Configure Active Directory User Exceptions
Many organizations use service accounts in order to perform scheduled tasks or automatic updates. If a user logs in while a service account is performing a scheduled task, the login event will be attributed to the service account. The result is that the policy for the service account will be applied instead of the user who is actively logged in and using the computer. The Active Directory User Exception should be applied to service accounts within your organization so that their login events to your Domain Controllers are ignored by the Cisco AD Connector.
Active Directory user exceptions are best used with:
- Service accounts that perform scheduled tasks: for example, software backups
- Service accounts that need to log in to the network to perform updates: for example, anti-virus clients
- Adding the IPs of RODCs which mirror events
Note: Do not use this feature with any user accounts you wish to have the login events recorded for, or accounts whose activity you wish to see in the reporting and that should have policy applied to it.
Table of Contents
- Prerequisites
- Set Up Active Directory User Exceptions
- Set Up Active Directory Group Exceptions
- Set Up Active Directory IP Address Exceptions
Prerequisites
- For information about the requirements for deploying the AD Connector, see Prerequisites for AD Integration with VAs.
Set Up Active Directory User Exceptions
- Navigate to Deployments > Configurations > Service Account Exception and click Add.
- Under Account Type choose User.
- Under Value enter the AD Username or login (sAMAccountName) for the account in the format "Username" (not "Username@domain").
Note: This is not necessarily the same account name as the one displayed in the AD Users Identities in the dashboard. Confirm the account username in the Active Directory Users and Computers snap-in, not the Umbrella dashboard.
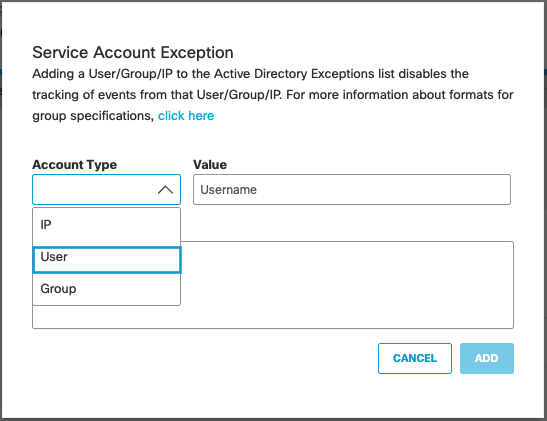
- Enter an optional description and click Create.
Note: In multi-AD domain environments, any user exception (sAMAccountName) configured will be blocked for all AD domains.
Set Up Active Directory Group Exceptions
You can add Active Directory Groups to the exception list. The Cisco AD Connector will ignore login events generated by all users and computers belonging to the specified group and any sub-groups and exclude them from the AD mappings. This can be used for AD groups that comprise only service accounts, so that the individual service accounts need not be specified as exceptions.
Note: Adding Active Directory Organization Units (OUs) is not supported.
- Navigate to Deployments > Configurations > Service Account Exception and click Add.
- Under Account Type choose Group.
- Under Value enter the Distinguished Name (DN) for the AD group that you want to add as an exception. For example, enter the AD group name as CN=Engineering,CN=Builtin,DC=mydomain,DC=com.
Note: This is not the same format as the one displayed in the AD Groups Identities in the Umbrella Dashboard. Please confirm the group DN in the Active Directory Users and Computers snap-in, not the Umbrella Dashboard. The group DN is case sensitive. You can also use this Powershell command to confirm the distinguished name for AD groups:
Get-ADGroup -Identity <ADGroupName>
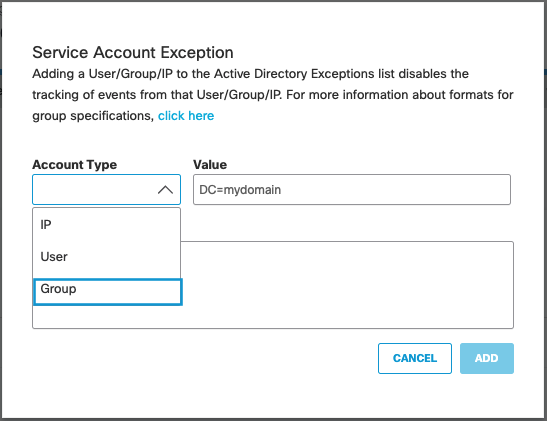
- Enter an optional description and click Create.
Set Up Active Directory IP Address Exceptions
IP addresses can also be added to the Exceptions list. The Cisco AD Connector will ignore all the events generated by the configured IP to exclude it from the AD mappings. An example use case would be the IP address of a Netscaler server or a RODC that mirrors events.
- Navigate to Deployments > Configurations > Service Account Exception and click Add.
- Under Account Type choose IP.
- Under Value enter the IP address.
Note: IP address ranges are not supported. Only individual IP addresses, such as 10.20.30.40, are supported.
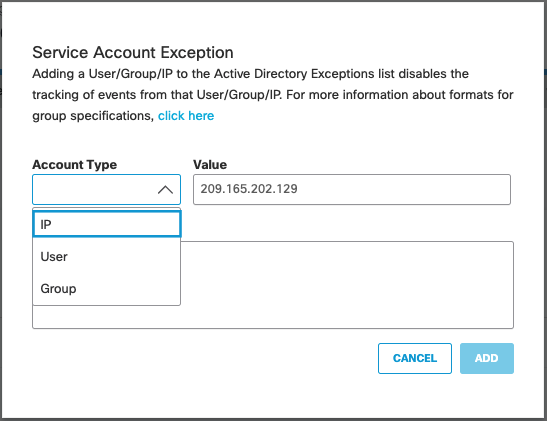
- Enter an optional description and click Create.
Prerequisites for AD Integration with VAs < Configure Active Directory User Exceptions > Prepare Your Active Directory Environment
Updated about 1 year ago
