identities from Okta
Umbrella supports the provisioning of users and groups identities from Okta. You do not need to deploy an on-premises Cisco Active Directory (AD) Connector to integrate your users and groups identities.
Users and groups from Okta integrate with the Umbrella roaming computer deployments:
- Umbrella roaming client
- Cisco Secure Client (AnyConnect Umbrella roaming security module)
Note: Since Okta does not store the private IP to AD user mappings, an on-premises Umbrella AD connector is required for Umbrella Virtual Appliance (VA) or IP-to-user mapping deployments.
Table of Contents
- Prerequisites
- Limitations
- Supported Features
- Import the ObjectGUID Attribute from Okta
- Configure the Cisco User Management Connector App
- Troubleshooting
Prerequisites
- A valid Okta subscription.
- No concurrent provisioning from on-premise Active Directory and Okta .
If you are using the on-premises Cisco AD Connector to import user and group identities to Umbrella, and now wish to import the same identities from Okta, ensure that the on-premises Cisco AD connector is switched off or that the Cisco AD Connector service on the connector machine is stopped. - Full admin access to the Umbrella dashboard. See Manage User Roles.
Note: Concurrent synchronization of the same user and group identities from the Cisco AD Connector and the Cisco Umbrella Okta application is not supported and leads to inconsistent policy enforcement.
Limitations
- Umbrella supports the provisioning of an unlimited number of users from Okta to Umbrella.
- Umbrella supports the provisioning of 1000 groups from Okta to Umbrella.
Note: If you have more than 1000 groups in the organization, contact Support to get assistance with provisioning the groups in Umbrella. - To ensure that all users are provisioned, ensure that the ‘Everyone’ group is assigned to the Cisco User Management Connector app. You can push other additional groups as required for group-based Umbrella policy enforcement.
- Okta does not support nested groups.
- If you have previously imported groups from on-premise Active Directory and are pushing the same groups from Okta, the groups from Okta will not overwrite the groups imported from on-premise Active Directory. You will need to re-assign any group-based Umbrella policies to the groups imported from Okta.
- Depending on the number of users and groups being provisioned, it can take several hours for these identities to be available on the Umbrella dashboard.
- After the initial provisioning of users and groups, it can take up to one hour for subsequent changes to users and groups to reflect on the Umbrella dashboard.
Supported Features
The following Okta provisioning features are supported:
- Create Users—New users created in Okta will also be created in Umbrella.
- Update User Attributes—Updates to a user's profile through Okta will be pushed to Umbrella.
- Deactivate Users—Deactivating a user through Okta deactivates the user in Umbrella.
- Group Push—Groups in Okta can be pushed to Umbrella.
Import the ObjectGUID Attribute from Okta
The on-premises Cisco AD Connector, Cisco AnyConnect, and Umbrella Roaming Clients rely on the objectGUID attribute for user and group identification. You need to ensure that the objectGUID attribute of users is synchronized from Okta to Cisco Umbrella only if either of the conditions below are true:
- You have previously imported AD users to Umbrella using the on-premise Umbrella AD connector, are now importing the same user identities from Okta and want the previously imported identities to be persisted for policy or reporting purposes.
- You have endpoints that are authenticating against on-premise Active Directory and are running the Cisco AnyConnect agent or Umbrella Roaming Client.
Note: Before setting up the import of the objectGUID, ensure that the on-premise Cisco AD Connector that is synchronizing these identities is switched off or that the Cisco AD Connector service on the connector machine is stopped.
The Okta Active Directory agent does not synchronize the objectGUID attribute of users from on-premise Active Directory to Okta by default.
