Add a Firewall Rule
The Umbrella cloud-delivered firewall provides firewall services without the need to deploy, maintain, and upgrade physical or virtual appliances at each site. The cloud-delivered firewall relies on your on-premise appliances to build tunnels to the Umbrella cloud without the need to upgrade or deploy any additional physical or virtual appliances.
Through the firewall rules written in the Umbrella dashboard, you can filter traffic at layer 3 and layer 4 that originates on the internal network but is destined for the internet. You can block apps at layer 7 as well.
Table of Contents
Prerequisites
- An internet connection that allows outbound IPsec traffic.
- An Umbrella account with the cloud-delivered firewall feature enabled.
- A network device capable of establishing an IPsec IKEv2 tunnel. For supported network devices, see Supported IPsec Parameters.
- Tunnel passphrase obtained from the Umbrella dashboard.
- At least one tunnel added. For more information about adding tunnels, see Network Tunnel Configuration.
Procedure
- Navigate to Policies > Management > Firewall Policy and click Add.

If Umbrella displays the message "You are missing a tunnel connection," click Add A Tunnel. Tunnels are required for firewall rules. For more information about adding tunnels, see Network Tunnel Configuration.

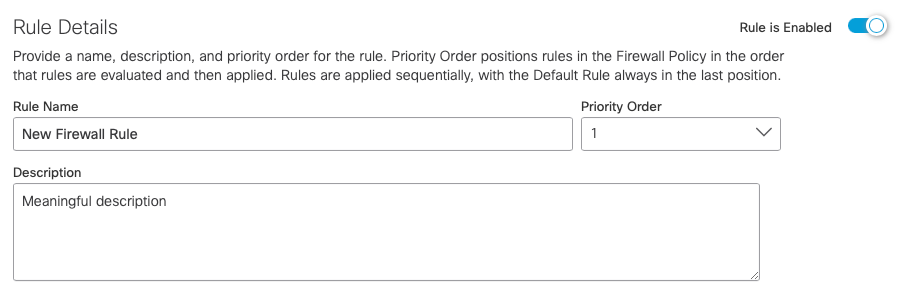
- Define the basic characteristics of your firewall rule:
a. Choose a descriptive Name and Description.
b. Choose a Priority Order. Priority Order positions rules in the Firewall Policy in the order in that rules are evaluated and then applied. Rules are applied sequentially, with the Default Rule always in the last position.
c. Enable or Disable your firewall rule.
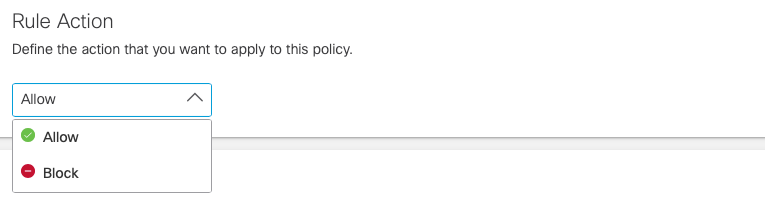
- Under Rule Action, choose Allow or Block.
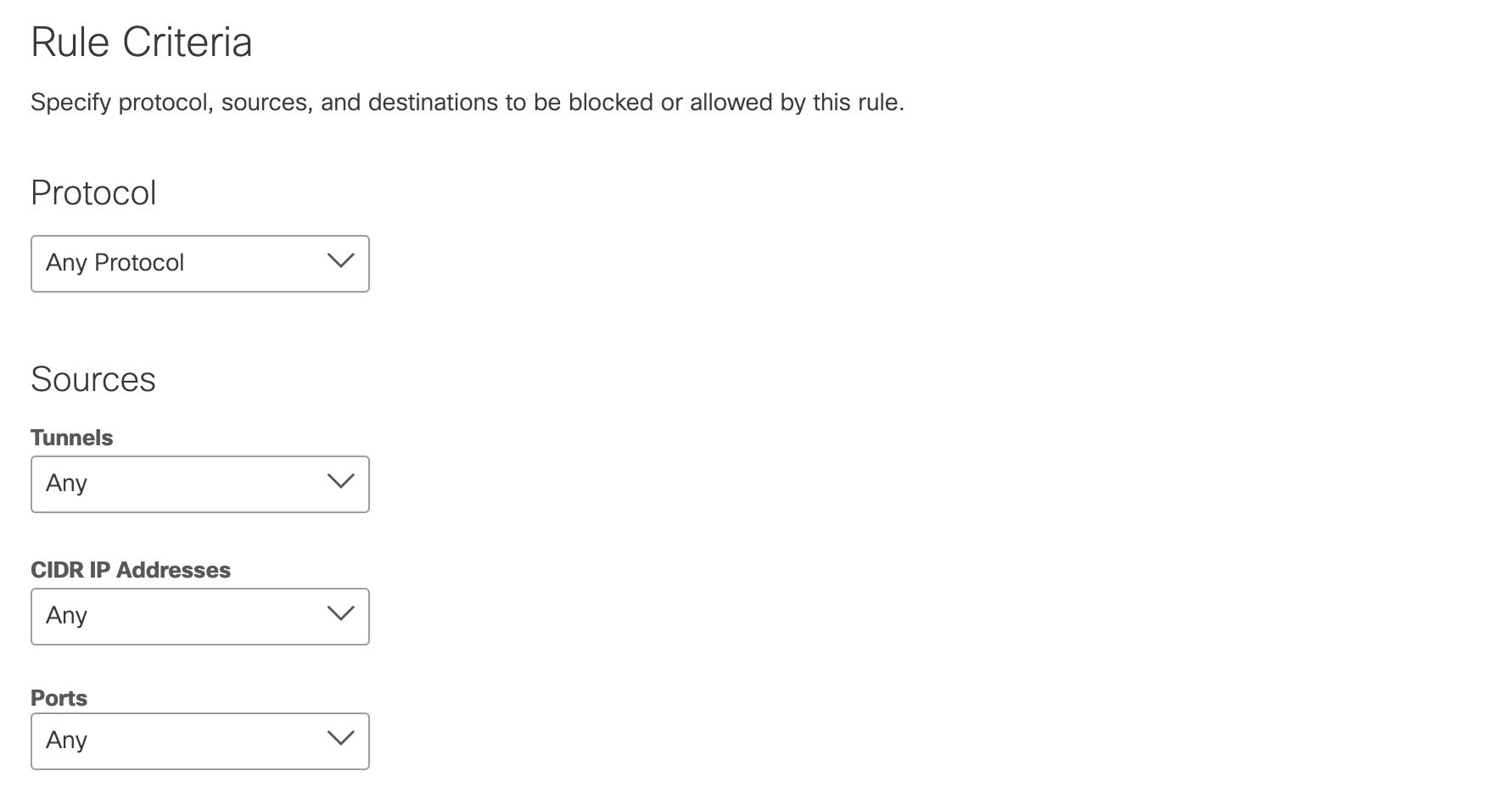
- Choose the rule's criteria.
a. Protocol—The protocols to which the rule applies. Options are TCP, UDP, ICMP, or any.
b. Source Tunnels—The source tunnel to which the rule applies. Search for tunnels to add them. Up to three tunnels are displayed dynamically as you begin entering text.
c. Source CIDR IP Addresses—The tunnel's source addresses (IP or CIDR) to which the rule
applies. You can choose Specify IP and add each CIDR IP address, or choose Any.
d. Source Ports—The tunnel's source ports to which the rule applies. You can choose Specify Port and enter ports or port ranges in a comma-delimited plain-text list, or choose Any.
e. Destination CIDR IP Addresses—The tunnel's destination addresses (IP or CIDR) to which the rule applies. You can choose Specify IP and add each CIDR IP address, or choose Any.
f. Destination Ports—The tunnel's destination ports to which the rule applies. You can choose Specify Port and enter ports or port ranges in a comma-delimited plain-text list, or choose Any.
g. Applications—The applications and application categories to which the rule applies. For more information, see Application Categories.

