Events Analysis
Events Analysis policies monitor User Events and Behavior Analytics (UEBA) in the environment. This can include logins and logouts, downloading, copying or deleting files, or changing settings or profile information. Different criteria within the Events Analysis policy configuration allow for many Events Analysis policies to coexist in an environment and monitor similar but different behavior. For example, if you wanted to monitor general login failures across the board for all users in the environment but also monitor login failures for a specific location, you would create two separate policies to monitor both scenarios.
Configuration
Platform
The platforms in which you wish to monitor UEBA activities.
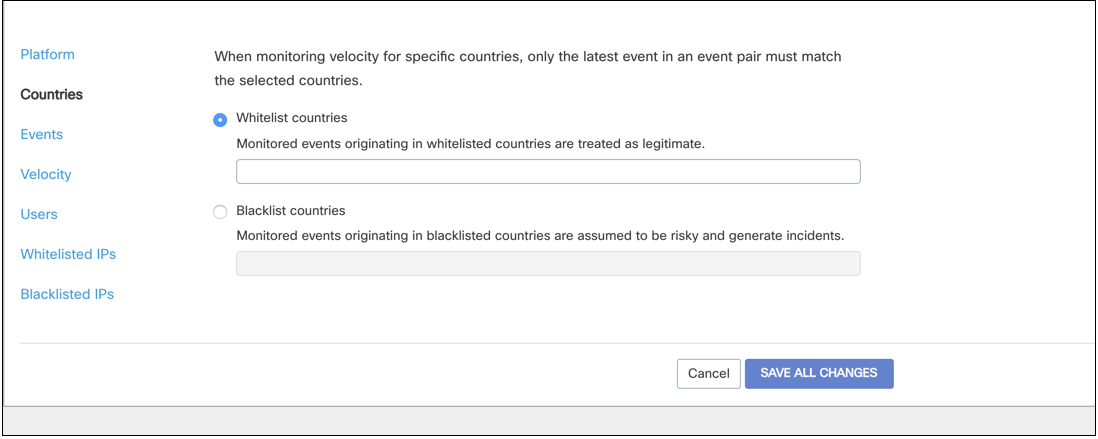
Countries
This section enables you to decide which countries are considered trusted (allow list) and which are risky (risk list). Countries on the allow list are considered valid and do not trigger incidents. Countries that are on the risk list trigger incident for events that occur in those countries.
To add countries to the allow list, select Allow-list countries and type in the name of any trusted countries.
To add countries to the risk list, select Risk-list countries and type in the name of any suspicious countries to generate incidents.
Velocity
When velocity is measured in a UEBA policy, only the latest of the two events are checked against the trusted and risky lists for a match.
Events
Choose the specific events you wish to monitor: platform (normalized) events, platform raw events, or events by threat category. You can also choose to monitor all events, all events with some exclusions, or to only monitor specific events.
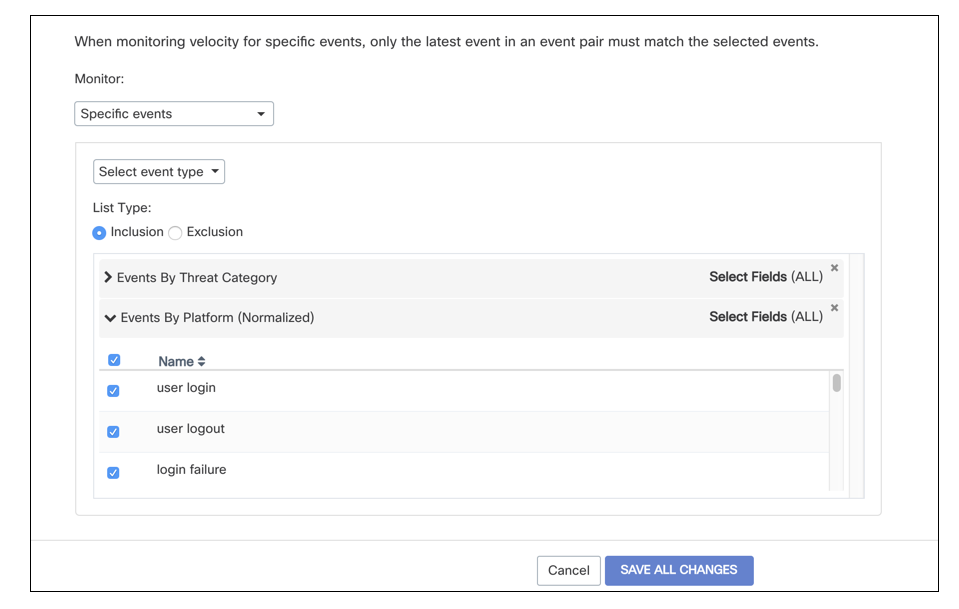
Velocity
Only the latest of a pair of events will be checked against the chosen events when monitoring for velocity. For example, if measuring for velocity and only "logins" are selected as monitored events, any event that might violate velocity that is not a login will not trigger an incident.
