Configure Web Policies and Destination Lists
Table of Contents
- Configure Ruleset Identities of Web Policy
- Configure Web Policy Rules
- Configure Destination Lists
- Configure Application Settings
- Configure HTTPS Inspection Policy
- Configure Active Directory (AD) Users and Groups
- Configure Microsoft 365 Compatibility
After successful registration, the Web policies get translated and pushed from Umbrella to Secure Web Appliance. The following policies are translated to SWA:
Configure Ruleset Identities of Web Policy
The Ruleset Identities of Web Policies in Umbrella are translated as one global Identification Profile with Authenticate option (if AD is integrated in Umbrella) or with an Exempt from Authentication option (if AD is not integrated in Umbrella) in SWA.
The Web policy is made up of rulesets and their rules. Through these configurations, the Web policy defines how security and access controls are applied to identities and the destinations they visit. By adding and configuring rulesets and rules, you determine when and how traffic is inspected and then allowed, blocked, restricted, or isolated.
While the Web policy includes a configurable default ruleset that is applied to all identities, to take advantage of the various features offered by Umbrella's cloud-based SIG, add your own organization-centric rulesets and rules. You can add multiple rulesets and rules so that various identities can be granted different permissions within the Web policy.
Note: Under Ruleset Identities, AD Groups, AD Users and Networks options are supported.
Configure Web Policy Rules
The Web policy rules in Umbrella are translated as Access Policies in SWA. Umbrella's Web policy is the heart of its cloud-based Secure Internet Gateway (SIG) platform, providing URL-layer visibility, security, and enforcement to your organization's web traffic.
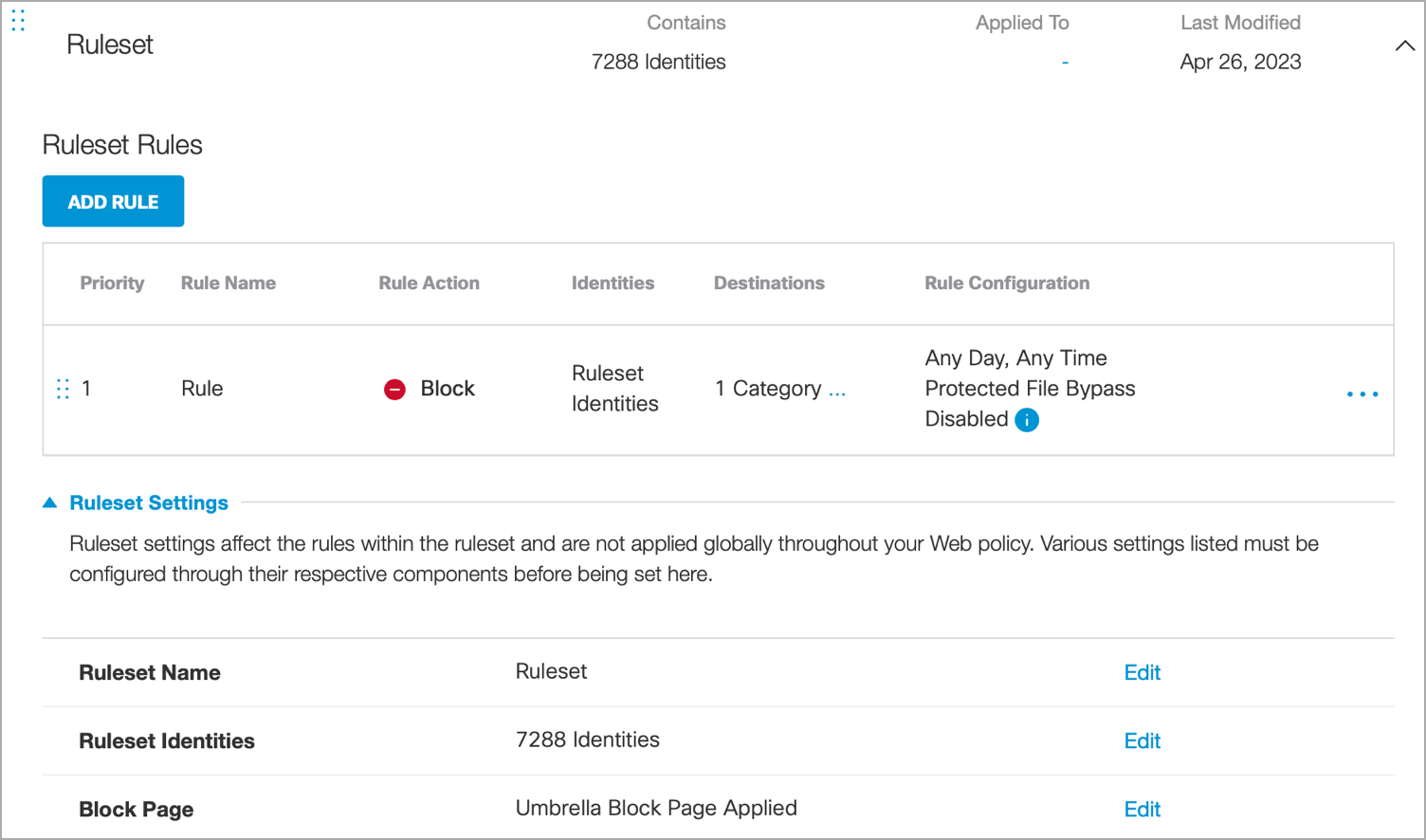
You can create a rule in Umbrella with internal networks configured as rule identities.
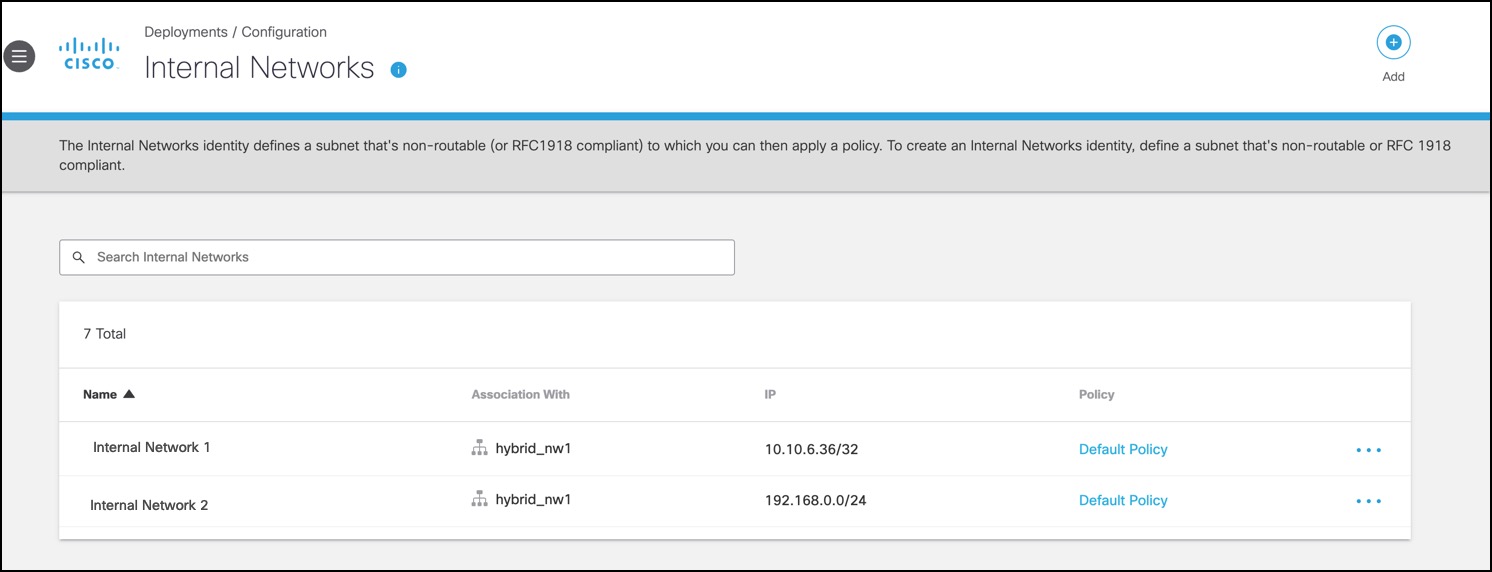
- In Umbrella, navigate to Deployments > Configuration > Internal Networks to create an internal network.
