Configure Tunnels Automatically with Catalyst SD-WAN cEdge and vEdge
Cisco Catalyst SD-WAN (formerly known as Viptela) automates both the deployment of IPsec (Internet Protocol Security) IKEv2 (Internet Key Exchange, version 2) tunnels with Umbrella and the IPsec configuration in cEdge and vEdge devices. You can apply the same templates to any number of Cisco Catalyst SD-WAN cEdge or vEdge devices and readily manage the tunnels in your organization.
Table of Contents
Prerequisites
- Umbrella SIG Essentials subscription.
- IOS-XE 17.2.1 or Cisco Catalyst SD-WAN 20.1 or later.
- For active/active tunnel pairs, use IOS-XE 17.4.1 or Cisco Catalyst SD-WAN 20.4.1 or later.
- Legacy Umbrella Management API key and secret. For more information about creating legacy Umbrella Management API credentials, see Add Umbrella Legacy API Keys.
Procedure
Follow the steps to configure and automatically deploy an IPsec tunnel in Cisco Catalyst SD-WAN.
- Enable NAT in the outside interface (internet facing interface in VPN0).
- Add one loopback interface for each IPsec tunnel.
- Add an Umbrella SIG credentials feature template (legacy Umbrella Management API key and secret).
- Add an Umbrella SIG tunnel feature template.
- Link feature templates to the device template.
- Route traffic to SIG and configure data policy for direct internet access.
Step 1: Configure the Outside Interface NAT
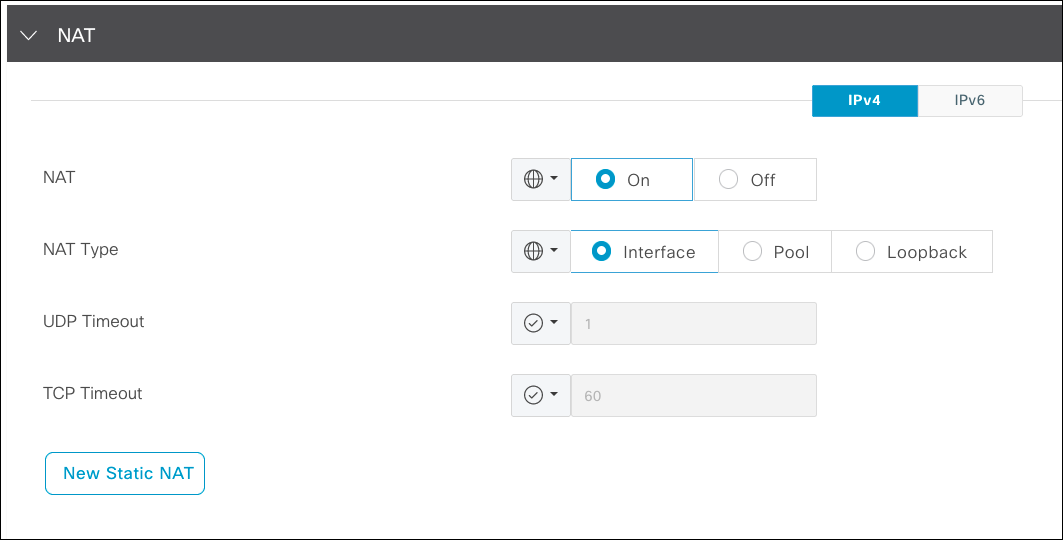
By enabling NAT on the internet facing interface, Cisco Catalyst SD-WAN automates the NAT port address translation (PAT) configuration. Traffic sourced from a private IP is automatically NATed to the interface in VPN0 after the routing decision.
- Navigate to Configuration > Templates > Feature Templates.
- Set NAT to ON and select Interface for the NAT Type.
Step 2: Configure a Loopback Interface
When you configure multiple tunnels from the same local public IP address to the same destination (Umbrella data center IP address), only one tunnel comes up if no unique information exists to identify the tunnel locally. Thus, all tunnels have the same source and destination IP address and UDP ports.
Sourcing tunnels from different loopback interfaces and NATing to the outside public IP creates dynamic port address entries, and each tunnel has a different source port. Umbrella forces NAT transversal so both IKE and ESP transport is over UDP 4500. This dynamic UDP source port is used by the local device and Umbrella to identify the tunnel. Viptela supports an upstream NAT device or multiple public IPs assigned to the edge device (one public IP per tunnel), but on-device NAT is the recommended option.