Velocity
When velocity is enabled in a policy it monitors pairs of events that occur over a large distance for each user to validate user activity. When a pair of events with a significant difference occurs in a short period of time with the same user, an incident is triggered.
For example:
A user logs into their org in San Fransisco, California at 1 pm. Two hours later at 3 pm, the same user logs in from Hong Kong, China. Because the user cannot possibly have been in both locations within two hours of one another, an incident is triggered.
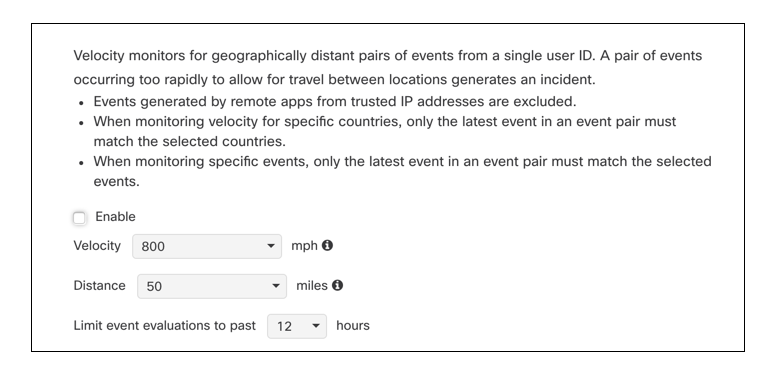
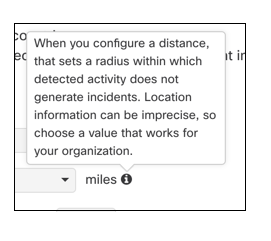
There are default settings for the velocity, distance, and range of time the events should be analyzed, however, these fields are all editable.
Users
You can select to monitor events of all users, all users with some exceptions, or only specific users, OUs, or Groups.
