Add an FQDN List to a Firewall Rule
A fully qualified domain name (FQDN) is the full name of a host or a server on the Internet. An FQDN specifies all domain levels written in the hostname.domain.tld format; for example, mail.yahoo.com, www.wordpress.org, or news.bbc.co.uk.
You can use FQDN lists to control access to destination domains using specific protocols or ports. FQDNs in firewall rules can filter outbound traffic with any TCP/UDP protocol, such as NTP (port 123), SSH (port 22), or RDP (port 3389). The firewall rules are enforced based on the IP addresses resolved from the associated FQDNs.
Once an FQDN list is added to a firewall rule, Umbrella will resolve IP addresses for the associated FQDNs and ensure the IP addresses of FQDNs are up to date. All packets are then inspected by the cloud-delivered firewall (CDFW) and blocked or allowed by checking the destination IP addresses against the IP addresses resolved from the FQDN list.
Table of Contents
Prerequisites
- An internet connection that allows outbound IPsec traffic.
- Full admin access to the Umbrella dashboard. See Manage User Roles.
- A network device capable of establishing an IPsec IKEv2 tunnel. For supported network devices, see Supported IPsec Parameters.
- At least one tunnel added. For more information about adding tunnels, see Network Tunnel Configuration.
Limitations
- Firewall destination lists are not designed to be used for HTTP/HTTPS traffic.
