Understand Isolated Destinations
Umbrella Packages and Feature Availability
Not all of the features described here are available to all Umbrella packages. Information about your current package is listed on the Admin > Licensing page. For more information, see Determine Your Current Package. If you encounter a feature here that you do not have access to, contact your sales representative for more information about your current package. See also, Cisco Umbrella Packages.
Remote browser isolation (RBI) protects identities from potential malware and other threats by redirecting browsing to a cloud-based host. Destinations supported by an RBI add-on can be isolated when added to a rule in a Web policy’s ruleset. When you add a rule and choose the Rule Action Isolate, the selected destination in the rule will create a remote browser when users attempt to access those destinations. Instead of blocking identities from the destination endpoints, a cloud-based browser hosts the browsing session for that destination.
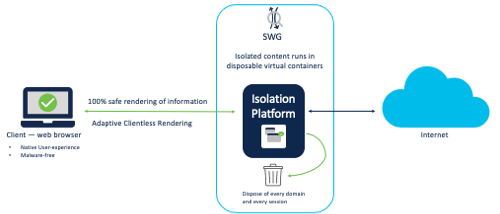
Table of Contents
Prerequisites
Various prerequisites must be met before you can successfully isolate destinations.
Umbrella Prerequisites
- HTTPS inspection must be enabled in the ruleset.
- If Selective Decryption is enabled or Selective Decryption lists are configured, the lists cannot include destinations (within destination lists, content categories, or application settings) that are required for isolation to ensure those domains and URLs can be decrypted.
- Destinations required or intended for isolation cannot be included in Internal or External bypass lists (Deployment > Domain Management).
Browser Prerequisites
- Access to third-party cookies enabled.
Note: By default, most browsers (for example, Google Chrome) have third-party cookies blocked in incognito mode. You must update this setting to allow access to third-party cookies for isolation to work. - Minimum supported browser versions:
- Apple Safari 9
- Google Chrome 34
- Microsoft Edge 12
- Mozilla Firefox 17
- Samsung Internet 11
- The Cisco Umbrella Root certificate or customer CA-signed certificate must be installed. For more information, see Install the Root Certificate and Add Customer CA Signed Root Certificate.
Note: Browser extensions and plugins are not supported and browser-specific features are not guaranteed to work. Regardless of the browser the user initiates the browsing session with, the cloud-based browser for isolation will always be Google Chrome.
Umbrella Package RBI "Add-Ons"
RBI and thus the Web policy rule's "Isolate" Rule Action is only available as an Add-on to your Umbrella package. If available and chosen as the Rule Action, the availability of destinations for selection when configuring a rule is based on your Umbrella package's RBI Add-on. There are several variations of the RBI add-on available, each with its own level of isolation.
Isolate Any
Any security categories, content categories, applications, and destination lists can be isolated.
Isolate Risky
Isolate is available for the following destination types:
- Security Categories: Malware, Command and Control Callbacks, Phishing Attacks, and Potentially Harmful
- Content Categories: Uncategorized
Isolate Web Apps
Isolate is available for the following destination types:
- Content Categories Chat, File Storage, File Transfer Services, Instant Messaging, Organizational Email Professional Networking, Social Networking, and Webmail.
- Applications:
| Application Category | Applications |
|---|---|
| Cloud Storage | Box Dropbox Google Drive WeTransfer LinkedIn Slideshare Huawei Mobile Cloud |
| Collaboration | Slack Facebook Messenger ICQ Line |
| Office Productivity | Smartsheet Lucidchart Gmail Yandex Mail Mail.ru Trello |
| Social Media | Facebook |
Most cloud applications support third-party authentication. For example, you can sign in to your Dropbox account by authenticating through Google Sign-In. Unless both domains hosting the application and the authentication provider are isolated, the third-party authentication will not function correctly. Umbrella automatically detects redirection to third-party authentication providers from already isolated websites and isolates these transactions. For example, you can configure a rule to isolate the content category Online Storage and Backup to ensure that the cloud application Dropbox is isolated. If a user attempts to sign in to Dropbox using Google sign-in, Umbrella automatically isolates requests to additional Google domains, such as auth.google.com and auth.youtube.com.
If a third-party authentication provider is found to not be supported, contact Umbrella support.
Limitations of Isolation
Only top-level page requests can be isolated and pages can either be entirely isolated (top-level request and resource requests) or not. Isolation only functions for an entire application, not for specific actions such as uploads or posts. When an application is isolated, it can no longer be blocked, allowed, or warned, even at the action level. For example, if one rule in a ruleset is configured to block Box Cloud Storage uploads, but another rule is configured to isolate Box Cloud Storage for the same identities, uploads for Box Cloud Storage will not be blocked.
5 GB is the maximum file size that can be downloaded through the isolation environment when RBI is enforced on a browser connection. A user with Full Admin access can create a rule to allow files larger than 5 GB to be downloaded. The rule must be above the isolate rule in the ruleset. See, Add a Ruleset to the Web Policy. This will allow the user to download the file and properly scanned by the file scanner.
Applications cannot be isolated if you are using Certificate Pinning. If the application cannot be isolated, then it cannot be decrypted.
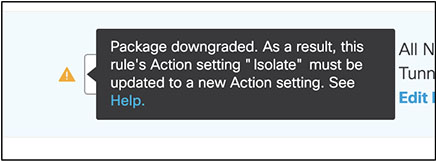
Expired or Downgraded Add-Ons
If your RBI package expires or downgrades, any rule with Isolate will no longer work as expected. You must update the Action setting for these rules.
Confirm SafeSearch for a Web Policy Ruleset < Understand Isolated Destinations > Monitor Bandwidth Usage in the App Discovery Report
Updated over 1 year ago
