Office365
Table of Contents
##Introduction
Cloudlock for Office365 incorporates the monitoring of Sharepoint, OneDrive and Azure Active Directory data. Cloudlock monitors files and folders within OneDrive, files stored in Sharepoint sites, and AzureAD user activity as well as app authentications.
For prerequisites and installation steps see Office 365 Quick Start Setup Guide.
For information on Office365 Applications Firewall see Apps Firewall.
Monitoring Scope
Cloudlock for Office365 supports a monitoring scope for organizations that want to customize which users are monitored. You can configure your monitoring scope in the Platforms tab of the Settings Page by selecting the Office365 platform. You have the option to monitor files and activities of all users/groups, specific users/groups, or all users/groups with the exception of specific users/groups.
Cloudlock automatically imports domains from your organization daily. Any domains that should not be monitored must be managed in the O365 environment configuration settings.

Policies
Cisco Cloudlock monitors Office365 in the following policies:
Data Loss Prevention (DLP)
- Predefined
- Build Your Own: Context Only
- Build Your Own: Custom Regex
Policy Configuration
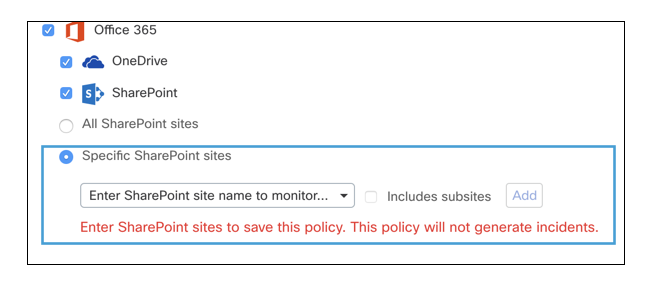
When selecting the Office365 platform in a DLP policy configuration, you have the option to choose OneDrive, Sharepoint, or both. You can select individual sites for Sharepoint or sites as a collection to be monitored.
User Events and Behavior Analytics (UEBA)
- Build Your Own: Event Analysis
Events Analysis policies do not distinguish between Azure, OneDrive and Sharepoint, however, the individual platform can be seen in the Incident Details or the raw event details on the Activities Page.
Response Actions
In addition to the Global Response Actions available in all platforms, Office365 also has three unique Response Actions:
Remove Collaborators
Removes all users (except the file owner) as collaborators on the file.
Revoke File Share
Expires the public share URL.
OneDrive: Quarantine Users' Files
Isolates a file to the Cloudlock Quarantine folder in OneDrive and removes all collaborators and access (including the original owner) with the exception of the admin. This feature is only for customers with O365 OneDrive Business packages.
Sharepoint: Quarantine
Documents in violation are quarantined moved to Cloudlock_Quarantine/ folder in the admin’s OneDrive. All collaborators and owners’ access is removed with the exception of the admin and the file is deleted from the Sharepoint site.
Quarantine Undo for O365 Sharepoint and OneDrive
In cases of a false positive, an admin may opt to undo the quarantine action. The file will be copied back from the admin’s Cloudlock Quarantine/ OneDrive folder to /Documents/Restored from Quarantine folder in the original user’s OneDrive. The owner of the file once returned will be “Cloudapp-app.”
##Incident Examples
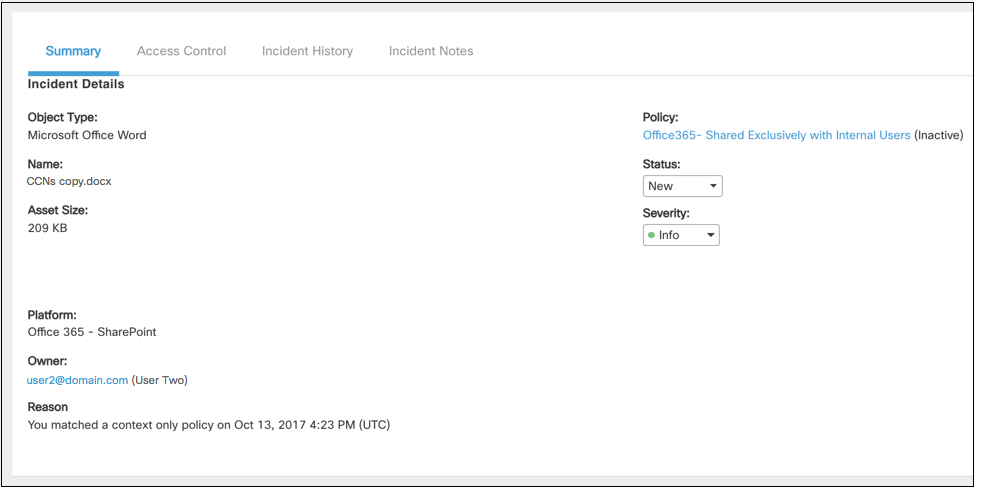
This incident was triggered when the user violated a context only policy by sharing content externally through Sharepoint.