Trusted IPs
You can enable the Trusted IP Library so that activities that take place at listed IP addresses will not trigger an incident. You can choose to include the entire library or only selected IPs from the list.
Risky IPs
You can enable the Suspicious IP Library so that activities that take place at listed IP addresses will trigger an incident. You can choose to include the entire library or only selected IPs from the list.
Threshold
The threshold enables you to detect when a number of events have occurred within a selected time frame. For example, you may want to create an incident if an event occurs three times within an hour (such as attempted logins).
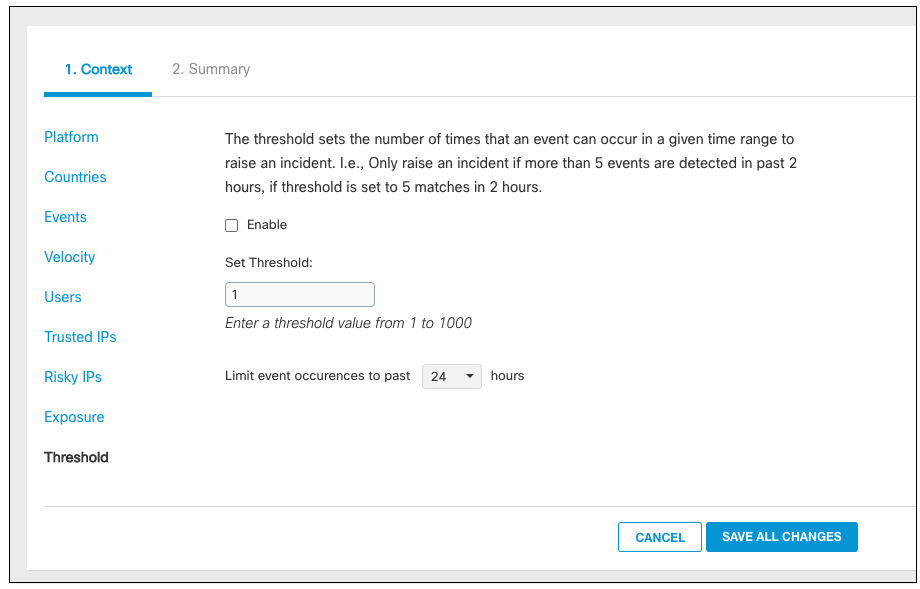
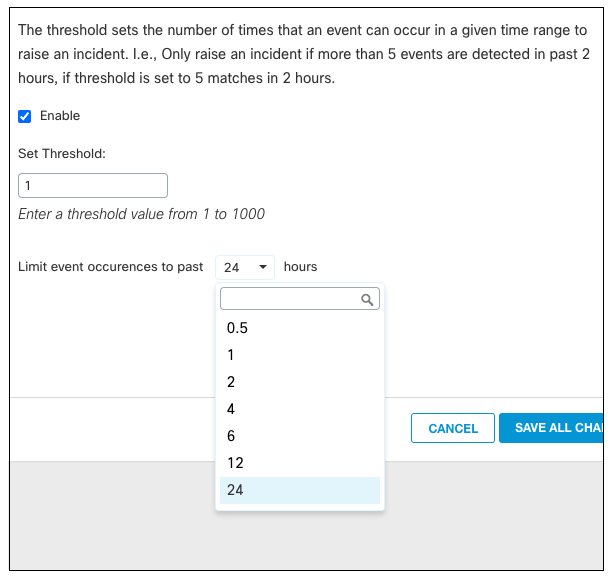
