Add a Real Time Rule to the Data Loss Prevention Policy
There is only one data loss prevention policy. Rules are added to the policy to define what traffic to monitor (identities and destinations), the data classifications that require monitoring, and whether content should be blocked or only monitored.
Prerequisites
- HTTPS Inspection must be enabled either on the Web Default Policy, or at least one web policy ruleset where the same identity is configured in a DLP rule. For example, if the identity "Network A" is configured for a DLP rule, it must also be configured for a web policy ruleset where HTTPS is enabled. For more information, see HTTPS Inspection.
- Full Admin access to the Umbrella dashboard. See Manage User Roles.
Procedure
- Navigate to Policies > Management > Data Loss Prevention Policy, click Add Rule, and choose Real Time Rule.
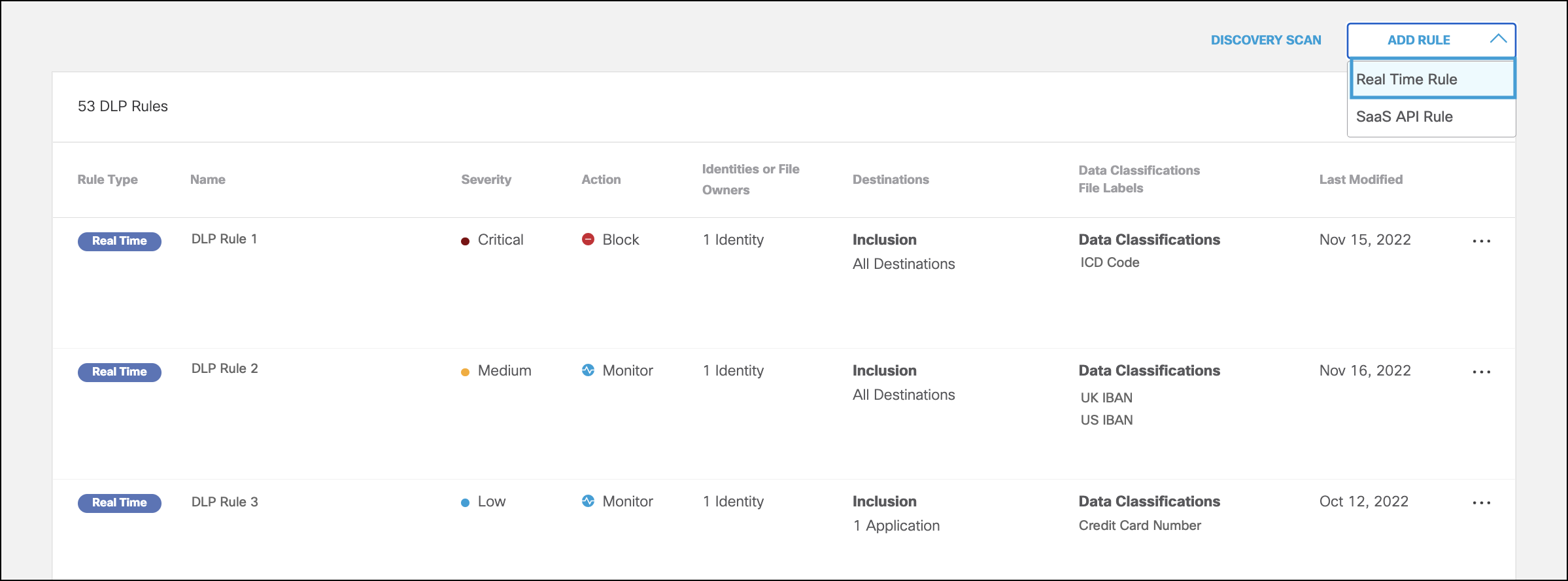
- Under Add New Real Time Rule, give your rule a meaningful name and description.
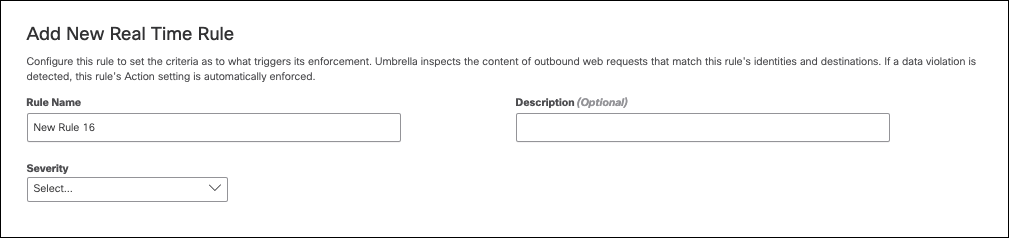
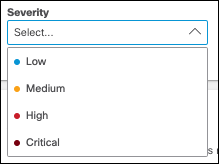
- Choose a severity for your rule based on the risk involved or importance within the ruleset.
