Configure Tunnels with Palo Alto Prisma SDWAN
Palo Alto Prisma SDWAN provides per-application policy enforcement of application traffic flows from branch offices over disparate links to data centers as well as direct-to-internet flows for SaaS applications, and general internet usage. Integrating Prisma SDWAN and Cisco Umbrella enables customers to secure their internet bound traffic with best-in-class security.
Table of Contents
- Configure Tunnels in Umbrella
- Configure Palo Alto Prisma
- Verify the Configuration
- Troubleshoot the Configuration
Configure Tunnels in Umbrella
- Navigate to Deployments > Core Identities > Network Tunnels and click Add.
- Give your tunnel a meaningful name and choose Others from the Device Type drop-down.
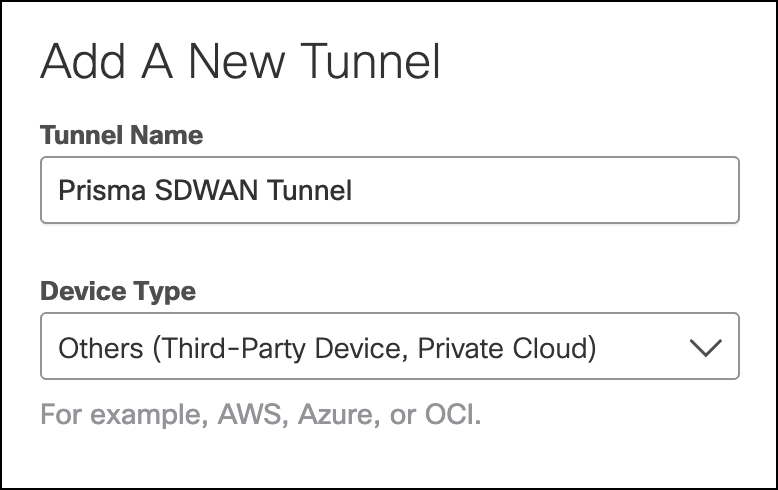
- Select Fully Qualified Domain Name (FQDN) or IP Address/Network for the Authentication Method. Add the Tunnel ID and create a passphrase.
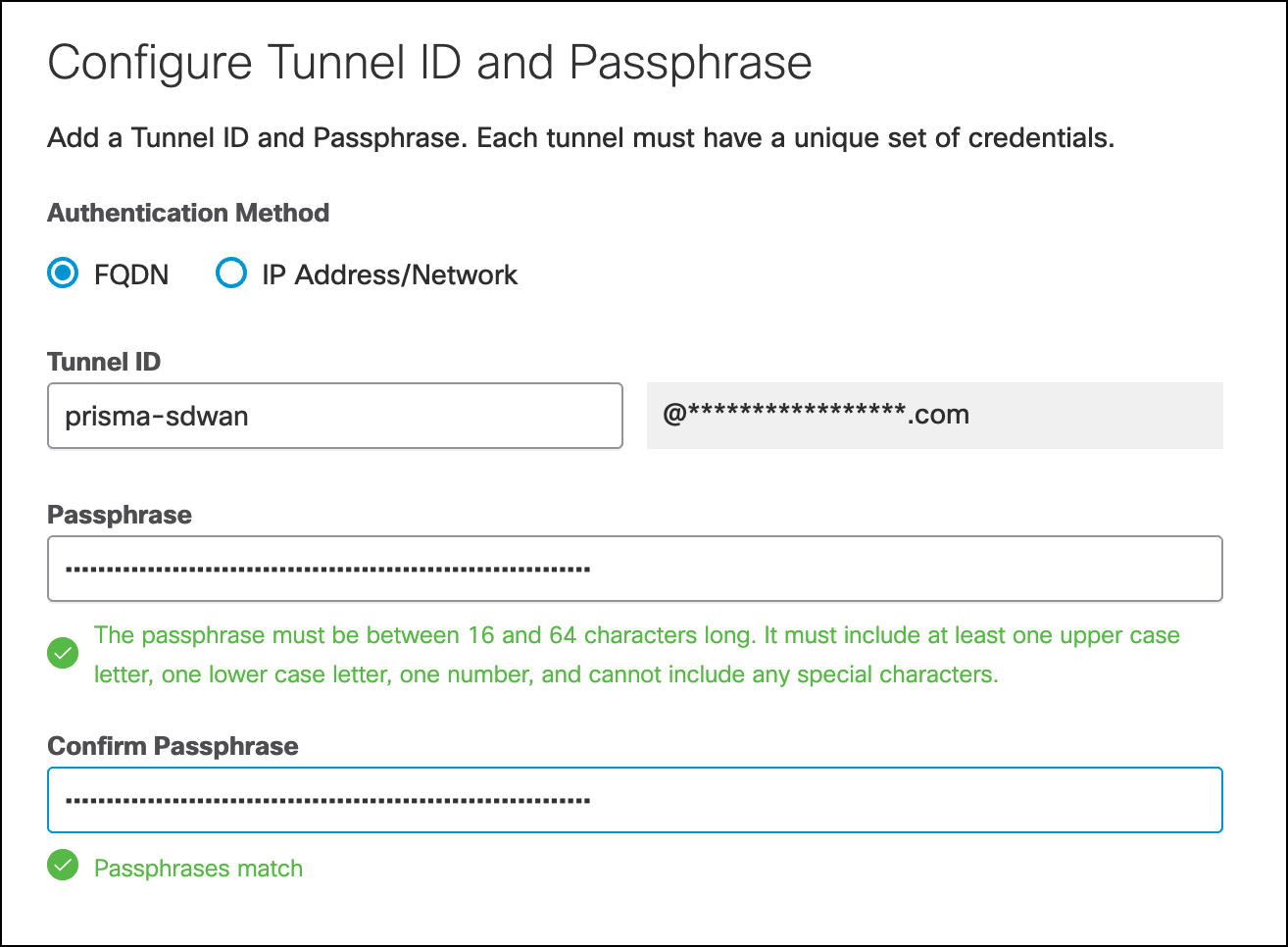
- Choose an appropriate site from the Associate Tunnel with Site drop-down list and optionally, enter an IP address to the IP Address Ranges field which you would like to send to Umbrella SIG.
- Copy the Tunnel ID and passphrase and save for Configure the Prisma IPsec Profile.
Configure Palo Alto Prisma
Configure the Prisma IPsec Profile
- In Prisma SD-WAN, navigate to Policies > Stacked Policies, click IPsec Profiles, and click Add IPsec Profile.
- Provide a meaningful name and click Next.
- Enter the IKE Group settings to align with Umbrella's Supported IPsec Parameters and click Next.