The time frame for the threshold can be changed once the feature is enabled and ranges from 30 minutes to 24 hours.
Once the threshold is configured and enabled for a policy, an incident will occur when the number of events within the time period is met, and all occurrences of the events up to the event that triggered the policy will appear in the incident details. Additionally, any events that occur after the threshold is met will populate in the incident's details.
Incident Examples
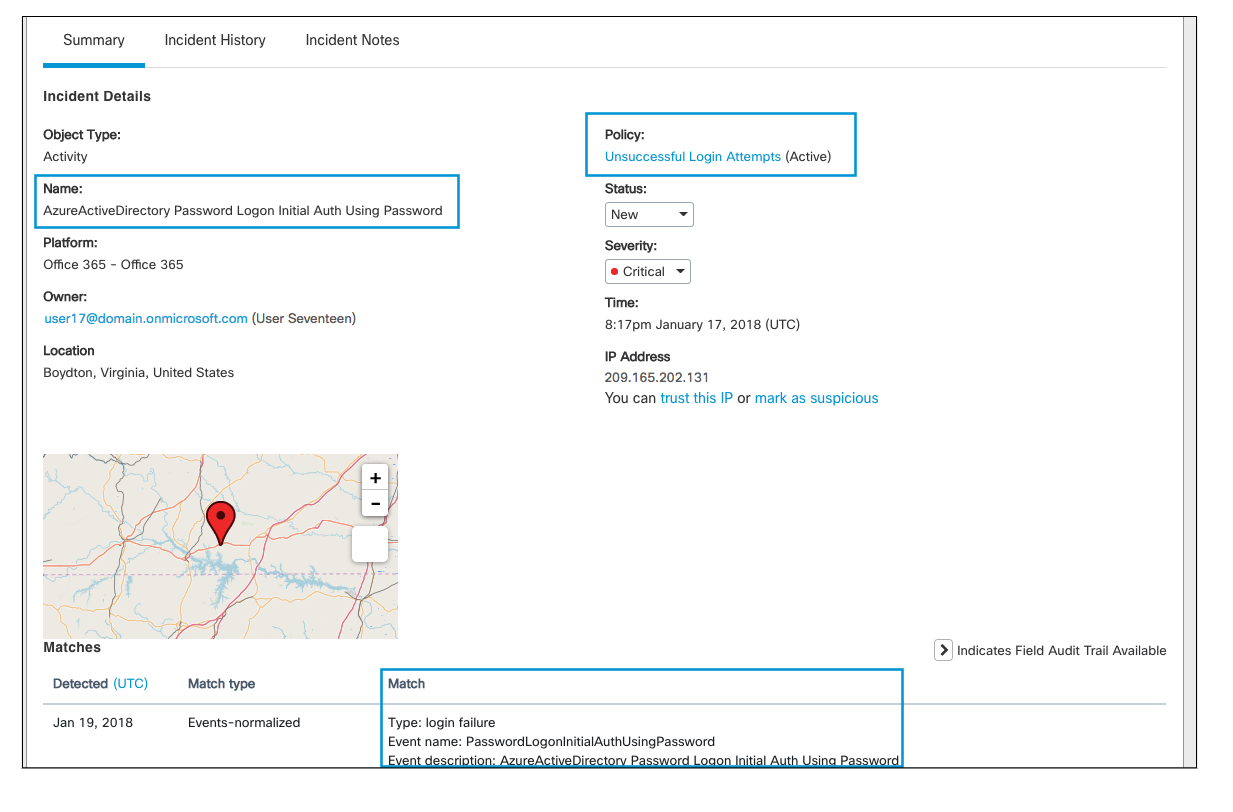
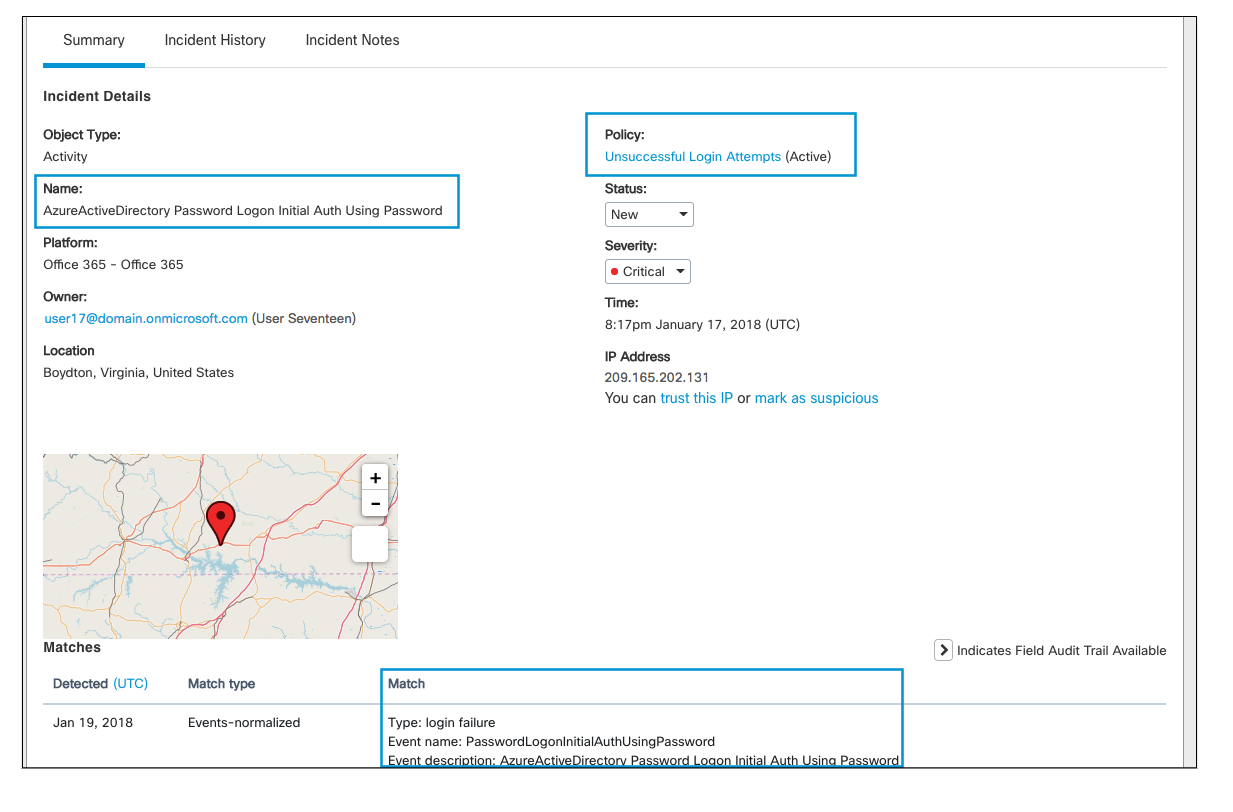
1. Failed Logins
In this incident, a user failed to log into their Office365 suite which triggered an incident.
2. Download Activity
This policy monitors download activity from users' OneDrive accounts. In this incident, a user downloaded a file from their OneDrive which triggered an incident.
