Encryption and Authentication
The Umbrella roaming client utilizes technology that authenticates and situationally encrypts DNS queries, providing security and privacy not previously available at a scalable and reliable level. This article provides in-depth, detailed technical information and context for the security-focused attributes of the Umbrella roaming client.
Table of Contents
- Concepts
- DNSCrypt
- DNSCrypt versus DNSSEC
- Encryption and Authentication
- Encrypted State
- Unencrypted State
Concepts
DNS is one of the only protocols that does not provide optional or required encryption. Compare that to many other essential protocols handling sensitive data, such as HTTP, IMAP, SSH, RDP, POP3, SMTP, which have encrypted versions that can be utilized or are already encrypted on their own.
The encryption and authentication of DNS packets between the local computer and recursive DNS server is a relatively new concept, one that is not accomplished by utilizing DNSSEC. DNS packets sent between a computer and recursive DNS server can be manipulated or sniffed, which can be used to gain information about a specific computer or network to perform an attack.
DNSCrypt
The Umbrella roaming client utilizes the DNSCrypt protocol to address two important security aspects of DNS:
Data Privacy—DNS packets are encrypted; therefore, the packet data won't be viewable if sniffed/captured between the endpoint computer and the recursive DNS server.
Authentication—DNS packets are signed with a unique signature that must be verified both on the endpoint computer and the recursive DNS server, preventing DNS spoofing and other forms of DNS-based attacks.
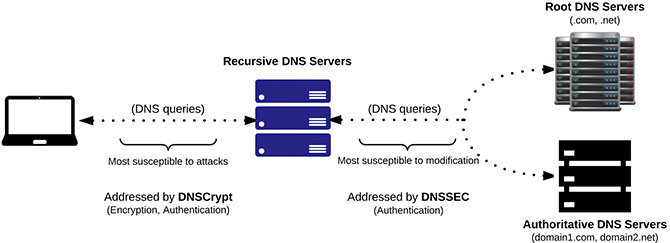
DNSCrypt versus DNSSEC
DNSCrypt authenticates and situationally encrypts the DNS queries between the endpoint computer and recursive DNS server. The computer and recursive DNS server both must support DNSCrypt.
DNSSEC provides authentication between the recursive DNS server, the root DNS servers, and the authoritative DNS servers which support DNSSEC. The recursive DNS servers and Authoritative DNS Servers must both support DNSSEC.
Encryption and Authentication
The Umbrella roaming client encrypts DNS queries only when it is in the encrypted state. If the Umbrella roaming client is in another state, it will still authenticate the packets, preventing DNS spoofing and other types of DNS-based attacks, but the queries will be sent unencrypted (in plaintext).
Read more about Umbrella roaming client states to find out how and when the Umbrella roaming client is in a certain state.
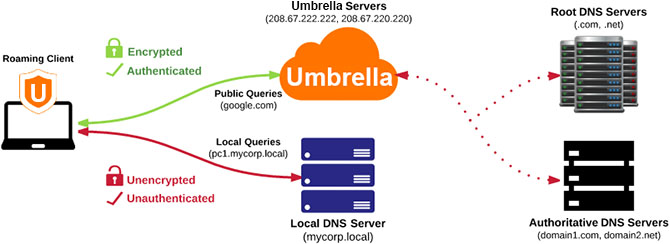
Encrypted State
The Umbrella roaming client sends encrypted, authenticated DNS queries to Umbrella if both conditions are true:
- The Umbrella roaming client is in the encrypted state.
- The DNS query does not search for a domain or a subdomain of the domain that is found on the internal domains list. For more information about internal domains, see Domain Management.
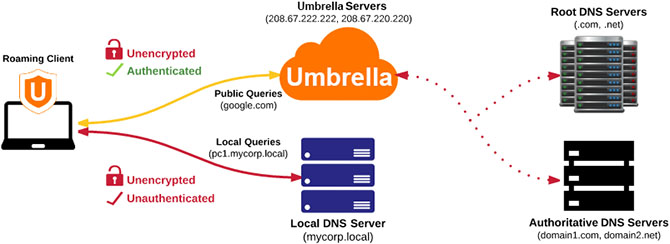
Unencrypted State
The Umbrella roaming client sends unencrypted, authenticated DNS queries to Umbrella if any conditions are true:
- The Umbrella roaming client is in any state except the encrypted state.
- The domain which is being queried is a domain, or subdomain thereof, on the Internal Domains list.
- The domain which is being queried receives an NXDOMAIN response from Umbrella, and the NO_NXDOMAIN parameter was not intentionally set to "1" when the Umbrella roaming client was installed.
Roaming Computers Settings < Encryption and Authentication > Command-line and Customization for Installation
Updated almost 2 years ago