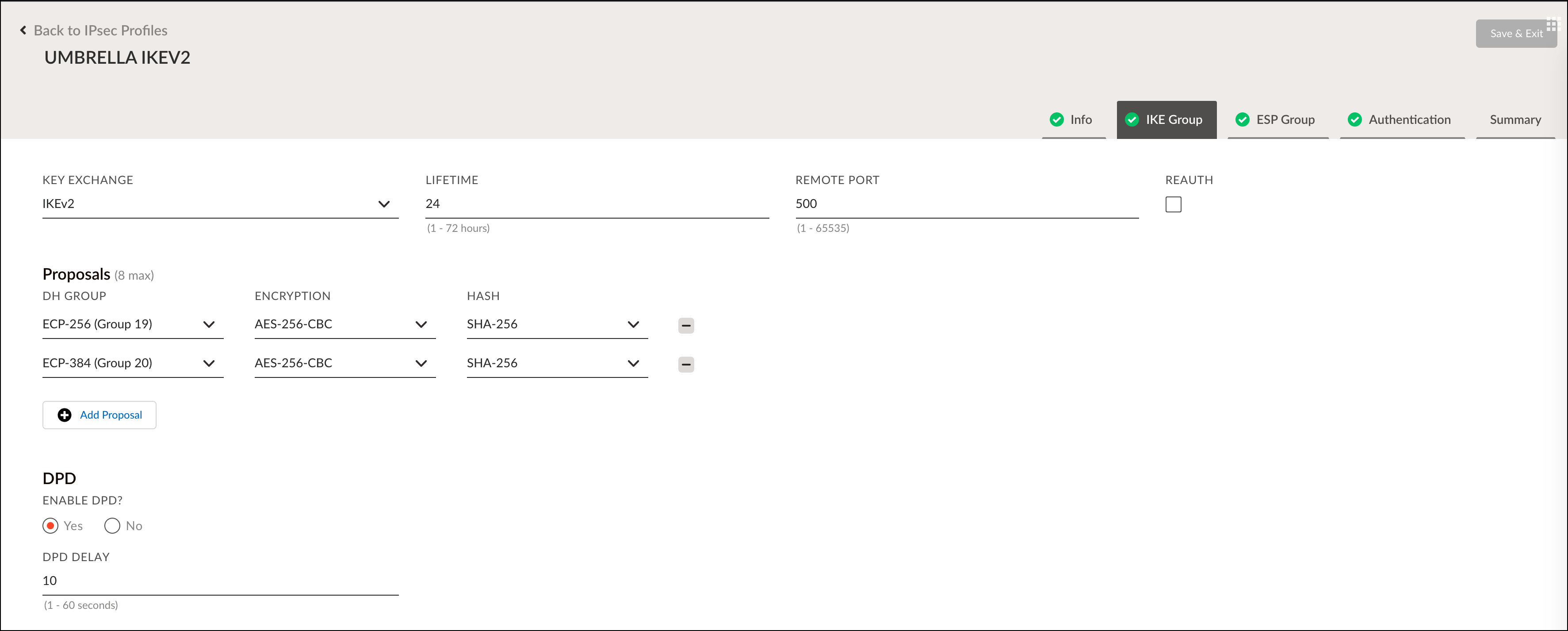
- Enter the ESP Group settings to align with Umbrella's Supported IPsec Parameters and click Next.
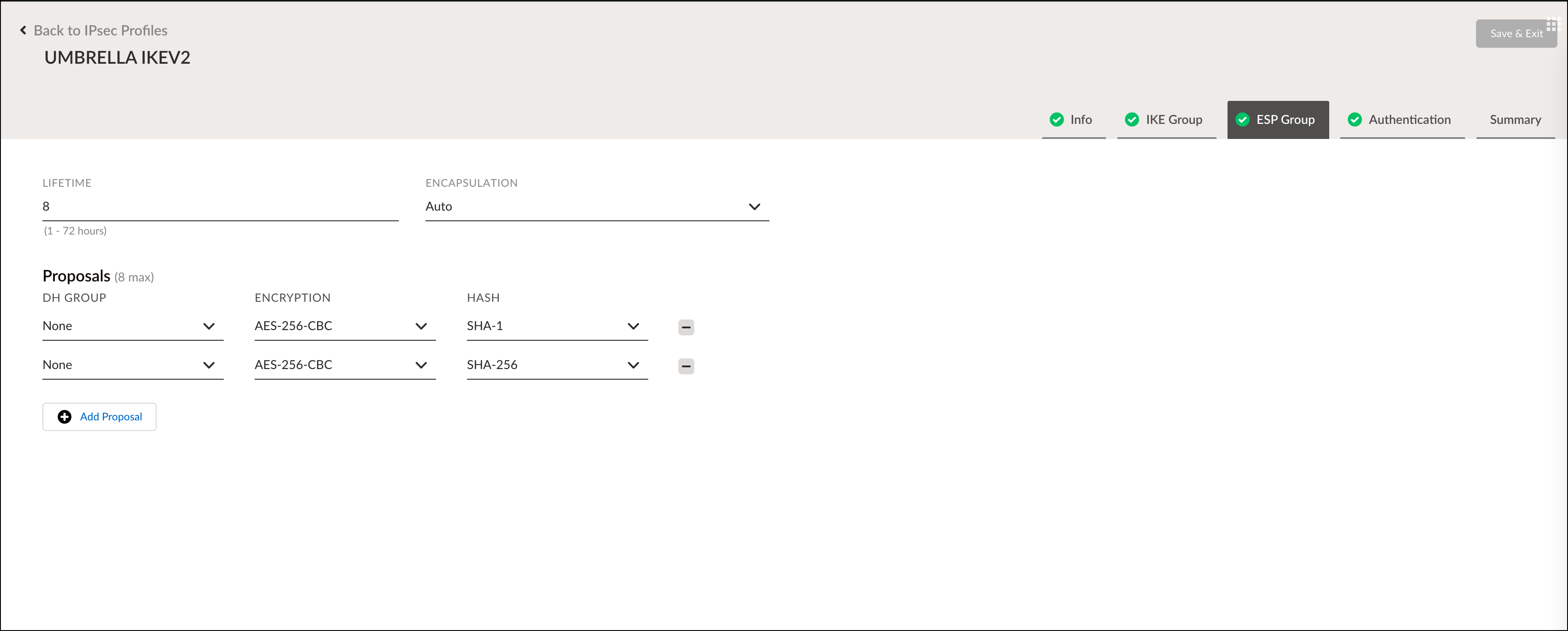
- Set the Authentication Type to None and click Next.
Note: Authentication must be configured per device. - Review and verify the configuration and click Save and Exit.
Configure the Prisma Service Endpoint Group
- In Prisma SD-WAN, navigate to Policies > Stacked Policies, click Service & DC Groups, and click Endpoints.
- Select Standard VPN from the Prisma SD-WAN drop-down.