- The rule behavior is not predictable when the target destination (FQDN) may resolve to many different IP addresses or receive answers which are geolocation-specific. For example, if the resource is on a CDN (Content Delivery Network), the IP address in the firewall policy could be different from the address the client is trying to access leading to inconsistent firewall policy application.
- Neither implicit nor explicit wildcards are supported.
- Private/internal domains are not supported since the DNS server being used by CDFW is not configurable.
- FQDN lists are not designed to filter URLs or web-based applications. It is recommended that you use Umbrella SWG URL filtering and firewall rules with internet-based application controls for general web-based access control.
- FQDN lists must only be used as a fallback solution if URL filtering or Layer 7 App Control do not work.
- Each firewall rule can only have one FQDN list added.
Procedure
- Navigate to Policies > Management > Firewall Policy and click Add or expand an existing firewall rule.

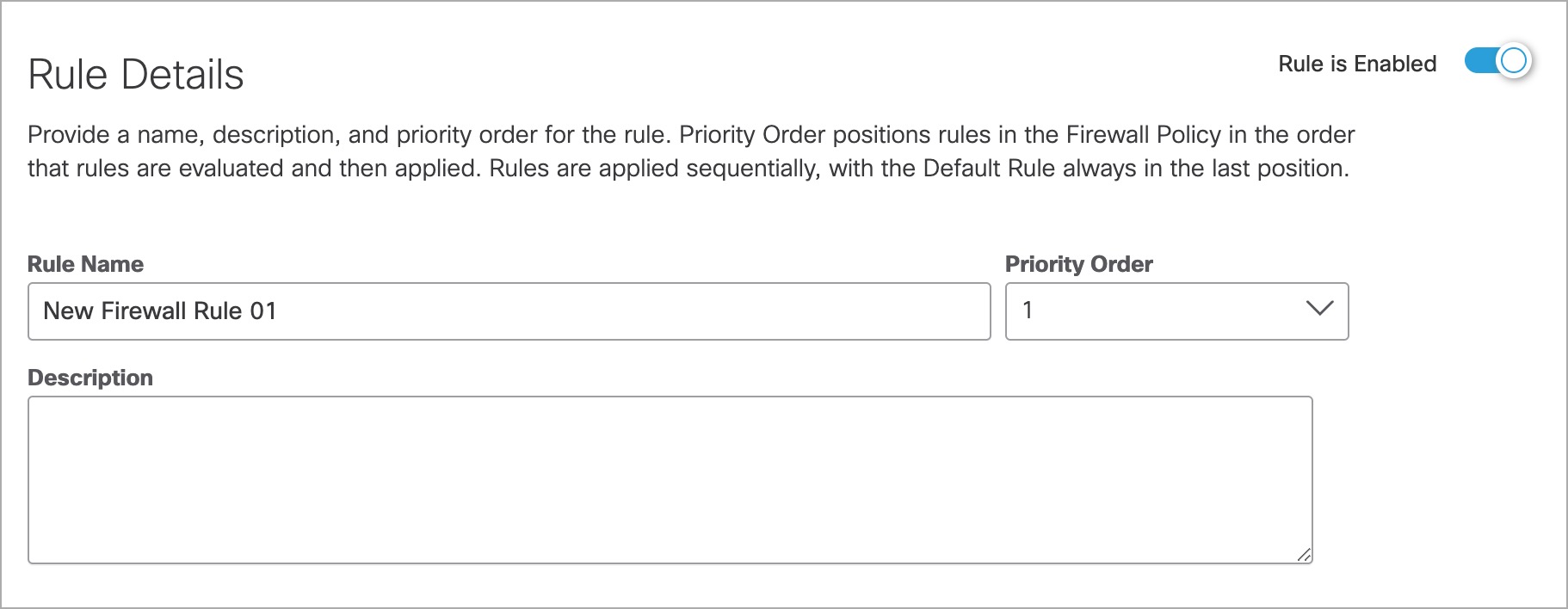
- Define the basic characteristics of your firewall rule:
a. Choose a descriptive Rule Name and Description.
b. Choose a Priority Order. Priority Order positions rules in the Firewall Policy in the order in that rules are evaluated and then applied. Rules are applied sequentially, with the Default Rule always in the last position.
c. Enable or Disable your firewall rule.
- Choose a Rule Action to apply to this policy.

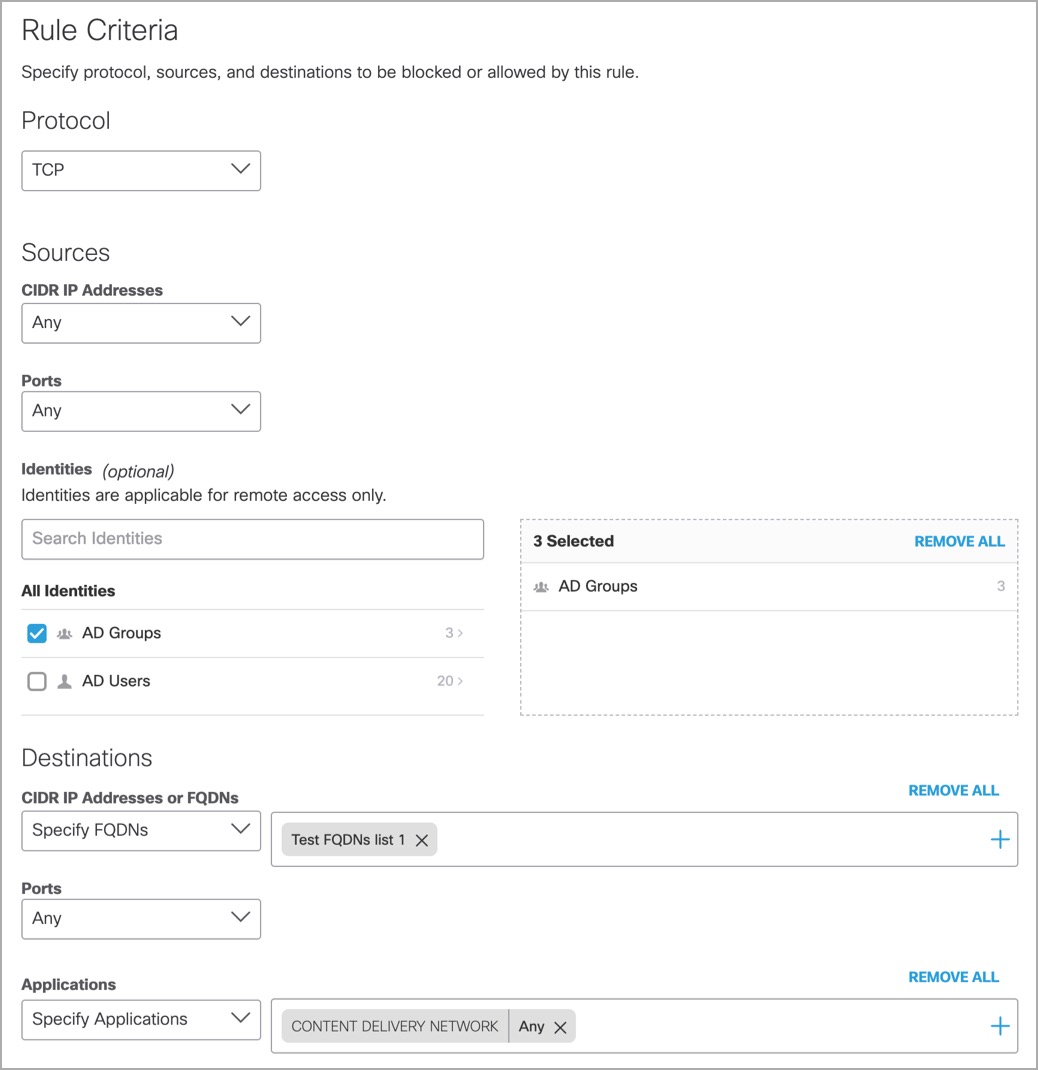
- Under Rule Criteria, choose an option for protocol, sources, and destinations to be blocked or allowed by this rule.