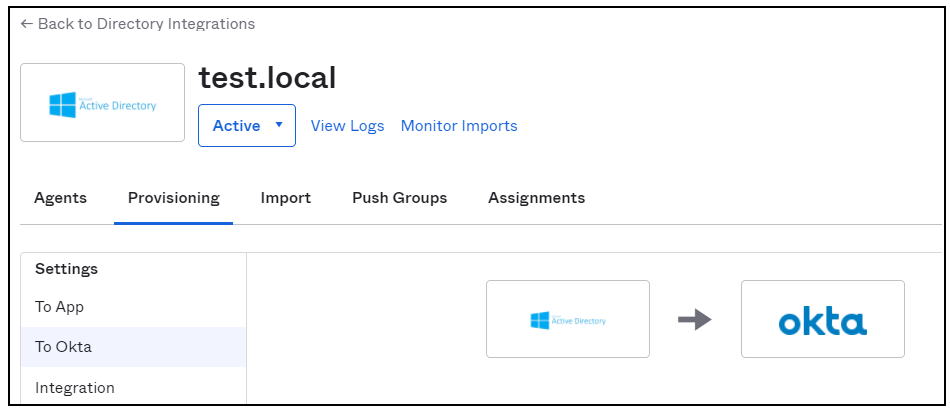
- Navigate to the Directory Integrations tab on your Okta portal, and click the Provisioning tab. Select To Okta from the drop-down list.
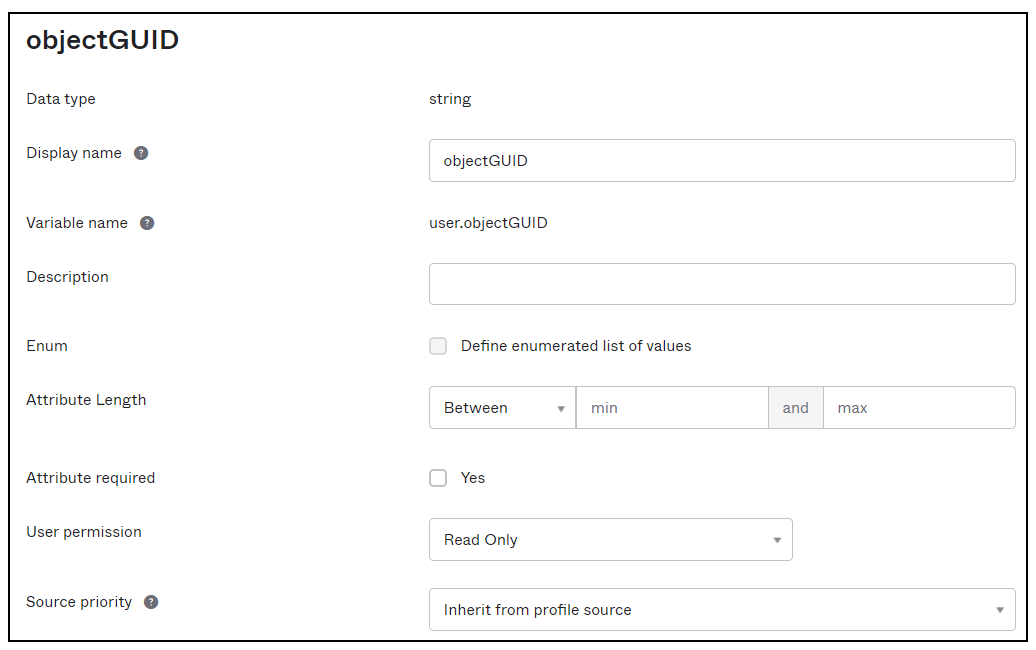
- Navigate to Profile Editor under Okta Attribute Mappings and create a custom attribute of string type called objectGUID.
- Create a new User Profile Mapping for your AD domain to Okta User:
appuser.externalId > objectGUID - Under Okta Attribute Mappings, do a Force Sync of attributes to ensure that the objectGUID attribute for users is imported from AD.
