Data Loss Prevention for Google Chat
Table of Contents
- Introduction
- Pre-requisites
- Features
- Domain Wide Delegation
- Policies
- Configure Response Actions
- Incident Examples
- Limitations
Introduction
The Cloudlock's Data Loss Prevention (DLP) feature for Google Chat helps organizations monitor and protect sensitive information that are shared within their Google Chat environment. This feature ensures that data security policies are enforced across the communication channels within Google Chat.
Pre-requisites
Pre-requisites for using Cloudlock’s DLP on Google Chat:
- Domain Wide Delegation: Ensure that Cloudlock is integrated with your Google Workspace environment through Domain Wide Delegation. For procedure on adding these delegations, see Domain Wide Delegation
- Define DLP Policies: Create and configure DLP policies that specify the types of sensitive information to monitor and the actions to take in case of policy violations.
- Review Incidents and Reports: Regularly review incidents and reports generated by Cloudlock to stay informed about policy violations.
Features
- DLP on One-to-One Messages:
Cloudlock's DLP feature can monitor and apply data loss prevention policies to the direct messages exchanged between any two users within the organization. This feature ensures sensitive information is protected even in private conversations.
Key Capabilities:- Near real-time scanning of one-to-one messages for sensitive data.
- Application of predefined DLP policies to prevent data breaches.
- Alerts and notifications for policy violations.
- DLP on Group Messages:
Cloudlock extends its DLP capabilities to group messages, enabling organizations to enforce data protection policies in conversations involving multiple participants.
Key Capabilities:- Near real-time monitoring of group messages for sensitive information.
- Enforcement of DLP policies in group chat settings.
- Generation of alerts and reports on policy violations.
- DLP in a Space:
Cloudlock's DLP feature also supports monitoring and policy enforcement in Google Chat Spaces, which are virtual rooms for team communication and collaboration.
Key Capabilities:- Continuous near real-time monitoring of messages within Google Chat Spaces.
- Application of DLP policies to protect sensitive information shared in spaces.
- Alerts and detailed reporting on DLP policy breaches, configurable through policies.
Domain Wide Delegation
Steps to authorize Google Chat for the customers
You need to navigate to your Google Workspace Domain Wide Delegation with sufficient admin permissions. Contact your super admin to obtain the admin permissions.
- On the Domain Wide Delegation page, authenticate using an account with sufficient admin permissions and go to your Google Workspace Domain Delegation.
- On the Google Workspace Domain page, click Add new.
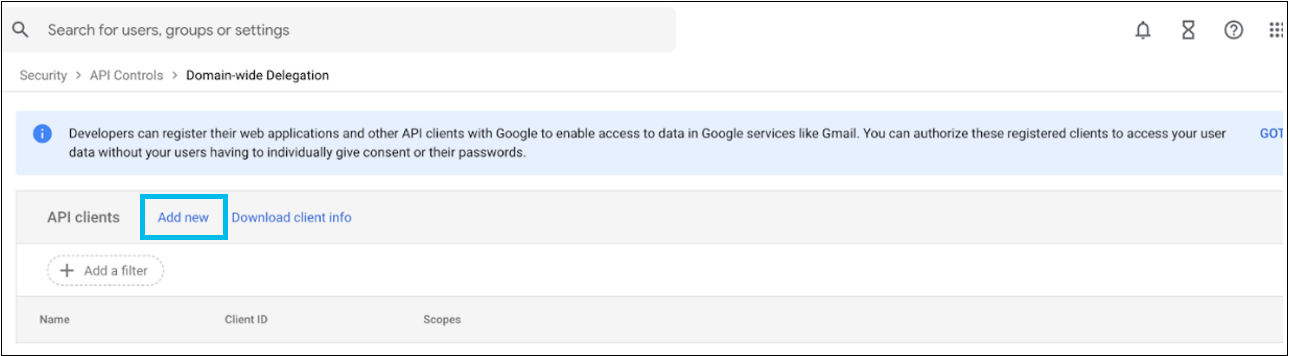
Add a new client ID window appears.