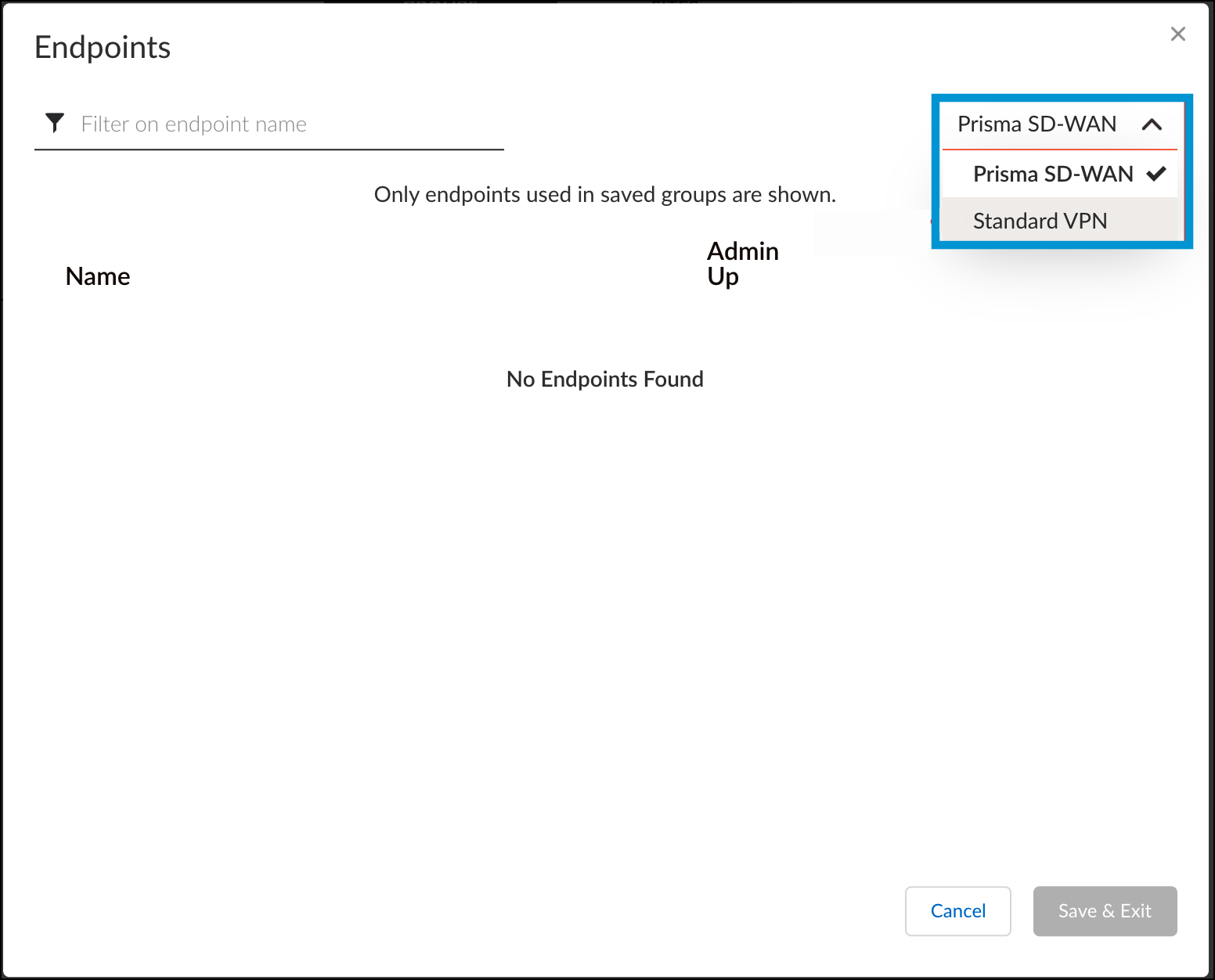
- Click Add Endpoint, enter a meaningful name and optional description, and then click IPs & Hostnames.
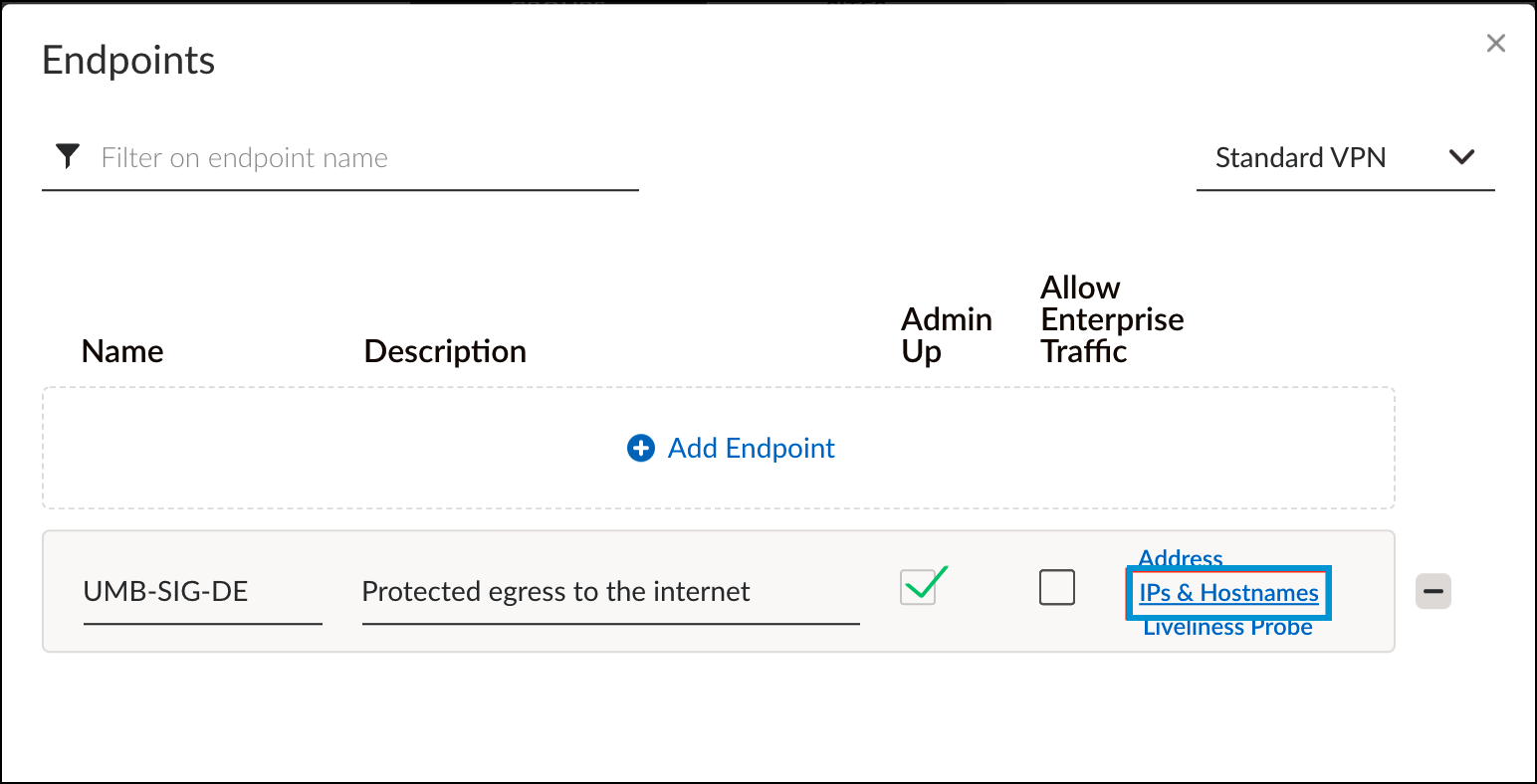
- Enter the Umbrella IPsec head-end IP(s) that are desired for this endpoint.
