Policies Page Overview
The Policies tab enables you to do three major things: add or modify a policy, view and filter your existing policies, and view your Suspicious and Trusted IP Libraries.
Table of Contents
Add a Policy
To add a new policy to your environment click Add a Policy. There are two options: Add Predefined Policy or Build Your Own.
Add a Predefined Policy
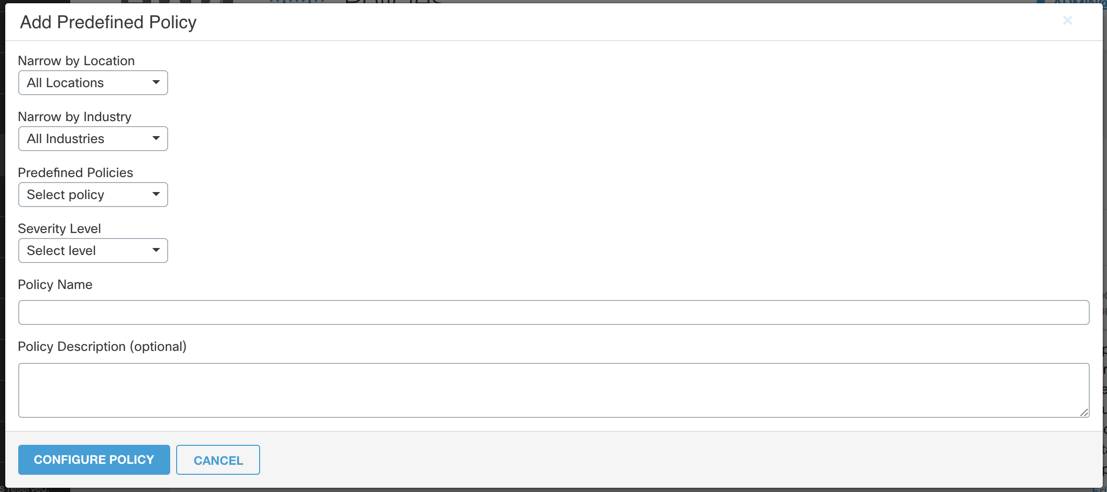
You can filter Predefined policies by location and industry, as shown by the window when this type of policy is chosen.
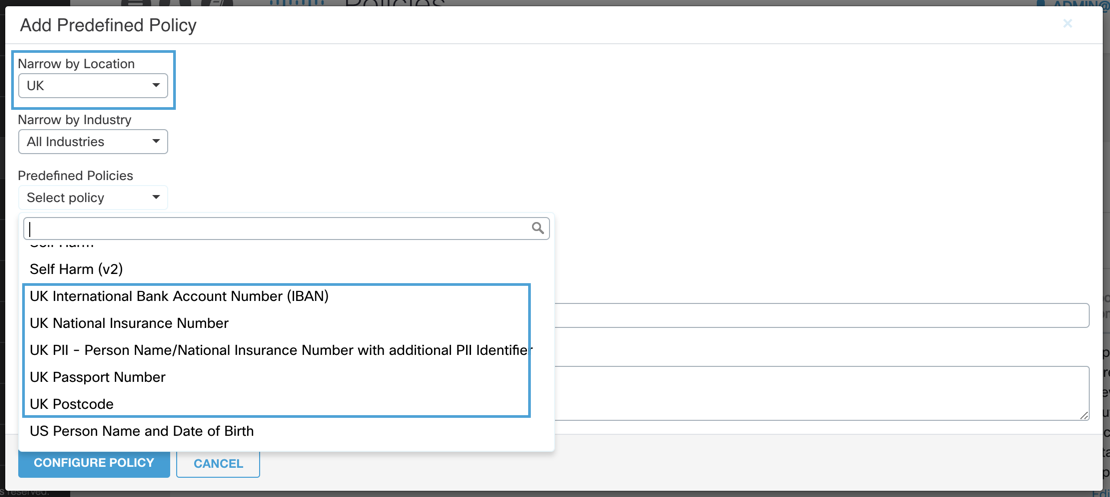
Narrow by Location—Choose from a list of countries to filter possible policies to those related to that country. For example, if you were looking for only UK Passport or ID information, you could narrow the list of policies by selecting only the UK for Location.