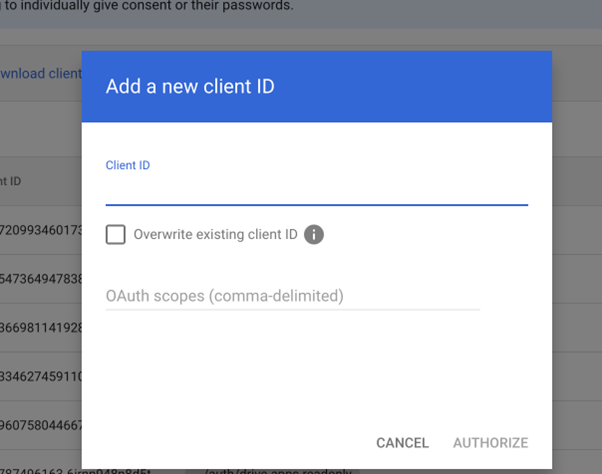
- Enter the Client ID, which is the Cloudlock Google Chat App ID, to access the Customer Environment for DLP.
Note:
Contact your customer support team to obtain the Client ID.
- In the OAuth Scope (comma-delimited) field, enter the following link:
https://www.googleapis.com/auth/userinfo.email,https:/www.googleapis.com/auth/userinfo.profile,https:/www.googleapis.com/auth/admin.directory.user.readonly,https:/www.googleapis.com/auth/admin.reports.audit.readonly,https:/www.googleapis.com/auth/drive,https:/www.googleapis.com/auth/admin.reports.usage.readonly,https:/www.googleapis.com/auth/chat.delete,https:/www.googleapis.com/auth/chat.memberships,https:/www.googleapis.com/auth/chat.messages,https:/www.googleapis.com/auth/chat.spaces,https:/www.googleapis.com/auth/activity
Note:
All mandatory scopes must be configured to ensure Cloudlock can fetch events and perform DLP for Google Chat. If even a single scope is missing, Google Chat for Cloudlock will not perform DLP.
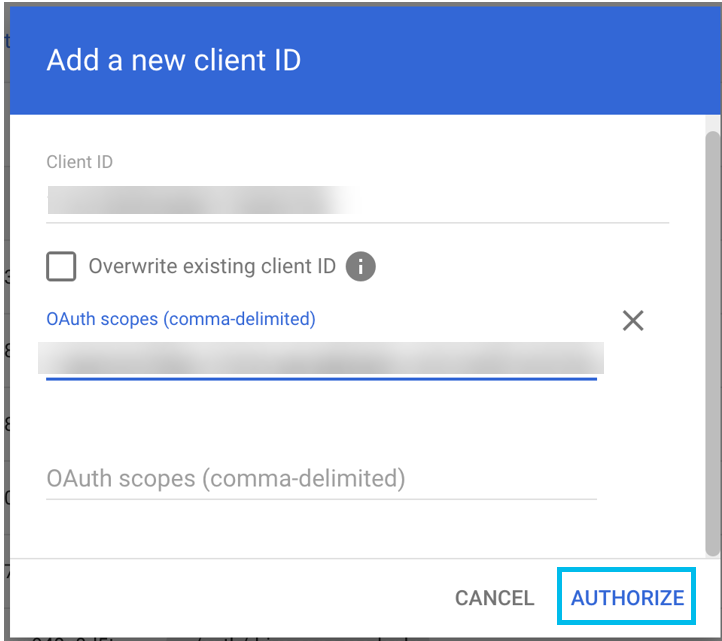
- To allow Cloudlock to access the specified list of scopes, click AUTHORIZE .