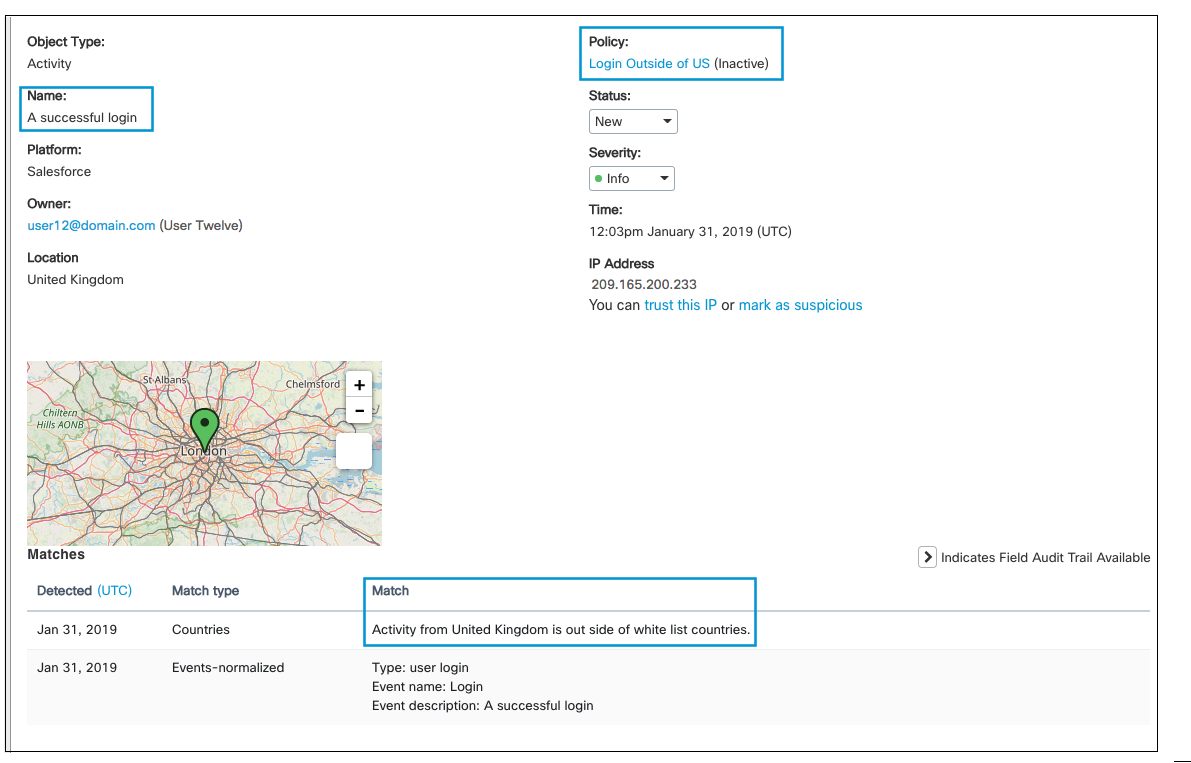
3. Logins Outside a Specified Country
This policy monitors any logins outside of the United States. In this incident, the user successfully logged into their Salesforce account outside of the U.S. in London, UK.
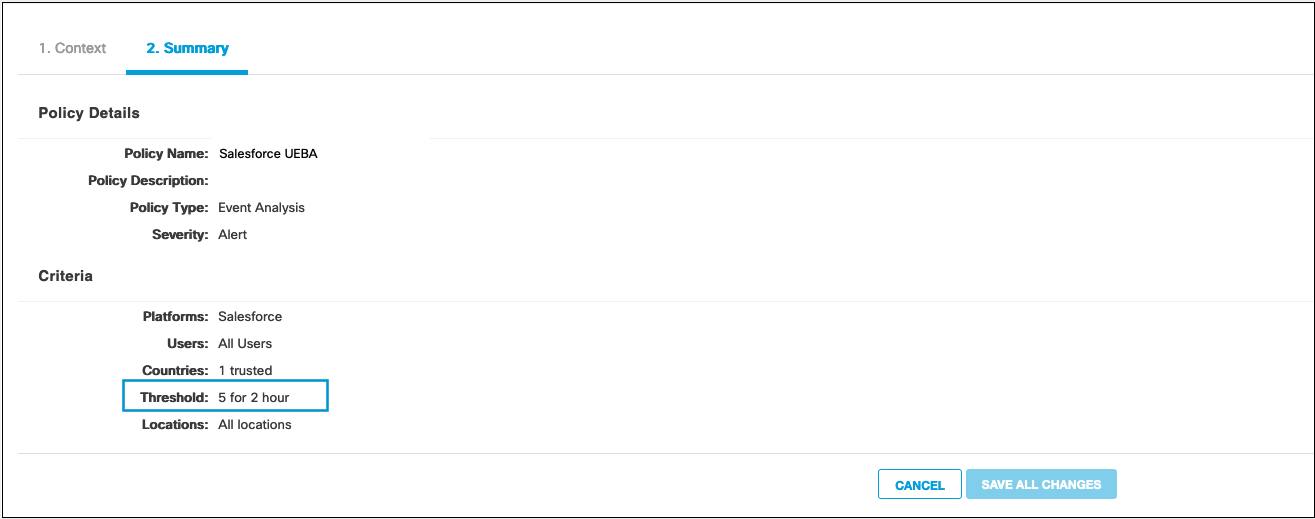
4. Logins with Threshold
This policy monitors user logins five times within a 2 hour period.