You can list multiple peer IPs separated by commas. Prisma SD-WAN checks the round-trip time for each of the IP addresses in the list and chooses the destination with the lowest latency. For a complete list of Umbrella IPsec head-end IPs, see Connect to Cisco Umbrella Through Tunnel. - Click Done and Save & Exit.
- In the Groups tab, click Add and select Standard VPN.
- Define a name of the Endpoint Service Group, selected the endpoint you just created and click Done.
Configure the IPsec Tunnel
- In Prisma SD-WAN, navigate to Map > Claimed Devices, and click the device where the IPsec tunnel will be configured.
- Click the Interface configuration tab, click the "+" icon to add an interface, select Standard VPN, and then click Add.
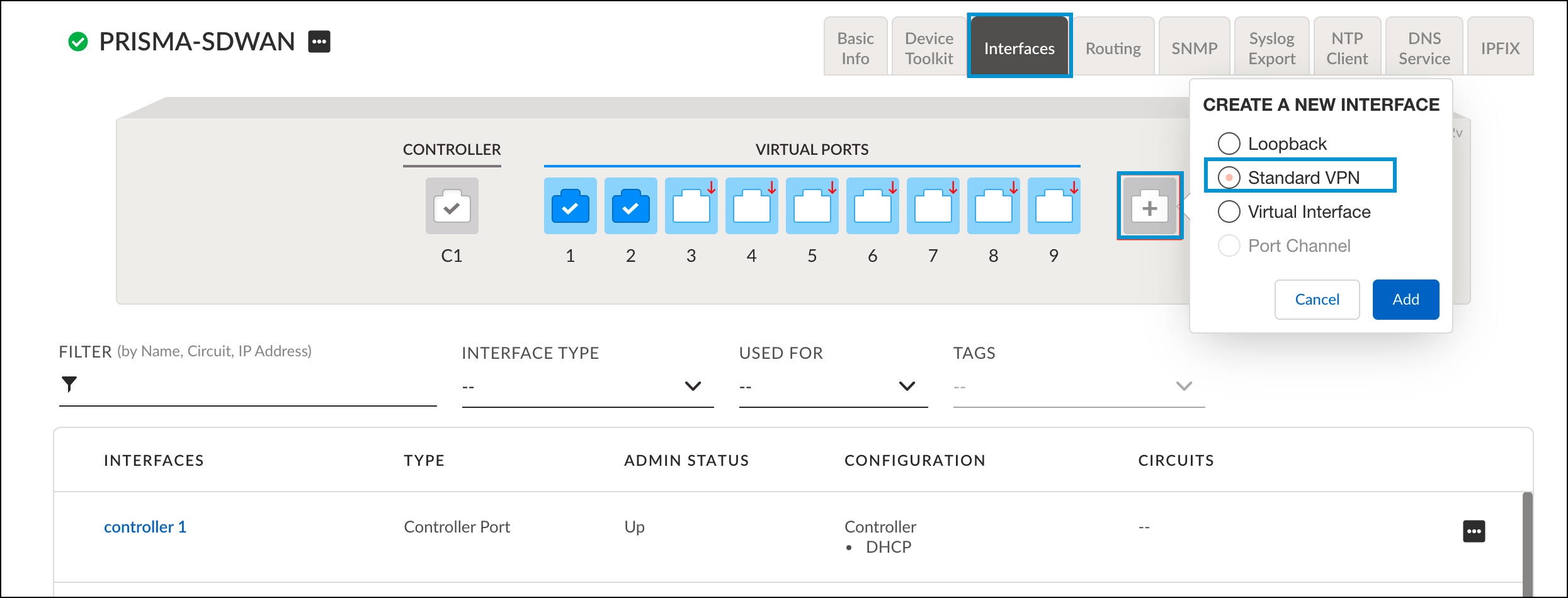
- Configure the tunnel with the following fields:
- Name—Provide a tunnel name.
- Interface Type—Standard VPN
- Standard VPN Type—IPsec
- Parent Interface—The interface designated for outbound/internet communications.
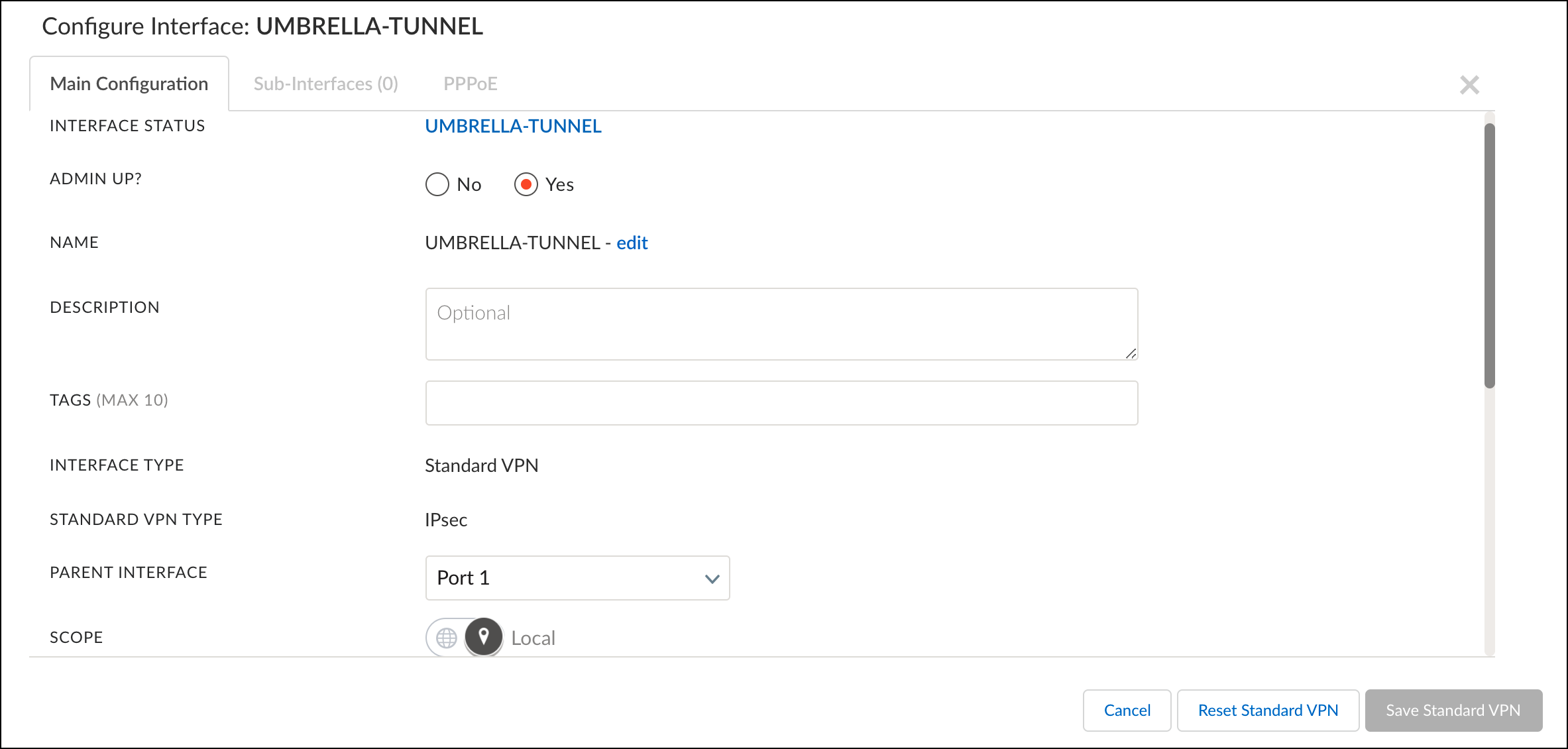
- Inner Tunnel IP Address/Mask—Use a dedicated RFC-1918 address.