- Navigate to Configuration > Templates > Feature Templates and click Add Template.
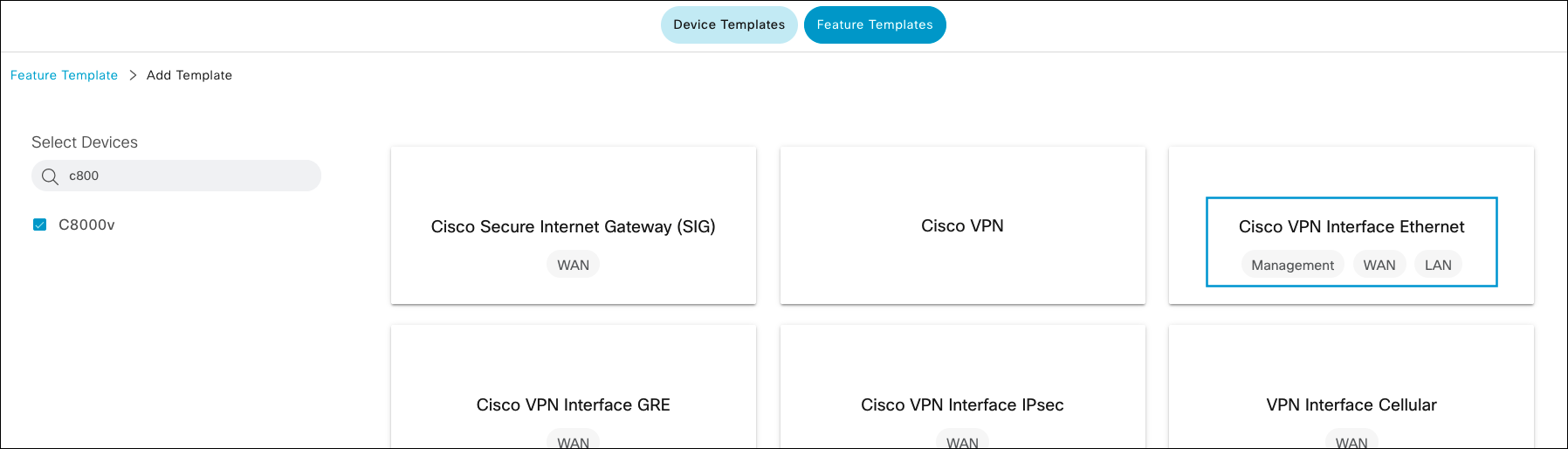
- Select the device type and click Cisco VPN Interface Ethernet.
- Provide a name and description for the template, name for the interface, and an IP address.
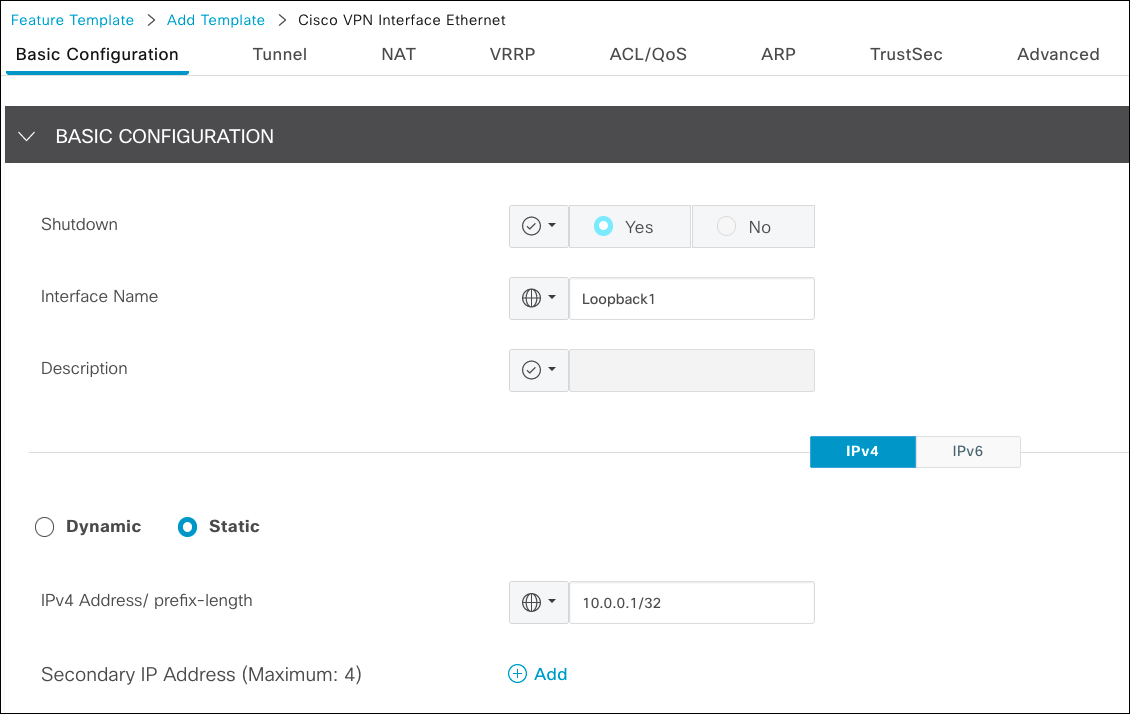
- Click Save.