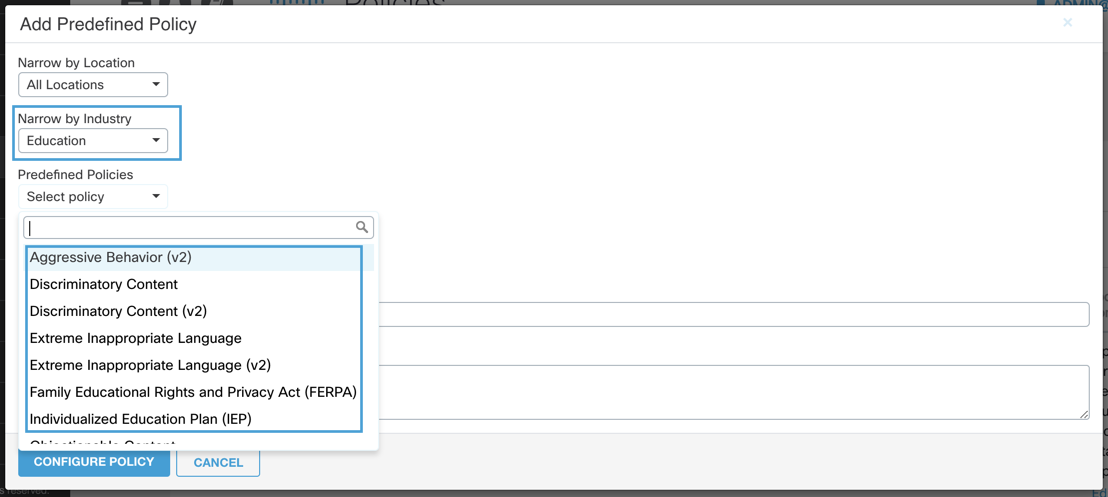
Narrow by Industry—Cloudlock uses predefined policies in the industries of Education, Finance, Government, and Healthcare. There is also a General category for generic identification such as IP Addresses, Date of Birth, or Email Address. Filtering policies by Education, for example, will populate policies related to the Education industry (e.g. FERPA, Objectionable Content, Self Harm, US Student Loan Application Information.)
Predefined Policies—All available Predefined Policies which can be filtered byLocation and/or Industry.
Severity Level—You can set the Severity Level based on how significant a violation of this policy would be.
Policy Name and Description—You choose the name of the policy which will be displayed in the policies listed in the Policy tab. You can also add a Description to differentiate between similar policies.
Add a Build Your Own Policy
There are three types of Build Your Own Policies: Context Only, Custom Regex and Event Analysis.
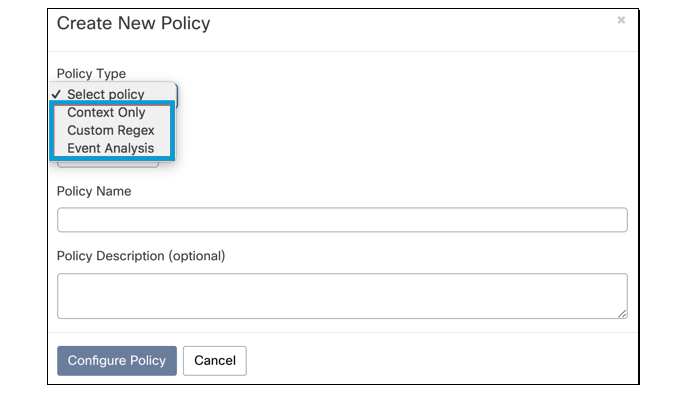
Context Only—Policies that match criteria based on exposure (e.g. domain-wide, public, to specific groups).
Custom Regex—Policies that use regular expressions created by the user to match the content.
Event Analysis—Policies that monitor user activity such as logins, downloads, file updates, adding users, etc. The events differ depending on the platforms chosen.
You define Severity, Policy Name, and Description based on the significance and purpose of the policy in the environment.
View Existing Policies
Policies are listed by Name, Description, Status, Type, Severity, Detection Criteria, Response Actions, and Last Modified.
