Trusted Access Scopes
This policy enables you to determine which access scopes are low-risk and classify apps as Trusted. Any selected scopes are considered Trusted and trigger an incident if a user authorizes and installs an app that requests one of those scopes. The default scope category Basic Information are high risk and thus pre-selected.
Configure the Policy
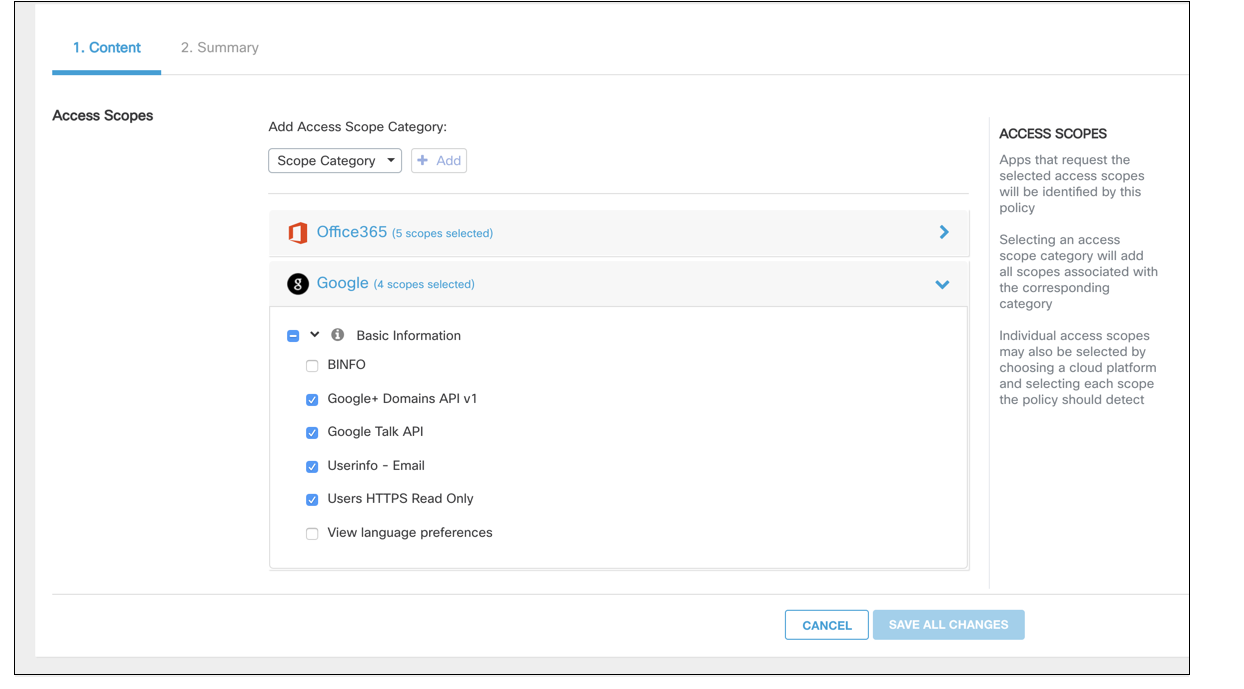
In the policy configuration, select a scope category and click Add to add it to the list of scopes considered Trusted.
Expand the Scope categories to view the list of possible scopes requiring access in each category. (For a complete list of scope categories per platform, see Access Scopes.) Choose which scopes in each category should be Trusted, or mark the checkbox to the left of the category to include all scopes within the category.
Updated over 3 years ago