- Associate it with a public network.
Internal Networks are translated as subnets in the access policy and decryption policy in Secure Web Appliance. An additional policy will be created with the selected Network Identities to allow all the URL categories. For more information, refer to Internal Networks.
Note:
- Under Rule Actions, Allow, Warn and Block options are supported.
- Under Destinations, Content category, Destination Lists, and Application Settings are supported.
Configure Destination Lists
The Destination lists on Umbrella are translated as Custom and External URL Categories in Secure Web Appliance. Create a Destination list in Umbrella (Policy > Policy Components > Destination Lists) and associate it with a Web policy
Destination lists enable you to customize your policy to block or allow any domains and then apply those lists to your policies. Destination lists are used to control identity access to websites. You add destinations to a destination list and then add that destination list to a policy. A destination list is a list of internet destinations: domains, URLs, and CIDRs. For more information on adding a destination list, refer to Add a Destination List.
Configure Application Settings
Application Settings, also known as CASI in Umbrella are translated as ADC Applications in the Access policies of SWA. You can select application categories or specific applications in the Umbrella Rules, and the same rule action is applied to the Access policy applications in SWA. Custom URL categories consisting of domains for the selected applications are created and pushed to the SWA. You can view the domains by navigating to URL Filtering > Custom and External URL Category Filtering, and selecting the Action as Monitor in the URL Filtering section of the Access policy.
Once these rules are translated to SWA, you can view them by navigating to Web Security Manager > Access Policies > Applications.
Important
Enable Application Discovery and Control (ADC) in SWA for translation of the rules of the selected applications from Umbrella to SWA.
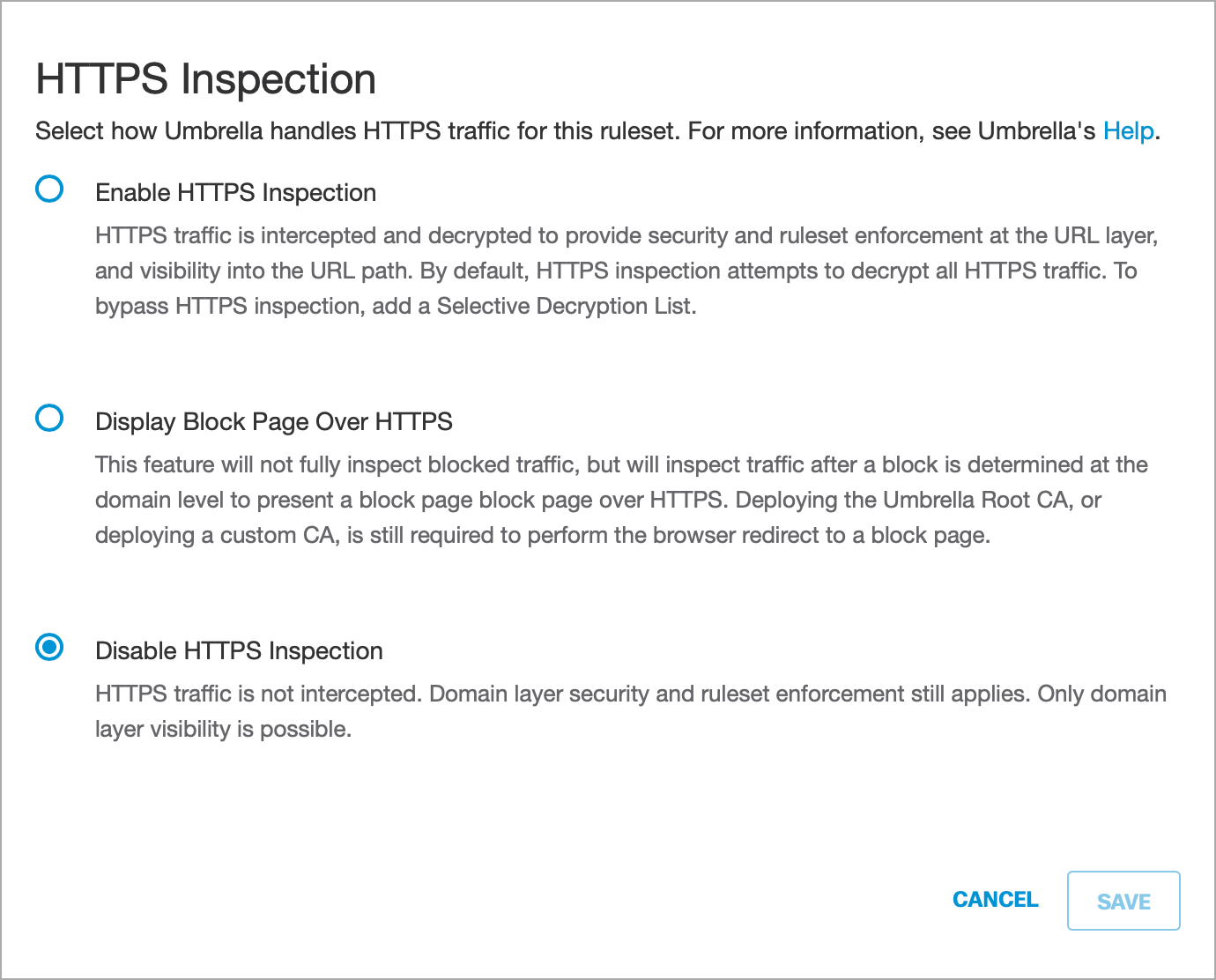
Configure HTTPS Inspection Policies
HTTPS Inspection policies in Umbrella are translated as Decryption policies in SWA so that they can be used along with identities.
- In Umbrella, navigate to Policies > Management > Web Policy.
- Under Ruleset Settings, select HTTPS Inspection.
- Click Edit.
- Choose how the policy handles HTTPS traffic.
For more information, refer to the Edit HTTPS Inspection section under Add a Ruleset to the Web policy.
Note:
- In Umbrella, for each ruleset, a decryption policy will be configured. In SWA, Decryption Policies will be
enabled only if HTTPS Proxy is enabled. - Translating Applications from Umbrella as Decryption Policies in SWA is not supported.
- The WBRS is disabled in SWA for the decryption policies that are translated from Umbrella.
- The default action of Decryption policies translated from Umbrella is set to Decrypt.
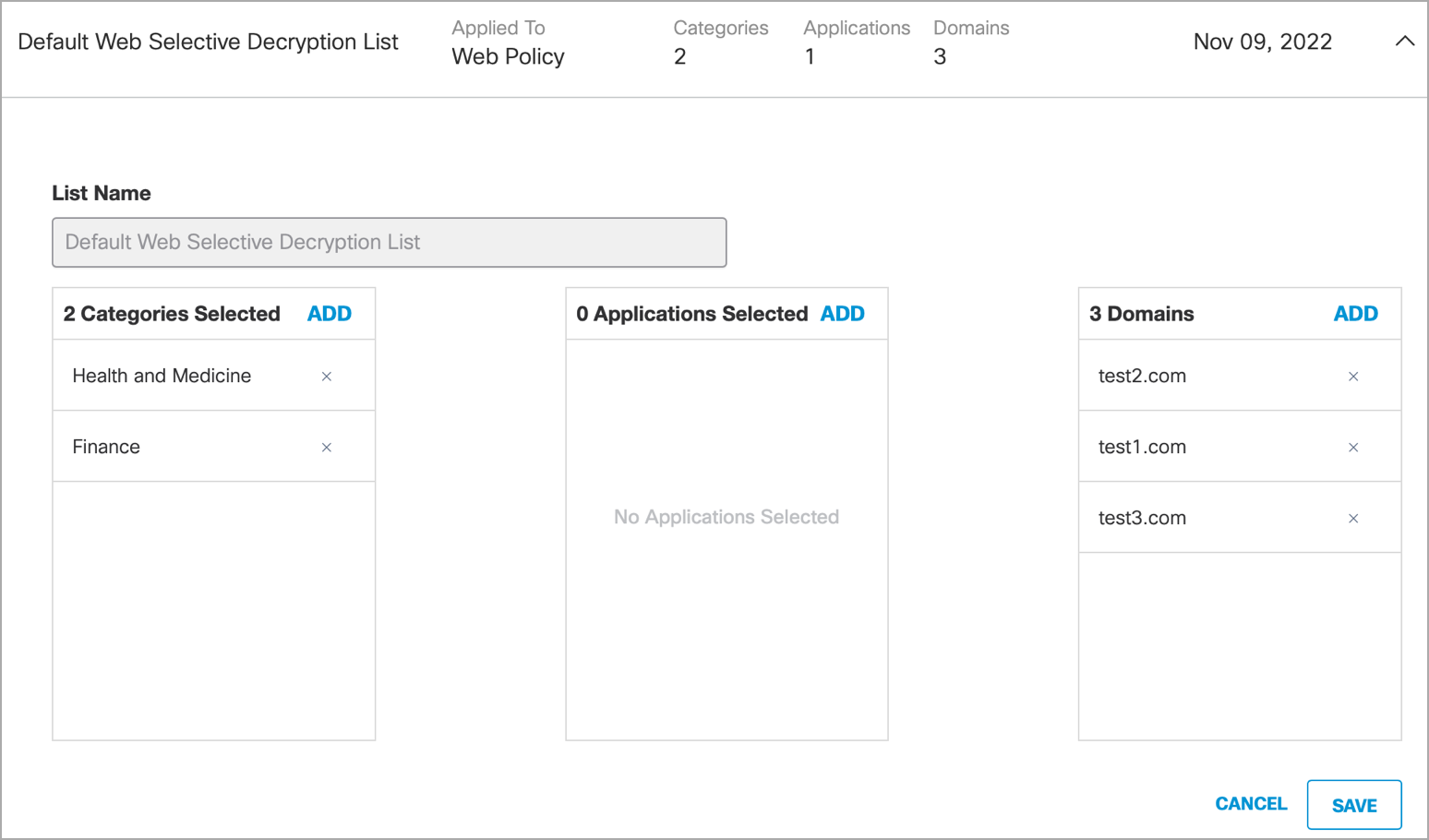