Configure the Cisco User Management Connector App
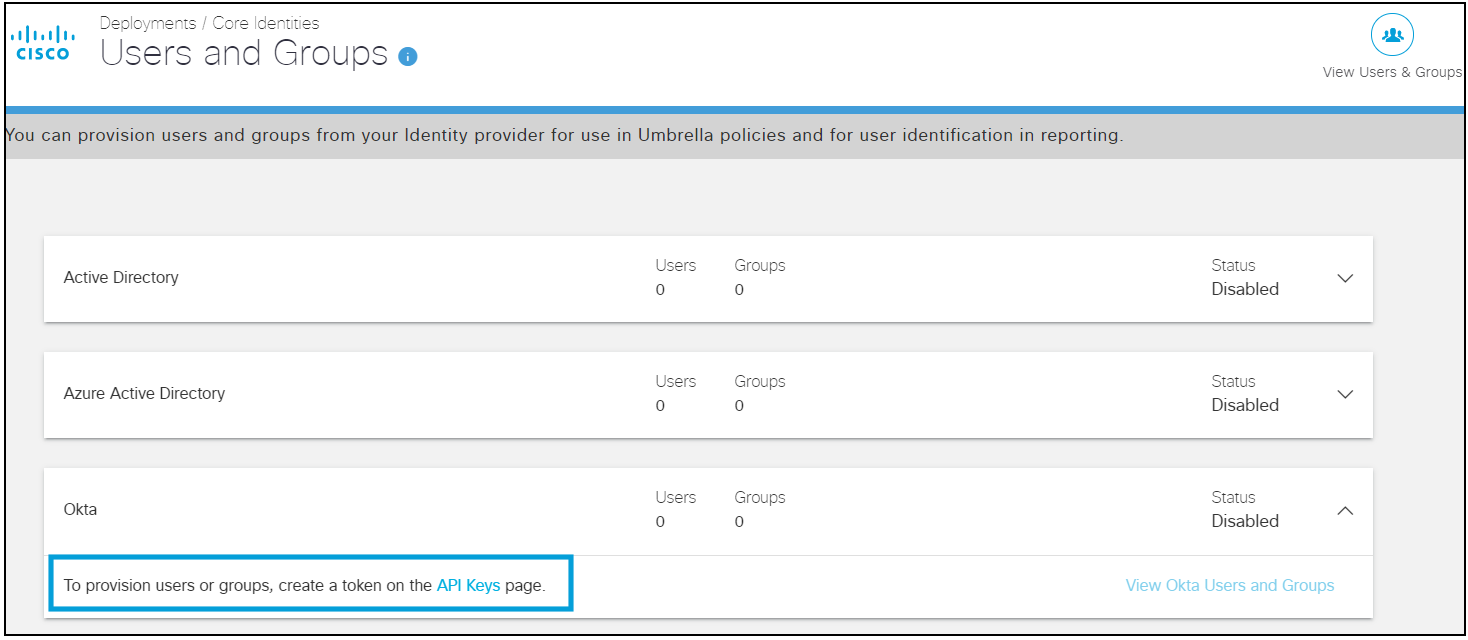
- In Umbrella dashboard, navigate to Deployments > Core Identities > Users and Groups.

- Expand the Okta card and click API Keys.
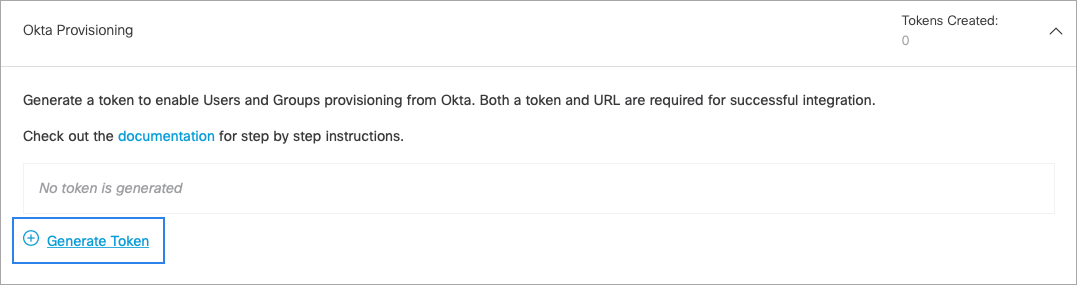
- Expand Okta provisioning on the API Keys page and click Generate Token.
Umbrella only displays the generated token once. Copy and save the URL and the token.
