Admin Audit Log Report
The Admin Audit log records changes that have been made by your administrative team in your organization's Umbrella settings. Logs appear when change events occur in the dashboard, such as adding a user or modifying a policy. You can access data in 90-day increments. For more information about the details of the logs, see Admin Audit Logs.
Prerequisites
- A minimum of Read Only access to the Umbrella dashboard. See Manage User Roles.
Generate Admin Audit Log Report
- Navigate to Reporting > Management > Admin Audit Log.
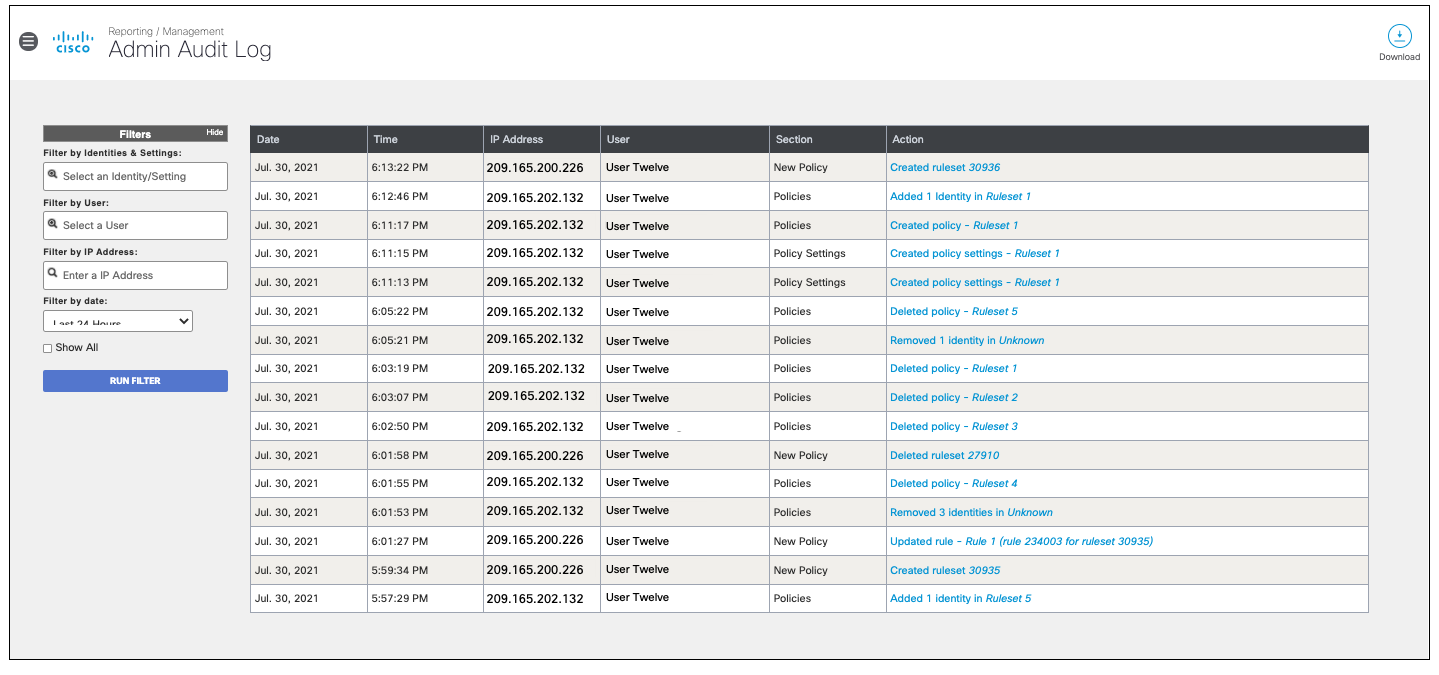
- Configure filters and then click Run Filter.
Optionally, select Show All to include events created by agents outside of the organization.
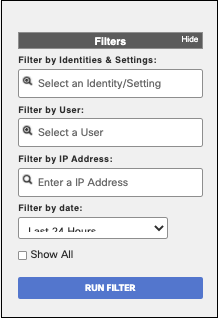
Identities & Settings—Filter by identity or setting.
User—Filter by user.
IP Address—Filter by IP address.
Date—Select a date range to see the changes for that period or select a user or the IP of the network that made the changes. The maximum supported range is 90 days.
Note: Any identity or setting that was deleted or re-named as part of an admin change will not be searchable in the filter as it is no longer in the database. However, the change has still been recorded and can be filtered by the User, IP Address or time range.
- Click an Action to view further details of an event.
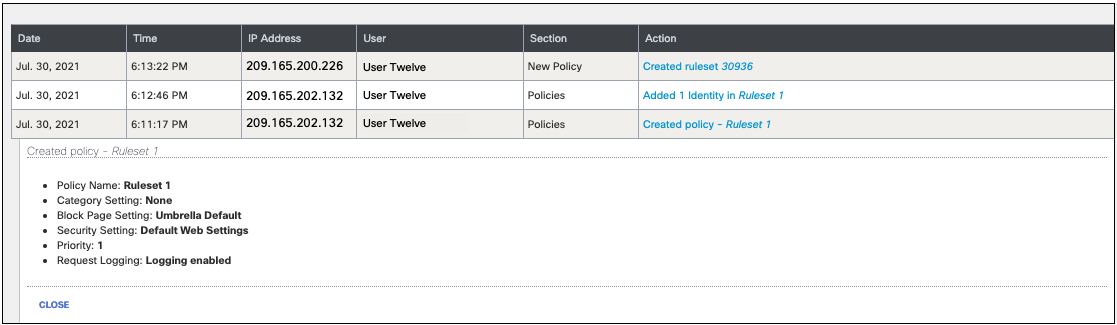
Identity Details < Admin Audit Log Report > Export Admin Audit Log to an S3 Bucket
Updated almost 2 years ago