If you have more IPsec tunnels to deploy for your organization, repeat Step 2: Configure a Loopback Interface for each tunnel.
Step 3: Add an Umbrella SIG Credentials Feature Template
The SIG credentials template is used by Cisco Catalyst SD-WAN cEdge and vEdge devices to authenticate to the legacy Umbrella Management API. Once you add the legacy Umbrella Management API key and secret and the Umbrella organization ID (found in the Umbrella dashboard URL) to the template, edge devices send an API request to Umbrella and create the IPsec tunnel. You can view the registered network tunnel identity in the Umbrella dashboard from the Overview report.
- Navigate to Configuration > Templates > Feature Templates and add a new template.
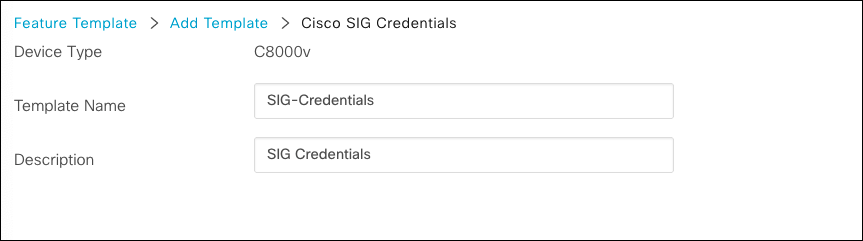
- Choose a device type, select Cisco SIG Credentials template, and provide a name and description for the template.
- Enter the Umbrella organization ID, Registration key, and Secret, and then click Save.
Provide the legacy Umbrella Management API key in Registration Key and legacy Umbrella Management API secret in Secret.
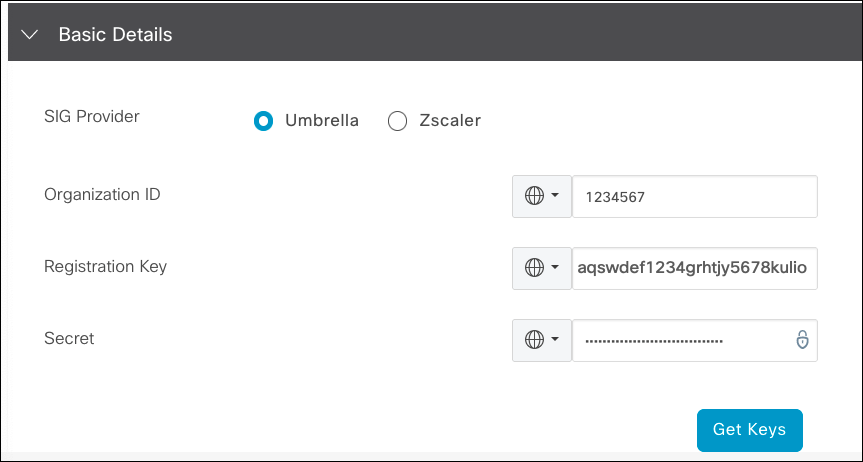
Note: If Cisco Catalyst SD-WAN is linked to Smart Account, you can add the Umbrella Management API key and secret, and organization ID by clicking on Get Keys.
