Configure Tunnels with Alibaba Cloud IPsec
Alibaba Cloud VPN Gateway is an Internet-based service that securely and reliably connects enterprise data centers, office networks, and Internet terminals to virtual private clouds (VPCs) of Alibaba Cloud through encrypted channels.
Alibaba Cloud IPsec-VPN connects networks based on routes. It facilitates the configuration and maintenance of VPN policies and provides flexible traffic routing methods. You can use IPsec-VPN to connect a data center to a VPC or connect two VPCs. IPsec-VPN supports the IKEv1 and IKEv2 protocols. All on-premises gateway devices that support these two protocols can connect to VPN gateways on Alibaba Cloud.
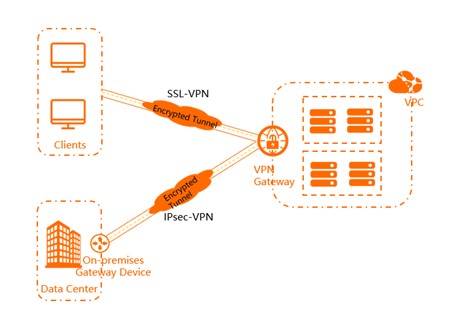
Table of Contents
Configure Tunnels in Umbrella
You must select an Umbrella SIG Data Center IP address to use when creating the IPsec tunnel.
In the sample commands, <umbrella_dc_ip> refers to this IP address. We recommend choosing the IP address based on the data center located near to your device. For more information, see Connect to Cisco Umbrella Through Tunnel.
- Navigate to Deployments > Core Identities > Network Tunnels, and then click Add.
- Enter an appropriate name in the Tunnel Name field and choose Other from the Device Type drop-down list.
- Under Tunnel ID Format, click the IP Address radio button and enter the Alibaba Cloud VPC NAT gateway public IP address in the IP Address field. Enter the same Pre-Shared-Key (PSK) Passphrase in the Passphrase and the Confirm Passphrase fields.
- Choose an appropriate site from the Associate Tunnel with Site drop-down list and optionally, enter an IP address to the IP Address Ranges field which you would like to send to Umbrella SIG.
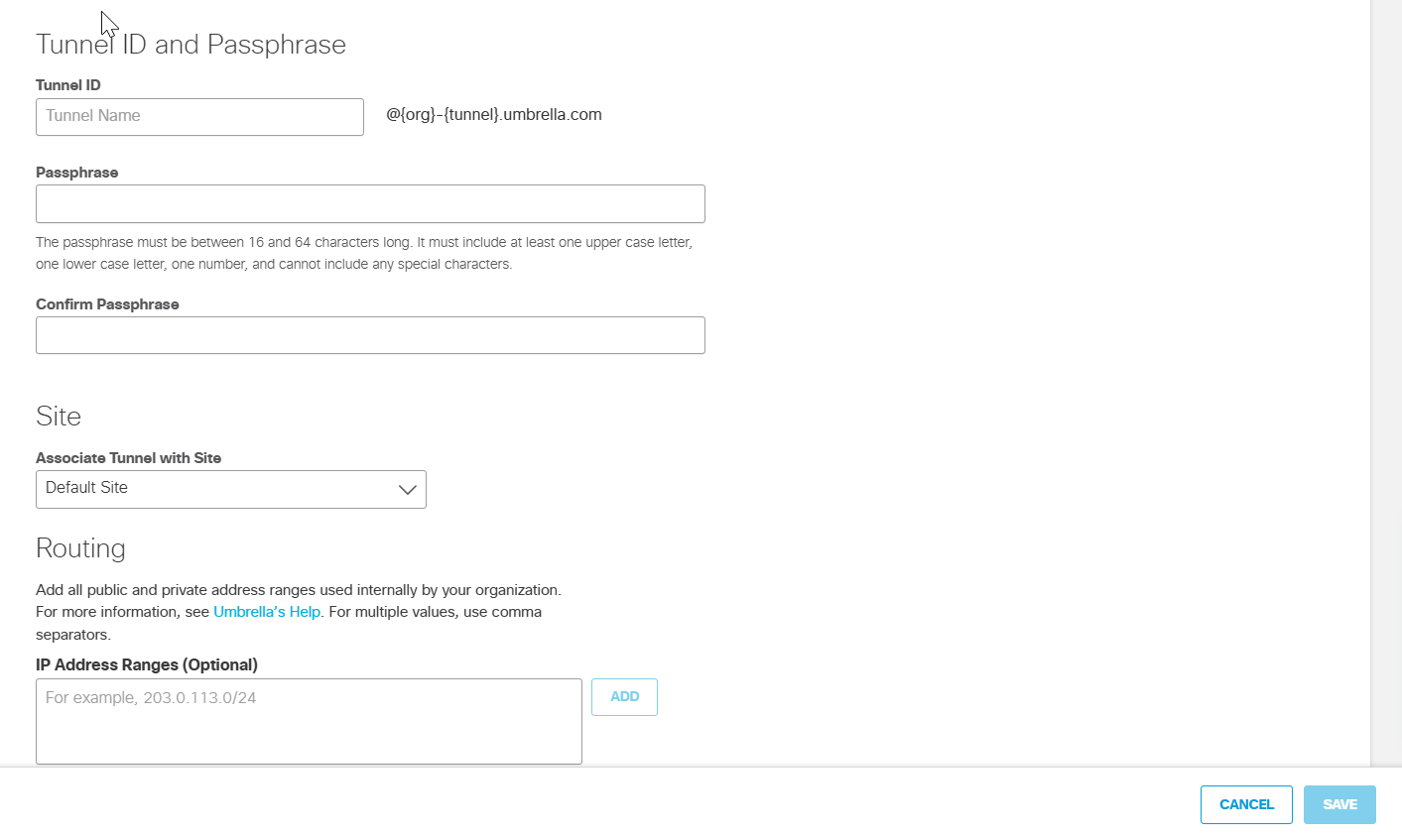
- Click Save and then copy the Tunnel ID and Passphrase.
The new tunnel appears in the Umbrella dashboard with a status of Not Established. The tunnel status is updated once it is fully configured and connected with Alibaba Cloud IPSec VPN.
Configure Alibaba Cloud IPsec VPN
Prerequisites
Before you use IPsec-VPN to connect a data center to a VPC, the following requirements must be met:
- The gateway device in the data center supports the IKEv1 and IKEv2 protocols.
- IPsec-VPN supports the IKEv1 and IKEv2 protocols. All gateway devices that support these two protocols can connect to VPN gateways on Alibaba Cloud.
- A static public IP address is assigned to the gateway device in the data center.
- The CIDR block of the data center does not overlap with the CIDR block of the VPC.
- You must read and understand the security group rules that apply to the Elastic Compute Service (ECS) instances in the VPC, and the security rules allow gateway devices in the data center to access cloud resources.