- Endpoint—The Endpoint Group configured in Configure the Prisma Service Endpoint Group.
- IPSec Profile—The profile created in Configure the Prisma IPsec Profile.
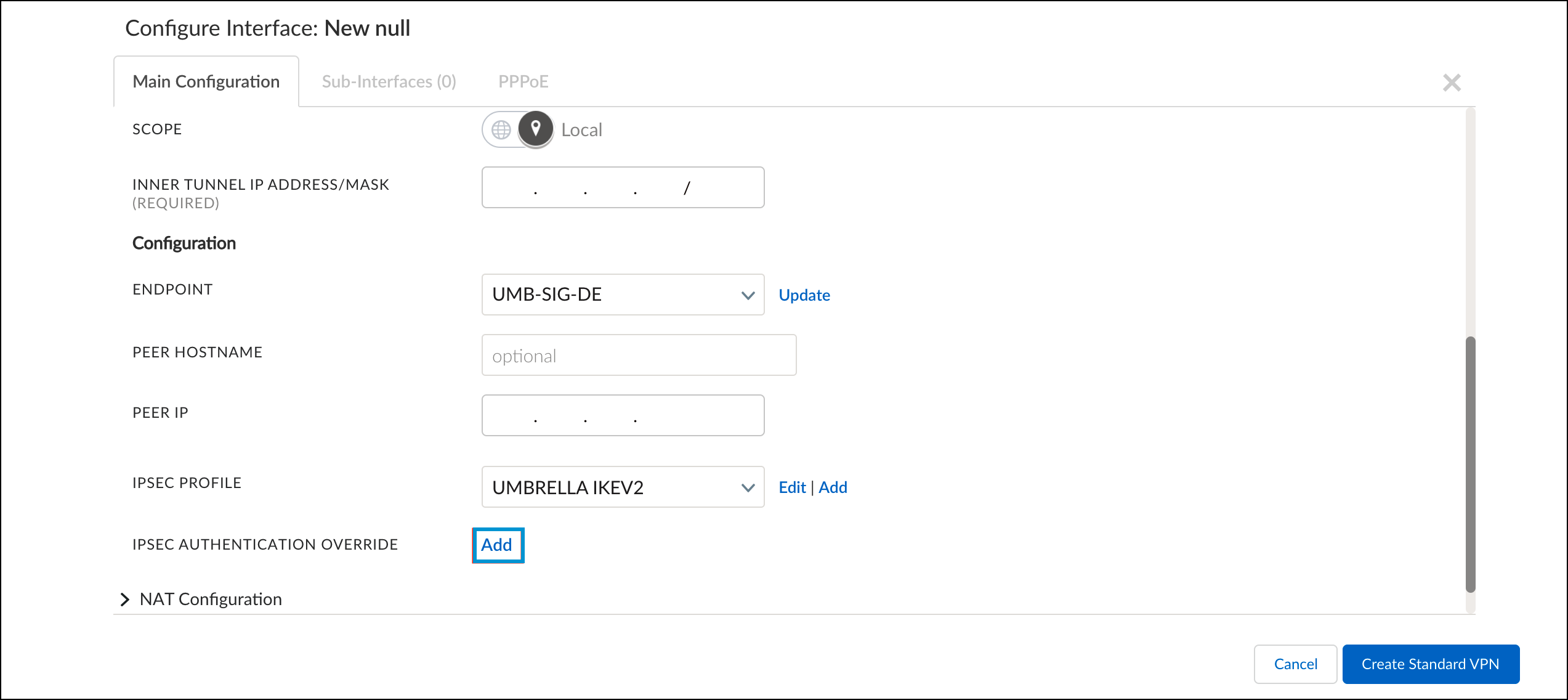
- For IPsec Authentication Override, click Add and configure the fields as follows:
- Type—PSK
- Secret—The pre-shared key created in Configure Tunnels in Umbrella.
- Local ID Type
- Choose Interface IP Address if you configured the Umbrella tunnel to use an IP address as the tunnel ID.
- Choose Custom and specify the FQDN tunnel ID under Local ID if you configured the Umbrella tunnel to use FQDN.
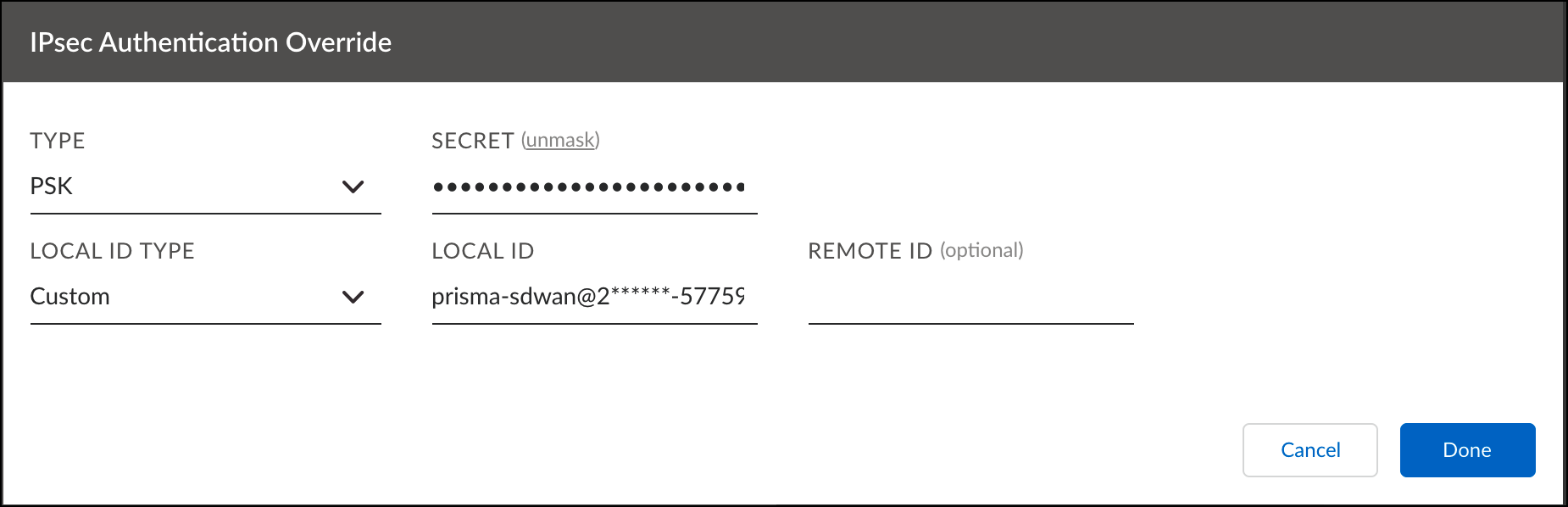
- Click Done and then click Create Standard VPN.
