Cisco SD-WAN Powered by Catalyst SD-WAN and Umbrella
This guide is for Cisco Catalyst SD-WAN (formerly known as Viptela) customers who need to enable Umbrella DNS services. For instructions on connecting an Cisco Catalyst SD-WAN device to Umbrella SIG, see Configure Tunnels Manually with Viptela vEdge or Configure Tunnels Manually with Viptela cEdge.
Cisco’s SD-WAN and Umbrella integration enables you to deploy Umbrella across your SD-WAN to hundreds of devices in minutes and instantly gain web and DNS-layer protection against threats. You gain the cost-savings and improved performance of direct internet access (DIA) at branch offices, without sacrificing security or the burden of managing devices individually.
With the integration, administrators can create policies and view reports on a per-VPN basis.
This document details how to configure Umbrella DNS redirect security policies with Cisco SD-WAN. For more comprehensive information about configuring additional Cisco SD-WAN Security policies, see the SD-WAN Security Deployment Guide.
For more information about Cisco SD-WAN hardware compatibility, see the SD-WAN Compatibility Matrix.
Notes: Automatic policy assignment based on VPN name - Cisco Catalyst SD-WAN (Viptela) VPNs, represented by network devices in the Umbrella dashboard, is automatically placed in an Umbrella policy if the Cisco Catalyst SD-WAN (Viptela) VPN name matches the name of an existing Umbrella policy. Otherwise, all Cisco Catalyst SD-WAN (Viptela) VPNs are covered by the Umbrella default policy unless they are manually added to another policy. Policy assignment can be done in the UI or via API.
Prerequisites
- Cisco Catalyst SD-WAN (formerly known as vManage) version 20.1/IOS XE 17.2 or later.
- A security K9 license to enable Umbrella Integration.
The device must be running either:
SD-WAN cEdge IOS XE 16.10 software image or later.
SD-WAN vEdge 20.3.1 software image or later.
Limitations
- If an application or host uses IP address directly instead of DNS to query domain names, policy enforcement is not applied.
- If a client is connected to a web proxy, the DNS query does not pass through the device. In this case, the connector does not detect any DNS request, and the connection to the web server bypasses any policy from the Umbrella portal.
- When the Umbrella Integration policy blocks a DNS query, the client is redirected to a Umbrella block page. HTTPS servers provide these block pages and the IP address range of these block pages is defined by the Umbrella portal.
- The type A, AAAA, and TXT queries are the only records that are redirected. Other types of queries bypass the connector.
- Only the IPv4 address of the host is reported to Umbrella.
- A maximum of 64 local domains can be configured under the bypass list. The allowed domain name length is 100 characters.
Configure Umbrella and Cisco Catalyst SD-WAN
- In the Umbrella dashboard, navigate to Admin > API Keys and click Create.

Authorization: Cisco Catalyst SD-WAN (vManage) Version 19.2/IOS-XE 16.12 and Earlier
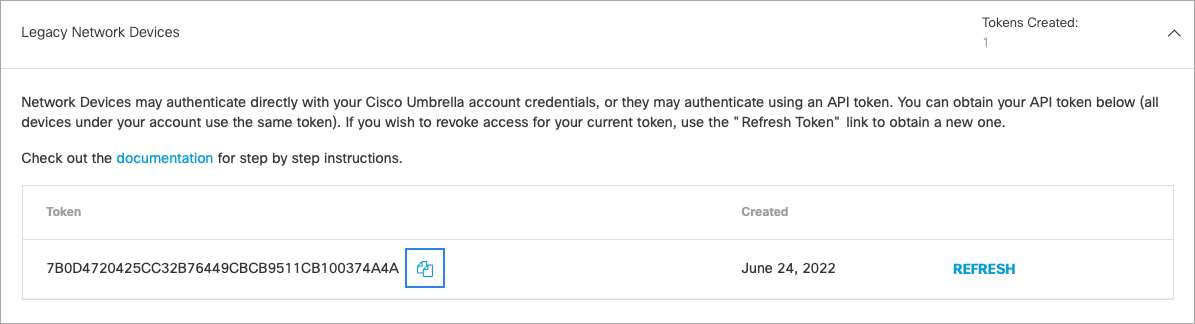
- Expand Legacy Network Devices and click Generate Token.
- Copy your token. The API token is a long alphanumeric set of characters.
Authorization: vManage Version 20.1 and Later
- Expand Umbrella Network Devices and click Generate Token.