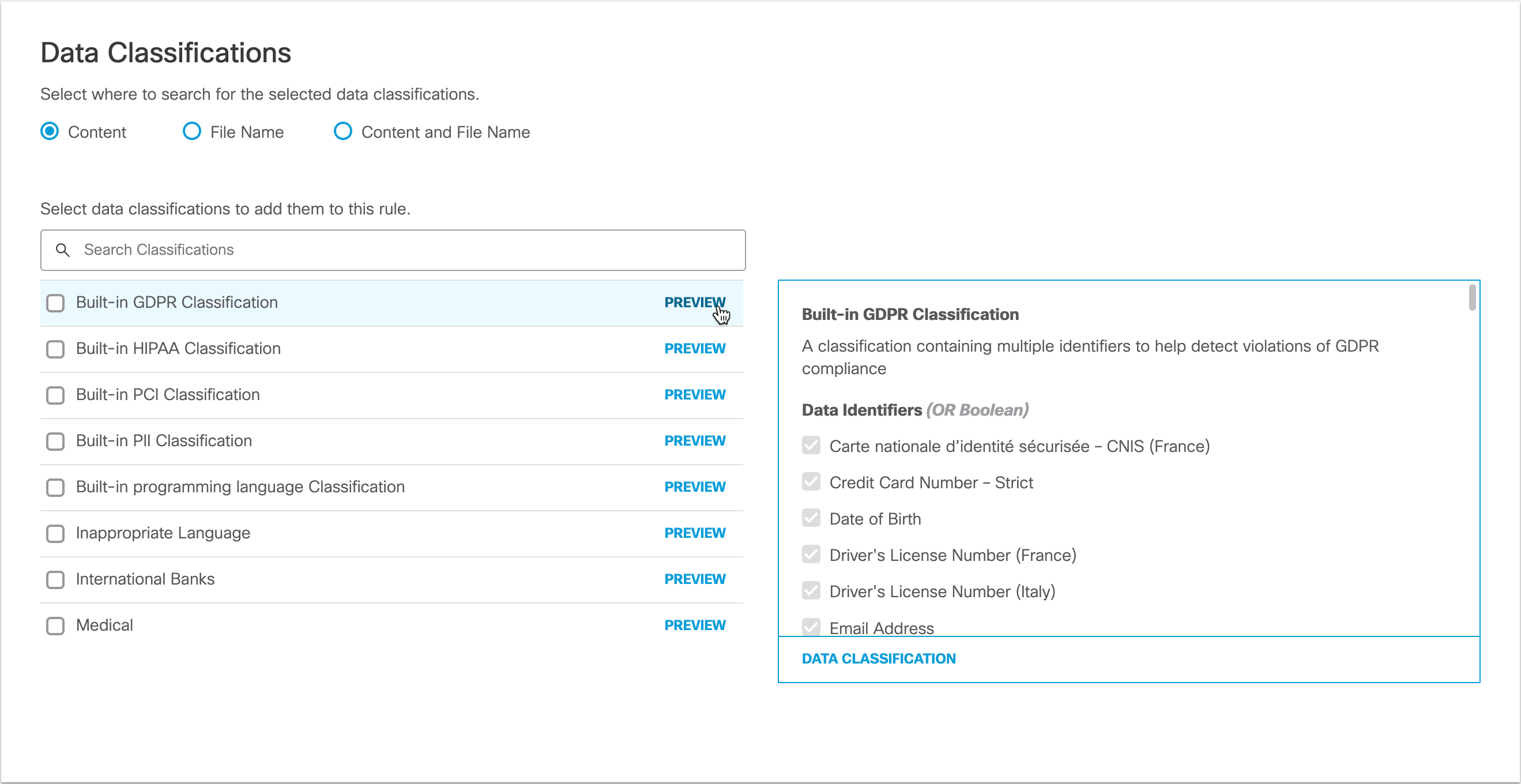
- Select where in uploaded files you would like this rule to search for the data classifications that you choose.

- Content—(Default) Searches only the content of files for the selected data classifications.
- File Name—Searches only file names for certain vetted applications. When vetted apps are included in All Destinations (See Step 8), the system attempts to identify file names but may not always succeed.
