Provision Identities from Azure AD
Umbrella supports the provisioning of user and group identities from Azure Active Directory (Azure AD). You can provision users and groups from Azure AD through the Cisco User Management Connector Gov app in the Azure AD portal. Then, after provisioning your identities, view and manage the user and group identities in Umbrella.
User and group identities from Azure AD integrate with Umbrella DNS-layer security and Umbrella Secure Web Gateway (SWG) deployments. You do not need to deploy an on-premises Umbrella Active Directory Connector.
Umbrella DNS
- Enables user identity support for the Umbrella roaming client and AnyConnect Roaming Security module.
Umbrella SWG
- Enables user identity support for the AnyConnect SWG module.
- Provisions user and group identities for use with end-user SAML authentication.
Note: Azure AD does not store the private IP to AD user mappings. You must use an on-premises Umbrella AD connector for Virtual appliance (VA) or IP-to-user mapping deployments.
Table of Contents
- Prerequisites
- Limitations
- Procedure
- Configure Cisco User Management Connector Gov App in Azure AD Portal
- View Users and Groups in Umbrella
Prerequisites
- A valid Azure AD subscription with a premium Azure AD license.
- No concurrent provisioning of the same user or group identities from on-premises AD and Azure AD. If you are using the on-premises Umbrella AD Connector to import user and group identities to Umbrella, and choose to import the same identities from Azure AD, ensure that the on-premises Umbrella AD connector is switched off or that the OpenDNS Connector service on the connector machine is stopped.
Note: Concurrent synchronization of the same user and group identities from the Umbrella AD Connector and the Cisco Umbrella Azure AD app is not supported and leads to inconsistent policy enforcement. - Import of the ObjectGUID attribute from Azure AD to Umbrella. The on-premises Umbrella AD Connector and Cisco AnyConnect and Umbrella roaming clients rely on the ObjectGUID attribute for user identification. If all of your endpoints are running the Cisco Secure Client/AnyConnect version 4.10 MR6 or above, you do not have to import the ObjectGUID attribute from Azure AD.
- Before you set up the import of the ObjectGUID attribute, ensure that the on-premises Umbrella AD Connector that is synchronizing these identities is switched off or that the OpenDNS Connector service on the connector machine is stopped.
- To ensure that the ObjectGUID attribute for users is synchronized from Azure AD to Umbrella, your endpoints must authenticate against on-premises AD and run the Cisco AnyConnect agent or Umbrella roaming client. For more information about how to import the ObjectGUID attribute for users, see Tutorial: Configure Cisco Umbrella User Management Gov for automatic user provisioning..
- Full admin access to the Umbrella dashboard. For more information, see Manage User Roles.
Note: If you previously configured a policy against groups imported from on-premises AD, and then choose to import the same groups from Azure AD, you must reconfigure the policy to map it to the Azure AD groups instead of the on-premises AD groups. In a policy, on-premises AD group names are displayed with the domain name preceding the group name, for example: Domain1\ADGroup1. For Azure AD, only group names are displayed on the policy page, for example: ADGroup1.
Limitations
- You can provision no more than 200 groups from Azure AD to Umbrella. Umbrella supports the provisioning of an unlimited number of users from Azure AD to Umbrella.
- To ensure that all users are provisioned, create a dynamic All Users group and assign this group to the Cisco User Management Connector Gov app. For more information, see Dynamic Membership Rules for Groups in Azure Active Directory. You can assign additional groups as required for group-based Umbrella policy enforcement.
- After the initial provisioning of users and groups, Azure AD synchronizes changes to Umbrella once every 40 minutes. Synchronization of updates to identities from Azure AD to Umbrella may take up to one hour.
- The number of users and groups that you import may effect when the identities become available in Umbrella.
Note: Azure AD does not support nested group memberships for group-based assignment to any SaaS application.
Procedure
- Navigate to Admin > API Keys.
- Click Static Keys and expand Azure Active Directory Provisioning.
