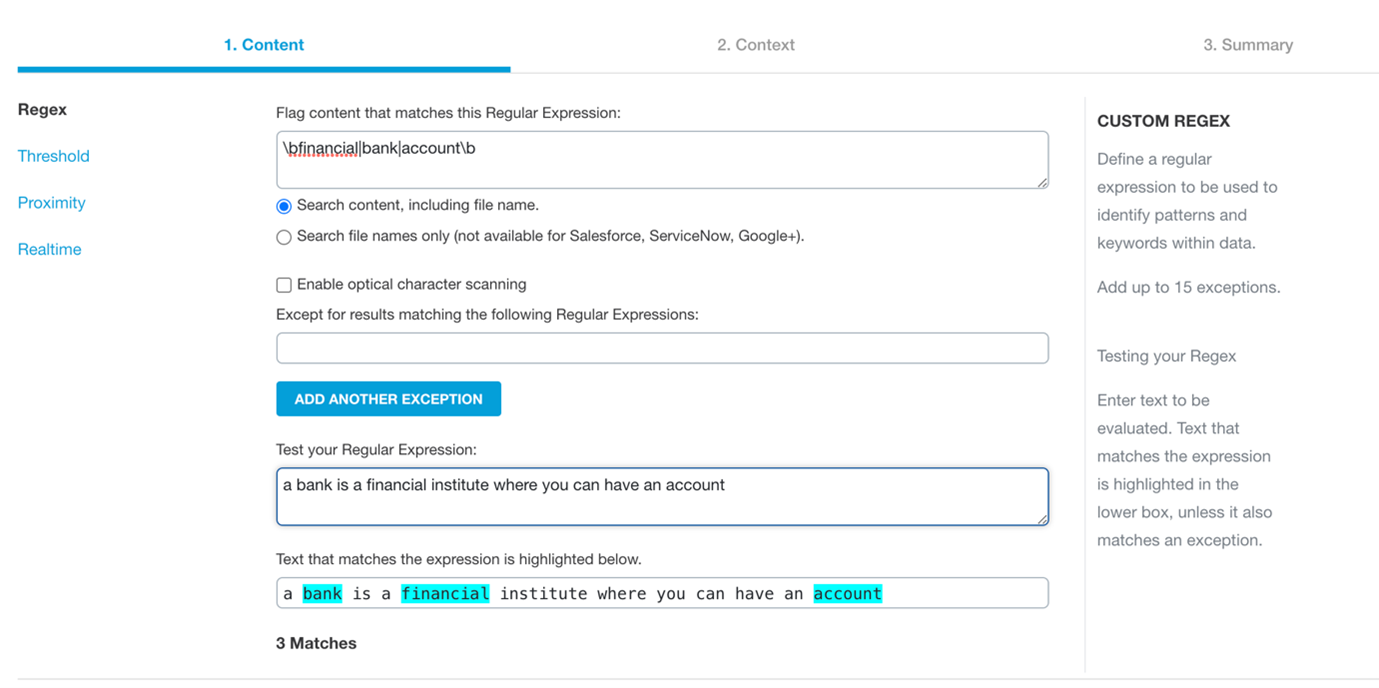
Custom Regex
Custom Regex policies are used to monitor specific words or phrases in content and the exposure of the content. The policy is similar to a Context Only Policy, except that in addition to the exposure of files the policy can search for specific content that is exposed. For example, if the user that created the policy below (for an O365 environment, documents owned by Group X exposed outside of the domain) wanted to monitor documents with the words "financial", "bank", "account" etc they would create a regular expression (regex) to apply these phrases to the monitoring.
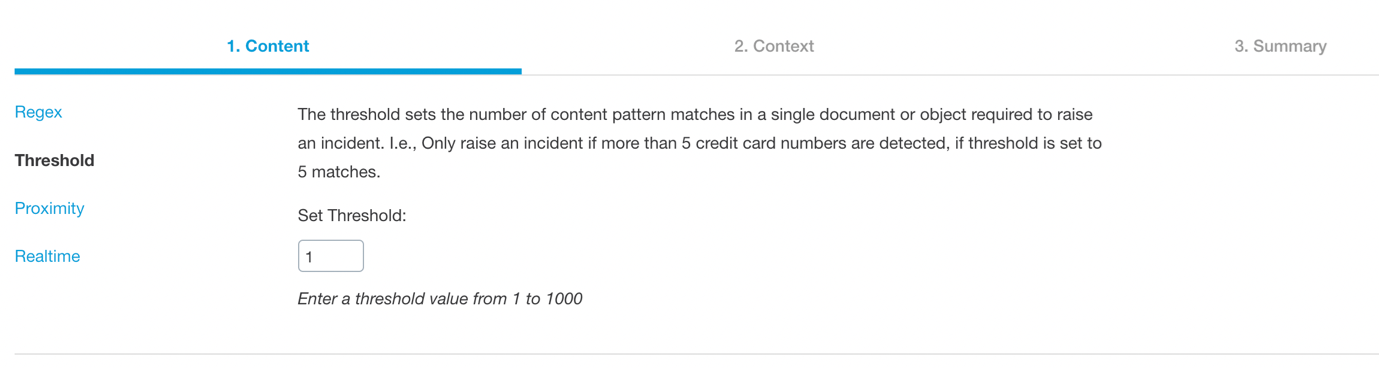
Threshold
Threshold determines how many times the expression is found in a file before being flagged as an incident. You may not be interested in a document where the word "account" is mentioned once, for example, but if it were mentioned at least five times in the same file that might be more cause for concern.