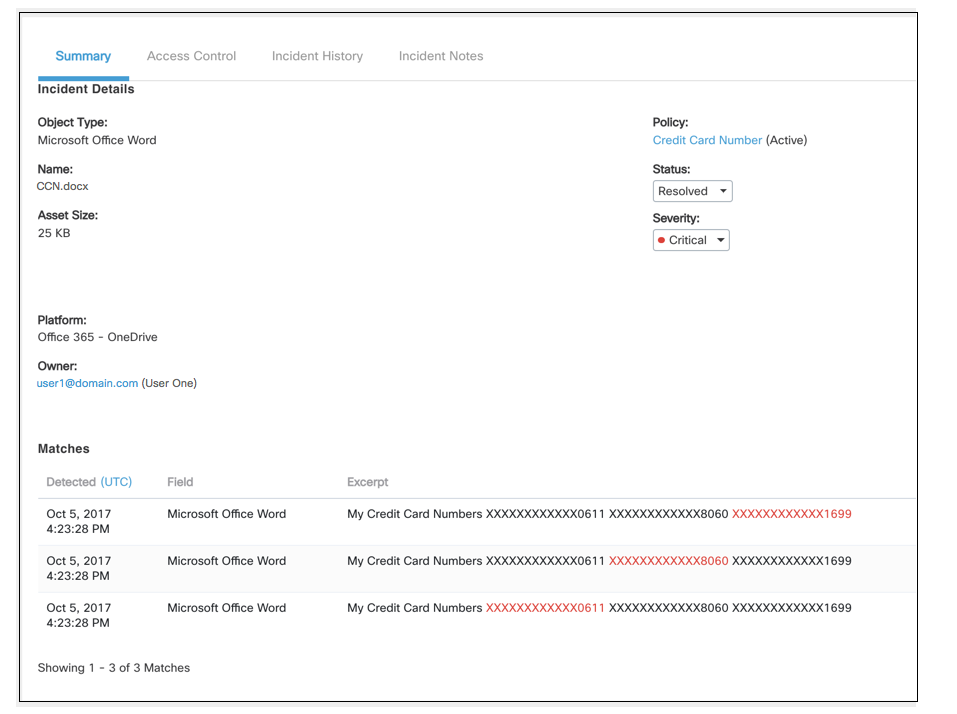
This incident was triggered when the user violated a custom regex policy with a document listing credit cards numbers.
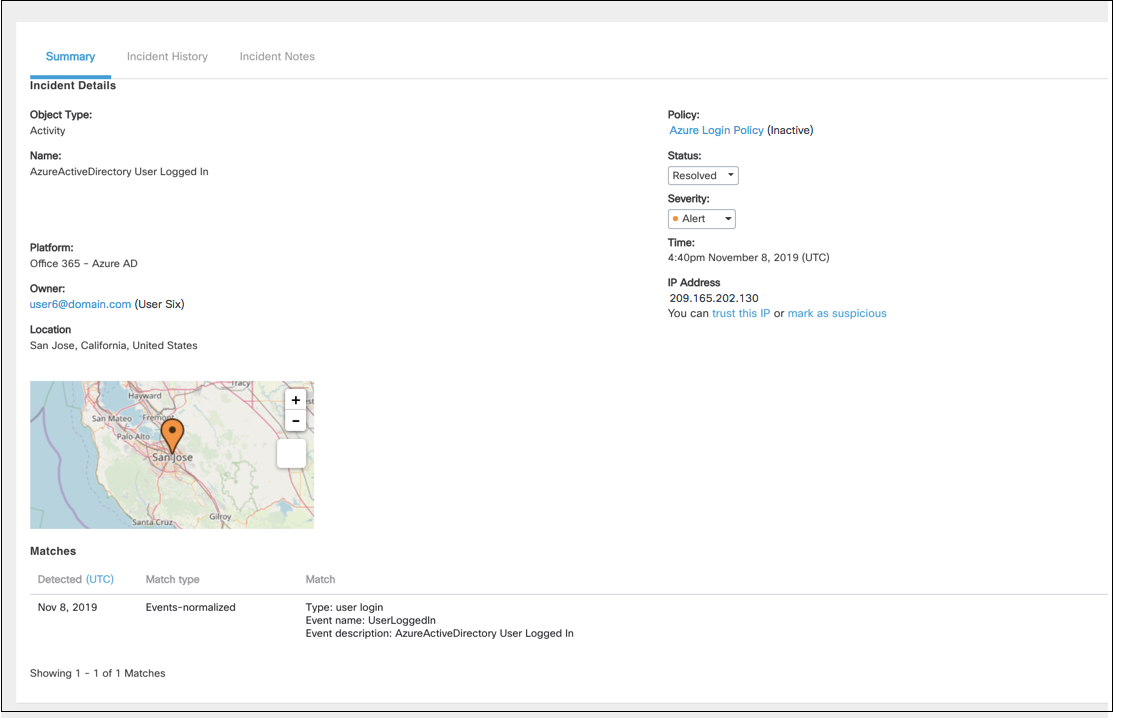
This incident represents a violation of a UEBA Events Analysis policy. In this case, a user logged in with their Azure AD credentials.
View an Object
For DLP incident you can click View Object in the uppermost right corner to view the file that violated the policy.
Viewing Account
The account that is logged into Cloudlock must be within the Office365 org in order to view the object of an incident.
Updated about 2 years ago
