Enable Cisco Secure Malware Analytics (Threat Grid)
Web Policies Only
Cisco Secure Malware Analytics (Threat Grid) Malware Analysis is only available for the Web policy.
Cisco Secure Malware Analytics (Threat Grid) is Cisco's malware analysis and threat intelligence platform. Secure Malware Analytics (Threat Grid) generates and gathers malware intelligence through static and dynamic runtime sample analysis, as well as from other Cisco integrations. When you enable Umbrella's File Inspection and Secure Malware Analytics (Threat Grid) features, files not blocked through File Inspection and that are unknown to Advanced Malware Protection (AMP) file reputation or blocked by Umbrella's anti-virus (AV) may be submitted by Umbrella to Secure Malware Analytics (Threat Grid) for malware analysis. This includes file types known to carry malware or be a conduit for malware, such as EXE and PDF files.
Thus, a file not blocked by Umbrella because File Inspection does not detect that the file is malicious can be downloaded when requested; however, with Secure Malware Analytics (Threat Grid) enabled, an unknown file is also submitted to Threat Grid for further examination. Secure Malware Analytics (Threat Grid) may also sandbox a submitted file so that it can be analyzed in safety to determine whether or not it is malicious. If Secure Malware Analytics (Threat Grid) determines that a file is malicious, Secure Malware Analytics (Threat Grid) sends this information to AMP and Umbrella's File Inspection feature blocks any new attempts to download the file, which is now known to be malicious. While Secure Malware Analytics (Threat Grid) does not protect against the first download of a new or unknown malicious file, it is an important addition to your organization's defenses against threats because it can prevent future downloads. The next device in your organization that attempts a download is now protected. In fact, now that AMP knows about this file, all Umbrella SIG customers with File Inspection enabled are protected.
For more information about AMP, see Advanced Malware Protection (AMP).
Umbrella's Secure Malware Analytics (Threat Grid) Integration
Secure Malware Analytics (Threat Grid) integration with Umbrella is included with Umbrella's secure web gateway (SWG). This integration includes access to a version of Secure Malware Analytics (Threat Grid)'s dashboard.
When you enable Secure Malware Analytics (Threat Grid) for the first time, you must choose a sandbox location. Once this location is set, you are sent an email from Secure Malware Analytics (Threat Grid) with credentials information including your login and a link to reset your password, which you must do within 36 hours. You cannot use your Umbrella credentials to log into Secure Malware Analytics (Threat Grid). Your login credentials to Secure Malware Analytics (Threat Grid) give you access to Secure Malware Analytics (Threat Grid)'s functionality that allows you to view files submitted to Secure Malware Analytics (Threat Grid) by Umbrella's File Analysis feature. For more information about how to use Secure Malware Analytics (Threat Grid), see Secure Malware Analytics (Threat Grid)'s Help which is available from the Secure Malware Analytics (Threat Grid) dashboard.
When integration is enabled through Umbrella, Secure Malware Analytics (Threat Grid) is limited to examining a maximum of 500 files (or unlimited for SIG Advantage) per 24 hours. As well, there is a file size limitation of 50 MB. Files over 50 MB in size are not submitted to Secure Malware Analytics (Threat Grid). You must log into Secure Malware Analytics (Threat Grid) to monitor the number of files submitted within a 24 hour period. At the end of the rolling 24 hour time period, this quota is cleared and submissions start again—if this hard limit of 500 files is reached; otherwise, submissions continue unabated. To increase this limit of 500 files per 24 hours, contact your account manager.
For multi-org deployments of Umbrella, the rolling limit of 500 files (or unlimited for SIG Advantage) per 24 hours is shared between the parent and child organizations. The limit of 500 files is calculated by combining all child and parent organization submissions. Each child organization does not have its own limit of 500 files per 24 hours.
Cisco Umbrella SIG Advantage Secure Malware Analytics (Threat Grid) Quota
There is no limit to Secure Malware Analytics (Threat Grid) files for SIG Advantage licenses. To determine your current package, navigate to Admin > Licensing. For more information, see Determine Your Current Package. See also, Cisco Umbrella Packages.
Depending on your package, access to Secure Malware Analytics (Threat Grid)'s dashboard may have a number of features disabled which are only available to SIG Advantage customers. If you are a Secure Malware Analytics (Threat Grid) Cloud customer and have access to the full functionality of Secure Malware Analytics (Threat Grid), you can link your Umbrella account to your Secure Malware Analytics (Threat Grid) Cloud portal. For more information, contact your account manager or Secure Malware Analytics (Threat Grid) support.
For more information about Secure Malware Analytics (Threat Grid), see Cisco Secure Malware Analytics (Threat Grid).
Monitor and Review Secure Malware Analytics (Threat Grid) Malware Analysis
Umbrella does not provide you with information about Secure Malware Analytics (Threat Grid)'s activities. You must log into Secure Malware Analytics (Threat Grid) to view files that have been submitted to Secure Malware Analytics (Threat Grid) by Umbrella's File Analysis feature. For more information about how to use Secure Malware Analytics (Threat Grid), see Secure Malware Analytics (Threat Grid)'s Help which is available from the Secure Malware Analytics (Threat Grid) dashboard.
Files submitted by Umbrella to Secure Malware Analytics (Threat Grid) that become marked as malicious can be reviewed under the File Retrospective section of Umbrella's Overview report. For information about how to get a better understanding and visibility into files marked as malicious by Secure Malware Analytics (Threat Grid), see File Retrospective Events and Secure Malware Analytics (Threat Grid).
Supported Files
The following file types are supported for submission to Secure Malware Analytics (Threat Grid):
bat, bz2, chm, dll, doc, docx, eml, exe, gz, hta, hwp, hwt, hwpx, iso, jar, jtd, jtt, jtdc, jttc, lnk, msg, msi, mhtml, rar v5, rtf, xls, xlsx, ppt, pptx, pdf, ps1, sep, slk, swf, tar, vbe, vbn, vbs, wsf, xml, xps, xz, zip, 7-zip
The following mime types are not supported for submission to Secure Malware Analytics (Threat Grid): text/html
MS Office documents, PDFs and executables are all submitted to Secure Malware Analytics (Threat Grid).
For more information about supported file types, see Secure Malware Analytics (Threat Grid) documentation accessible through the Secure Malware Analytics (Threat Grid) dashboard under Sample File Types.
Secure Malware Analytics (Threat Grid) Sandbox
The first time you enable Secure Malware Analytics (Threat Grid) Malware Analysis, you must select a sandbox region: Europe or North America. Once selected, this location cannot be changed. This sandbox is a protected environment within which Secure Malware Analytics (Threat Grid) is able to detonate unknown files to determine whether or not they are harmful. Not all files submitted to Secure Malware Analytics (Threat Grid) are sandboxed.
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
Procedure
Like File Inspection, Secure Malware Analytics (Threat Grid) Malware Analysis can only be enabled through the Web policy's wizard.
- Navigate to Policies > Management > Web Policy and expand an existing ruleset or click Add to add a new ruleset.

