Identity Support for the Roaming Client
Identity support is an enhancement to the Umbrella Roaming Client and the AnyConnect Umbrella Roaming Security Module.
- Identity support provides Active Directory user and group identity-based policies, in addition to user and private LAN IP reporting.
- Identity support does not provide reporting by group, or policy by LAN IP.
- Identity support does not provide support for Active Directory (AD) organizational units (OUs) but does support AD Groups.
- You can use identity support as an alternative or in addition to the Umbrella Virtual Appliance (VA). Identity support can provide insights for devices that use Network Address Translation (NAT) to map an IP address to a single egress IP.
- Identity support enables granular reporting—down to the individual user or device—and the ability to set very specific policies for identities in Umbrella.
- Identity support is available for all Umbrella roaming computers.
Umbrella Packages
Umbrella Identity Support for AD Users and Groups is not available with all Umbrella packages. If you encounter a feature that you do not have access to, contact Umbrella sales about your current package. For more information, see Cisco Umbrella Packages.
Table of Contents
- Prerequisites
- On-Premises Identity
- Procedure
- Prerequisites for AD Integration
- Configure Identities on macOS
- LAN IP Address Reporting Only—No AD integration
- Enhanced Roaming Client UI
- AnyConnect Umbrella Roaming Security Module UI
- Identity Support in DNS Policy
- Identity Support in Umbrella Reports
- What Information is Sent to Cisco Umbrella and When
Prerequisites
Identity support of AD Users and Groups is available for the Umbrella Roaming Client and the AnyConnect Umbrella Roaming Security Module.
Windows:
- Umbrella Roaming Client for Windows, minimum version 2.1.0
- AnyConnect Umbrella Roaming Security Module for Windows, minimum version 4.5.01
macOS:
- Umbrella Roaming Client for macOS, minimum version 2.0.39
- AnyConnect Umbrella Roaming Security Module for macOS, minimum version 4.5.02
On-Premises Identity
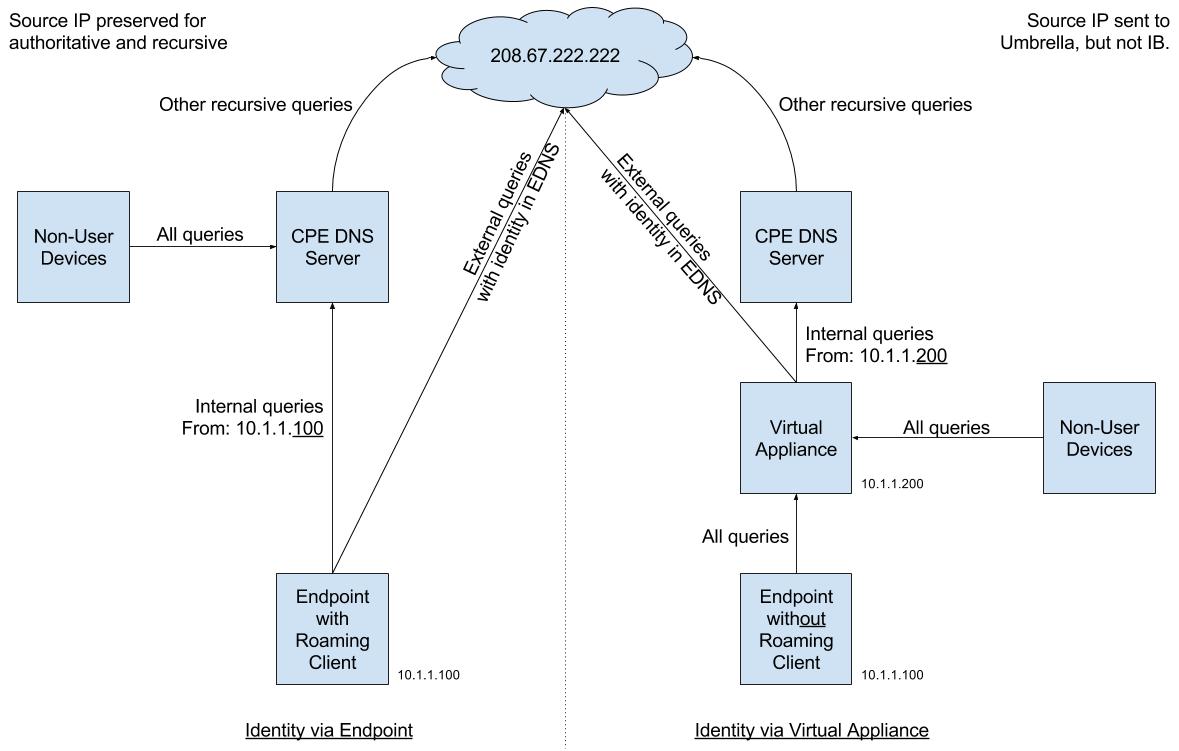
In addition to improving off-network visibility and policy granularity, you can use the Roaming Client or AnyConnect roaming security module with identity support in on-network scenarios where the Umbrella Virtual Appliance (VA) is not deployed.
