Enable Cisco Security Cloud Sign On
Security Cloud Sign On enables you to sign into your Cisco products with one set of credentials. For more information, see the Cisco Security Cloud Sign On Quick Start Guide.
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
- All users must have a Cisco Security Cloud Sign On account.
All Users Must Have a Cisco Security Cloud Sign On Account
Enabling Security Cloud Sign On as a SAML provider requires a Cisco Security Cloud Sign On account assigned to your Umbrella application. Any users without an account will not be able to authenticate to the Umbrella dashboard.
Procedure
- Navigate to Admin > Authentication.

- In the SAML Dashboard User Configuration section, click Enable SAML.
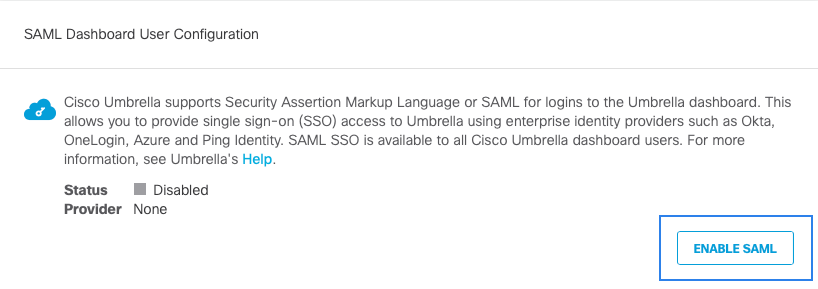
- Select Cisco Security Cloud Sign On and click Next.
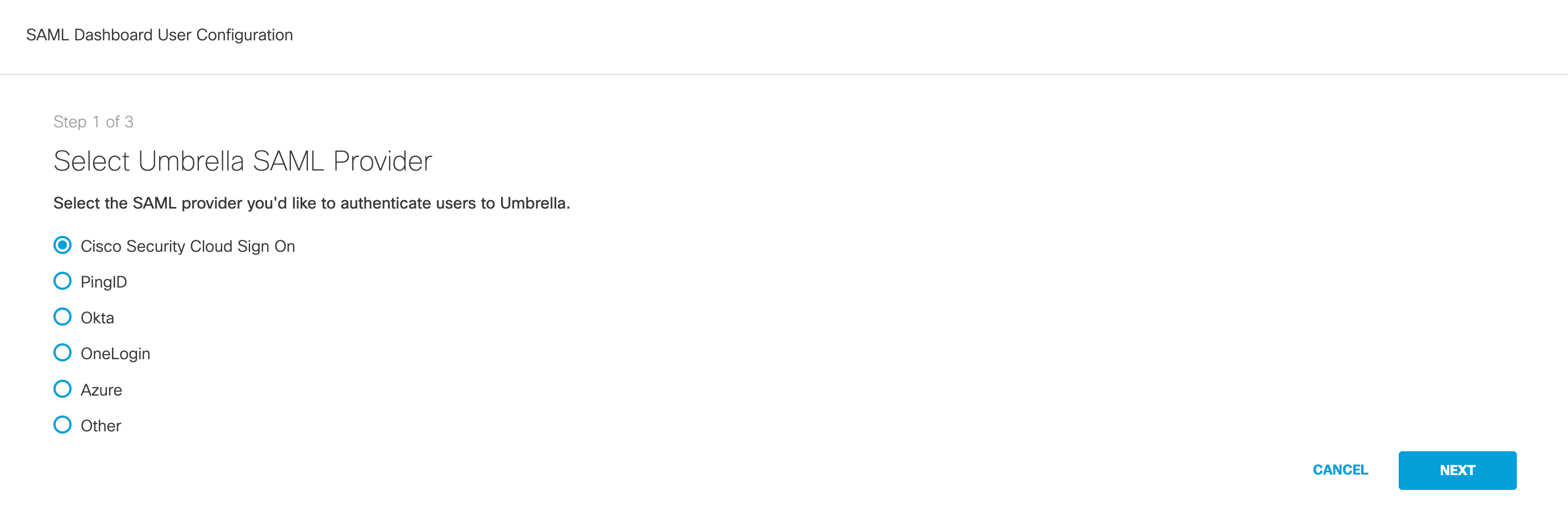
- Click Cisco Security Cloud Sign On to create a Cisco Security Cloud Sign On account and on the following window click Sign up now. For more information about creating this account, see Cisco Security Cloud Sign On Quickstart Guide.
