Configure Duo Security for Cisco Umbrella SAML
Duo Security for SAML configuration can be authenticated in one of the following ways:
- Upload the identity provider's (IdP) metadata file
- Manually configure IdP fields
Table of Contents
- Prerequisites
- Configure Cisco Duo Single Sign On (SSO) Application
- Configure Cisco Umbrella for SAML with Metadata Upload
Prerequisites
- Cisco Duo Single Sign On (SSO) must be enabled and configured. For more information, see Duo Single Sign-On.
- id.swg.umbrellagov.com must be sent to the Umbrella secure web gateway (SWG) and not sent directly to the internet.
- SAML metadata must have a signing key.
- Ensure that your IDP Endpoint—the URL used to communicate with your identity provider—bypasses the Umbrella proxy to avoid an authentication loop.
- Configure SAML with your identity provider (IdP) that supports SAML 2.0 POST profiles.
- Download your IdP's metadata file in XML format.
- Enable cookies for your browser.
- Enable SAML and HTTPS inspection on a Ruleset that includes the Network and Tunnel identities from which the user traffic arrives.
Configure Cisco Duo Single Sign On (SSO) Application
- Log in to the Duo admin portal, navigate to Applications, and click Protect an Application.
- Search for Cisco Umbrella (End Users) with the protection type 2FA with SSO hosted by Duo (Single Sign-On).
- Click Protect to start configuring Cisco Umbrella (End Users).
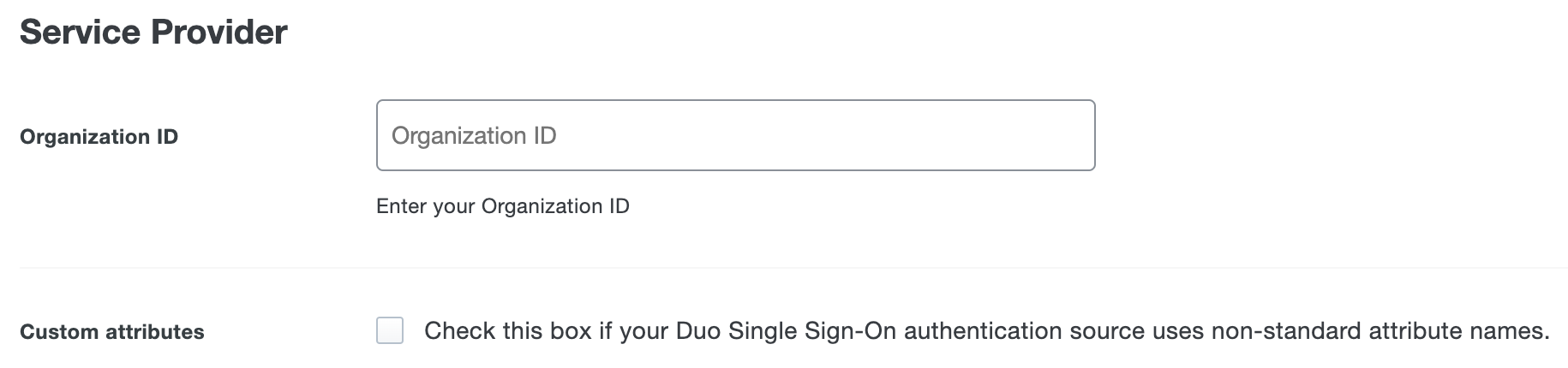
- Umbrella uses the Mail attribute, Username attribute, First name attribute, Last name attribute, and Display name attribute when authenticating. Duo allows you to choose either Active Directory or a SAML Identity Provider as your Duo Single Sign-On supported authentication source attributes. Configure Umbrella using your chosen Duo SSO supported authentication source attributes, which can be mapped to the Bridge Attributes as follows:
| Bridge Attribute | Active Directory | SAML IdP |
|---|---|---|
| <Display Name> | displayName | DisplayName |
| <Email Address> | ||
| <First Name> | givenName | FirstName |
| <Last Name> | sn | LastName |
| <Username> | sAMAccountName | UserName |
- If you are using non-standard attributes for your authentication source, check the Custom attributes box and enter the name of the attributes you wish to use instead.
- You can adjust additional settings for your new SAML application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy.
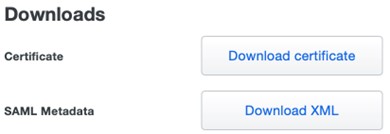
- Navigate to Downloads and click Download XML to download the Duo Security XML file.
Configure Cisco Umbrella for SAML with Metadata Upload
- Navigate to Deployments > Configuration > SAML Configuration and click Add.