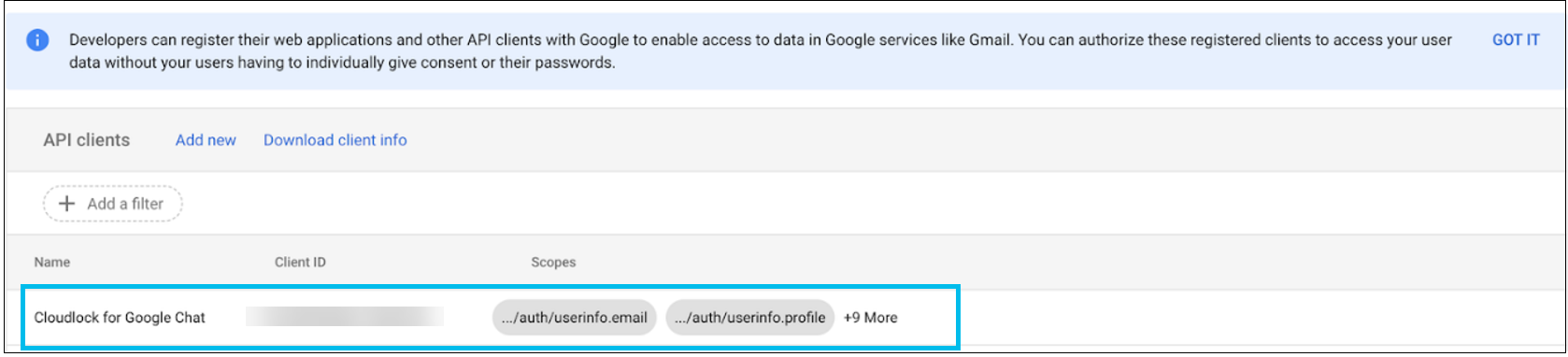
The App ID appears in the list.
Policies
Cisco Cloudlock monitors Google Chat environment using the following Data Loss Prevention (DLP) policies:
- Predefined
- Build Your Own: Context Only
- Build Your Own: Custom Regex
Following are various exhibits on policies, incidents, and response actions for the DLP Google Chat:
Configuring Policy for Google Chat
Select the Google Chat platform under the Platform section in the policy configuration settings.
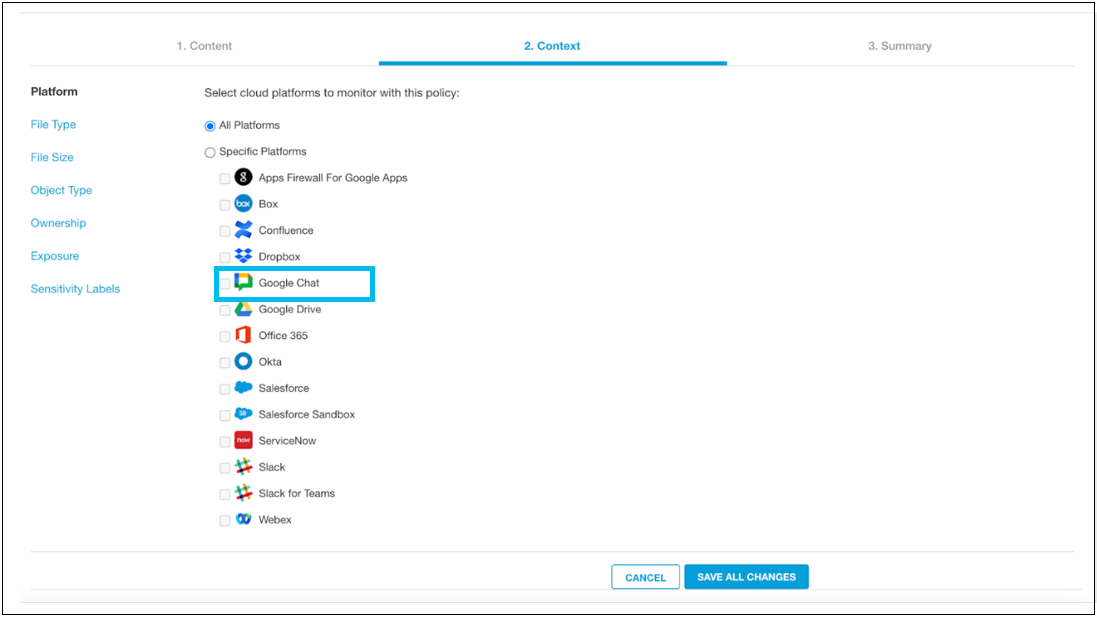
