Configure the Umbrella Connector
You will need to obtain your Network Devices API token and enable the Umbrella connector to register the ASA.
Table of Contents
- Prerequisites
- Obtain Your API Token
- Configure Umbrella Global Settings
- Enable Umbrella in the DNS Inspection Policy
Prerequisites
- Full Admin access to the Umbrella dashboard.
- For more information about prerequisites, see Prerequisites.
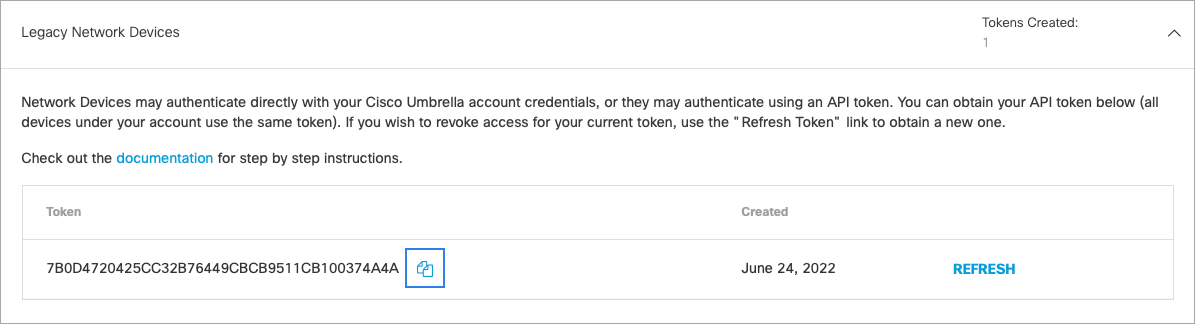
Obtain Your API Token
- Navigate to Admin > API Keys.

- Expand Legacy Network Devices and click Generate New Token.
- Copy the token so that you can complete the next steps.
Configure Umbrella Global Settings
- Enter Umbrella configuration mode.
ciscoasa(config)# umbrella-global
- Configure the API token.
ciscoasa(config-umbrella)# token <api_token>
- (Optional.) If you intend to enable DNSCrypt, you can optionally configure the DNSCrypt provider public key for certificate verification. If you do not configure the key, the default currently distributed public key is used for validation.
ciscoasa(config-umbrella)# public-key <key>
The key is a 32-byte hexadecimal value. Enter the hex value in ASCII with a colon separator for every two bytes. The key is 79 bytes long. The key is preconfigured to B735:1140:206F:225d:3E2B:d822:D7FD:691e:A1C3:3cc8:D666:8d0c:BE04:bfab:CA43:FB79, which is the public key of the Umbrella Anycast servers.
If you modify the value, the DNSCrypt certificate download can fail. Revert to using the default public key by entering the no public-key command.
- (Optional.) Configure the idle timeout after which a connection from a client to the Umbrella server will be removed if there is no response from the server.
ciscoasa(config-umbrella)# timeout edns 00:01:00
The timeout is in hours:minutes:seconds format, and can be from 0:1:0 to 1193:0:0. The default is 0:02:00 (2 minutes).
- (Optional.) Configure the local domain names for which Umbrella should be bypassed.
You can identify local domains for which DNS requests should bypass Cisco Umbrella and instead go directly to the configured DNS servers. For example, you can have your internal DNS server resolve all names for the organization's domain name on the assumption that all internal connections are allowed.
You can enter your local domain name directly. Optionally, you can create the regular expressions that define the name, then create a regular expression class map and specify it on the following command:
local-domain-bypass { regular_expression | regex class regex_classmap}
Example:
ciscoasa(config)# umbrella-global
ciscoasa(config-umbrella)# local-domain-bypass example.com
Enable Umbrella in the DNS Inspection Policy
You can enable Umbrella globally by adding it to the preset_dns_map DNS inspection policy map.
However, if you have customized DNS inspection policy and have applied different inspection policy maps to different traffic classes, you must enable Umbrella on each class where you want the Umbrella connector enabled.
- Edit the preset_dns_map inspection policy map and enter parameter configuration mode.
ciscoasa(config)# policy-map type inspect dns preset_dns_map
ciscoasa(config-pmap)# parameters
- Enable Umbrella and optionally specify the name of the Umbrella policy to apply to the device.
The tag is the name of a policy as defined in Umbrella. During registration, Umbrella will assign the policy to the device (if the policy name exists). If you do not specify a policy, the default policy is applied.
Tag Naming Restrictions
Tags cannot contain spaces. If the Umbrella policy you are referencing contains spaces, you can substitute the spaces for dashes (-).
ciscoasa(config-pmap-p)# umbrella [tag <umbrella-policy>]
- (Optional.) Enable DNSCrypt to encrypt connections between the ASA and Umbrella.
Enabling DNSCrypt starts the key-exchange thread with the Umbrella resolver. The key-exchange thread performs the handshake with the resolver every hour and updates the device with a new secret key. Because DNSCrypt uses UDP/443, you must ensure that the class map used for DNS inspection includes that port. Note that the default inspection class already includes UDP/443 for DNS inspection.
ciscoasa(config-pmap-p)# dnscrypt
After Umbrella has been configured globally and enabled in DNS inspection, the ASA will register itself to your Umbrella account and can be found under Deployments > Core Identities > Network Devices.
First, check the service policy statistics, and look for the Umbrella Registration line. This should indicate the policy applied by Cisco Umbrella (the tag), the HTTP status of the connection (401 indicates that the API token was incorrect, and 409 indicates that the device already exists in Cisco Umbrella), and the device ID.
Import the Digicert Certificate Authority < Configure the Umbrella Connector > Verify Operation
Updated almost 2 years ago