Procedure
- Create a VPN Gateway—Enable the IPsec-VPN feature for the VPN gateway. You can create multiple IPsec-VPN connections for each VPN gateway.
- Create a Customer Gateway—Register the information about the gateway device in the data center to Alibaba Cloud through a customer gateway.
- Create an IPsec-VPN Connection—Connect a VPN channel between the VPN gateway and the gateway device in the data center. The data center can exchange encrypted data with Alibaba Cloud only after an IPsec-VPN connection is created.
- Configure the On-premises Gateway Device—Load the configuration of the VPN gateway on Alibaba Cloud to the gateway device in the data center. For more information, see Configure an H3C firewall device.
- Configure Routes for the VPN Gateway—Configure routes for the VPN gateway and advertise these routes to the VPC route table so the VPC and the data center can communicate with one another. For more information, see VPN Gateway route overview.
- Test the Connectivity—Log on to an Elastic Compute Service (ECS) instance that is not assigned a public IP address in the VPC. Run the ping command to ping the private IP address of a server that resides in the data center and test the connectivity.
Create a Customer Gateway
You can use a customer gateway to establish an IPsec-VPN connection between a virtual private cloud (VPC) and a data center or between two VPCs. After you create a customer gateway, you can update the information about a gateway device in the data center to Alibaba Cloud. Then, you can connect the customer gateway to a VPN gateway. A customer gateway can connect to multiple VPN gateways.
- Log in to Alibaba Cloud VPN Gateway console and navigate to Interconnections > VPN > Customer Gateways.
- Select the region where you want to create the customer gateway.
Note: You must deploy the customer gateway and the VPN gateway to be connected in the same region. - Under Customer Gateways, click Create Customer Gateway, then set the following parameters:
- Name—a name between 2 and 128 characters in length. It must start with a letter, and can include digits, underscores, and hyphens.
- IP Address—the static public IP address of the gateway device in the closest Umbrella data center. For more information, see Connect to Cisco Umbrella Through Tunnel.
- ASN—the autonomous system number of the gateway device in the data center.
Note: This is required when the VPN gateway has dynamic BGP enabled. - Description—a description for the customer gateway between 2 and 100 characters in length. It must start with a letter and can include digits, underscores, and hyphens.