- Content and File Name—Searches content and file names for the selected data classifications. Both content and file name do not need to match for the rule to apply, only one or the other.
Note: Choosing Content, File Name, or Content and File Name refers to scanning file uploads for the selected data classifications and configured file labels.
- Select Data Classifications to apply this rule; you can choose a data classification of your own making, or a built-in data classification provided by Umbrella. (See Manage Data Classifications and Built-In Data Classification Templates.) Hover over PREVIEW to view data identifiers associated with each data classification.
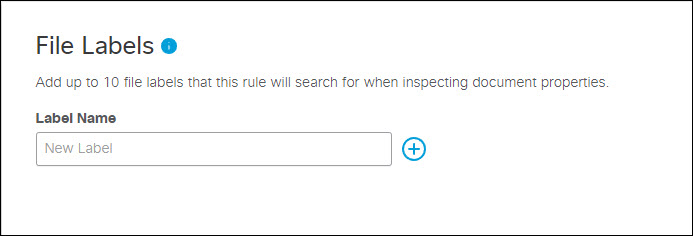
- Add up to 10 case-sensitive file labels to apply to this rule. The rule will search for any of the configured file labels in the value of the files' document properties. This includes Microsoft Office Document Properties, Microsoft Office Sensitivity Labels, and Adobe PDF Document Properties. File uploads to Confluence and Jira are not scanned for file labels.
Note: A DLP rule can be configured with either data classifications or file labels or both. When a DLP rule is configured with both, then a DLP event is raised when any of the selected data classifications and when any of the configured file labels are detected in the inspected file.
Microsoft Sensitivity Labels
Umbrella currently supports detection of Microsoft sensitivity labels in the file properties’ values of the inspected file for Microsoft Word, Excel, PowerPoint, and .pdf files. Ensure you configure the rule with the sensitivity labels, not the Display Names.
- Specify the Identities to apply to this rule:
- Select entire identity categories to include, or expand categories to select individual identities. Search for user name or by Group name. Selected identities will appear in the box on the right.
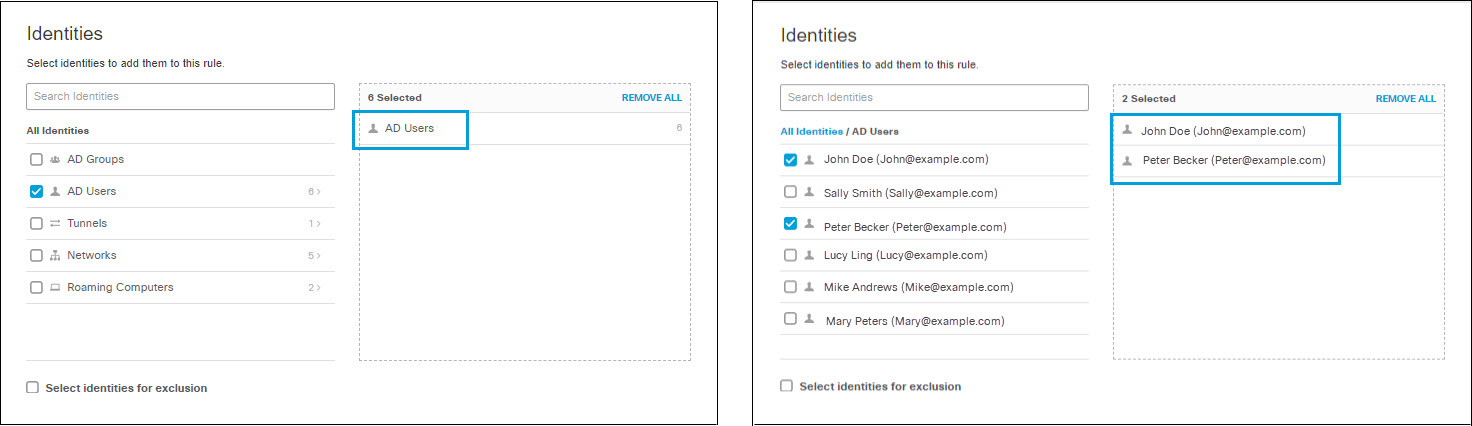
- Select Select identities for exclusion to exclude selected identities. Similarly to selecting identities for inclusion, you can select entire identity categories to exclude, or expand categories to select individual identities. Search for user name or by Group name. Selected identities will appear in the box on the right.