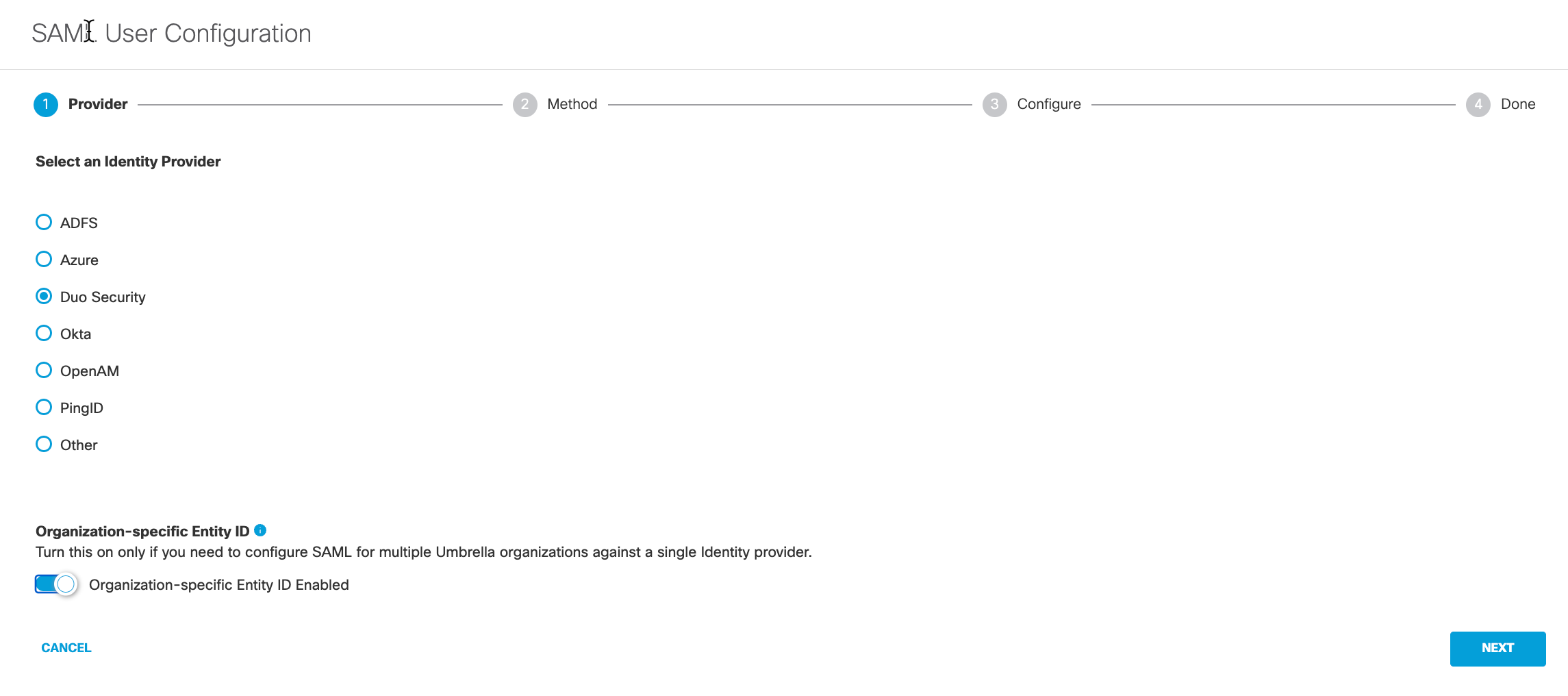
- Click the Duo Security radio button, toggle the Organization-specific Entity ID Enabled button to enable the entity ID, then click Next.
- Click the XML File Upload radio button, and then click Next.
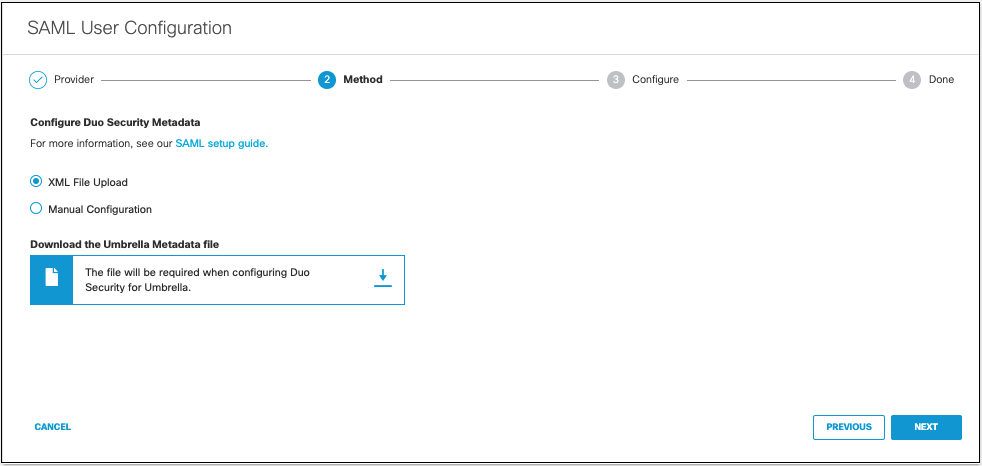
- Upload your Duo Security metadata file in XML format and click Next.
