Conduct a Pattern Search
Investigate supports standard regular expression pattern search functionality. You can search the Investigate database for a domain using a regular expression (RegEx). If you are not familiar with building a RegEx, there are several online tools that can help create a regular expression: for example, http://regexr.com.
The Investigate database contains the information about domains that were looked up within a specific time period. As such, when you query Investigate, you may find results that do not match a domain that resolves, but match domains in which Umbrella received DNS lookups. We do our best to sanitize the pattern search results, but nonexistent domains occasionally appear in the results.
Investigate Pattern Search enables you to discover newly queried domains that may include your company’s brand or intellectual property. You can use pattern search to find minor intentional misspellings—commonly used to confuse users in phishing emails—then identify campaigns targeted against your employees or customers. From those discoveries, pivot through the attacker’s infrastructures to identify a related attacker infrastructure that shares that network space or other domains registered by the same email addresses.
Investigate Smart Search is available to search for a fully-qualified domain name, IP, ASN, file hash, and email address. For more information, see Getting Started with Investigate.
About Pattern Search
In the dashboard, an Investigate pattern search is limited to 500 results. The Umbrella Investigate API /search endpoint can return up to 1000 records. If the results of your query exceed these limits, we recommend that you refine the RegEx and perform multiple pattern searches. Alternatively, you can limit the time period for the search.
The pattern search results only extend back thirty days. Only newly queried domains are discovered, whether the domain was registered recently or not. The Investigate dashboard and the Investigate API pattern search include a date in which the domain was first seen—the first time Umbrella recorded a query for the domain. Domains seen before the query time period are not found in the search result—including almost all common, well-known domains.