Note: Selecting empty identity categories for inclusion or exclusion has no effect on the rule until those categories become populated. Identities added to a category after the category has been included or excluded from a rule will be included or excluded from the rule as if they were members of the category at the time the rule was created.
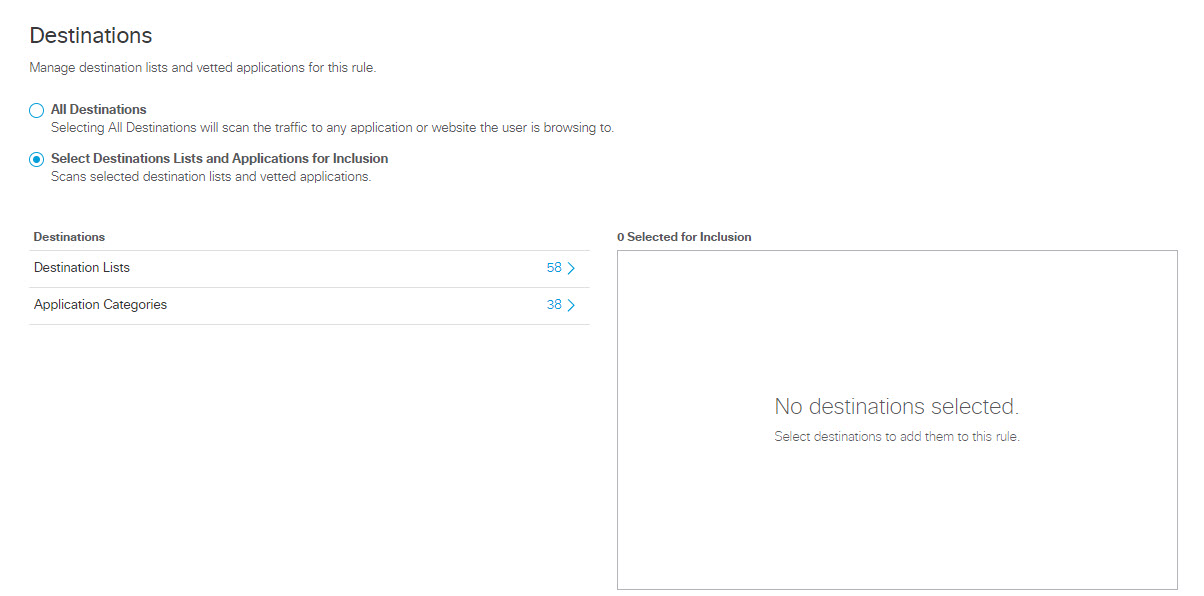
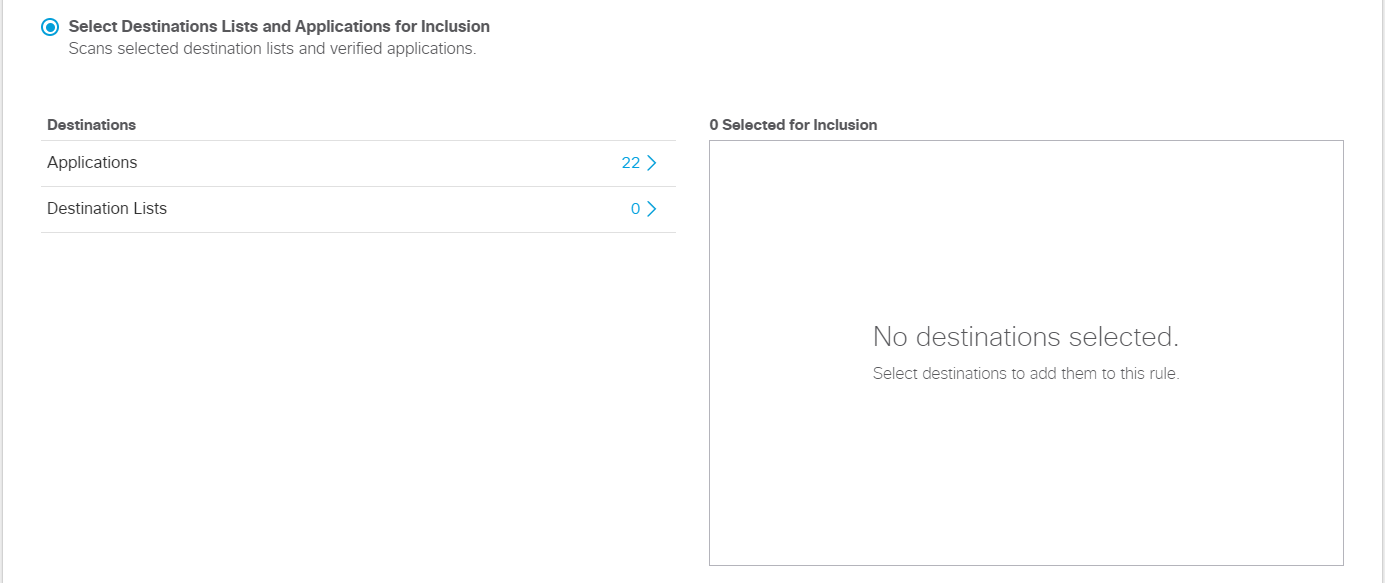
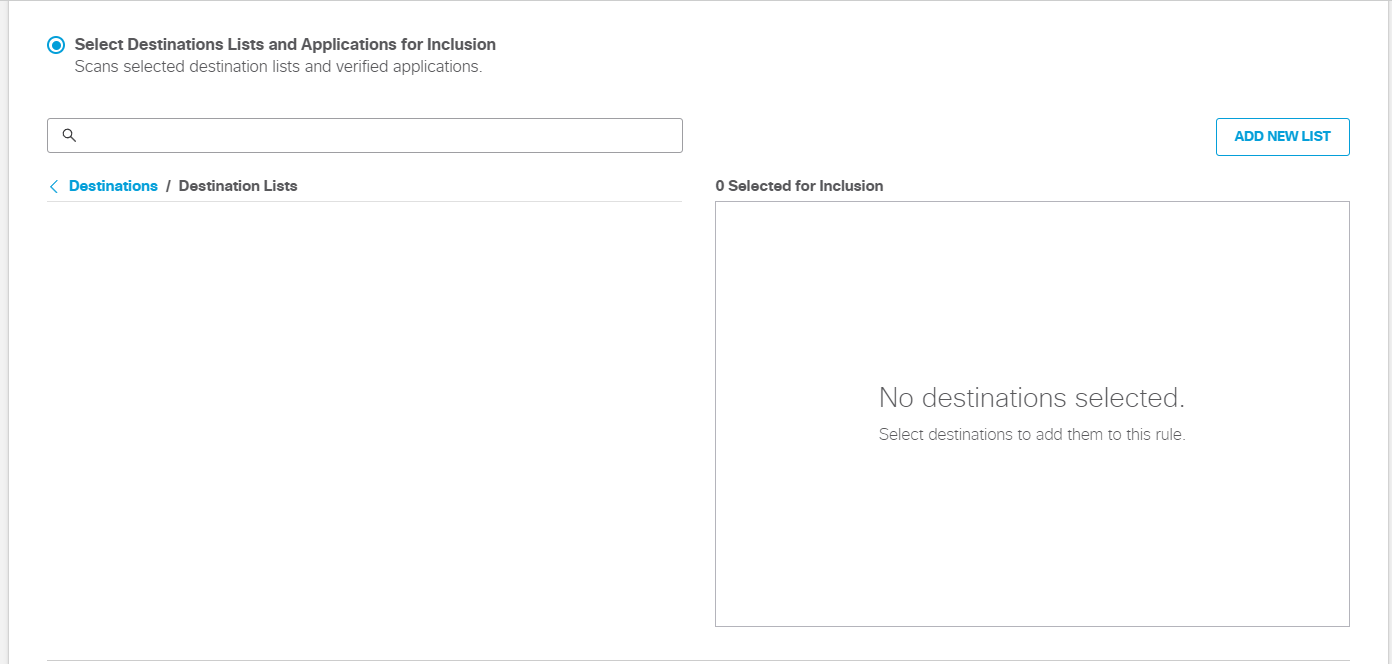
- Under Destinations, select All Destinations or Select Destination Lists and Applications for Inclusion.
- All Destinations—Monitors all outbound web requests or blocks all file uploads that originate from the selected identities for this rule.
- Select Destination Lists and Applications for Inclusion—Monitors all web requests and blocks all file uploads matching the identities selected on the rule, the selected destination lists, and supported applications.
