Active Directory Federation Services (ADFS) SAML Setup Guide
Cisco Cloudlock can integrate with many SAML (Security Assertion Markup Language) providers in order to provide single sign-on (SSO). While Cisco Cloudlock provides direct support for SAML providers such as Okta, OneLogin and PingOne, SAML is sufficiently open that other vendors’ offerings can be integrated as long as they satisfy the parameters below.
#Prerequisites
- The administrator configuring the SAML SSO must have an OAuth authorization for logging in to Cisco Cloudlock.
- Each user authenticating into CloudLock using SAML SSO must have the same identity in Cloudlock and the SAML Identity Provider (IDP).
- The response from the IDP must be completely signed. Simply signing the assertion component of the response is not sufficient.
- Two parameters are required to be included in the in the application: SAML_SUBJECT and emailAddress. Both values must point to the emailAddress field from the SAML IDP.
- The ACS URL and entity id are same and are in the following format: https://{cloudlockdomain}/gate/saml/sso/{customerdomain}, where {cloudlockdomain} can be platform.cloudlock.com or app.cloudlock.com. The {customerdomain} must be controlled by an organization that is registered with cloudlock.
Configuration
While the specific configuration steps differ for every SAML provider, the broad outline of the process is generally the same:
- Log into the SAML provider and identify Cisco Cloudlock as an application to be integrated.
You will typically need the Cisco Cloudlock URL your organization has been assigned. - Identify the user accounts that will be used to log into Cisco Cloudlock.
- Copy the required metadata from the SAML provider’s console.
You will paste this information into Cisco Cloudlock. - Log into Cisco Cloudlock using your default OAuth authorization.
- Open the Settings page > Authorization & API tab and enter the IDP metadata and URL as indicated.
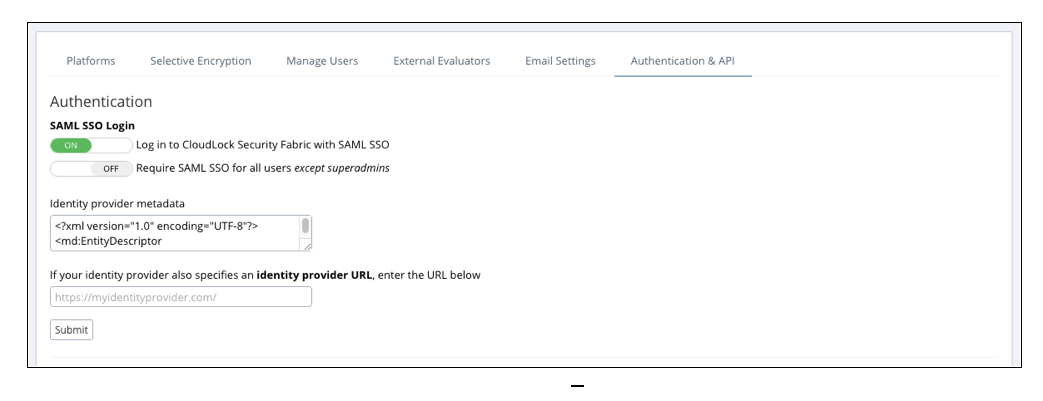
- Select Submit.
The SAML configuration process is generally complete at this point.
Updated about 3 years ago