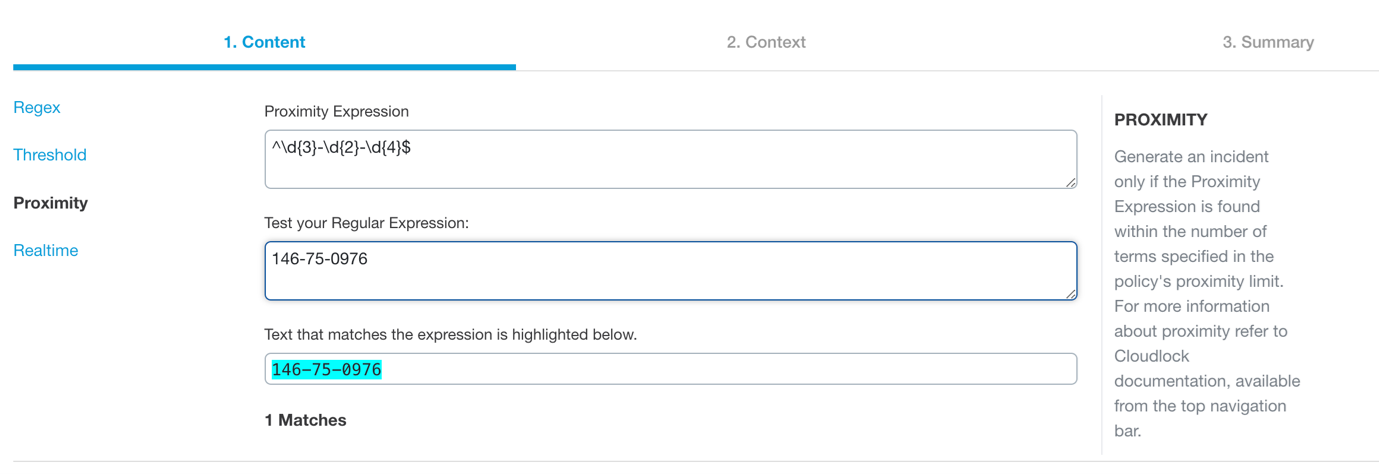
Proximity
Proximity expressions can be used to narrow down the content that is monitored and exposed. While several different types of documents might contain the words "financial" or "bank" or "account" all separately in different areas of the document, the user might want to narrow down documents that are more likely to be sensitive such as financial records that contain these words in proximity to other phrases or words or perhaps a sequence of numbers. A bank account number, social security or birth date might all be useful proximity expression for a financial regex, for example.
Field Character Limits
The regular expression, exceptions, and proximity expression fields all have a maximum character limit of 2048.
Real-time Data-loss Prevention
The Real-time Data-loss Prevention feature supports only the Webex platform. When you enable Real-time Data-loss Prevention, Cloudlock inspects Webex file uploads in real time.
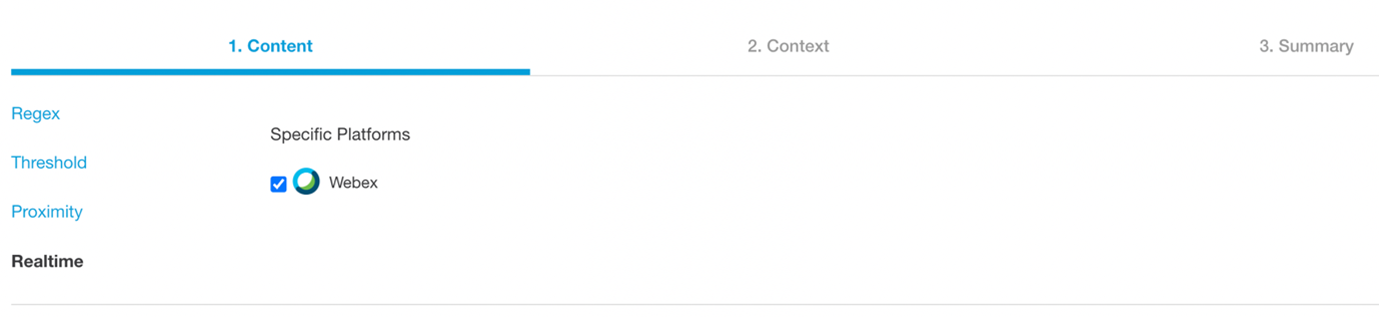
Real-time scanning for Webex
Once the Real-time DLP feature has been enabled for a policy in an organization, files shared over Webex by users of the organization, can be accessed by others only after the files have been inspected by Cloudlock.
Updated about 2 years ago