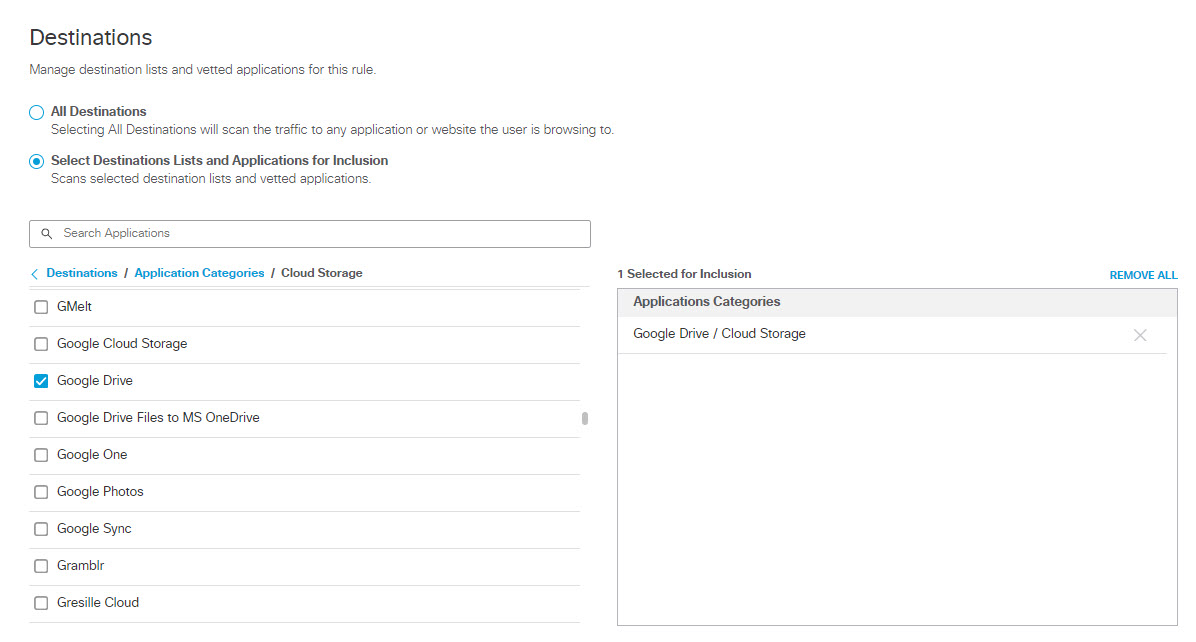
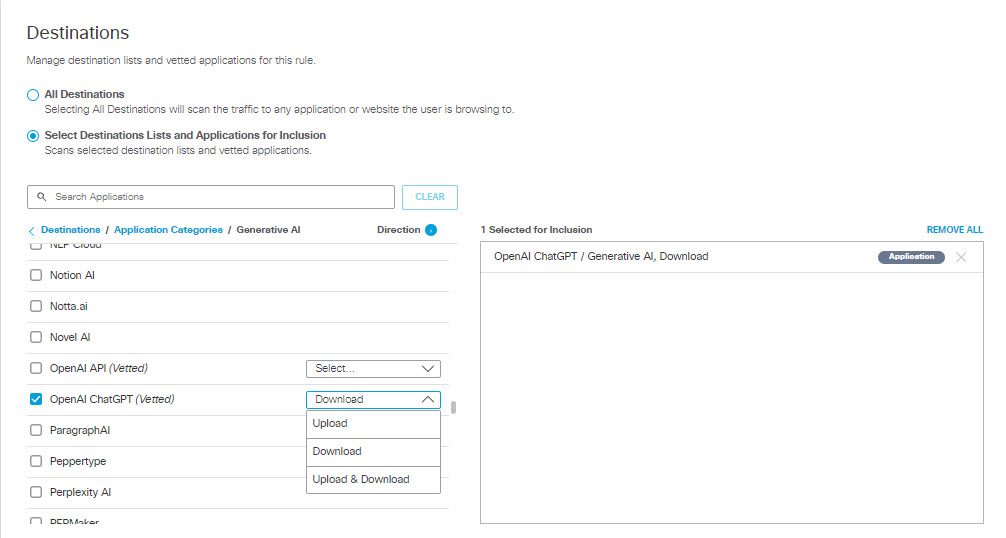
- To add applications for inclusion, under Destinations expand Application Categories. (See Application Categories) for a list of available categories.) Expand categories and check the boxes for the applications you want to add to the rule. You can search for an application by entering at least three consecutive letters from the application name in the search box.
Note: It is not possible to search for an application with fewer than three letters in its name—for example, "QQ" or "YY." These applications must be manually selected from the hierarchy under their respective categories, or wildcarded in search—for example, "QQ*". This behavior is by design.
- Note that for some applications (OpenAI API and OpenAI ChatGPT, for example) you can choose to scan any one of three traffic options: Upload (from your system to the application), Download (from the application to your system), or Upload & Download.