Pattern Search provides pre-configured time periods to constrain the search. The default and maximum time range to query Investigate is the last thirty days (Last 30 days). You can restrict the pattern search to include information about domains from the last seven days or the past 24 hours.
To perform a pattern search, navigate to Investigate > Pattern Search in Umbrella.
- Choose a time range from the Constrain RegEx search to drop-down list.
- In the search bar, click the ? (help icon) to display a list of operators for a RegEx search.
Operators
- *—An asterisk matches zero or more instances of the previous token.
- .—A period matches exactly one character.
- [ ]—Brackets match a class of characters. For example, use [0-9] to match single digits (0 to 9), or use [a-z] to match alphabetic characters (a to z).
- ( )—Parentheses group tokens together for modifiers. For example, (ya)* matches
ya,yaya, oryayaya. - ?—A question mark matches one or zero instances of the previous token. For example, hi(ya)? matches
hiorhiya.
Note: The period (.) character has meaning as a wildcard and as a literal in hostnames. If you would like to use this character as part of your pattern, you must escape it using the backslash character (\). For example, .\.umbrella\.com matches a.umbrella.com or b.umbrella.com.
RegEx Examples
To check for ‘typosquatting’ on a domain, enter a range of characters within a domain name. For example,
...\.yah[a-z]o\.com, matches both the correct domain (www.yahoo.com) and the misspelled version, (www.yahro.com), and any other typos found in the fourth character of the string along with any other non-www prefixes.
To search for domains without specifying the www prefix, simplify the RegEx to: yah[a-z]o\.com.
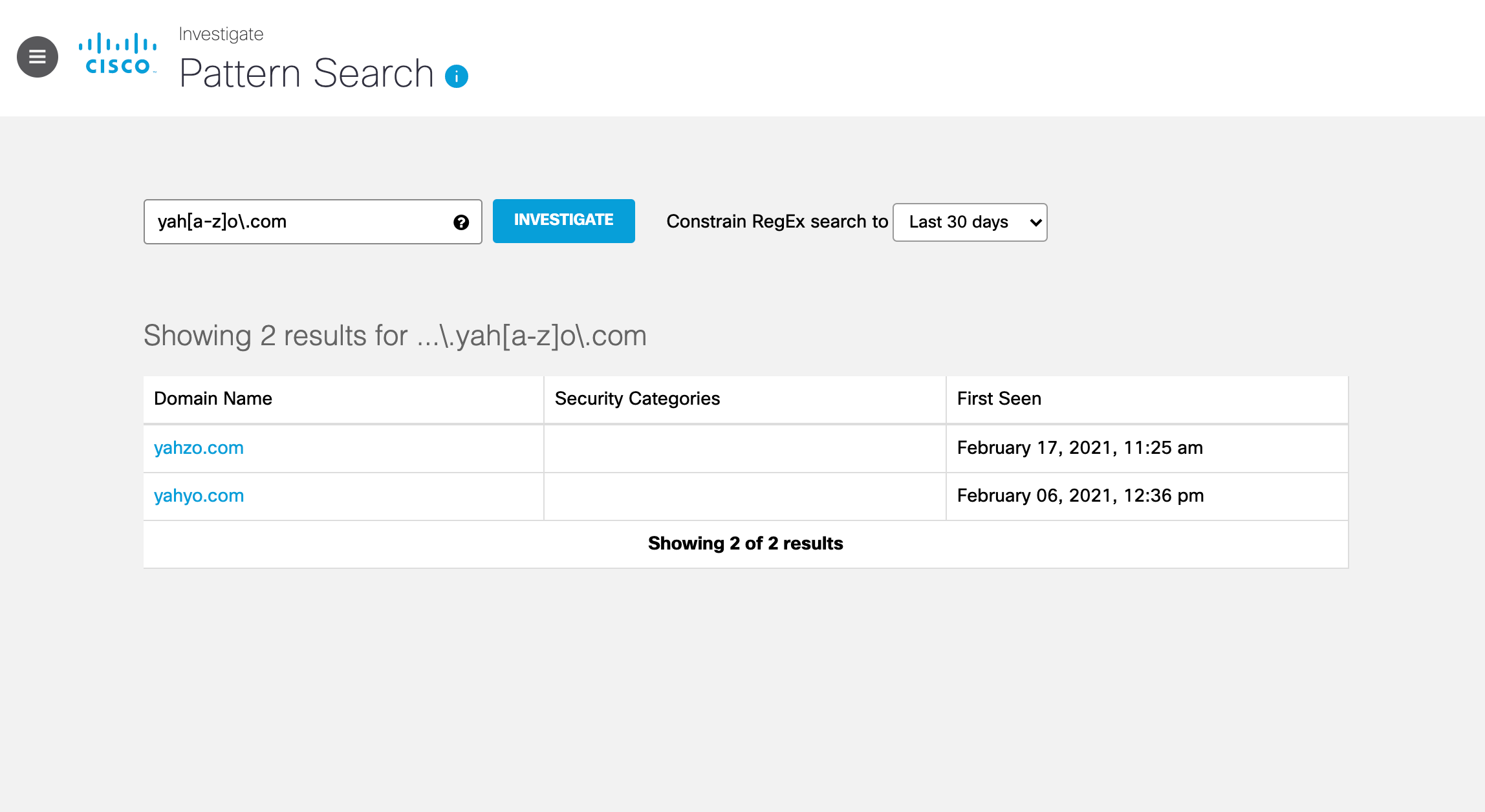
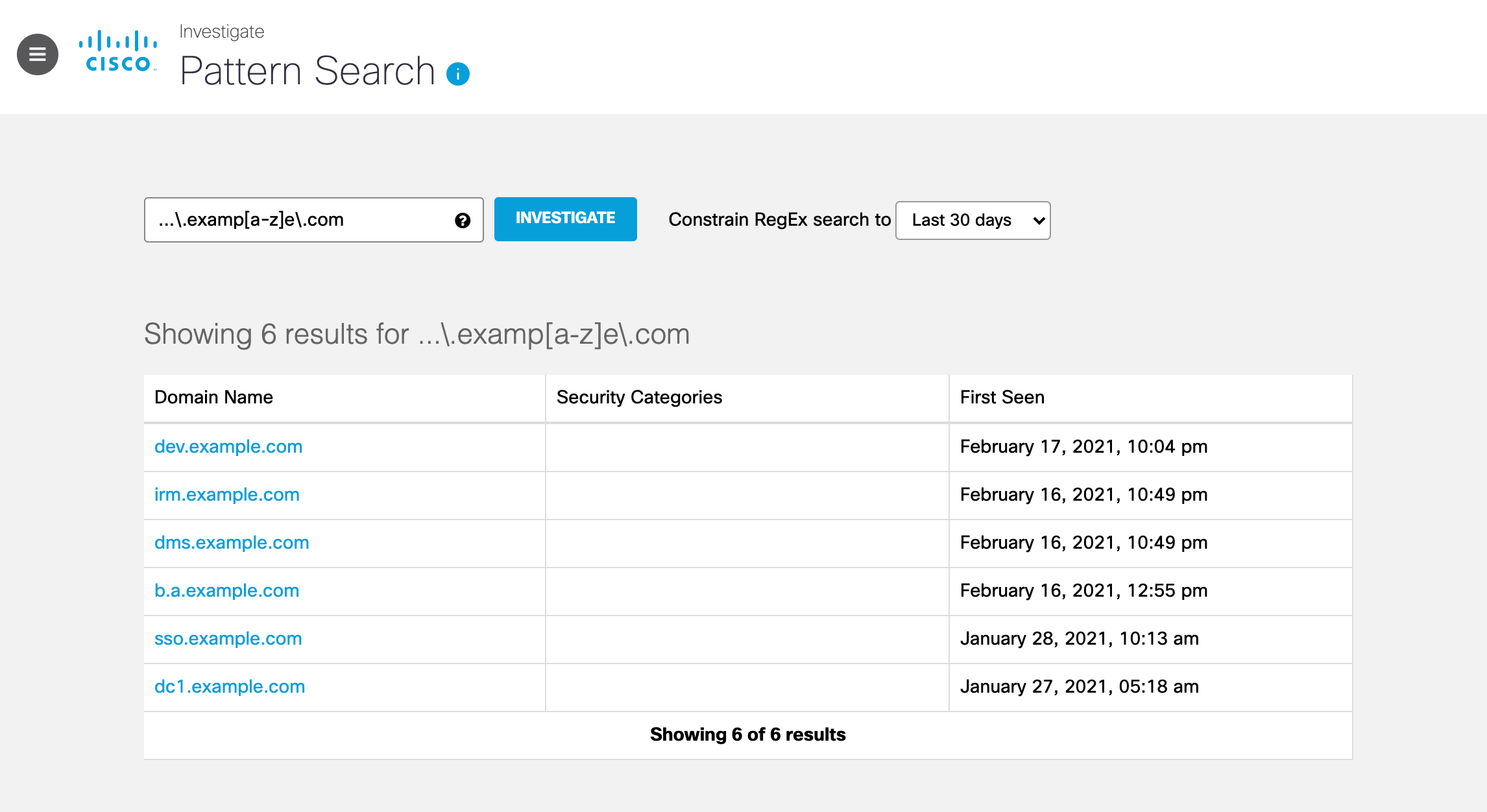
Pattern search returns the domain name and date when Umbrella recorded a DNS lookup against the hostname (First Seen).
Note: If the domains returned from your pattern search match any Umbrella security categories, Investigate lists the security categories with the domain.
Getting Started with Investigate < Conduct a Pattern Search > Manage the Investigate Only User Role
Updated over 1 year ago