- Click OK.
Create an IPsec-VPN Connection
When using Alibaba Cloud IPsec-VPN to create a site-to-site connection, you must configure the local gateway according to the IPsec connection configured for the Alibaba Cloud VPN Gateway. For more information, see Create and manage IPsec-VPN connections.
Before You Configure
- Make sure you have configured IPsec connections. For more information, see Connect a data center to a VPC.
- After you create an IPsec-VPN connection, download the configurations of the IPsec-VPN connection.
Following is an example of configuring the IPsec-VPN connection:
- Customer Gateway—includes the IP address of the closest Umbrella data center.
- Pre-Shared Key—is the Pre-Shared Key from the Umbrella dashboard.
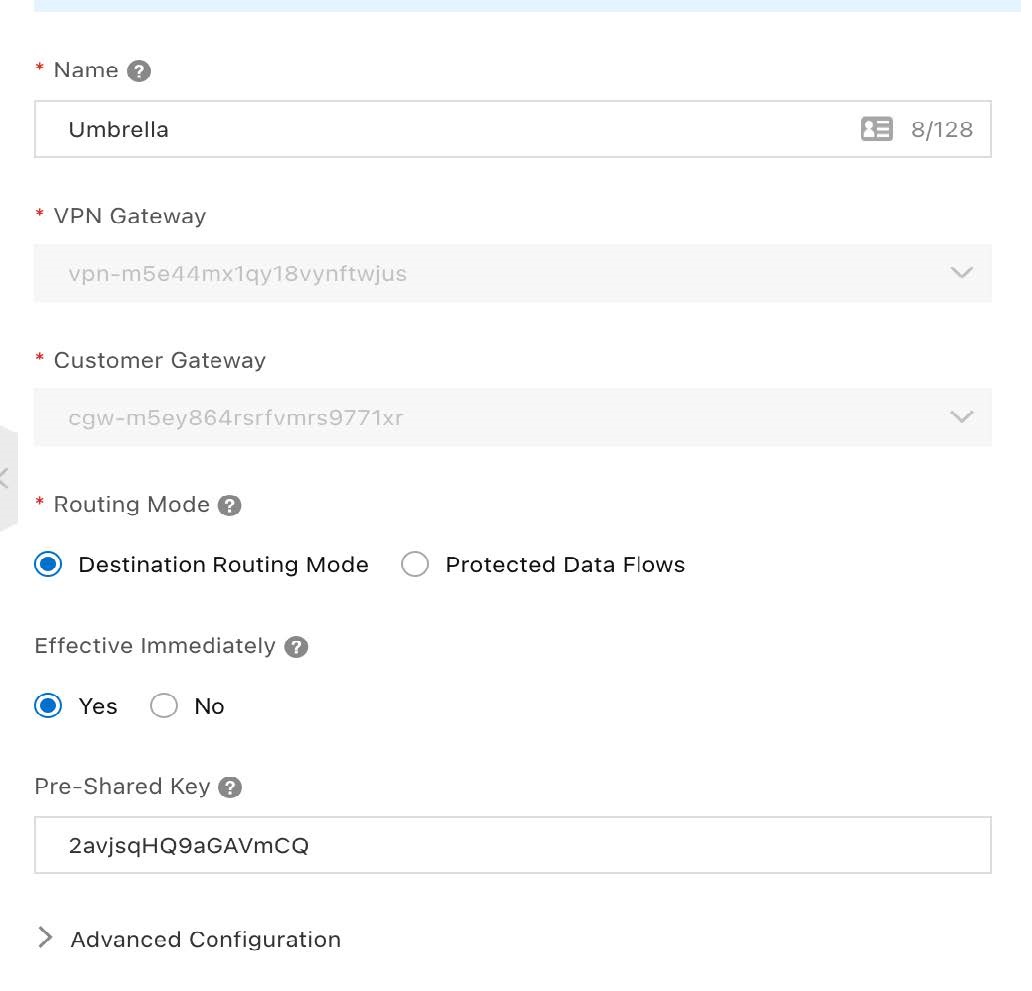
Under Advanced Configuration, for IKE Configurations:
- Version—ikev2
- Negotiation Mode—main
- Encryption Algorithm—aes256
- DH Group—group14
- SA Life Cycle (seconds)—86400
- Local ID—IP (address of local Alibaba Cloud NAT Gateway IP address)
- Remote ID—IP (address of nearest Umbrella data center)
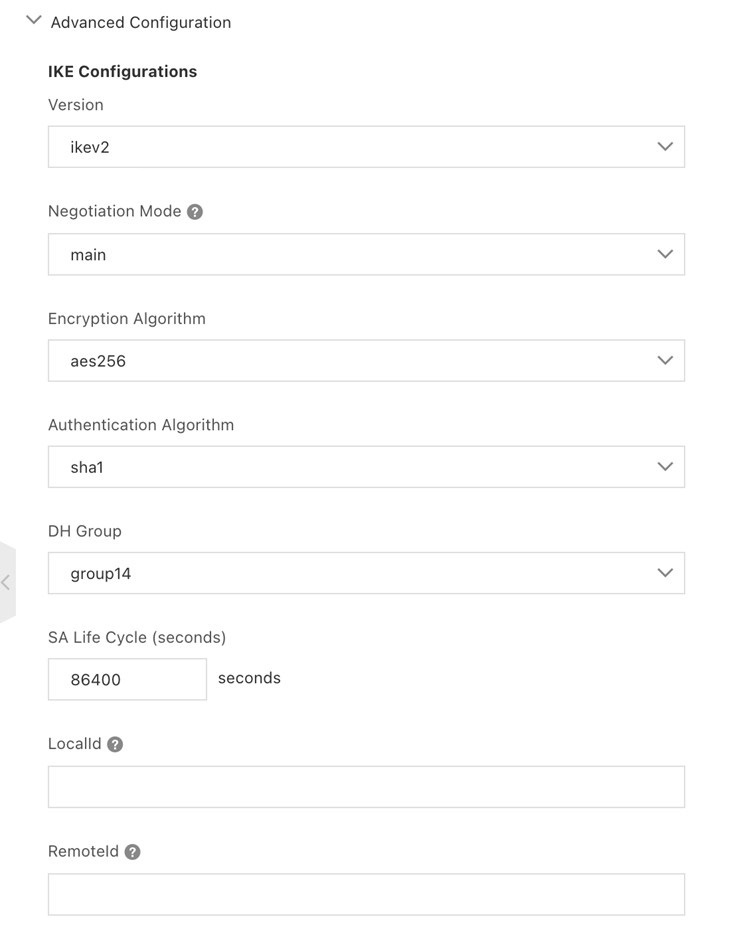
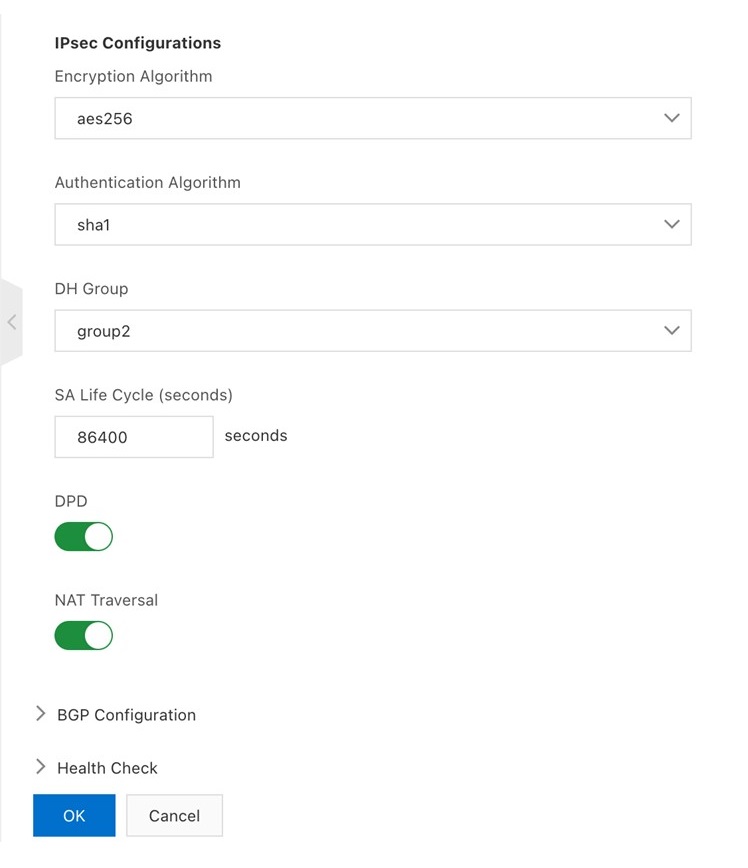
Under Advanced Configuration, for IPsec Configurations:
- Encryption Algorithm—aes256
- Authentication Algorithm—sha1
- DH Group—group2
- SA Life Cycle (seconds)—86400
- DPD—On (click toggle button to on status (green))
- NAT Transversal—On (click toggle button to on status (green))
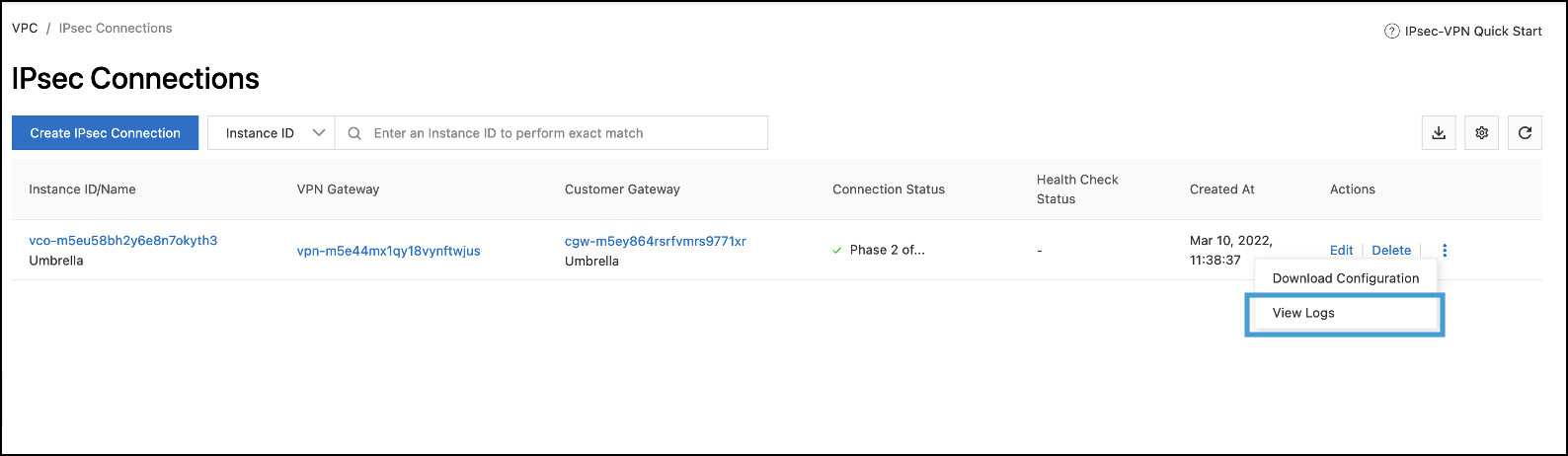
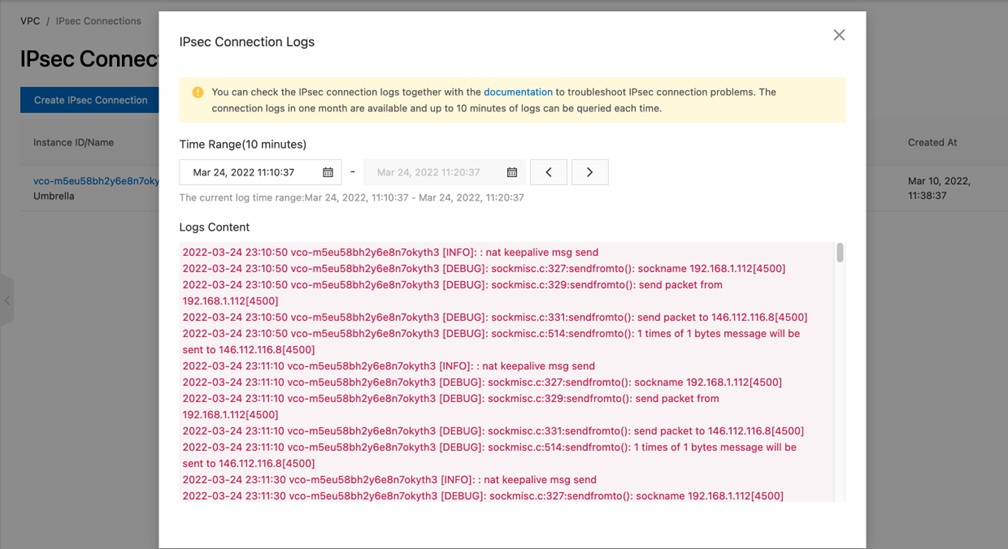
View Logs
- In the VPN Console, navigate to VPC > IPsec Connections. Find the connection, click the Action menu, and select View Logs.
Configure Tunnels with Palo Alto IPsec < Configure Tunnels with Alibaba Cloud IPsec > Configure Tunnels with Palo Alto Prisma SDWAN
Updated about 1 month ago