The translated categories from the Selective Decryption List in Umbrella are displayed under URL Filtering > Predefined URL Category Filtering and Domains from the Selective Decryption List in Umbrella are displayed under URL Filtering > Custom and External URL Category Filtering for a decryption policy.
The HTTPS inspection configuration in Umbrella is translated to Secure Web Appliance as follows:
- If enabled, the domains, and categories from the Selective Decryption List, are set to
Passthrough in Secure Web Appliance and the remaining categories to Decrypt. - If disabled, the Decryption policies are displayed with all Predefined URL Category Filtering as Monitor in Secure Web Appliance.
- If Display Block Page Over HTTPS is selected, the Decryption policies are displayed with all Predefined URL Category Filtering as Monitor in Secure Web Appliance.
Configure Active Directory (AD) Users and Groups
The Active Directory (AD) Users and Groups in Umbrella Web policies are translated to SWA policies so that they can be used along with identities, decryption policies, and access policies.
Identification profile will be created with the Realms as All Realms, Schema as Use Kerberos or NTLMSSP or Basic, and Authentication Surrogates as IP Address. The Apply same surrogate settings to explicit forward requests check box will be enabled.
- In Umbrella, navigate to Policies > Management > Web Policy > Ruleset Identities.
- Select Users and Groups from the integrated AD of Umbrella.
An additional policy will be created with the selected User and Groups of Ruleset Identities to allow all the URL categories.