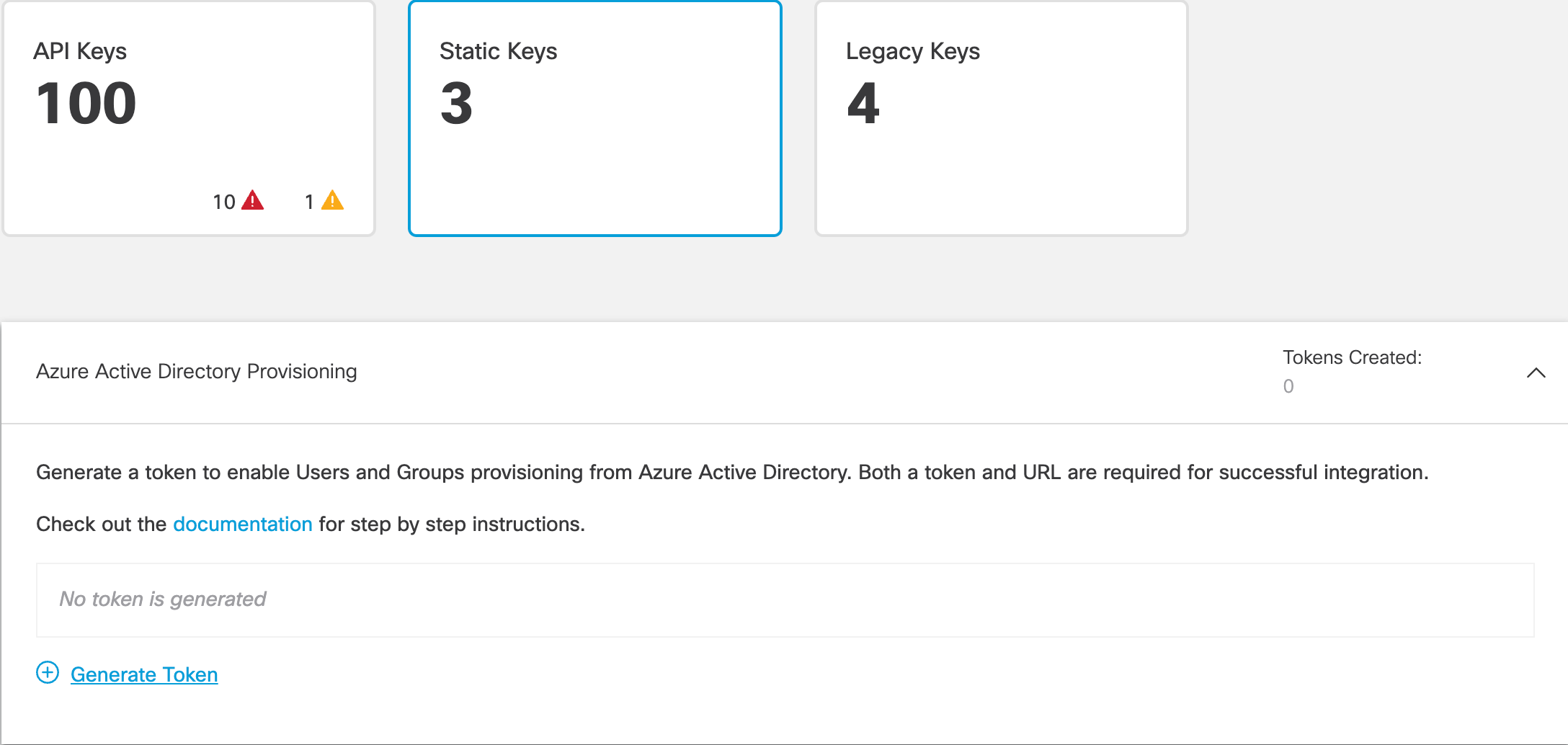
- Click Generate Token.
- Copy and save your generated token.
- Copy and save the Azure Active Directory Provisioning URL,
https://api.umbrellagov.com/identity/v2/scim'.
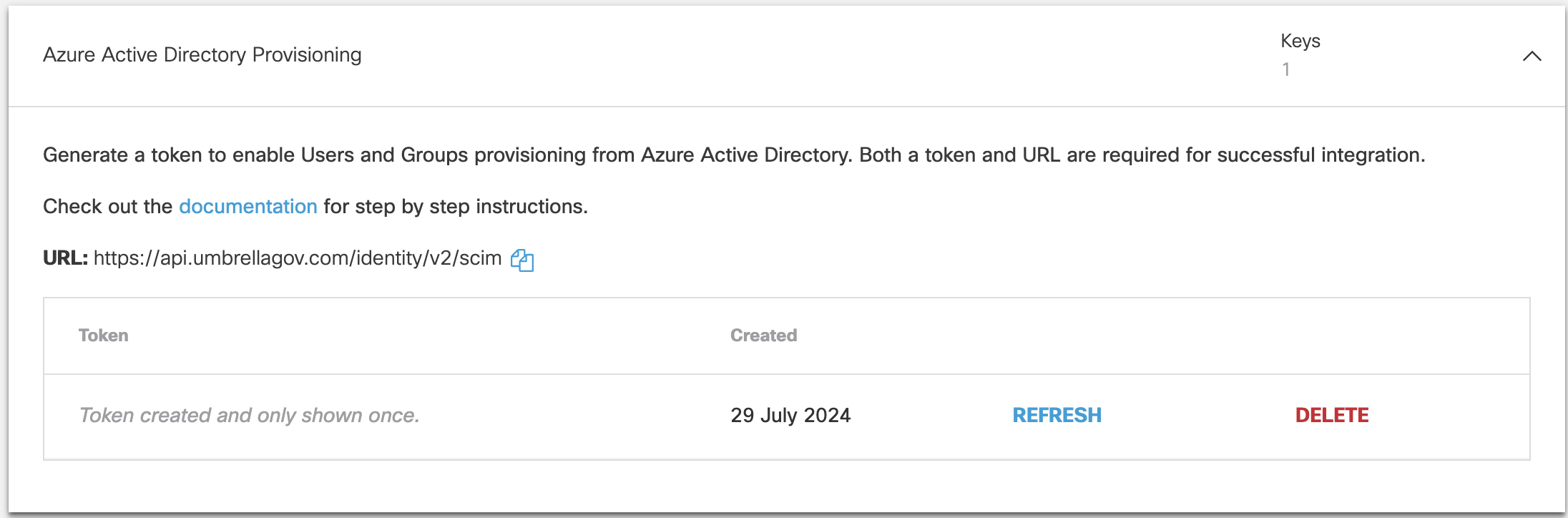
Note: We recommend that you refresh your token at least once every 180 days. To ensure that provisioning of users and groups is not impacted, immediately copy your new token to the Cisco User Management Connector Gov app in the Azure AD portal.
Configure Cisco User Management Connector Gov App in Azure AD Portal
With your Umbrella token and Azure Active Directory Provisioning URL, set up the Cisco User Management Connector Gov app in