Step 4: Add an Umbrella SIG Tunnel Feature Template
The Umbrella SIG feature template provides the configuration for the IPsec tunnel. Depending on your version of Cisco Catalyst SD-WAN, you can have more than one active tunnel. The latest version of Cisco Catalyst SD-WAN supports up to four active tunnels and four passive tunnels.
For higher throughput, Cisco Catalyst SD-WAN supports Equal-Cost Multi-Path (ECMP) over no more than four active tunnels, and uses passive tunnels for faster failover in case an Umbrella data center goes offline. When you pre-provision a tunnel to a different data center, the failover happens faster. However, if a very fast data center failover is not required, you do not have to pre-provision a tunnel to a different data center.
Note: Umbrella tunnels are part of a high available zone with three data centers in the zone.
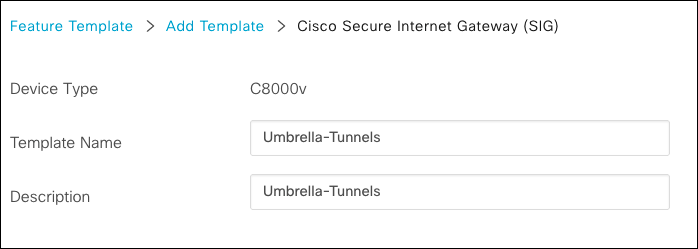
- Navigate to Configuration > Templates > Feature Templates and add a new template.
- Choose the device type, select Cisco Secure Internet Gateway (SIG) template, and provide a name and description for the template.
- For Tracker, provide a private IP address.
The tracker automatically configures an HTTP GET probe tohttp://service.sig.umbrella.comand the result is used to check the Umbrella service chain.- If the probe returns the HTTP
200status code, the service chain to Umbrella Secure Internet Gateway (SIG) is functional. - If the probe fails, the tunnel is not used for traffic forwarding. If required, you can set up additional trackers.
- If the probe returns the HTTP
- For Configuration, click Add Tunnel and provide the following:
- Interface Name—A name for the interface, such as
ipsec 1oripsec 2. - Tunnel Source Interface—The loopback interface if multiple tunnels or if a single tunnel. You can use the actual internet-facing interface, but loopback is always the preferred method.
- Data Center—Select Primary for all active tunnels and Secondary for passive tunnels. We recommend that you have a secondary tunnel.
- Tunnel Route-via Interface—Choose the device interface for the tunnel.
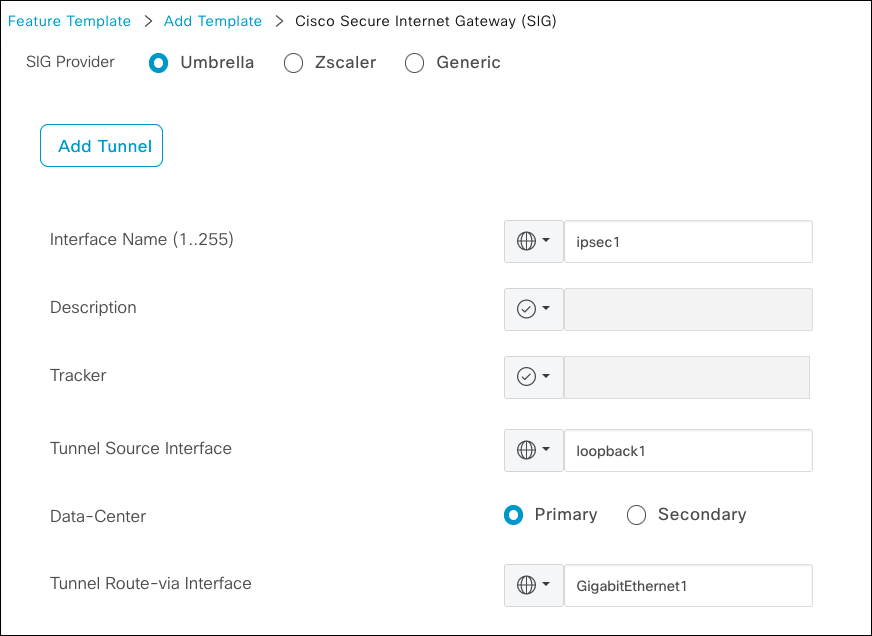
- Click Add and repeat this step up to eight times. Use a different loopback interface for each tunnel source interface.
