Umbrella Policies Overview
Umbrella policies provide a unified point of configuration of the Umbrella DNS-layer security, cloud-delivered firewall (CDFW), and secure web gateway (SWG). Umbrella's core policy types are DNS, web, firewall, and data loss protection (DLP).
Table of Contents
- Traffic Flow Through Umbrella
- How Umbrella Applies Policies
- DNS Policy
- Firewall Policy (CDFW)
- Web Policy (SWG)
- Data Loss Prevention (DLP) Policy
Traffic Flow Through Umbrella
Traffic forwards to Umbrella from networks, IPsec tunnels, network devices, and client connectors and forwarders. Umbrella represents a network entity, user, or group as an identity in an Umbrella policy. Umbrella policy settings apply to an identity and a destination.
When Umbrella receives a destination request from an identity, Umbrella applies the enabled DNS policies to the destination. If the Umbrella DNS-layer security does not block the destination, Umbrella forwards web traffic to the cloud-delivered firewall and the secure web gateway. If HTTPS inspection is enabled on the web policy, the DLP policy monitors and blocks sensitive data transmission in outbound web traffic.
The following diagram displays how traffic flows from network entities and client connectors through Umbrella.
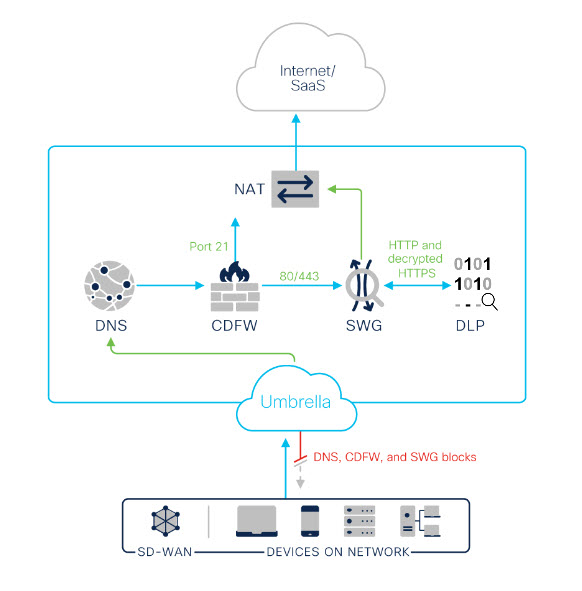
How Umbrella Applies Policies
- Upon receiving a DNS request, Umbrella matches an enabled DNS policy to an identity and destination. The DNS-layer security applies the action defined in the DNS policy.
- If you enable a Firewall policy, Umbrella forwards any requests allowed by the DNS-layer security to the cloud-delivered firewall. The Umbrella cloud-delivered firewall either filters the request or forwards the web traffic on port 80 or 443 to the secure web gateway (SWG).
- If you enable a web policy, the Umbrella secure web gateway (SWG) evaluates web traffic on ports 80 and 443 and applies the actions defined in the web policy.
- If you enable HTTPS inspection in the web policy, the DLP policy monitors and optionally blocks sensitive data detected in outbound web traffic.
- Next, allowed traffic egresses through Network Address Translation (NAT).
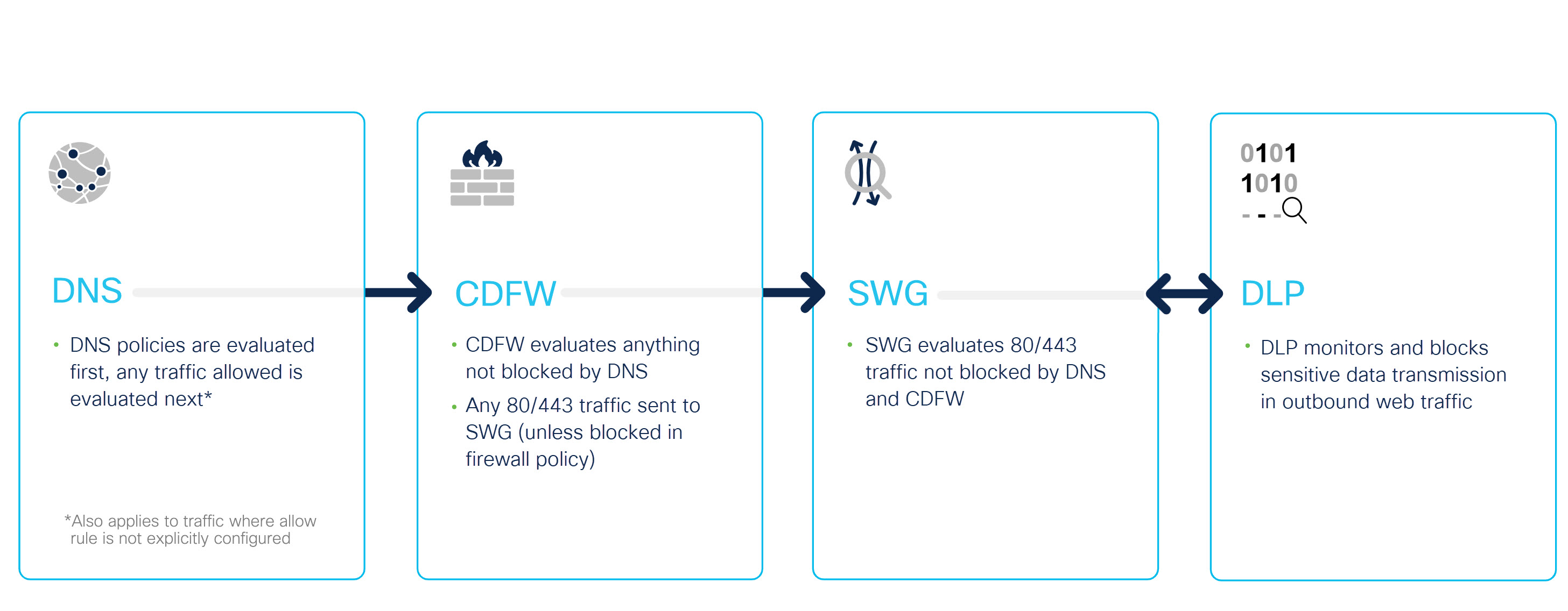
DNS Policy
The Umbrella DNS policy enables the configuration and access control settings of the DNS-layer security for an identity.
- For more information about the DNS policy, see Manage DNS Policies.
- For information about Umbrella identities and DNS policies, see DNS Policy Precedence and Best Practices for DNS Policies.
Firewall Policy (CDFW)
The Umbrella Firewall policy enables the configuration and access control settings of the Umbrella cloud-delivered firewall (CDFW). In the Firewall policy, you can add destinations (ports, protocols, and applications) and IPsec tunnels. The cloud-delivered firewall (CDFW) filters web traffic on non-standard ports and standard web ports (80 or 443).