Configure the Prisma Path Policy
Prisma SDWAN uses network policies that define path, priority, and network context for an application. These policies are defined in network policy sets that contain the network policy rules. To leverage the best security of the Umbrella Secure Internet Gateway, you must define the applications an organization wishes to send to Umbrella in the network policy set.
- In Prisma SD-WAN, navigate to Policies > Stacked Policies, click Path, select Path Sets and click Add Set.
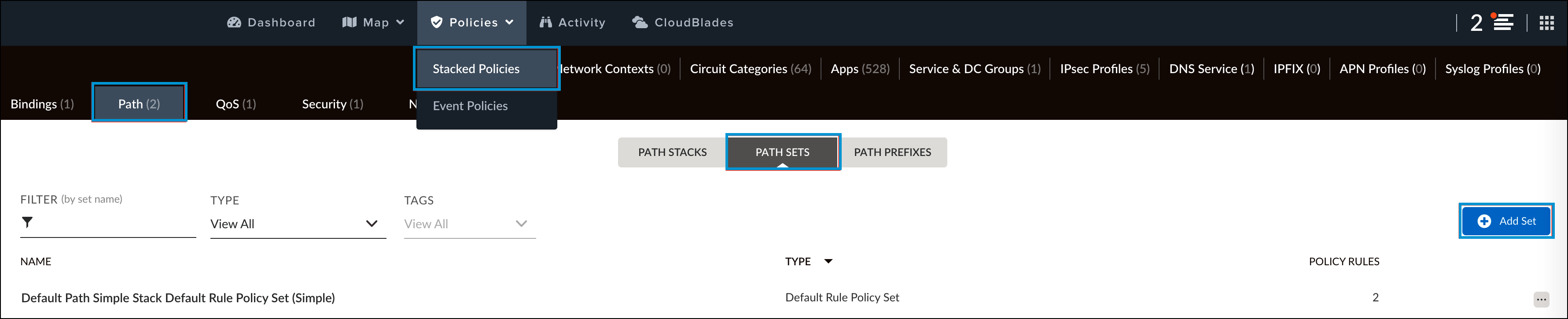
- Provide a meaningful name for the policy and click Done.
- Click on the newly created policy set and click Add Rule.
- In the Info tab, provide a name for the policy rule.
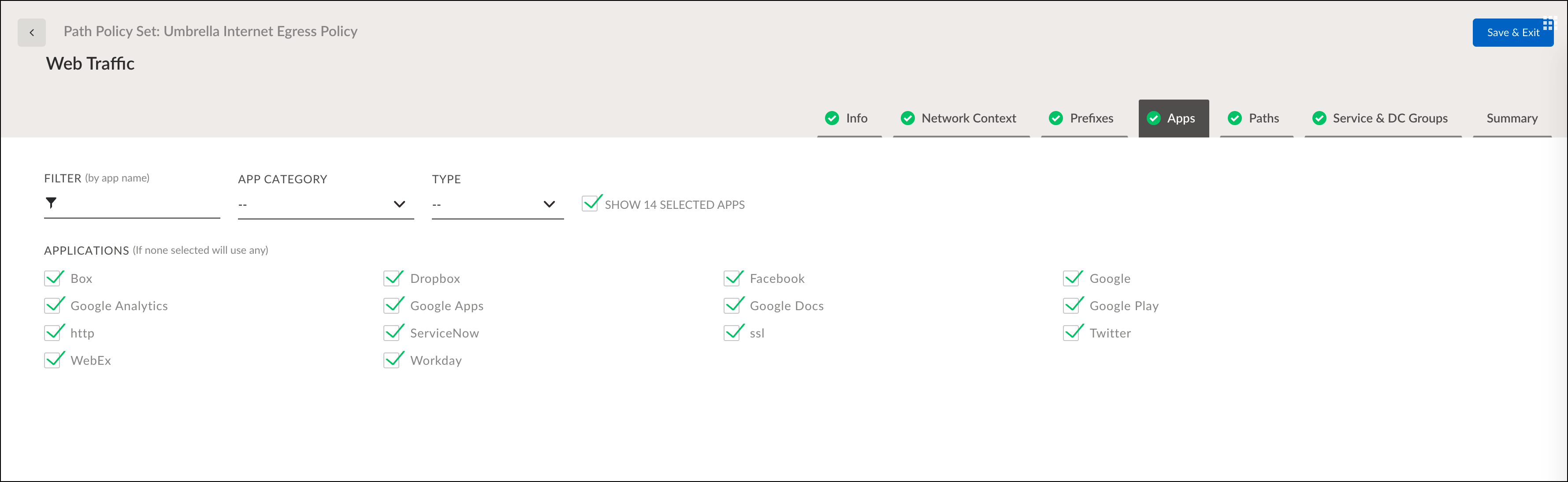
- Click the Apps tab and select app to be forwarded to Umbrella for enforcement. By default, if no applications are selected then all traffic will be routed to Umbrella.
- Click the Paths tab, select Standard VPN from the Overlay drop-down and Any Public from the Circuit Category drop-down.