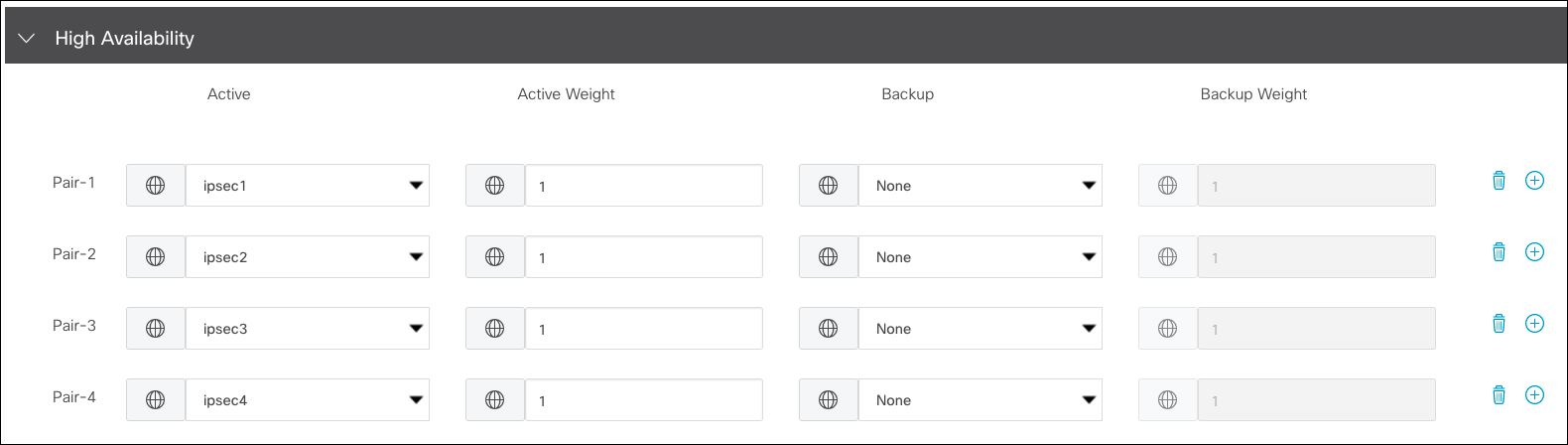
- Under High Availability, add up to four pairs and select the previously created IPsec tunnels.
If sourcing from different internet links, you can provide Active Weight for the link. Traffic load sharing applies the value of Active Weight—the link speed—to the link.
- Under Advanced Settings, specify a data center for the primary data center and a data center for the secondary data center, or keep the default auto selection. Click Save.
Step 5: Configure a Device Template
Once you create all the feature templates, you must link the feature template to one or more edge devices.