- For more information about the Firewall policy, see Manage the Firewall Policy.
- For information about setting up a Firewall rule, see Add a Firewall Rule.
Web Policy (SWG)
The Umbrella web policy describes the URL-layer visibility in your network and enables the configuration and access control settings of the Umbrella secure web gateway (SWG). The secure web gateway evaluates web requests on port 80 or 443. The secure web gateway provides full URL reporting, content control, malware scanning and evaluation by antivirus engines, full or selective SSL decryption, and app visibility.
If you enable HTTPS inspection on the web default policy, or on as least one web policy ruleset where the same identity is configured in a data loss prevention (DLP) policy rule, the DLP can monitor and optionally block outgoing web traffic.
- For more information about the Web policy, see Manage the Web Policy.
- For information about Umbrella identities and the Web policy, see Web Policy Precedence, and Best Practices for the Web Policy and Rulesets.
Data Loss Prevention (DLP) Policy
If HTTPS inspection is enabled on the web default policy or on at least one web policy ruleset where the same identity is configured in a DLP rule, the DLP policy can monitor and optionally block outgoing web traffic. The DLP policy rules define which traffic to monitor based on identities and destinations, the data classifications that require monitoring, and whether content should be blocked or only monitored. The DLP policy provides two types of rules, and a feature called Discovery Scan:
- Real-time rules define what web proxy traffic to monitor (based on identities and destinations), the content or document properties to search for, and whether content should be monitored or blocked.
- SaaS API rules use cloud tenant APIs to scan for data violations in cloud-stored files. As files in the selected tenant change in content or context (sharing), Umbrella assesses the changed file against rule criteria and enforces the rule action when a match is found. Rule actions vary depending on the platform being scanned.
- Discovery Scan inspects the content of all files in a selected tenant that are modified over a selected date range. As files in the selected tenant change in content or context (sharing), Umbrella assesses changed files against both real-time rules and SaaS API rules and if a violation is detected, the offending file is listed in the Data Loss Prevention Report.
For more information about elements of the DLP policy, see:
- Manage the Data Loss Prevention Policy
- Add a Real-time Rule to the Data Loss Prevention Policy
- Add a SaaS API Rule to the Data Loss Prevention Policy
- Manage Data Classifications
- Discovery Scan
- Data Loss Prevention Report
Determine Your Current Package < Umbrella Policies Overview > SWG Data Centers
Updated almost 2 years ago