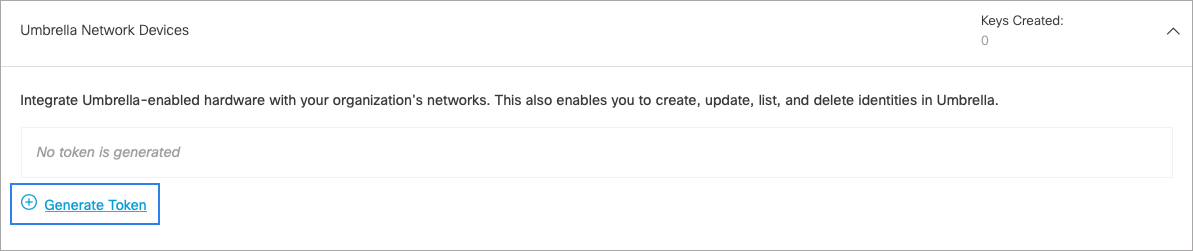
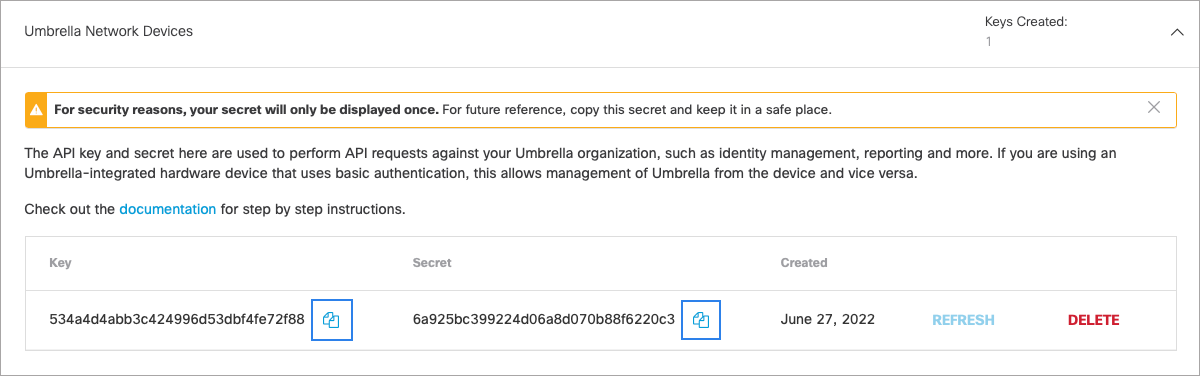
- Copy your Key and your Secret.
Note: You have only one opportunity to copy your Secret. Umbrella does not save it and it cannot be retrieved after its initial creation.
Insert Authorization Data
- In the Cisco Catalyst SD-WAN (vManage) dashboard, navigate to Configuration > Security and click the Custom Options dropdown.
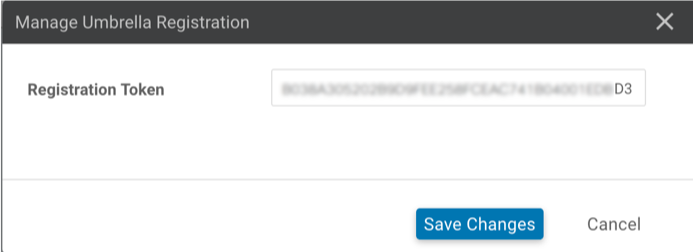
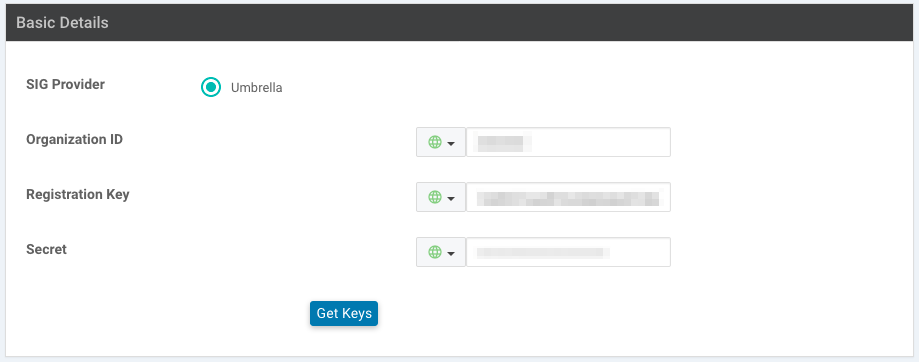
- Select the Umbrella API Token. In the Manage Umbrella Registration box that appears, paste the token (legacy vManage) or the key and secret plus your Umbrella org ID (Cisco Catalyst SD-WAN (vManage) 20.1 and later) into the appropriate fields.
Cisco Catalyst SD-WAN (vManage) pre-20.1:
Cisco Catalyst SD-WAN (vManage) 20.1 and later:
- If you have an existing Security Policy, you can edit that policy to add DNS Security. You can also click Add Security Policy to create a new Security Policy.

- Click Create New, then enter a policy name. Since the Umbrella Token ID has already been applied, Umbrella Registration Status shows “green” (configured).