- Navigate to Configuration > Templates > Device Templates and click the device or devices where you want to deploy SIG tunnels.
- Under Transport & Management VPN, add the loopback interfaces and SIG Tunnel Template.
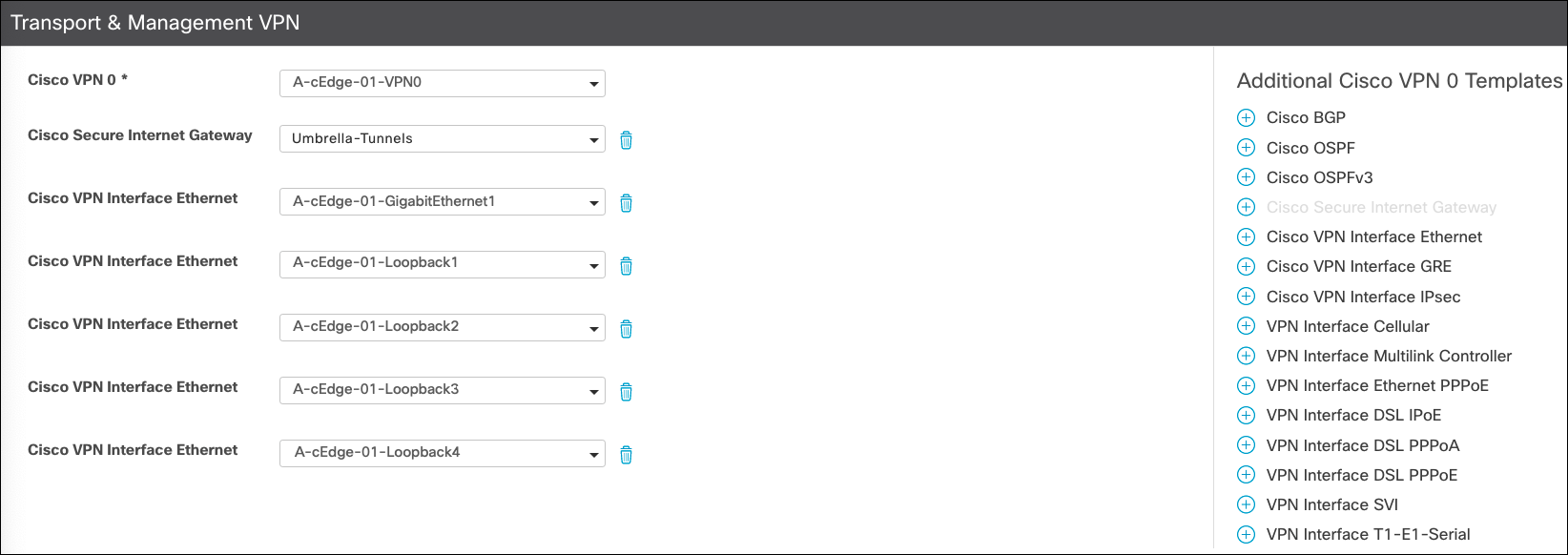
- Under Additional Templates, select the SIG credentials template that you created and click Update.
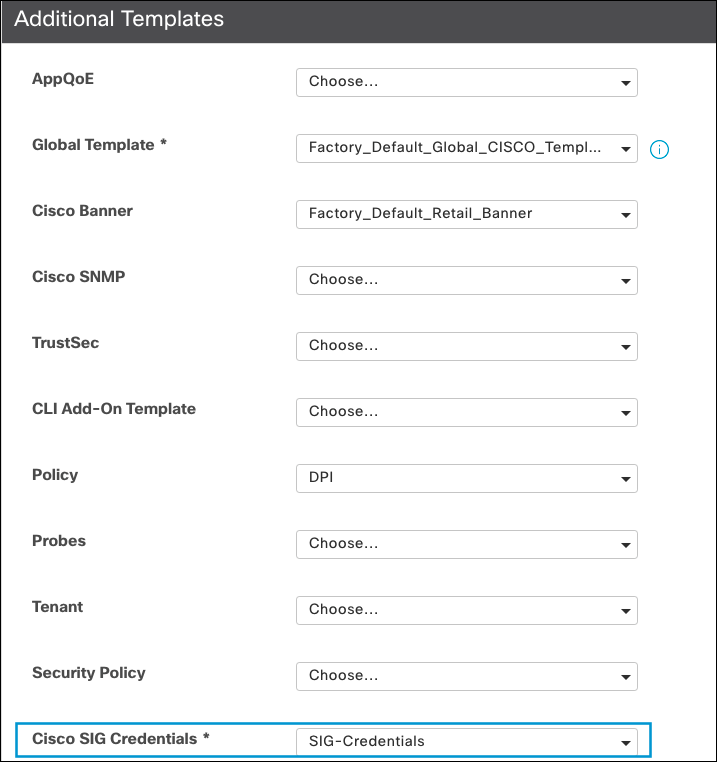
Once the configuration is deployed, the tunnel is established and ready for traffic forwarding.
Step 6: Route Traffic to Umbrella SIG
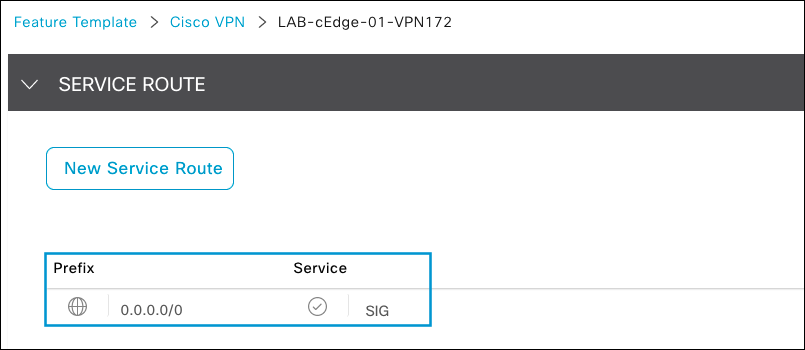
- Navigate to Configuration > Templates > Feature Templates and click the service side VPN feature template.