Deploying the Umbrella VA requires that all devices use the VA as their DNS server while on-network. Some organizations have DDI (DNS, DHCP, and IPAM (IP Address Management)) solutions already in place.
With a DDI solution in place, pointing all devices to the VA for DNS can cause loss of function of identity and granular policy for internal queries. When internal queries for internal domains are conditionally forwarded by the VA to the DDI solution, the queries use the source IP of the VA. Thus, internal queries that use the source IP of the VA prevent the DDI solution from detecting which endpoint or user originated the query.
By contrast, the roaming client sends internal domain queries directly to the DDI solution instead of using the VA. Sending queries for internal domains directly to the DDI ensures that the source IP address is preserved, and in turn, prevents loss of information or function in the DDI solution.
Procedure
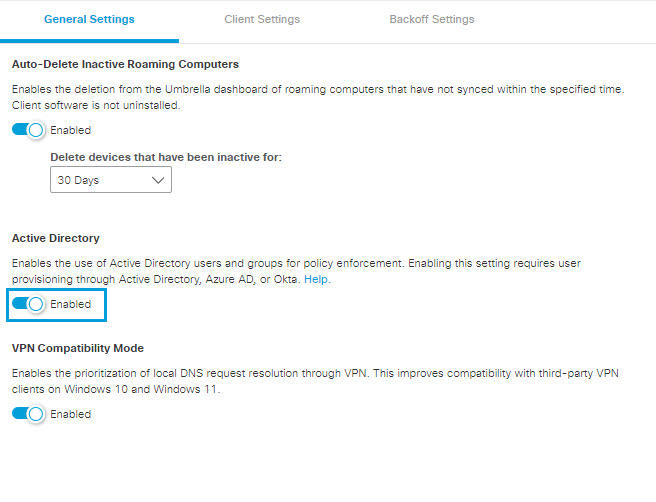
As of October 2017, to prevent unexpected behavior due to changes in policy enforcement, the identity support option for roaming clients is enabled by default for all new accounts. For Umbrella accounts created before October 2017, you must manually enable identity support for roaming clients.
- Navigate to Deployments > Core Identities > Roaming Computers and click Settings.
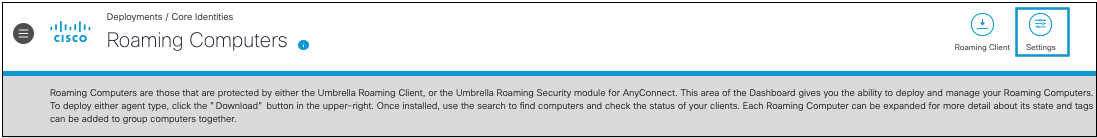
- From the General Settings tab, enable Active Directory.
Note: Changes to the roaming client AD settings may require up to one hour to take effect.
Prerequisites for AD Integration
To configure AD user and group identity support in a roaming computer, you must meet the following prerequisites.
- At least one domain controller registered to sync AD user and group data to Umbrella. This is accomplished by running a script.
- You must install and run at least one Umbrella AD Connector service to perform the sync. If the connector is not installed, Umbrella cannot sync any changes from AD.
- When logged into your device, ensure that you are part of the domain. User identity information on non-domain devices and Bring Your Own Devices (BYODs) is not reported to the dashboard.
For more information, see Provision Identities from Active Directory.
Configure Identities on macOS
Umbrella supports various applications to configure user and group identities on macOS devices.
| Application | Roaming Computer Deployments | Notes |
|---|---|---|
| Active Directory Binding | Roaming Client 2.0.39+ AnyConnect 4.5.02+ | |
| Enterprise Connect | Roaming Client 2.3.50+ AnyConnect 4.9.01+ | For macOS devices running Umbrella Roaming Client 2.2.50 or AnyConnect 4.9.01095 (MR1) and higher, Enterprise Connect is supported. Your macOS device is not required to join to the domain. With older versions of the agent software, you must join the macOS device to the domain. |
| NoMAD | Roaming Client 2.3.4+ AnyConnect 4.10.03+ | Recommended |
| MDM Managed Preferences | Roaming Client 3.0.22+ AnyConnect 4.10.06+ * Secure Client 5.0.0+ | Recommended You must push the user identity to the client. For more information, see macOS Mobile Device Management. |
Umbrella does not support the following applications to configure user and group identities on macOS devices.