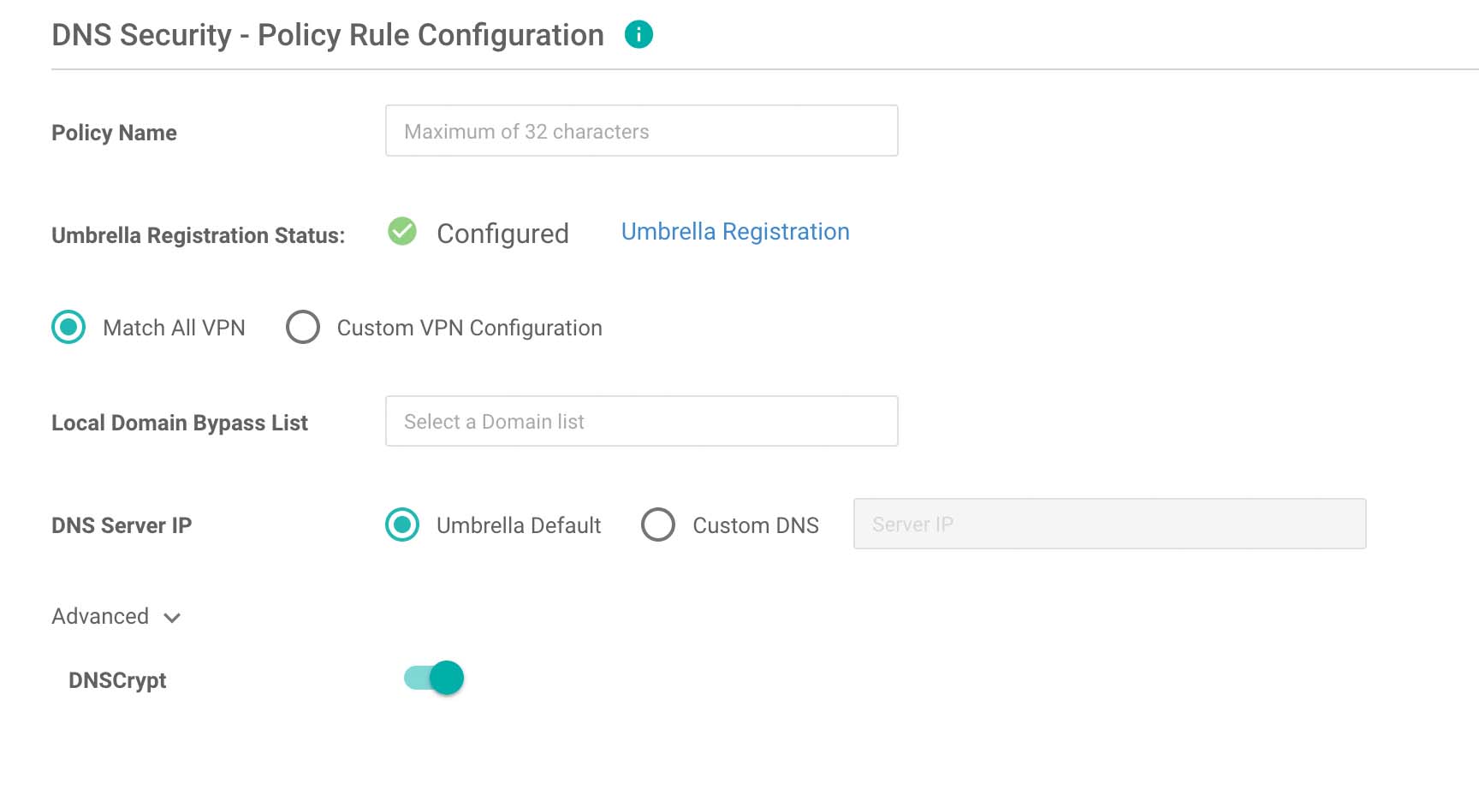
- Choose whether to apply your policy to all VPNs, or only selected VPNs. You can also create a domain bypass list for internal addresses that should not be redirected to Cisco Umbrella.
- Under Advanced settings, you can optionally enable DNSCrypt to encrypt DNS packets with EDNS (Device ID and Client IP) data.
- Click Save DNS Security Policy.
- You should now see a Network Device identity in the Umbrella dashboard for each VPN that was registered. If the VPN name at the time of registration matched an existing policy name in the Umbrella dashboard, then the Network Device representing that VPN will automatically be placed into that Umbrella policy. Otherwise, all VPNs as represented by Network Devices will be part of the default Umbrella policy.
Configure Mobility Express for Umbrella < Cisco SD-WAN powered by Catalyst SD-WAN and Umbrella > Integration for RV-series Routers
Updated almost 2 years ago
