Troubleshoot Virtual Appliances
Table of Contents
- Reset a Virtual Appliance's Password
- Use Configuration Mode to Troubleshoot
- Establish a Support Tunnel From the VA
- Troubleshoot Intermittent DNS Resolution Failures on a VA Deployed on Azure Platforms
- Troubleshoot Intermittent DNS Resolution Failures on a VA Deployed on non-Azure Platforms
- Troubleshoot DNS Resolution in Configuration Mode
- Troubleshoot DNS Resolution Failures Behind a Firewall
Reset a Virtual Appliance's Password
If you forget a virtual appliance's (VA’s) password, you can reset it through the Sites and Active Directory page.
- Navigate to Deployments > Configuration > Sites and Active Directories.
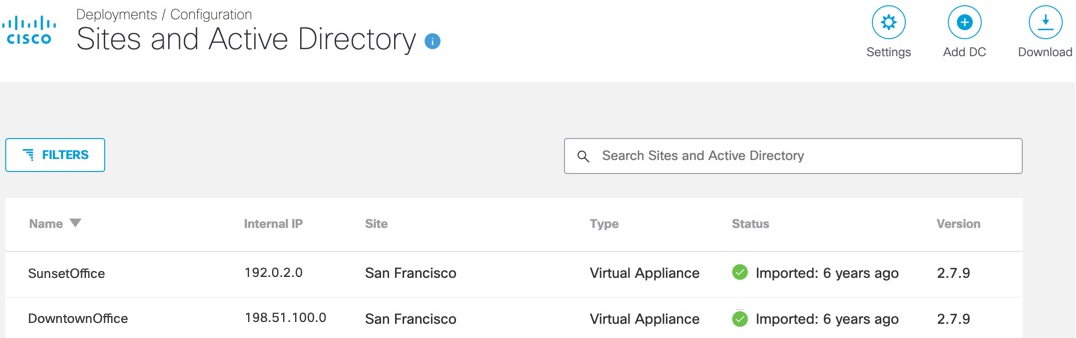
- Hover over a VA listing and click the Reset Password icon.
Note: The Reset Password icon only appears when you hover over a VA listing.
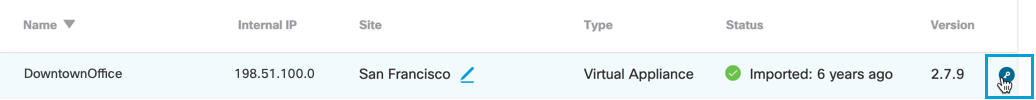
- Click Reset to confirm that you want Umbrella to generate a new password for the VA.
Note: It can take up to 15 minutes for the password to be reset.
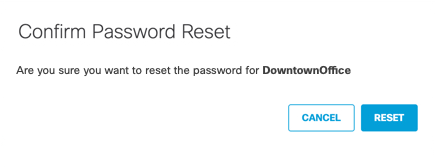
- Click Download to retrieve the reset password.

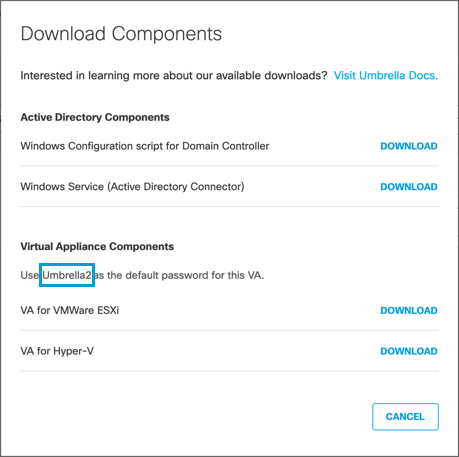
Umbrella lists a new password in the Virtual Appliance Components section of the Download Components modal.
Use Configuration Mode to Troubleshoot
The virtual appliance (VA) allows basic troubleshooting commands to be executed using the Configuration Mode. See Virtual Appliance Commands for a complete list of commands supported by the VA.
- To enter the Configuration Mode, on the VA console, press Ctrl+B.