- Under Ruleset Settings, for File Analysis, click Edit.
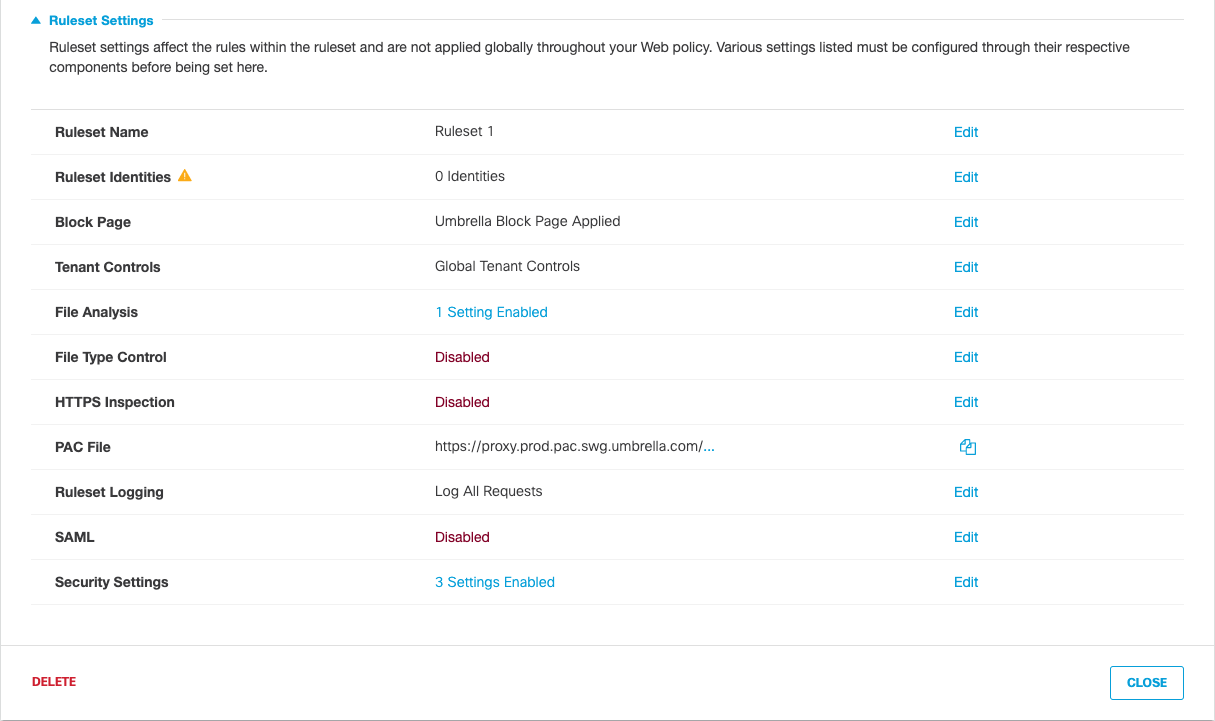
- If disabled, enable File Inspection.
Note: File Inspection is disabled by default.

- Enable Secure Malware Analytics (Threat Grid).
Note: To enable Secure Malware Analytics (Threat Grid) Malware Analysis, File Inspection must be enabled.

a. If you are enabling Secure Malware Analytics (Threat Grid) Malware Analysis for the first time, select a Sandbox Region (North America or Europe), acknowledge that you understand that this location cannot be changed, and then click Save.
Note: The region you select should match the region for which your Secure Malware Analytics (Threat Grid) API key was generated. Europe uses panacea.threatgrid.eu and North America uses panacea.threatgrid.com.
Your new sandbox region is set and cannot be changed.
b. From the email you receive from Secure Malware Analytics (Threat Grid), use your credentials to change your password, accept Secure Malware Analytics (Threat Grid)'s End User Agreement and log into Secure Malware Analytics (Threat Grid).
Note: You must log into Secure Malware Analytics (Threat Grid) within 36 hours of setting your sandbox region.
Enable File Inspection for the Web Policy < Enable Cisco Secure Malware Analytics (Threat Grid) > Test File Inspection
Updated almost 2 years ago