- Apple AppSSO (Kerberos SSO)
- JAMF Connect
Note: All supported configuration options require that you provision a user identity to Umbrella from AD, Azure AD, or Okta, and that you enable identity support.
LAN IP Address Reporting Only—No AD integration
Your setup is complete. No additional configuration steps are required.
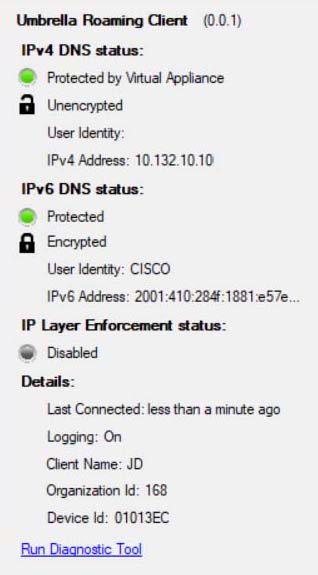
Enhanced Roaming Client UI
With identity support enabled, the roaming client displays additional user identity information in its local user interface.
AnyConnect Umbrella Roaming Security Module UI
Unlike the enhanced roaming client UI, the AnyConnect Umbrella roaming security module UI does not show whether identity support is enabled. To test whether identity support is enabled, you must create a user identity-based policy and browse to a blocked or allowed site.
Identity Support in DNS Policy
Depending on the type of mode, the roaming client provides identity support for various types of Umbrella deployments in the Umbrella DNS policy.
Protected (encrypted or unencrypted) mode
- Identities supported by the roaming client:
- Roaming Computer
- AD User
- AD Group
- Identities not supported by the roaming client:
- AD Computer
- Internal Network
Behind VA, On Protected Network, and Unprotected modes
- Identity support is not available.
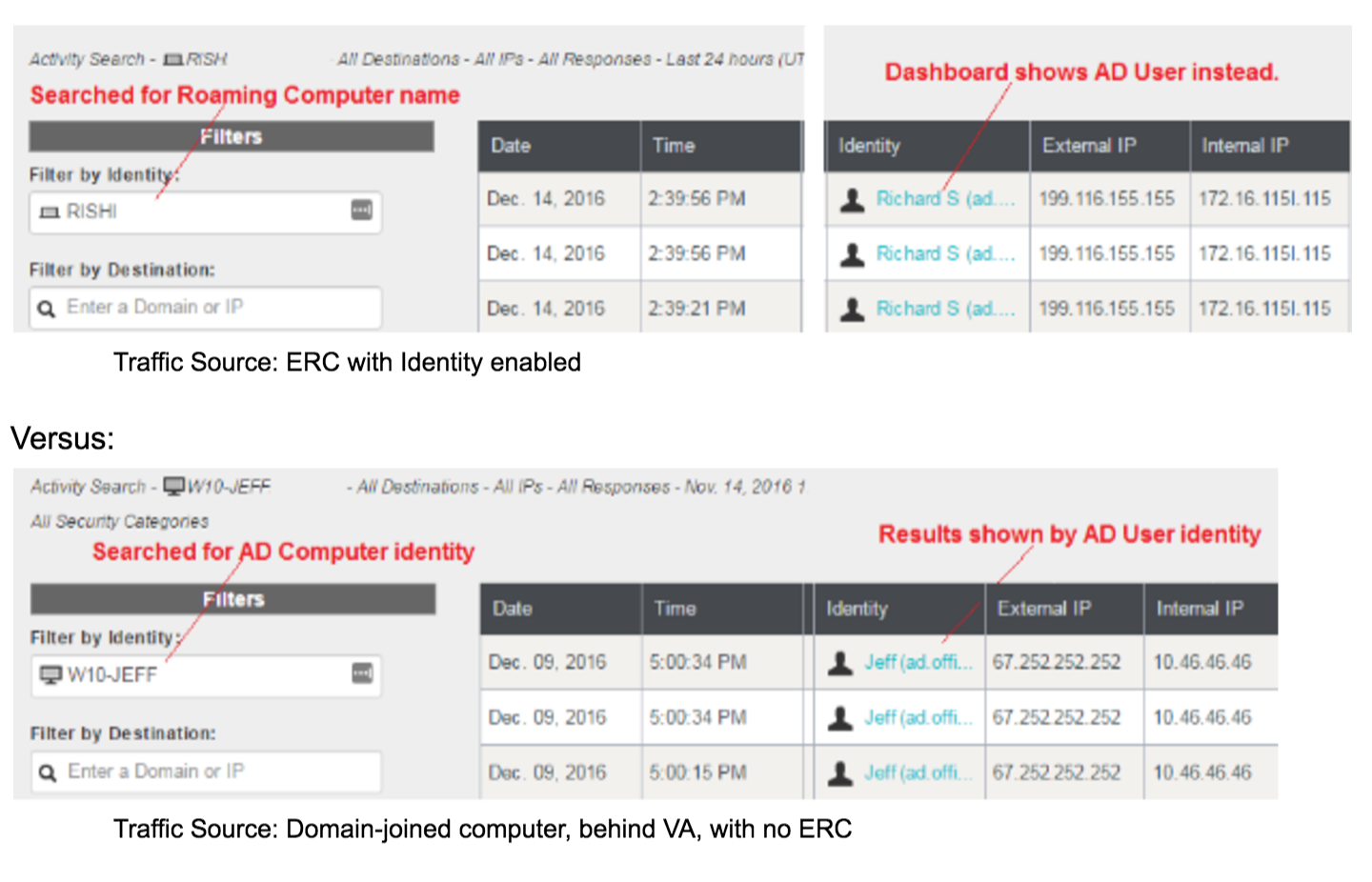
Identity Support in Umbrella Reports
When searching for an AD User, you can view on-network and off-network traffic in the same report, whether behind a VA while on-network or roaming off-network. Use the external IP to differentiate the on-network versus off-network activity.
View Traffic in Umbrella
Umbrella reports traffic sent from roaming clients similarly to traffic sent from a VA. Multiple identity types are associated with each query. Umbrella chooses which identity to display by default in the reports. Typically, the identity that matches the active policy is shown. Searching on the other identity types displays the same traffic.
What Information is Sent to Cisco Umbrella and When
AD Directory Structure
The AD Connector is used to upload the AD directory structure, and sync on changes. The AD Connector’s sync behavior is identical to when it is deployed with a VA. Only one AD Connector is needed for an organization, not one per site like the VA.
Informational Warnings for the Connector