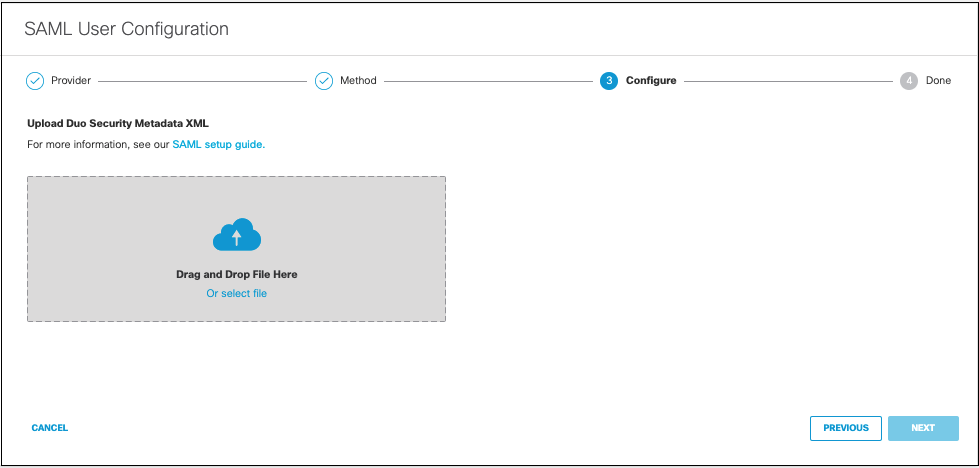
-
Choose how often Umbrella re-authenticates the users from the Re-authenticate Users drop-down list. Make sure Daily is selected.
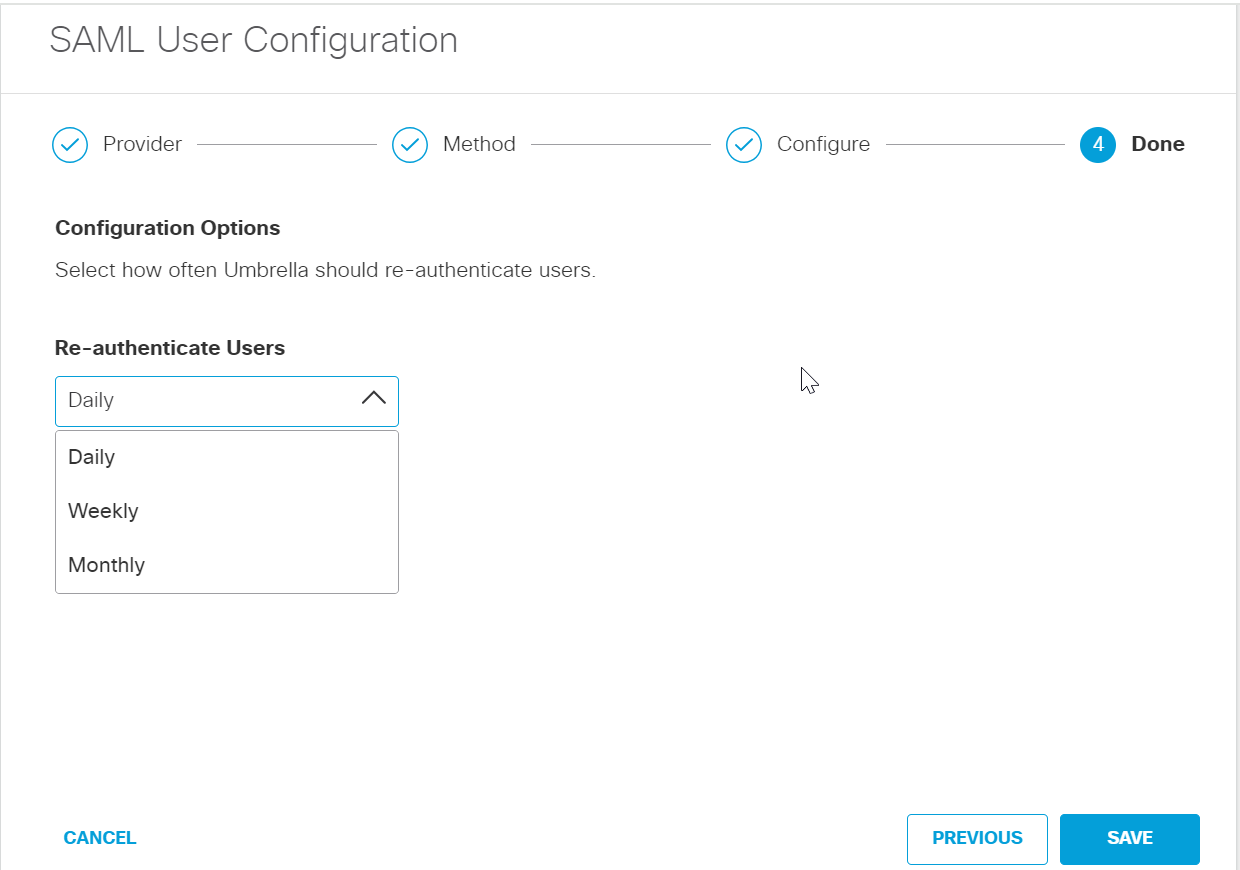
-
Click Save. Your new configuration appears as SAML Web Proxy Configuration.
Configure AD FS for SAML < Configure Duo Security for Cisco Umbrella SAML > Configure PingID for SAML
Updated about 1 year ago
