Active Directory Policy Enforcement and Identities
Configure User identities for policy enforcement so that the Cisco Secure Roaming Client module can apply user identities to DNS and web traffic.
Table of Contents
Procedure
- Deploy the AD Connector as described in the Active Directory Setup Guide.
- In the Umbrella dashboard, navigate to Deployments > Core Identities > Users and Groups and click View Users & Groups to confirm that the groups and users are added.
- To provision users and groups from Active Directory, see [Connect Active Directory to Umbrella to Provision Users and Groups](doc: 5-connect-active-directory-to-umbrella).
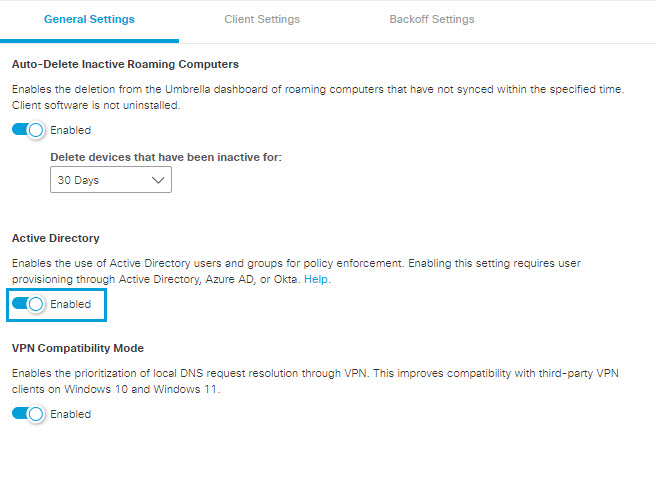
- Navigate to Deployments > Core Identities > Roaming Computers and click Settings.
- Under the General Settings tab, enable Active Directory. (This is enabled by default for all new accounts).
macOS User Identity
macOS has many options to do user identity, from traditional native binding (phasing out), Enterprise Connect (end of life), NoMaD (acquired and launched as JAMF Connect), JAMF Connect, and AppSSO. Cisco currently supports:
- Native Binding
- NoMaD branded implementations
- Enterprise Connect
- MDM User Identity Injection
At this time Cisco Umbrella does not support JAMF Connect or AppSSO (Kerberos Extension) in the roaming client. Cisco provides native MDM profile support for user identity injection. Any MDM can push a managed preferences profile containing a user email address to set the current user by MDM.
Support versions:
- Cisco Secure Roaming Client module (formerly AnyConnect)
- Cisco Secure Client 5.0 and above
- AnyConnect 4.10 MR6 (and higher on 4.10)
- Umbrella Roaming Client
- Next 3.0.22 and above
This profile should be pushed to Managed Preferences (*/Library/Managed Preferences). This will not function without the version listed above.
com.cisco.umbrella.client.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>UPN</key>
<string>[email protected]</string>
</dict>
</plist>
Interpret Diagnostics < Active Directory Policy Enforcement and Identities > Virtual Appliances
Updated about 1 year ago