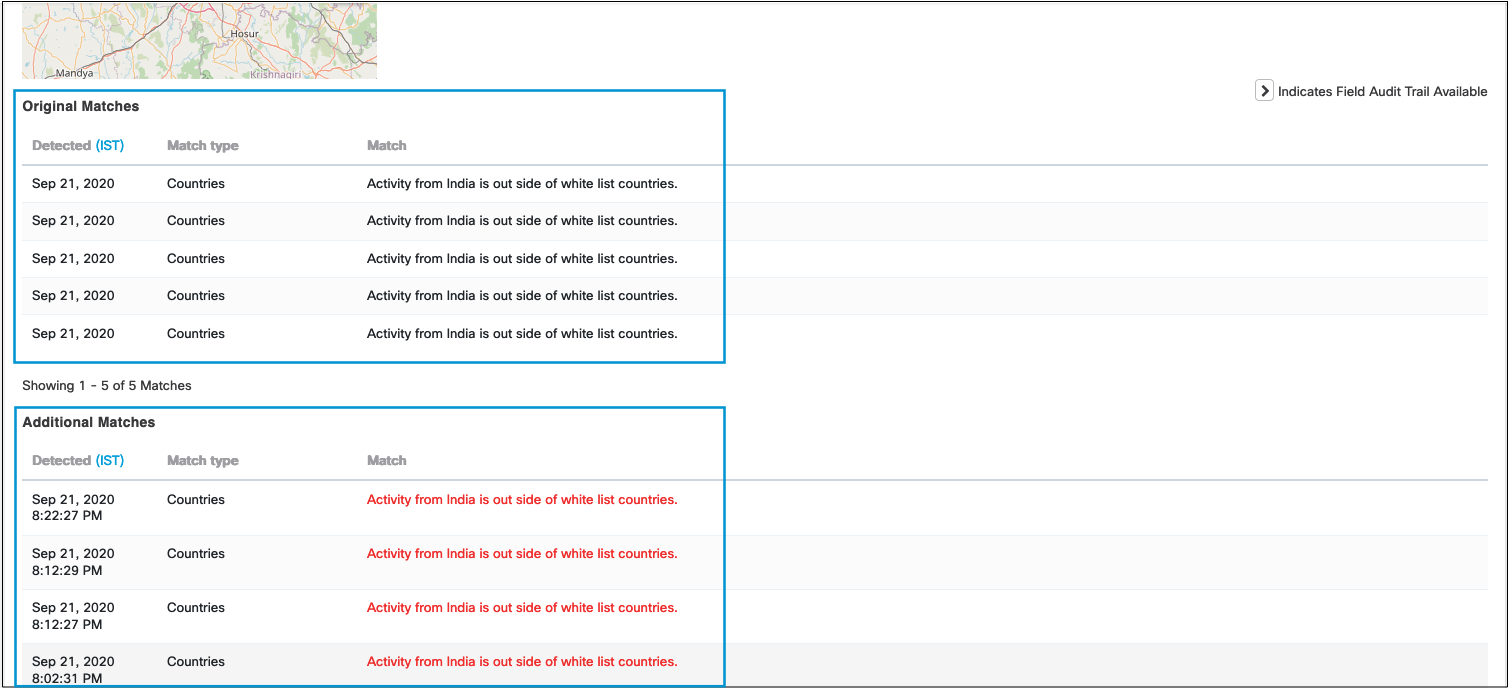
The incident details will show the matches that met the threshold (the first five in two hours in this case) and any additional matches after the threshold is met.
5. Incident History
Like other incidents, the Incident History for UEBA incidents provides details of any workflow or response actions initiated by policy or users.
Updated about 5 years ago