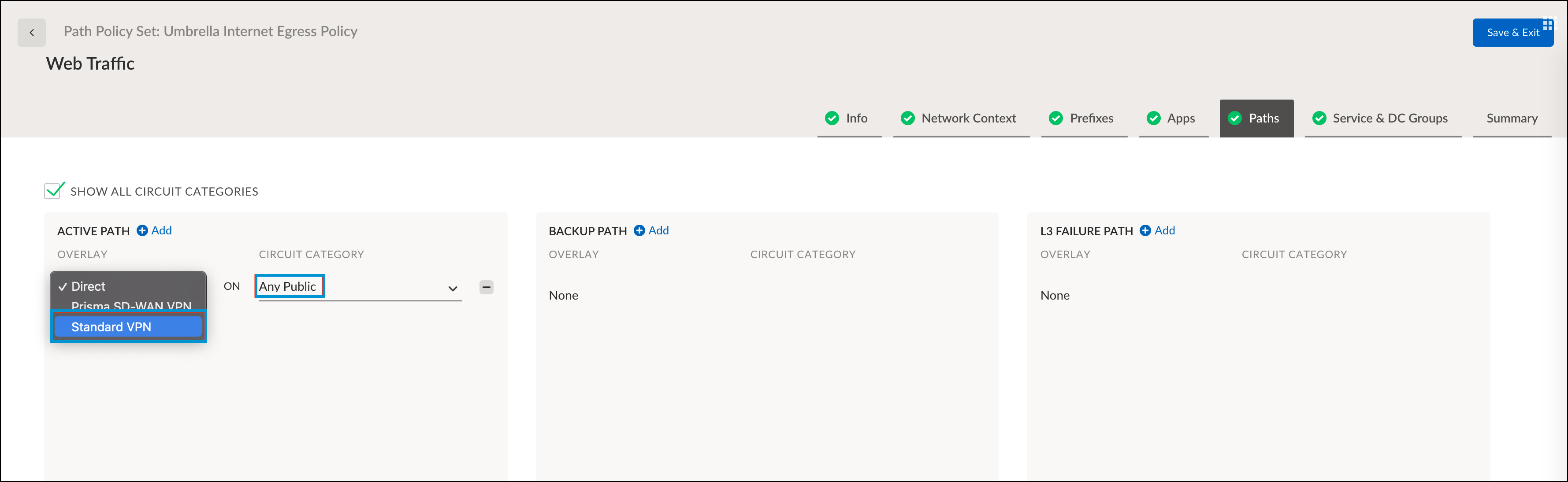
- Click the Service & DC Groups tab and choose the group created in Configure the Prisma Service Endpoint Group.
- Verify the configuration in the Summary tab and click Save & Exit.
Verify the Configuration
- In Umbrella, navigate to Deployments > Core Identities > Network Tunnels and find the newly configured tunnel. Verify the Tunnel Status is Active.
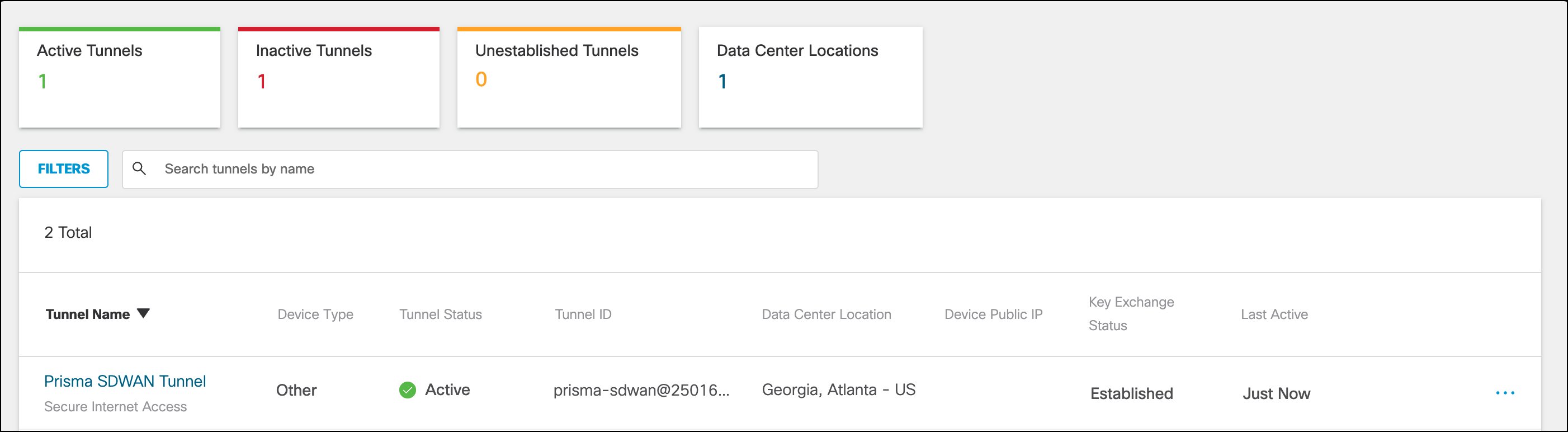
- Generate traffic on the LAN side of the Prisma SDWAN appliance or from an application specified in the Path Policy Set.
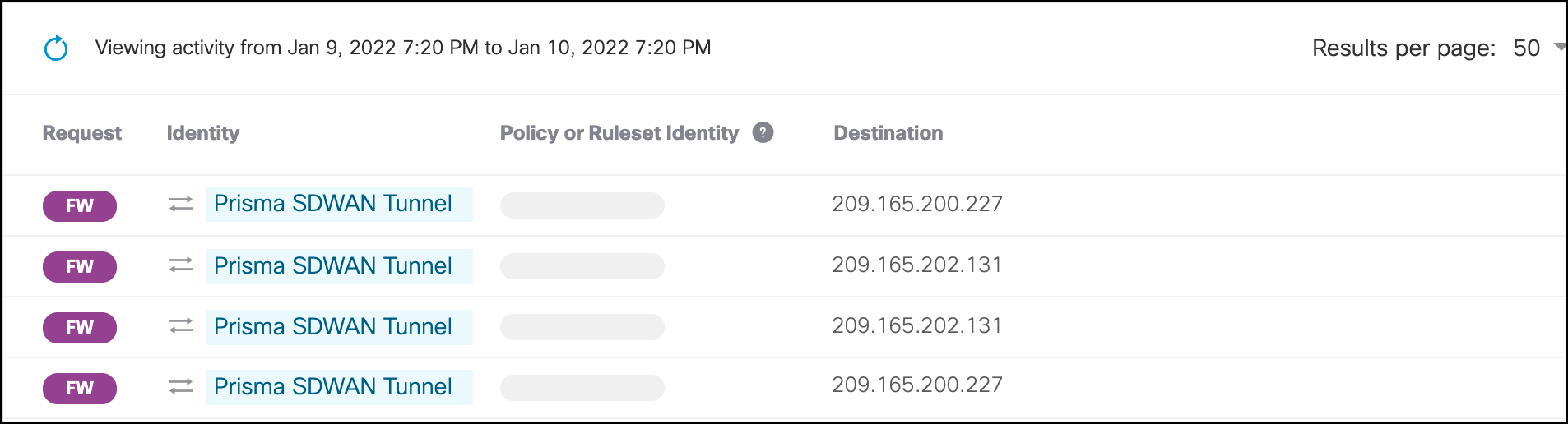
- In Umbrella, navigate to Reporting > Core Reports > Activity Search. Traffic for the tunnel should be logged and searchable by identity name.