- Log into Okta and add the Cisco User Management Connector app.
- On the Provisioning tab of this app, select Enable API integration and add the API token. Test the API credentials and click Save .
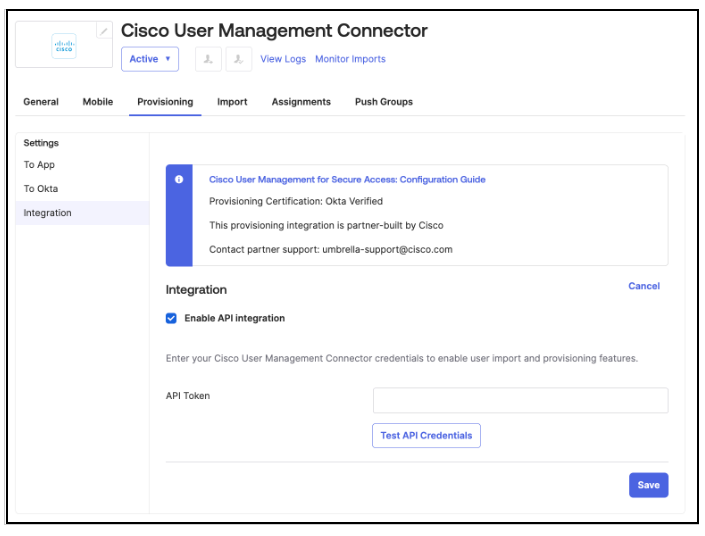
- In the Provisioning to App section, enable the Create Users, Update User Attributes, and Deactivate Users options. Without these options selected, identities will not be provisioned.
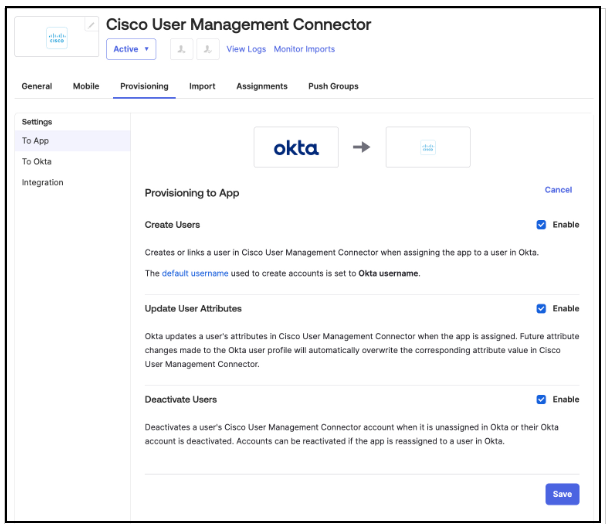
- Verify that the following attributes are chosen for synchronization to Umbrella. Other attributes are not required.
- Username
- Given name
- Family name
- Display name
- Primary email
Note: Umbrella does not list the Given name and Family name attributes for users. Umbrella only lists the Display name and Username attributes.
