Configure SAML Integrations
SAML single sign-on (SSO) authentication for logging into the Umbrella for Government dashboard is a separate topic. For information on configuring SAML SSO, see Get Started with Single Sign-On.
Because Umbrella for Government is not an open proxy, Umbrella for Government must trust the source forwarding web traffic to it. This can be accomplished by assigning either a Network or Tunnel identity to a ruleset of the Web policy. Rulesets created in this fashion apply broadly to any web traffic originating from the network or tunnel. However, to create more granular policies for users or groups, SAML can be implemented.
gateway.id.swg.umbrellagov.com must be sent to the Umbrella secure web gateway (SWG) and not sent directly to the internet.
Identities obtained from SAML can be matched to users and groups which have been provisioned by manually importing a CSV file from Active Directory (AD), or automatically by using AD-based provisioning with the Umbrella AD Connector or by synchronizing and provisioning from IDPs like Okta, Azure, and so on.
Note: User identity attribution can be configured using Active Directory, Azure AD, or Okta. For more information, see User and Group identities from Azure AD or Okta.
SAML Identities and the Web Policy
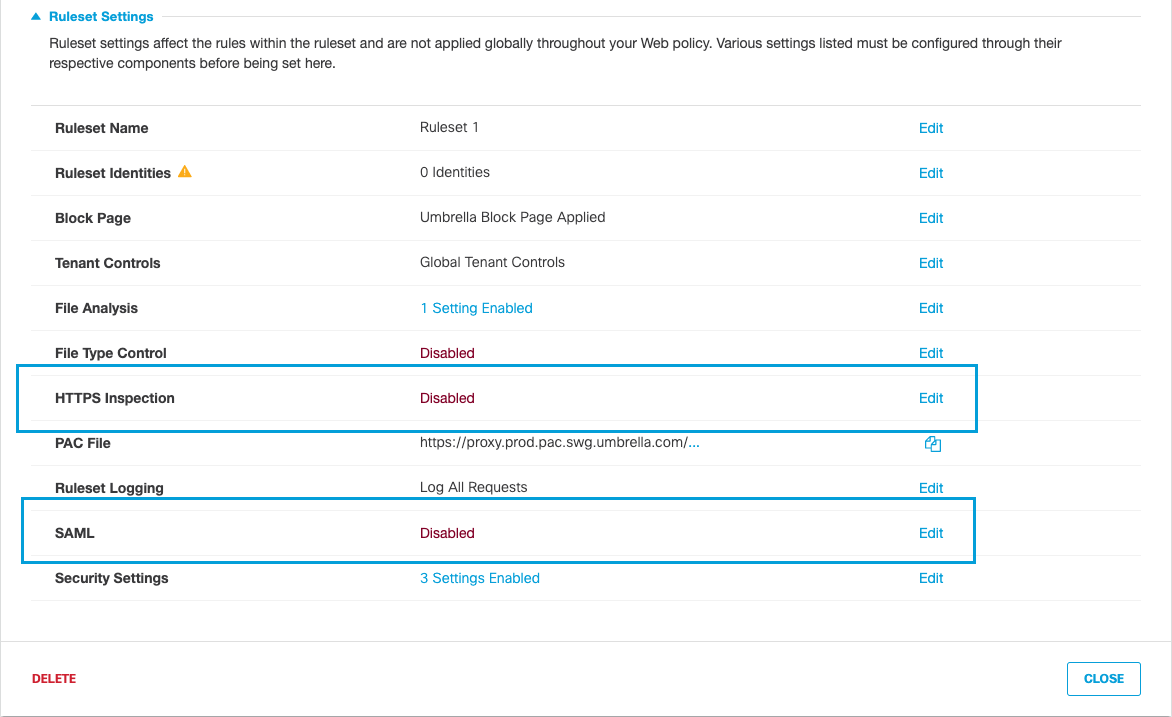
When configuring a ruleset for the Web policy to obtain the identity through SAML, you must enable SAML and HTTPS inspection. HTTPS Inspection is required because Umbrella needs to see into HTTPS packets for the SAML cookie acting as the authentication token/surrogate. Umbrella also requires that you install a root certificate on all client machines egressing from networks or tunnels where SAML is enabled. For more information about the Web policy, see Add a Ruleset to the Web Policy.