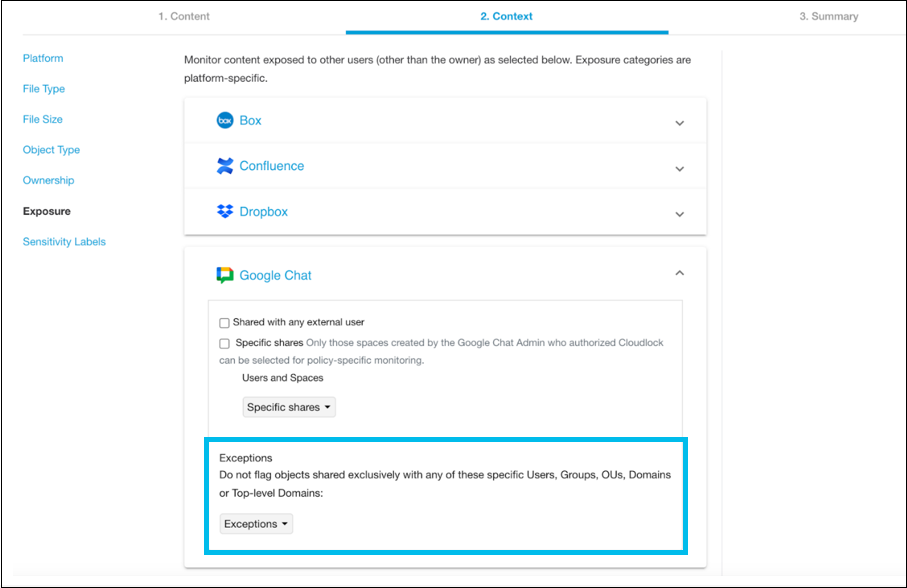
You can configure Google Chat-specific exposures in the policy to scan only selected users or spaces.
You can also choose to exclude users or spaces using exceptions:
Incident Examples
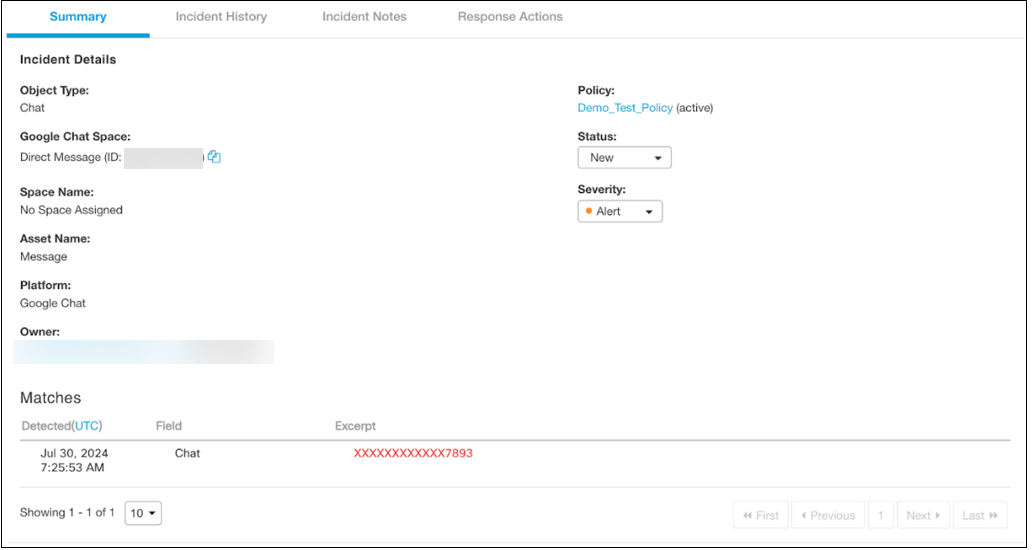
The following exhibit displays the incident being triggered when a user violates the configured policies (that includes predefined policy, custom regex policy, and context-only policy).
Configure Response Actions
The following figure shows a sample configuration of response actions for the Google Chat.