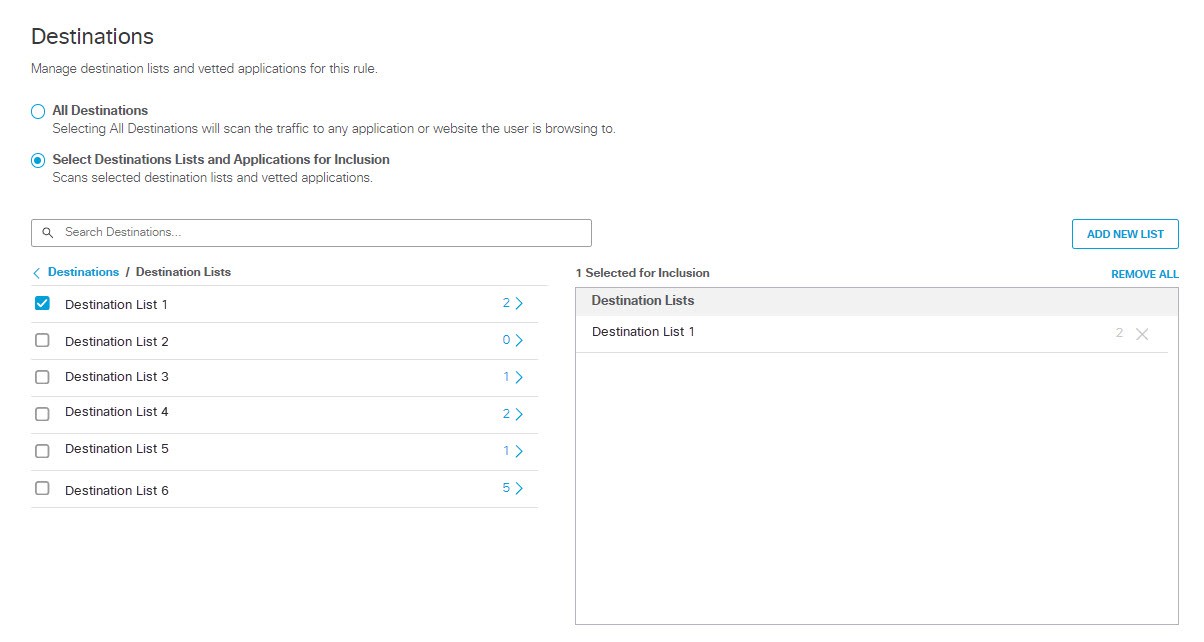
- To add destination lists for inclusion, under Destinations expand Destination Lists and check the boxes for the destination lists you want to add to the rule.
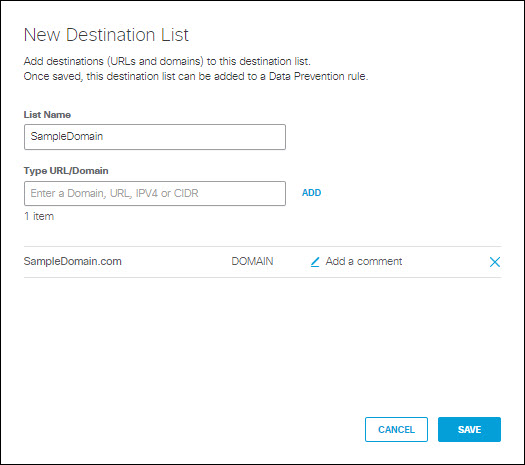
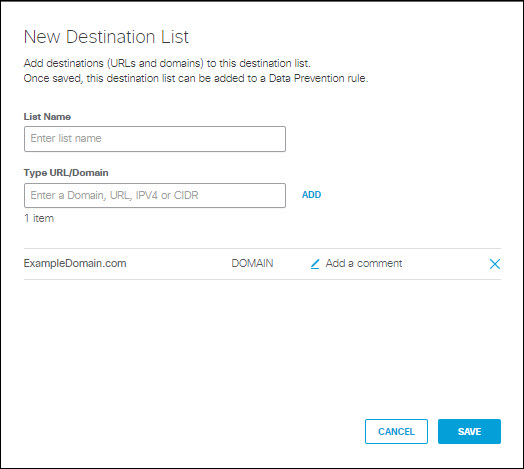
- To create a new destination list and add it for inclusion, under Destinations expand Destination Lists and click ADD NEW LIST. Under List Name enter a unique name for the list. For each URL/Domain to be in the list, enter a domain name, URL, IPV4 address or CIDR, and click Add. Click Save when done.