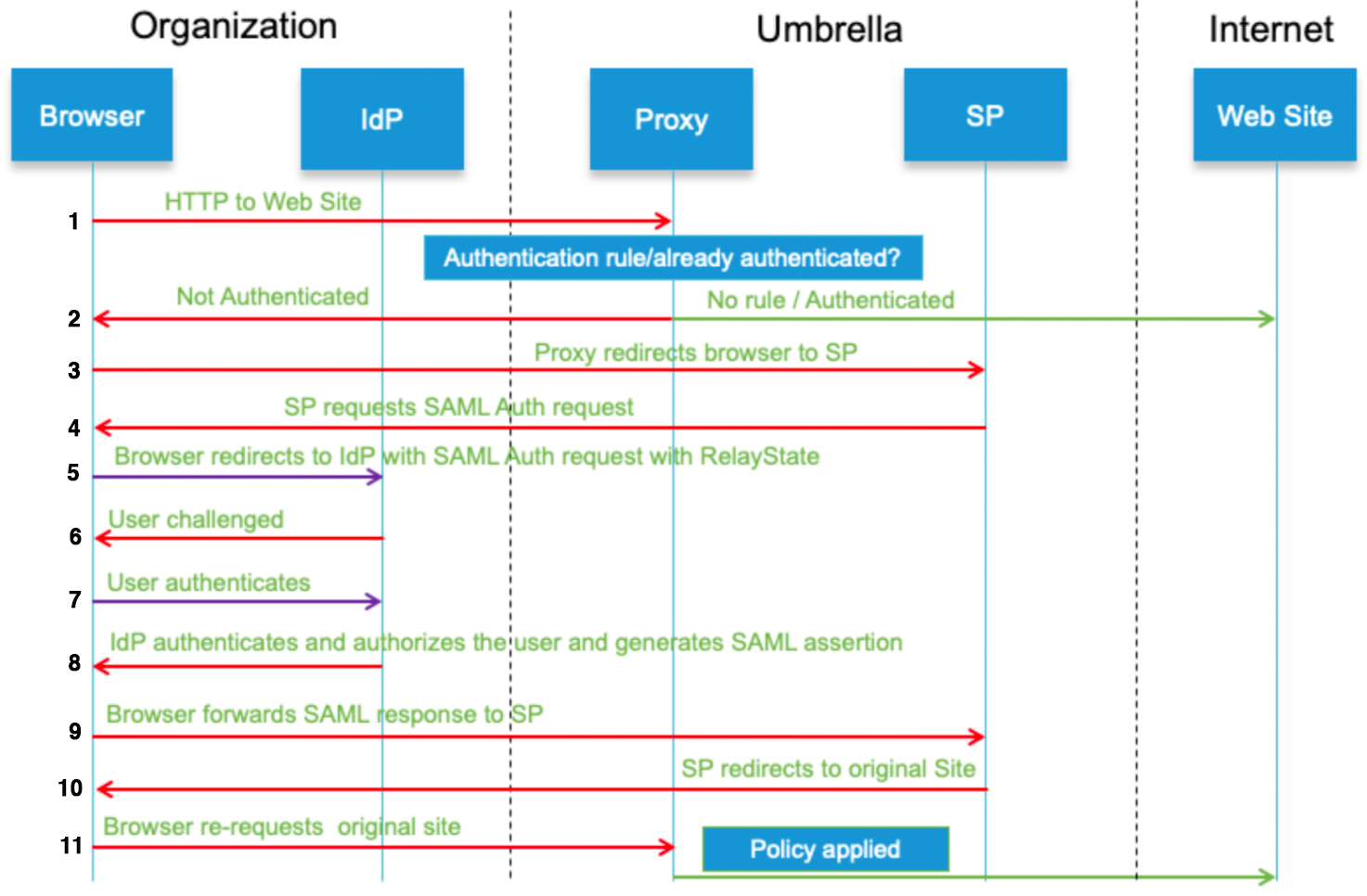
SAML Data Flow
Introduction < Configure SAML Integrations > Prerequisites
Updated about 1 year ago