You can also enter the Configuration Mode by initiating an SSH connection to the VA.
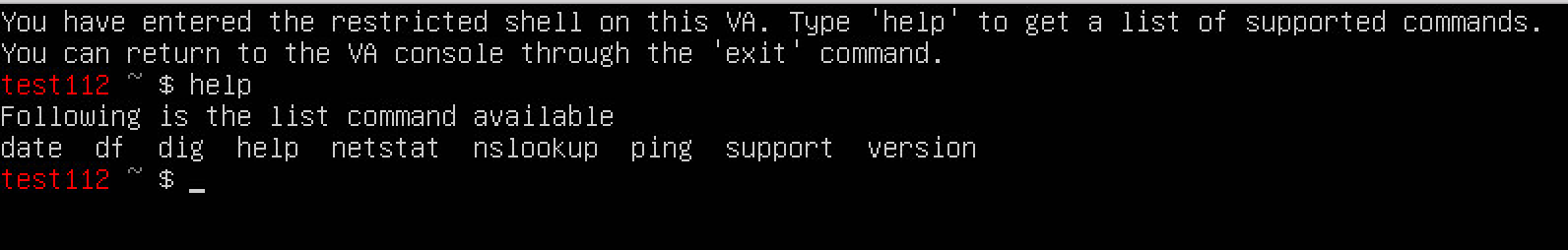
- To view a list of supported commands in the restricted shell, enter help.
- To return to the VA console, type exit.
If the VA console crashes, the VA automatically enters the restricted shell. In this case, contact Support and use the config command to set up an on-demand SSH tunnel to Umbrella. To assist Support, include the tunnel's parameters in the support ticket.
Establish a Support Tunnel From the VA
If you have raised a support ticket with Umbrella for any VA-related issues, you may be asked to set up an on-demand Support tunnel from the VA. For more information, see On-Demand Tech Support SSH Tunnel for Virtual Appliances.
Troubleshoot Intermittent DNS Resolution Failures on a VA Deployed on Azure Platforms
If you have deployed the VA on Azure as a stand-alone virtual machine (VM) without a public IP address, you might experience intermittent DNS resolution issues when heavy DNS traffic is directed at the VA. This is due to SNAT port exhaustion on virtual machines deployed to Azure (such as the VA) because Azure only pre-allocates 1024 UDP ports for standalone VMs without a public IP address. To address this issue, you may either need to assign a public IP to each VA or deploy VAs behind a public Standard Load Balancer in Azure.
Note: If you are assigning a public IP to a VA, make sure that there are no inbound port rules for this VA that allow inbound access from the internet.
Troubleshoot Intermittent DNS Resolution Failures on a VA Deployed on non-Azure Platforms
Although less common, SNAT port exhaustion can also occur on virtual machines (VMs) deployed on non-Azure platforms. For more information, see Port Exhaustion When Using Port Address Translation with Umbrella components.
Troubleshoot DNS Resolution in Configuration Mode
The 'nslookup' command can be used to test DNS queries on the VA. This test reflects how a users' DNS lookups will be answered and is subject to internal domains routing and other processing on the VA.
You can specify a server IP address as a parameter for nslookup. This is useful for testing a Local DNS server or the Umbrella cloud directly. These tests bypass the VA software.
Troubleshoot DNS Resolution Failures Behind a Firewall
The VA offers DNScrypt functionality that protects the content of your DNS queries. This functionality may be blocked by your firewall.
If you are using the Cisco ASA firewall, you can see an indication of this in the ASA log.
For example:
Dropped UDP DNS request from inside:192.168.1.1/53904 to outside-fiber:208.67.220.220/53; label length 71 bytes exceeds protocol limit of 63 bytes
DNS resolution is not affected by this blocking, but your DNS queries are not fully protected. For more information, see Cisco ASA Firewall blocks DNSCrypt.
To address this, ensure that your firewall allows outbound queries on port 443 and 5353 for both TCP and UDP to the Umbrella resolver IP addresses as mentioned in the Pre-requisites section.
SNMP Monitoring < Troubleshoot Virtual Appliances > Other Configurations
Updated over 1 year ago