Policy—Name of the policies.
Description—Descriptions of individual policies.
Status—Whether the policy is currently Active or Inactive. Clicking the dropdown on an individual policy will also give you the option to Delete a policy.
Type—Lists the type of policy such as App Action, Custom Regex, Event Analysis, Social Security Number (predefined content) and New Unclassified Apps.
Severity—Severity of the policy as chosen by the policy creator or modifier (Info, Warning, Alert, Critical). For example, a policy that is configured to monitor extremely sensitive data such as medical or financial information may be labeled as Critical, but a policy that monitors user logins may be labeled info if the information is not as significant.
Detection Criteria—Lists any criteria in Policy Configuration that you can modify such as Threshold, Proximity, Asset Type, Exposure, Platform, and Ownership. Clicking Edit will open the Policy Configuration page and enable modification of any of the criteria.
Response Actions—Lists any specified Response Actions chosen for that policy. Selecting Edit will open the Response Actions page to modify any Response Actions for that policy. You also have the option to Delete All Response Actions. Create will appear if no Response Actions are created.
Last Modified—A timestamp of the last time the policy was modified. Modification includes changes made to Policy name, Description, Status, Severity, Detection Criteria, and Response Actions.
##Suspicious and Trusted IP Libraries
The Suspicious and Trusted IP Libraries enable you to store lists of IP addresses or IP ranges that are either particularly questionable or unnecessary to monitor (such as office locations or VPNs).
###Add Suspicious IP
To add an IP address or range to the library select Add Suspicious IP. Fill out the form with the type of threat the IP poses, any notes, and the expiration date if the IP need only be added to the library temporarily. You can add a comma-delimited list of IP addresses or a range of IPs.
###Add Trusted IP
To add an IP address or range to the library select Add Trusted IP. Label the address with a department or location, add any notes, and specify a type (remote office or remote app). You can add a comma-delimited list of IP addresses or a range of IPs.
Delete and Import via CSV
Both libraries have two bulk action options: Delete and Import via CSV. Deleting will remove selected IP addresses from the library. Importing a CSV file adds a bulk list of IP addresses to the library.
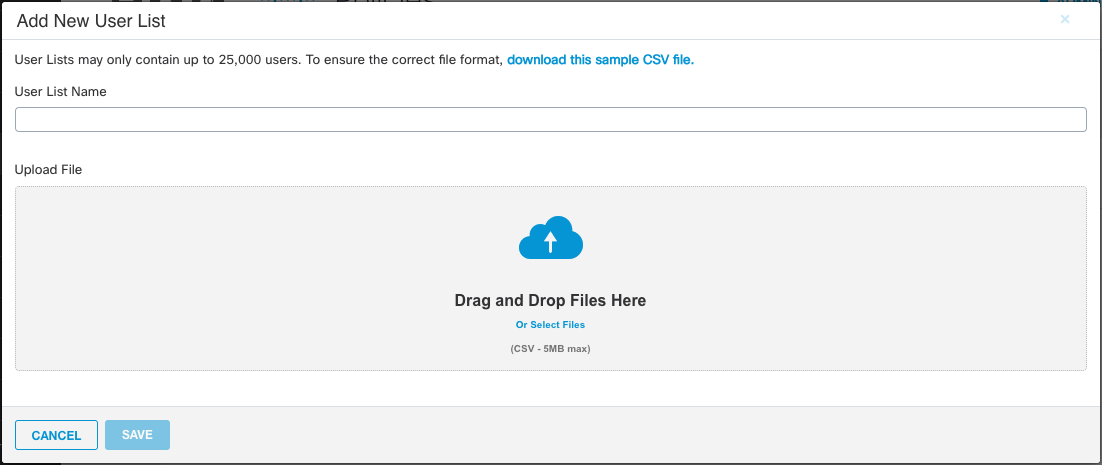
User List Library
The user list library enables you to create lists of users across platforms that may be unrelated to groups or OUs. User List Libraries can be applied to policies under the Ownership criteria.
To add a user list click Add User List. The maximum number of users per list is 25,000 and the maximum .csv file size upload is 5mb. You can delete a user list but only after it is disabled from any policies.
Updated about 2 years ago
