Web Policy Precedence
A Web policy consists of rulesets in which you can add identities and rules, and configure security settings. You can design any number of rulesets and rules to match the network entities, users, and groups in your system.
This guide describes how Umbrella selects a Web policy ruleset and applies a Web policy rule to an identity and a destination.
Table of Contents
Web Policy Rulesets
A Web policy ruleset defines a collection of identities and rules. Rulesets can include identities from a specific geographic area or physical office location, or from a group of networks, users, or roaming computers. Umbrella selects a ruleset from your list of rulesets by matching an identity associated with the requested web destination.
Add Identities to a Ruleset
You can add the following types of identity to a Web policy ruleset:
- Active Directory (AD) user
- Active Directory (AD) group
- Roaming Computer (MacOS or Windows)
- Internal Network
- Network Tunnel
- Network
For more information about identities, see Manage Identities.
Configure Security Settings
You can configure the following security settings within a Web policy ruleset:
- Block Page
- File Type Control
- HTTPS Inspection
- PAC File
- SAML
- Security Categories
- Tenant Controls
- Ruleset Logging
Set Up Rulesets
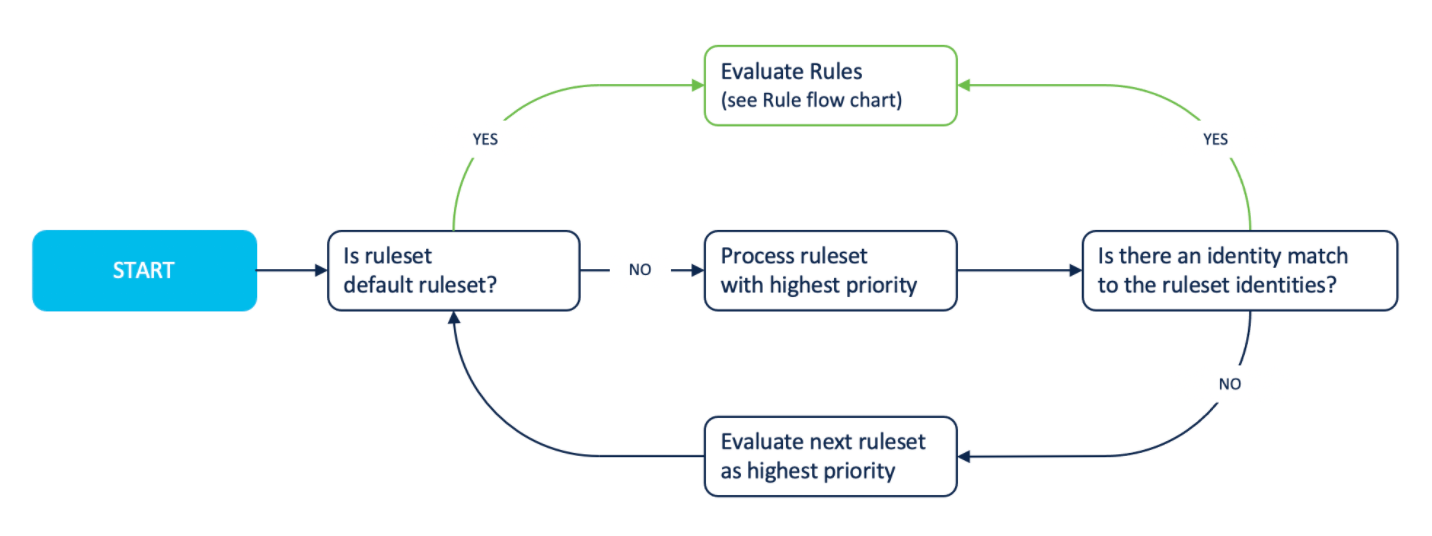
After you add a ruleset to your list of Web policy rulesets, you can set the priority for the ruleset. List your highest priority ruleset first. Umbrella evaluates the list of rulesets in descending order.
Note: If a matching identity is not found in any of your rulesets, Umbrella uses the Default Web policy ruleset.
Match an Identity to a Ruleset
When you send traffic from a network entity, user, or group, Umbrella checks for any matching identities in your Web policy rulesets. If a ruleset matches at least one of the identities associated with the web traffic, Umbrella selects the ruleset.
Example of related identities associated with a destination request:
- Active Directory (AD) user
- Active Directory (AD) group
- Network (public IP address)
To select a primary identity, Umbrella evaluates the identities associated with a destination request from most granular to least granular:
- Active Directory (AD) user
- Active Directory (AD) group
- Roaming Computer
- Network or Network Tunnel
Example of selecting the primary identity:
Umbrella checks the highest ranked ruleset for the Active Directory (AD) user and Network Tunnel identities. If the first ruleset does not match the AD user identity but matches the Network Tunnel identity, Umbrella selects the ruleset and assigns the Network Tunnel as the primary identity. The Umbrella reports display the Network Tunnel identity as the primary identity and the AD user as the secondary identity.
Note: The Umbrella reports log information for all identities selected by a Web policy ruleset, but only highlight the primary identity.
When roaming with AnyConnect on another Umbrella org's network, only the policies of the AnyConnect org will be evaluated. The traffic will also only be logged on the AnyConnect org.