Troubleshoot the Configuration
In the event that traffic is not routing to the internet, check the status of the tunnel in the Umbrella dashboard. In Umbrella, navigate to Deployments > Core Identities > Network Tunnels and find the newly configured tunnel. Verify the Tunnel Status is Active. If the status shows Inactive, the following commands can be used in the Prisma SD-WAN Device Toolkit to provide details about the tunnel and its status:
Service Link Summary—displays the information for the standard VPNs configured on the device. Use the ExtState in the command output to identify the state of the tunnel. For a more comprehensive list of the extended states, see Palo Alto documentation.
dump servicelink summary

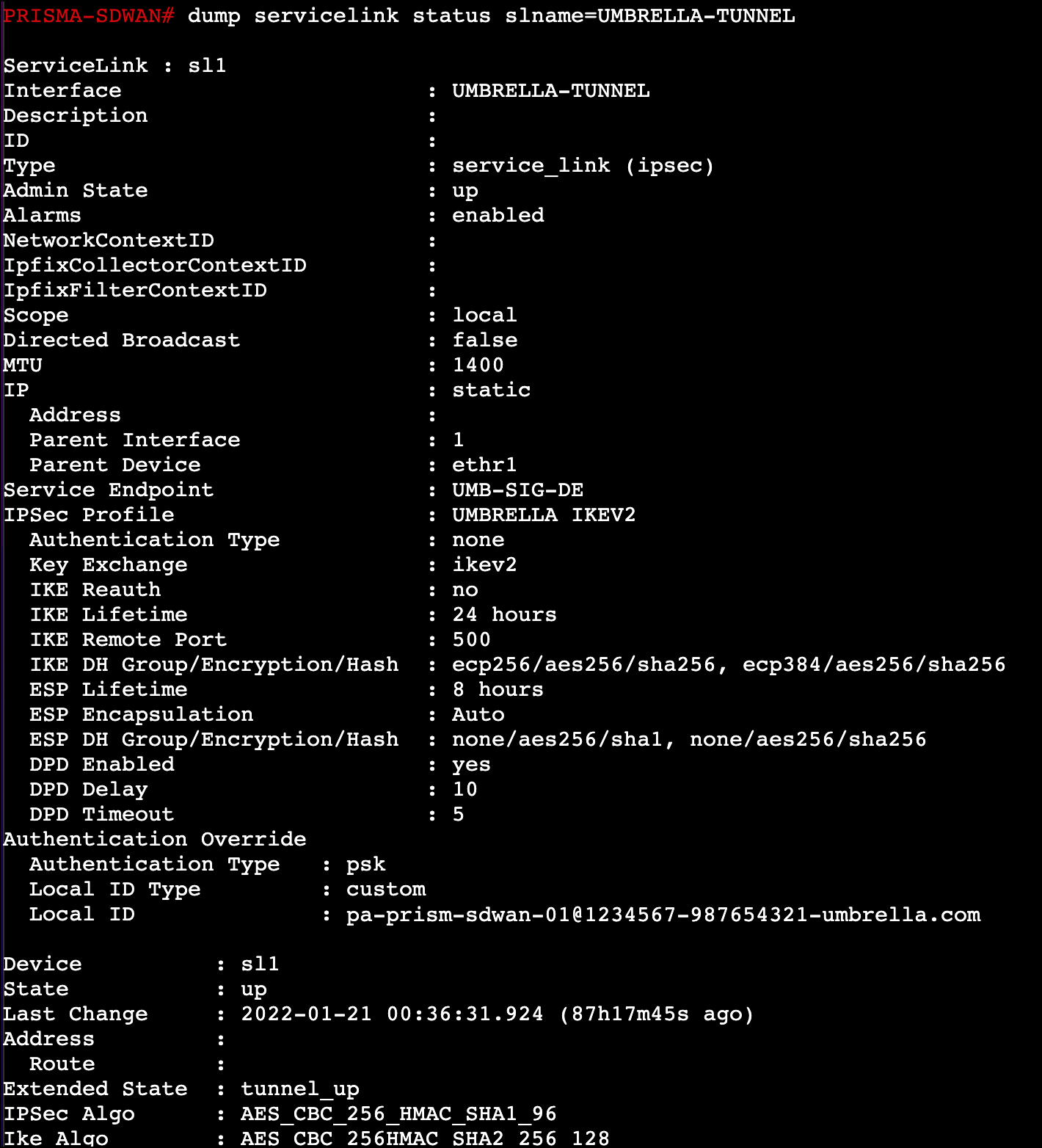
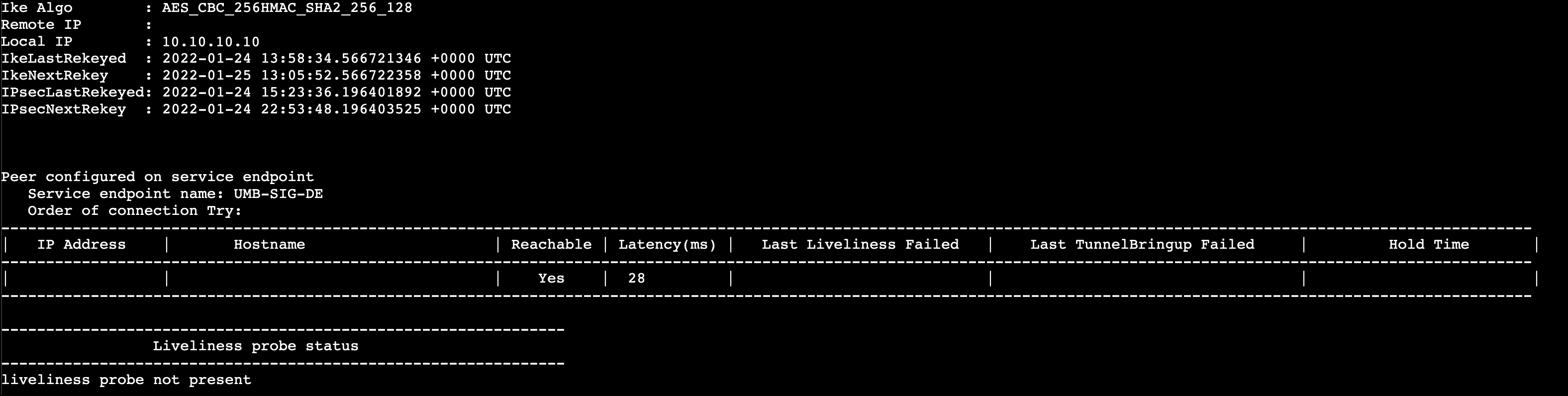
Service Link Status—Checks the status of the standard VPN’s configured on the device. You can verify the configuration of the VPN as well as which IPSec profile is in use.
dump servicelink status
Configure Tunnels with Alibaba Cloud IPsec < Configure Tunnels with Palo Alto Prisma SDWAN > Configure Tunnels with Cisco Router in AWS
Updated about 2 months ago