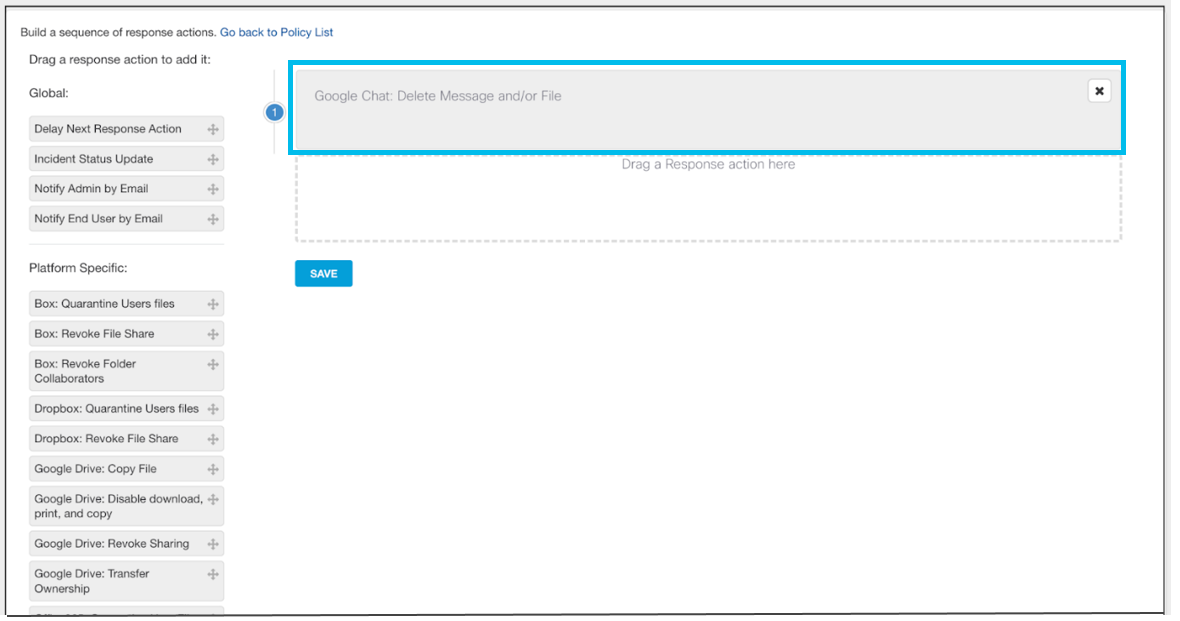
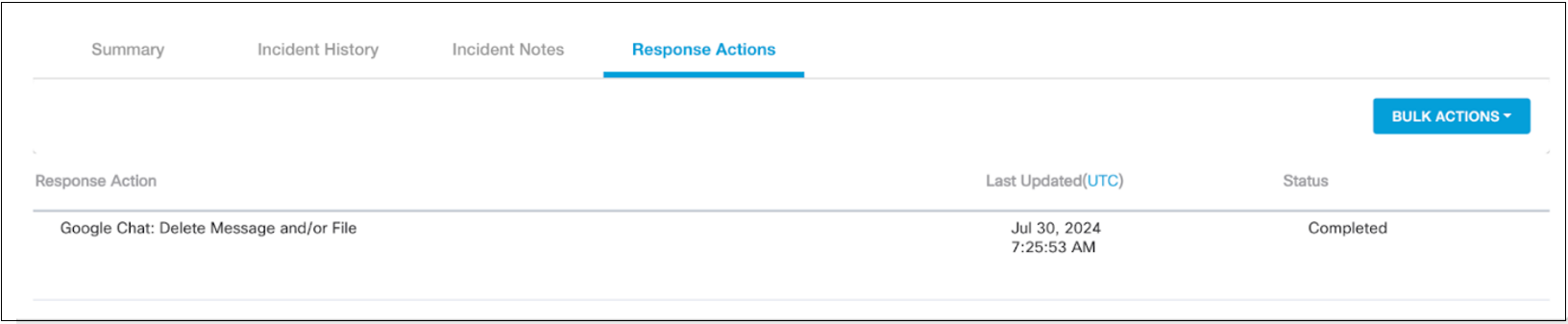
The following figure displays the response actions that were applied to the incident.
Limitations
Limitations for Cloudlock’s DLP on Google Chat:
- Messages from External Users: Google Chat messages received from users outside the organization are not subject to Cloudlock's DLP policies. This means that sensitive information shared by external users cannot be monitored or protected by the DLP feature.
- User Behavior Analysis: The current version of Cloudlock's DLP for Google Chat does not track or analyze user actions and behaviors for potential security risks or policy violations.
Updated about 1 year ago