Active Directory User Identity Source
In Umbrella, the Security Assertion Markup Language (SAML) Group or the AnyConnect Secure Roaming Client provides the identity of the Active Directory (AD) user.
Active Directory user identity providers:
- SAML
- SAML IP surrogate
- AnyConnect Secure Roaming Client
- Web Security Appliance
Note: The Umbrella Activity Search report lists the Active Directory user identity in the user identity source field.
Web Policy Rules
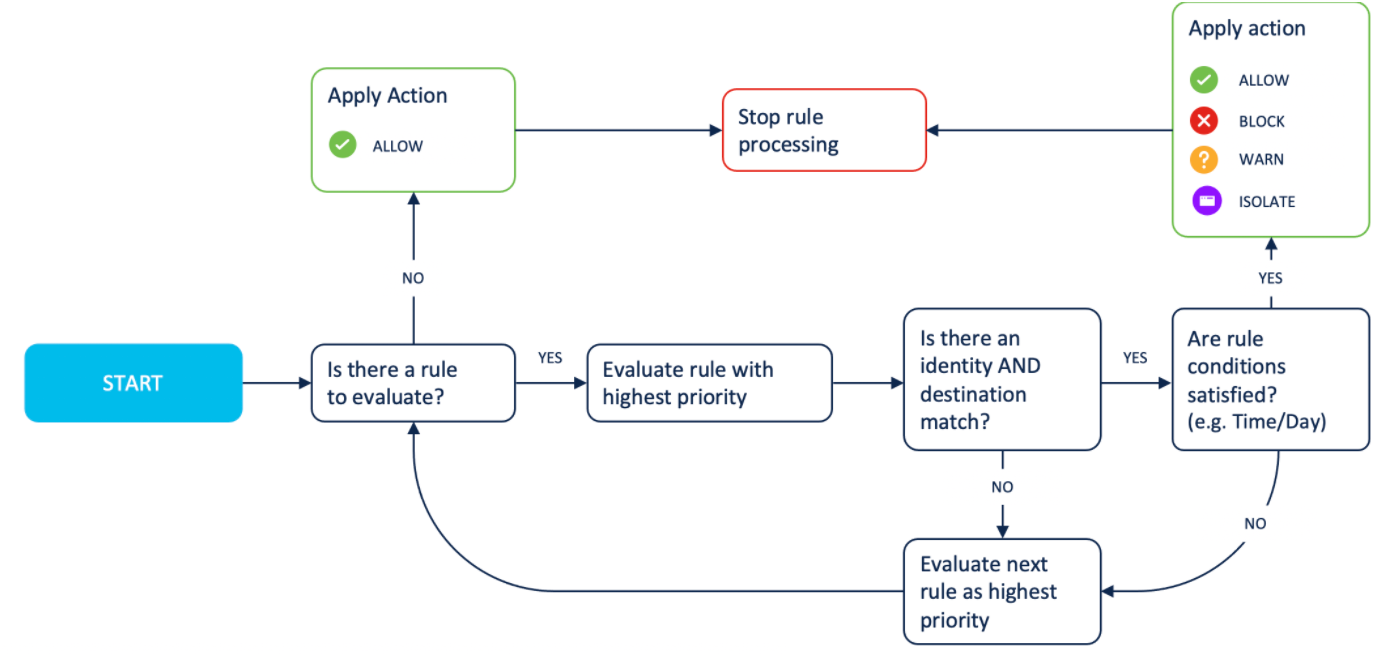
A Web policy rule is a collection of actions, destinations, and identities. You can define a Web policy rule and add a rule to a Web policy ruleset. List your highest priority rule first in your ruleset. Within a selected ruleset, Umbrella evaluates each rule in descending order. If Umbrella cannot match an identity and destination to a rule, Umbrella applies the security settings defined in the ruleset.
Note: The Umbrella Activity Search report logs information about the Web policy ruleset and rule applied for an identity and the requested web destination.
Add Destinations
Destinations are found in destination lists, represent web applications, or host types of web content category. A destination is either a URL, domain, IP address, or CIDR IP address. Within a rule, you can add content categories and configure application settings. You can also set up lists of destinations and assign access controls to each destination list.
Define Actions
For each destination, select a Web policy action. A Web policy action defines the type of access control that you want to enforce for a destination.
You can select the following actions in a rule:
- Allow
- Block
- Warn
- Isolate
Apply Web Policy Rule
When a rule matches an identity and destination, Umbrella applies each action associated with a destination list, content category, security category, or application.
Umbrella applies these action and destination combinations within a rule:
- Destination lists, Allow. If SSL decryption enabled, evaluate newly seen URL content. Apply antivirus and malware (Cisco Advanced Malware Protection (AMP)) checks.
- Destination lists, Block.
- Application, Allow. Apply antivirus and malware (Cisco Advanced Malware Protection (AMP)) checks.
- Content categories, Allow.
- Application, Block.
- Content categories, Block.
- Security categories, Block.
- Application, Warn. Display Warn Block Page. Apply antivirus and malware (Cisco Secure Endpoint (AMP)) checks.
- File type control, Allow (HTTPS file inspection, optional SSL Decryption).
- File type control, Block.
Test the Web Policy < Web Policy Precedence > Best Practices for the Web Policy and Rulesets
Updated about 1 year ago