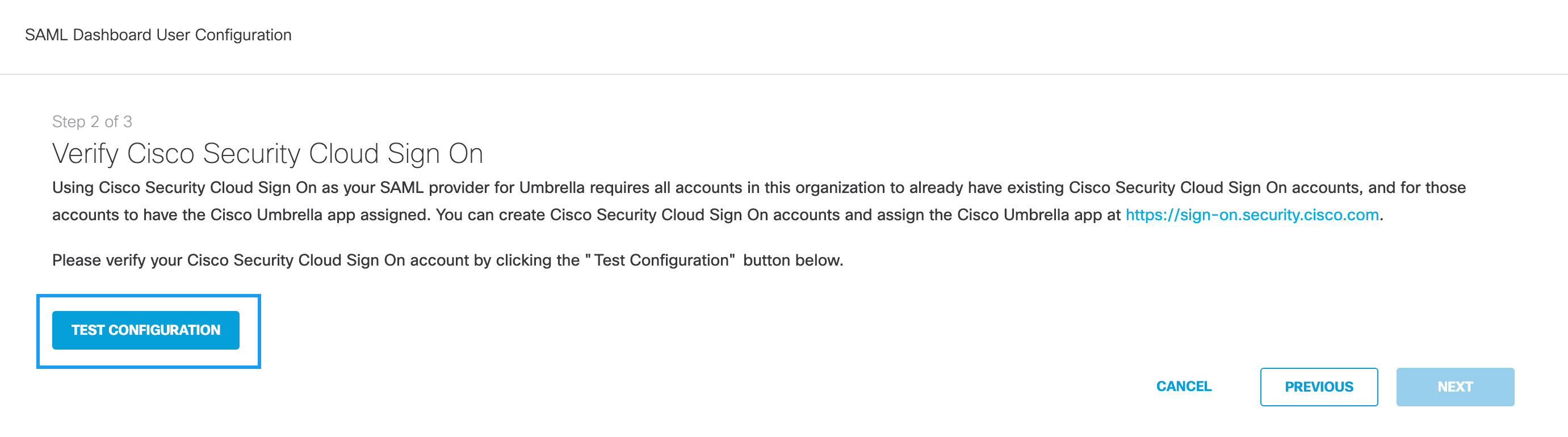
- Once an account is created, return to Step 2 of the configuration in Umbrella. Click Test Configuration.
- Sign in with the credentials provided when you created the Cisco Security Cloud Sign On account.
- Once the authentication is complete, a success modal appears:

- Dismiss the modal and return to Step 2 of the configuration in Umbrella. If the configuration is complete, a success message appears.
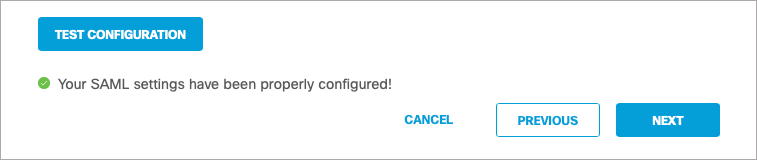
Test Configuration
The Test Configuration must be performed and successful for the set-up to complete.
- Click Next. The third step of the configuration appears informing you:
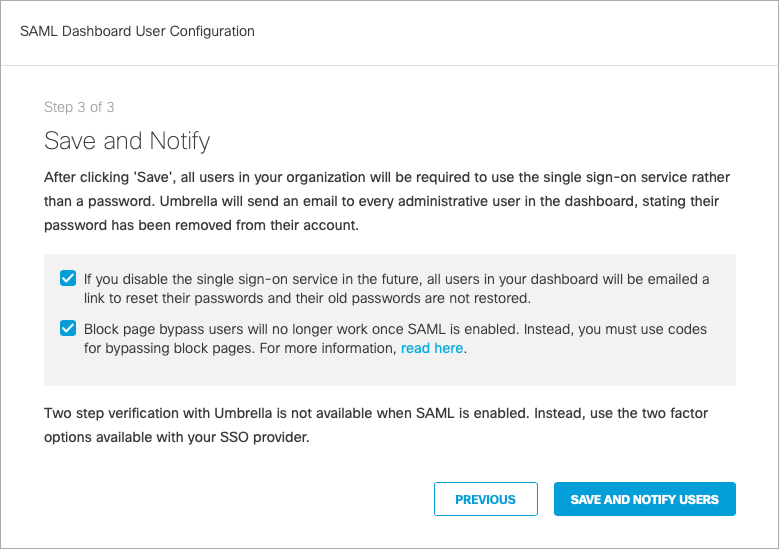
- This single sign-on service will now be required going forward.
- Umbrella will send an email to all dashboard users (not end-users) and a message to all admins in the dashboard to inform them of the mandatory SSO and that passwords are no longer accepted.
- If the SSO is disabled in the future all users will be emailed a link to reset their passwords as old passwords will not be accepted.
- Block page bypass users will no longer function once SAML is enabled.
- Check both boxes to acknowledge the information and click Save and Notify Users. Both boxes are required to be checked before saving the configuration.
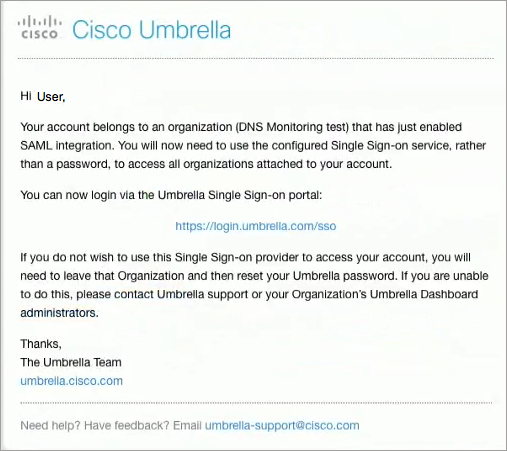
Cisco Security Cloud Sign On is now enabled in your organization. All users receive an email informing them of the required SSO.
Disable Two-Step Verification < Enable Cisco Security Cloud Sign On > Disable Cisco Security Cloud Sign On
Updated over 1 year ago