the Azure AD portal and provision user and group identities. For more information, see Tutorial: Configure Cisco Umbrella User Management Gov for automatic user provisioning..
- Navigate to the Cisco User Management Connector Gov app in the Azure AD portal.
- Add your token to the Secret Token field.
- Add the Azure Active Directory Provisioning URL to the Tenant URL field.
View Users and Groups in Umbrella
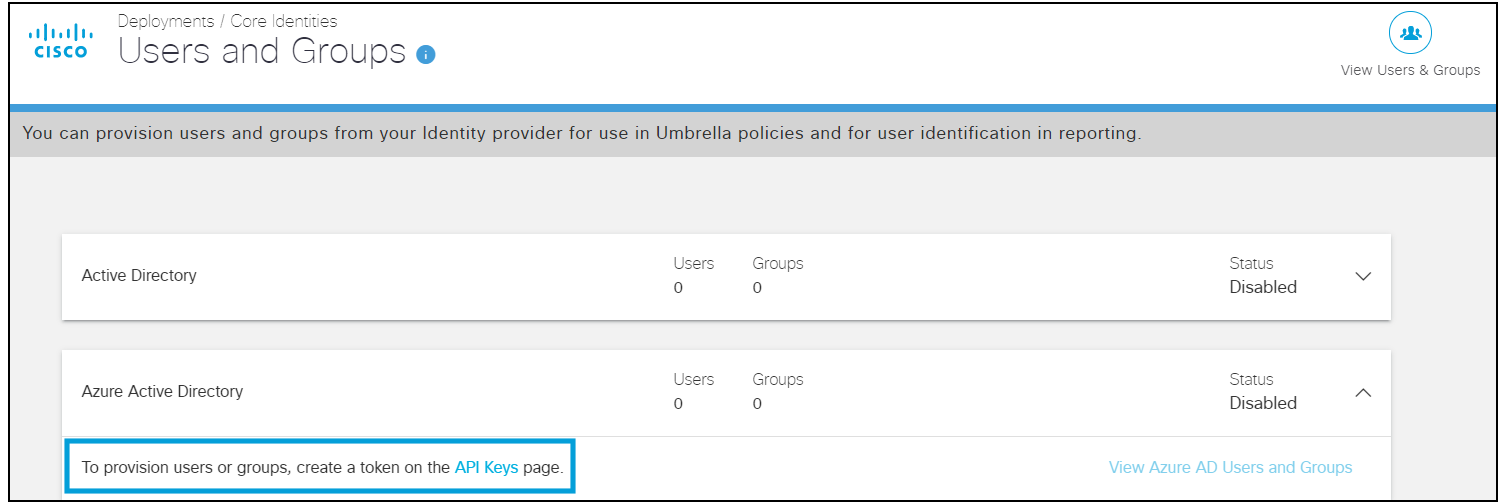
- Navigate to Deployments > Users and Groups to view the users and groups provisioned from Azure AD.
Provision Identities Through Manual Import < Provision Identities from Azure AD > Provision Identities from Okta
Updated about 1 year ago