- If you need to import the ObjectGUID attribute for users:
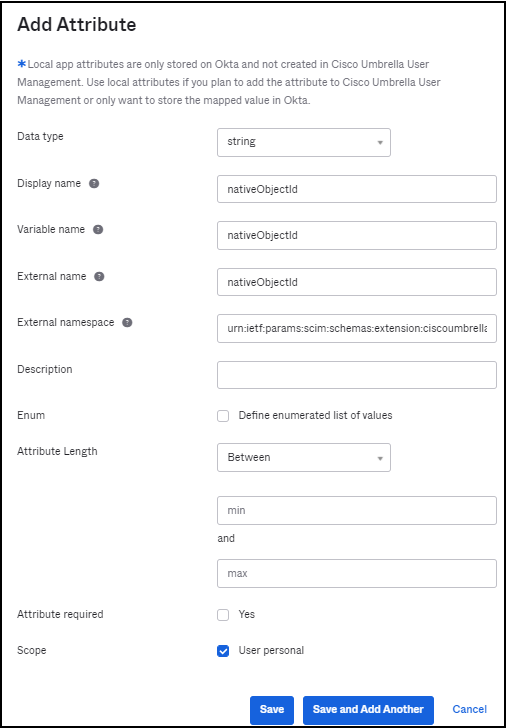
a. Add a new attribute with the following criteria:
- Display name, Variable name and External name all set to nativeObjectId
- Scope set to User personal
- External namespace set to
urn:ietf:params:scim:schemas:extension:ciscoumbrella:2.0:user
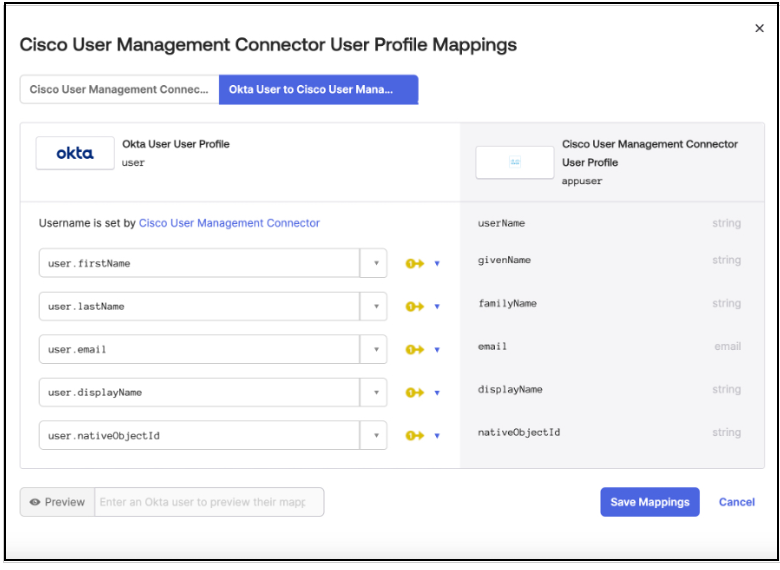
b. Navigate to the Profile Editor and create a new User Profile Mapping (Okta User to Cisco Umbrella User Management user) for user.objectGUID > nativeObjectId and save the mapping. Select the option to Apply the mappings to all users with this profile.
- Once provisioning is configured, assign users (people) to this app through the Assignments tab of the app. You can assign individual users or specific groups to the app. To assign all users, assign the Everyone group to the app.
Note: Assigning groups to the app will not provision these groups to Umbrella. Only users that are members of the assigned groups will be provisioned. Do not manually enter any value for the nativeObjectId field when assigning any groups and users. To avoid provisioning errors, leave this field as-is.
Once users and groups are assigned, these users will automatically start getting provisioned to Umbrella. Wait for all users to show up on the Umbrella dashboard before starting to push groups. This can take time depending on the number of users provisioned.
- Once you have confirmed that all users have been provisioned to Umbrella, you can provision groups and group membership to Umbrella using the Push Groups tab of the Cisco User Management Connector app on the Okta portal. Pushing a group does not sync any users and only provisions the group to Umbrella.
Note: Okta does not recommend pushing groups that are assigned to the application. So if you have assigned the ‘Everyone’ group to the application, you should not push the same group.
Cisco Umbrella supports provisioning of maximum 200 groups. It is recommended to push only those groups that you wish to configure Umbrella policy on.
- You can view the provisioning logs from the Cisco User Management Connector app to analyze the progress of provisioning.
- You can view the users and groups provisioned from Okta on the Users and Groups page.
Note: Umbrella recommends refreshing the SCIM token at least once every 90 days. You can refresh the token on the API Keys page of the Umbrella dashboard. Umbrella does not automatically refresh the SCIM token. Ensure that you immediately copy the new token to the Umbrella app on Okta so that provisioning is not impacted.
Troubleshooting
If you have issues integrating Okta SCIM with Umbrella, contact Umbrella Support.
Provision Identities from Microsoft Entra ID < Provision Identities from Okta > Active Directory Integration with the Virtual Appliances
Updated 4 months ago