Note: Adding a new destination list to the rule here automatically adds it for inclusion.
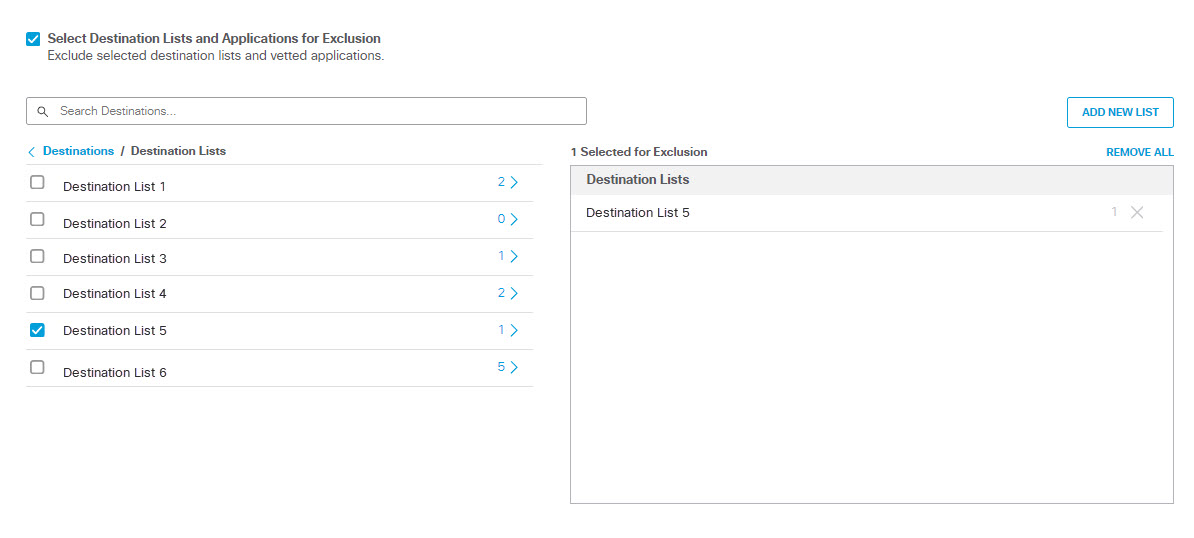
- Check the checkbox Select Destination Lists and Applications for Exclusion to select destinations and applications to exclude from this rule.
- To exclude applications, under Applications expand Destination Lists .
Note: It is not possible to search for an application with fewer than three letters in its name—for example, "QQ" or "YY." These applications must be manually selected from the hierarchy under their respective categories, or wildcarded in search—for example, "QQ*". This behavior is by design.
- To exclude destination lists, under Destinations expand Destination Lists and check the boxes for the destination lists you want to exclude from the rule.
- To create a new destination list and exclude it, under Destinations expand Destination Lists and click ADD NEW LIST. Under List Name enter a unique name for the list. For each URL/Domain to be in the list, enter a domain name, URL, IPV4 address or CIDR, and click Add. Click Save when done.
Note: Adding a new destination list to the rule here automatically adds it for exclusion.
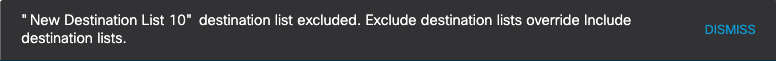
Note: When a destination list is selected for both inclusion and exclusion in a rule, it will automatically be excluded. Exclusion destination lists always override inclusion destination lists. Similarly, if a domain is included on an inclusion destination list and an exclusion destination list, the domain will be excluded.
- Under Action, from the drop-down list, choose Monitor or Block.
- Monitor—Monitor file uploads and data submitted in web forms.
The rule will search for content that matches supported workflows (See Supported Applications) and policy-configured destinations and identities. - Block—Block file uploads.
The rule will search for content that matches supported workflows (See Supported Applications) and the policy-configured destinations and identities. When content matches these workflows, the rule blocks the content.

Limited Availability
Umbrella can optionally block all password-protected files directed to destinations configured in the DLP rules. If enabled, this feature impacts all file types and all users and cannot be configured for finer granularity. This feature is not generally available; contact Umbrella Support to have it enabled in your account.
- Click Save.
Note: All fields must have options selected to save.
Manage the Data Loss Prevention Policy < Add a Real Time Rule to the Data Loss Prevention Policy > Understand Exclusions in a Real Time Rule
Updated about 1 year ago