If no VA is present, the AD Connector appears in an info state instead of the active (green) state. You can view the info states in Umbrella under Settings > Sites and Active Directory.
AD User ID
If the roaming client is running in unencrypted (transparent) mode, Umbrella sends an encoded version (hash) of the logged-in user's ID, preventing information leakage. The roaming client must meet all of these conditions to send the AD user information:
- Enable Identity feature in Umbrella
- An AD Connector is present and active
- Only one AD user is logged into the endpoint
Examples of when the AD user ID is sent or not:
- If two users are logged-on, the roaming client does not send the user ID for either user.
- If a non-AD user is logged-on, the roaming client does not send the user ID.
- If one AD user is logged-on, the roaming client sends the user ID, and then if you switch users to another user (AD or otherwise), without logging-out as the first user, the roaming client stops sending the user ID.
Note: The roaming client does not require an active connection to the domain controller or any AD server. The roaming client retrieves the user ID locally. Additionally, the roaming client does not utilize logon event and IP mapping like the VA.
User Group
User group (AD security group) information is sent from the AD Connector. The roaming client sends the AD user ID and relies on the cloud to find the correct user group(s). This is the same behavior as the VA.
LAN IP Address
The LAN IP address is always sent as long as the identity feature is enabled in Umbrella. The LAN IP address is always an IPv4 address. Umbrella makes its best effort to determine which network adapter is used, for example: a laptop having a wired and wireless connection simultaneously active. If Umbrella is unable to determine which network adapter is active, it returns the first non-reserved IP addresses in use by the device.
Important: Policy cannot be set or enforced on the LAN IP returned by the roaming client. The inclusion of LAN IP is only for visibility and reporting purposes. By comparison, only with a VA, and a Site and an Internal Network identity can Umbrella enforce a policy on LAN IP.
Device ID
The (non-AD) device ID is always sent. The roaming client behavior does not change.
Configure Policies < Identity Support for the Roaming Client > Status, States, and Functionality
Updated over 1 year ago