- Under Service Route, click New Service Route and add a default route and service SIG.
If multiple SIG tunnels exist, the traffic is automatically load-shared across the tunnels.
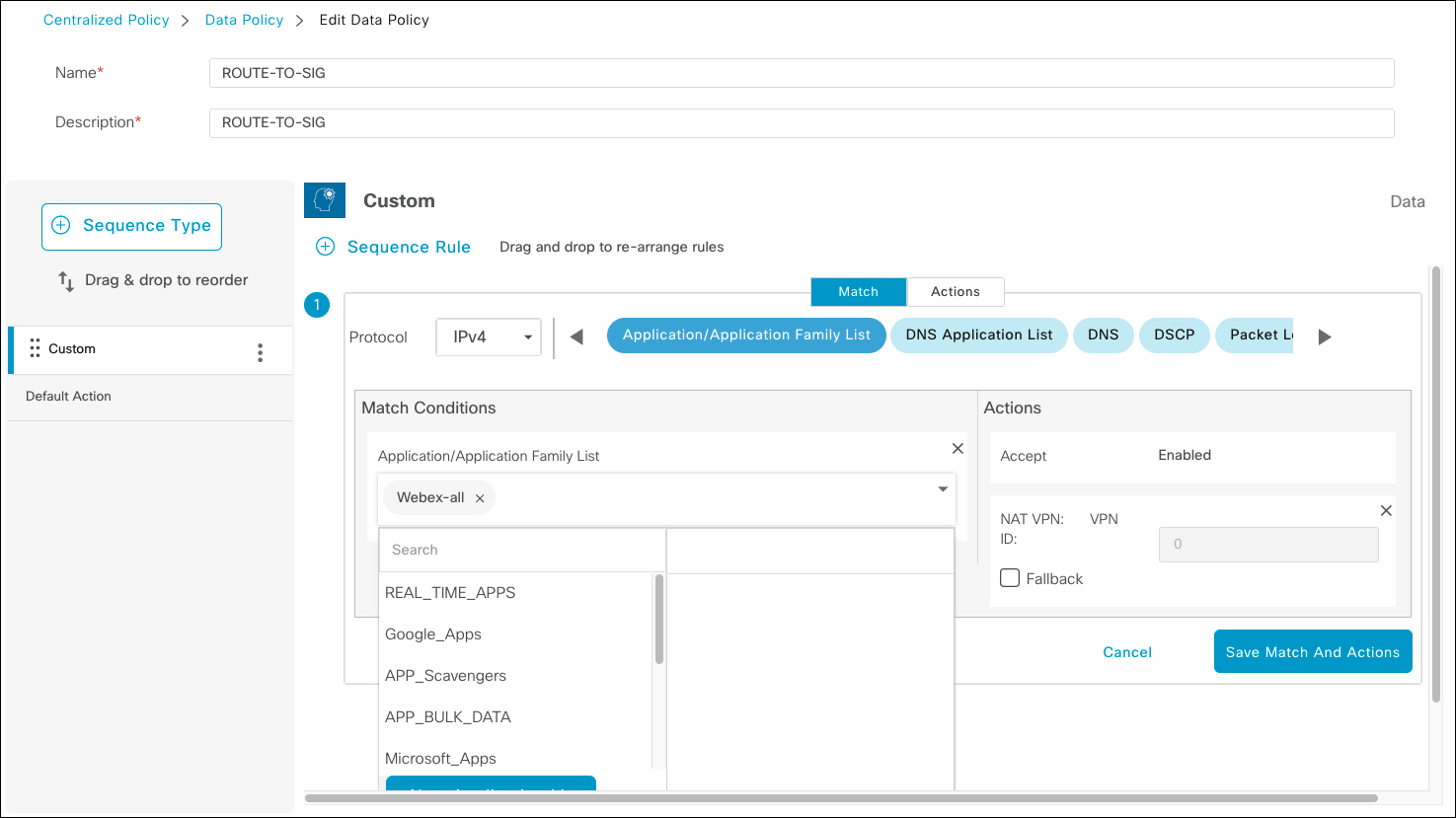
- To route specific traffic out of the SIG tunnel using Cisco SD-WAN Direct Internet Access (DIA), you need to edit or create a data policy.