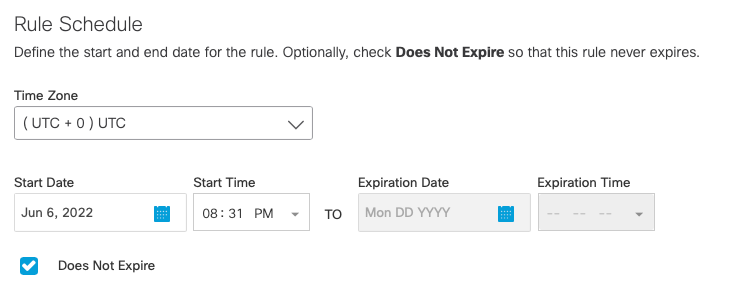
- Choose a Time Zone and configure Start and Expiration dates and times. Optionally, check Does Not Expire so that your rule will not expire.
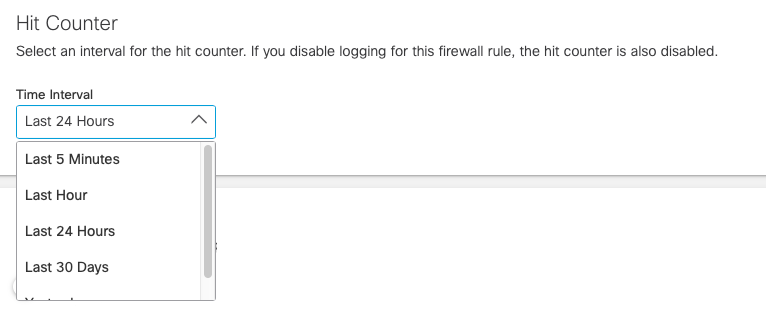
- Select an interval for the hit counter. If you disable logging for this firewall rule, the hit counter will also be disabled. For more information, see Monitor Hit Count.
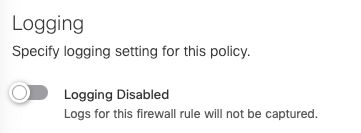
- Enable or Disable logging.
Note: Logging is disabled by default. If you disable logging, the hit counter will also be disabled.
- Click Save.
Network Tunnel Identity
By selecting a Network Tunnel identity in a firewall rule, the following identities may also apply to the firewall rule:
- Internal Network
- Network
Firewall Rule Settings
You can add Network Tunnel identities and define actions, ports, protocols, and applications in a firewall rule. Umbrella evaluates each firewall rule, starting with the highest ranked rule. When an identity and destination match a rule, Umbrella applies the action defined in the rule.
For example, if an identity requests a web application on port 80 or 443, Umbrella first checks for a matching firewall rule. If Umbrella finds a matching firewall rule, the cloud-delivered firewall (CDFW) applies the action defined in the rule.
For web application requests, Umbrella applies this sequence of checks.
- Umbrella first matches a firewall rule to an identity and destination.
- If the matching rule defines a Block action, the Umbrella cloud-delivered firewall blocks the request.
- If the matching rule defines an Allow action, the Umbrella cloud-delivered firewall forwards the request to the Umbrella secure web gateway (SWG). The secure web gateway applies the security settings defined in the Web policy. To learn about the Umbrella Web policy, see Manage the Web Policy.
Manage the Firewall Policy < Add a Firewall Rule > Add an FQDN List to a Firewall Rule
Updated about 1 year ago