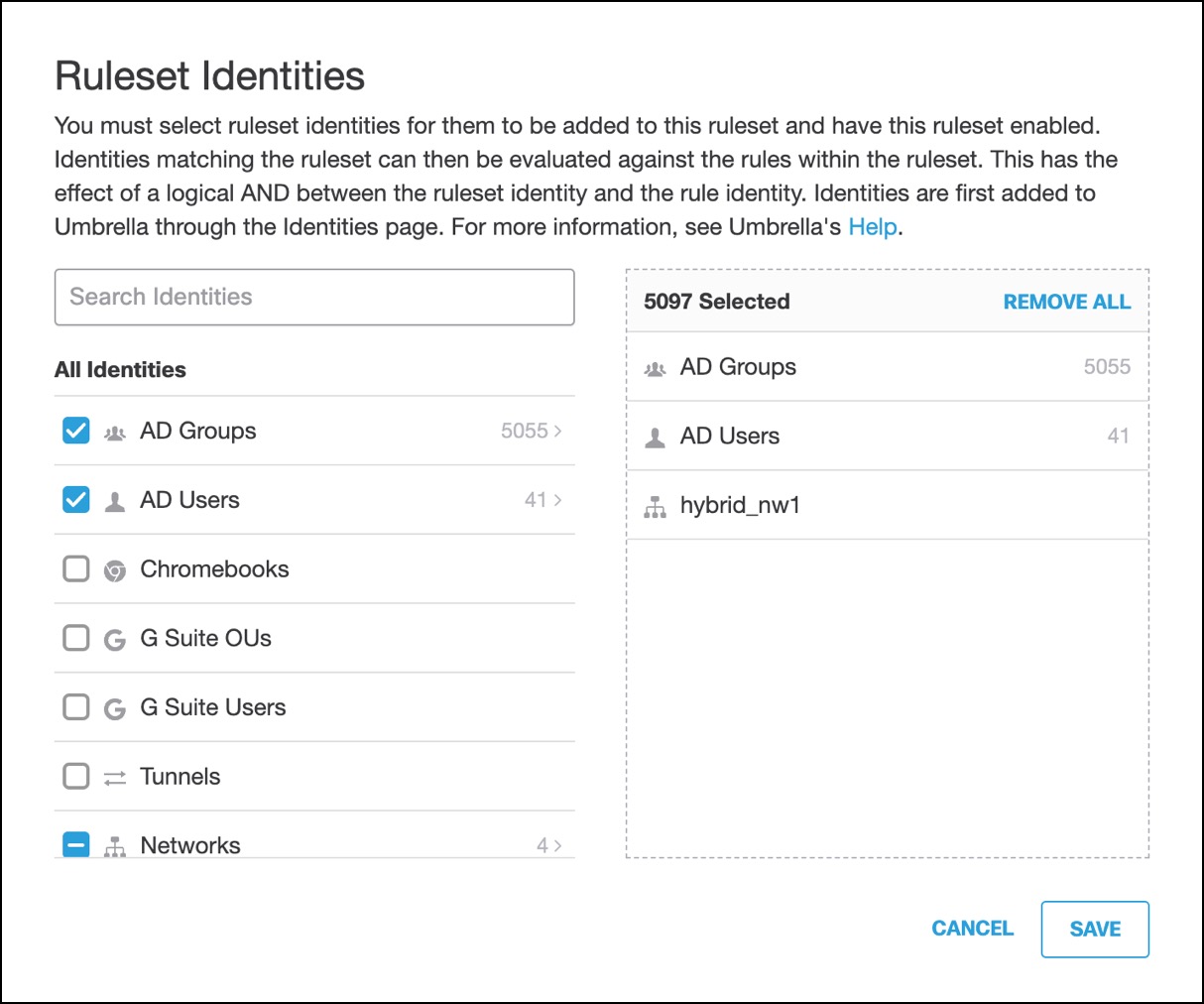
The selected AD Users and Groups in the ruleset identities must be selected as policy membership criteria in SWA under Web Security Manager > Decryption Policies > Policy Member Definition.
Configure Microsoft 365 Compatibility
- You can translate Microsoft 365 Compatibility configuration from Umbrella to Secure Web Appliance Custom and External URL Categories by choosing the Category Type.
- In Umbrella, if Microsoft 365 Compatibility is enabled (Policies > Management > Web Policy > Global Settings), Custom and External URL Categories in Secure Web Appliance will be created with the Category Type as External Live Feed Category and with Feed File Location as Office 365 Web Service. This category will be selected for the decryption policies configured from Umbrella under the URL Filtering section of SWA with Action as Passthrough.
Note: Decryption policies will be configured only if HTTPS Proxy is enabled in Secure Web Appliance.
Umbrella Integration with Secure Web Appliance < Configure Web Policies and Destination Lists > Policy Features
Updated over 1 year ago