- Under Traffic Rules click Add Policy if none exists or edit an existing policy.
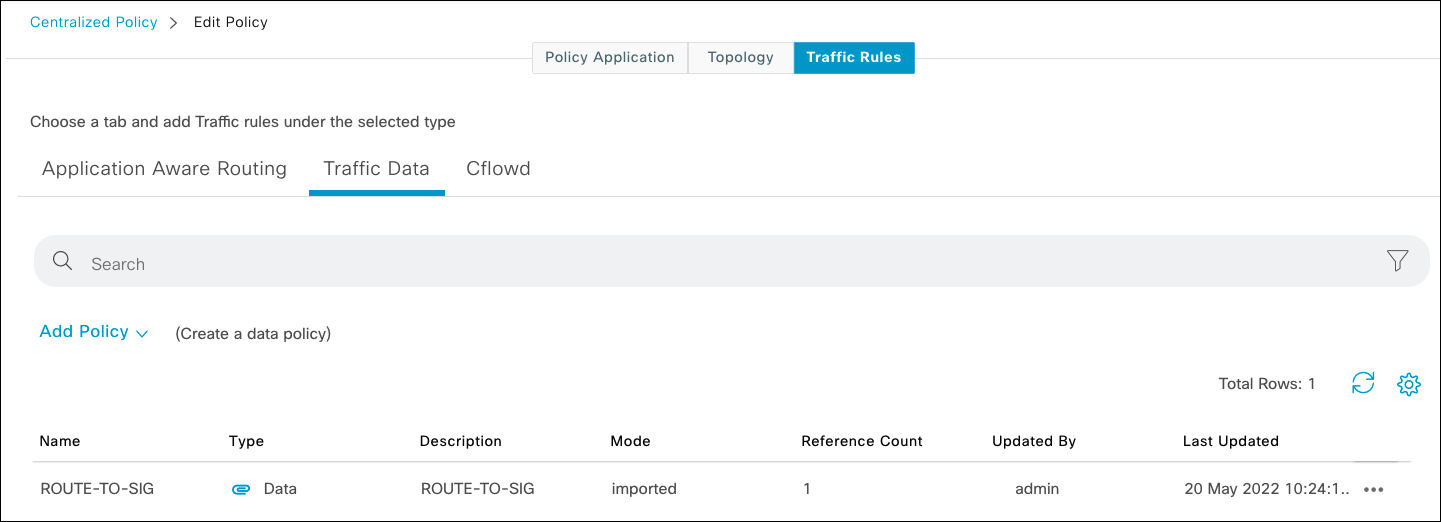
- Under Match Conditions, select the apps for DIA and under Actions select NAT VPN. Click Save Match and Actions.
Troubleshooting
Most tunnel error conditions are related to API requests to the legacy Umbrella API. Cisco Catalyst SD-WAN (vManage) automatically registers an organization's Umbrella Management API credentials with the Cisco Catalyst SD-WAN cEdge and vEdge devices. For more information, see Step 3: Configure Umbrella SIG Credentials Feature Template. The devices use the legacy Umbrella Management API key and secret to authenticate a request to the legacy Umbrella Management API.
The devices must resolve the fully qualified domain name (FQDN) and authorize a request for the organization to the legacy Umbrella Management API.
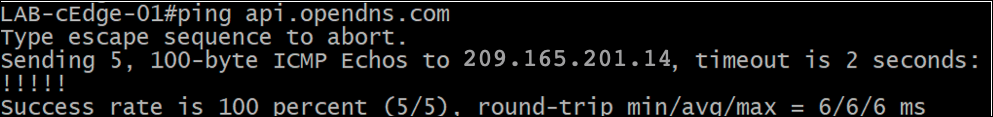
- To check if the edge device can resolve DNS queries, create an SSH session to the edge device and run the following command:
ping api.opendns.com
- To check the tunnel creation status, run the following command:
show sdwan secure-internet-gateway umbrella tunnel
The output displays any errors that occur when connecting to Umbrella from the edge devices.
Configure Tunnels with Catalyst SD-WAN cEdge and vEdge< Configure Tunnels Automatically with Catalyst SD-WAN cEdge and vEdge > Configure Tunnels with Meraki MX – Option 1
Updated almost 2 years ago