a. Protocol—The protocols to which the rule applies. Options are TCP, UDP, ICMP, or Any Protocol.
Sources:
b. Source CIDR IP Addresses—The tunnel's source addresses (IP or CIDR) to which the rule
applies. You can choose Specify IP and add each CIDR IP address, or choose Any.
c. Ports—The tunnel's source ports to which the rule applies. You can choose Specify Port and enter ports or port ranges in a comma-delimited plain-text list, or choose Any.
d. Identities: Select the groups and/or users to which the rule applies.
Destinations:
e. CIDR IP Addresses or FQDNs—The tunnel's destination addresses (IP or CIDR) to which the rule applies. You can choose Specify IP and add each CIDR IP address, or choose Any.
f. Ports—The tunnel's destination ports to which the rule applies. You can choose Specify Port and enter ports or port ranges in a comma-delimited plain-text list, or choose Any.
g. Applications—The applications and application categories to which the rule applies. For more information, see Application Categories.
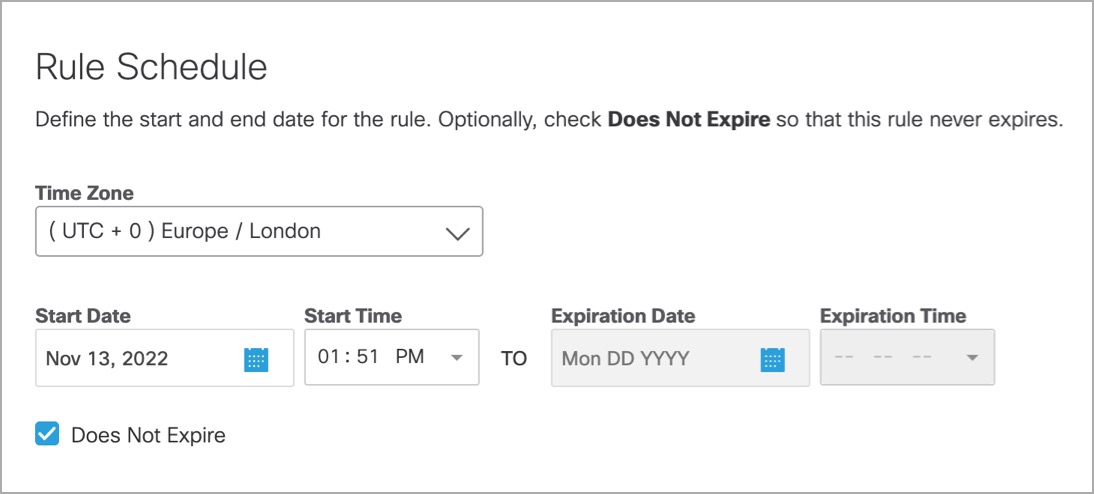
- Under Rule Schedule, select a Time Zone and configure Start and Expiration dates and times. Optionally, check Does Not Expire so that your rule will not expire.
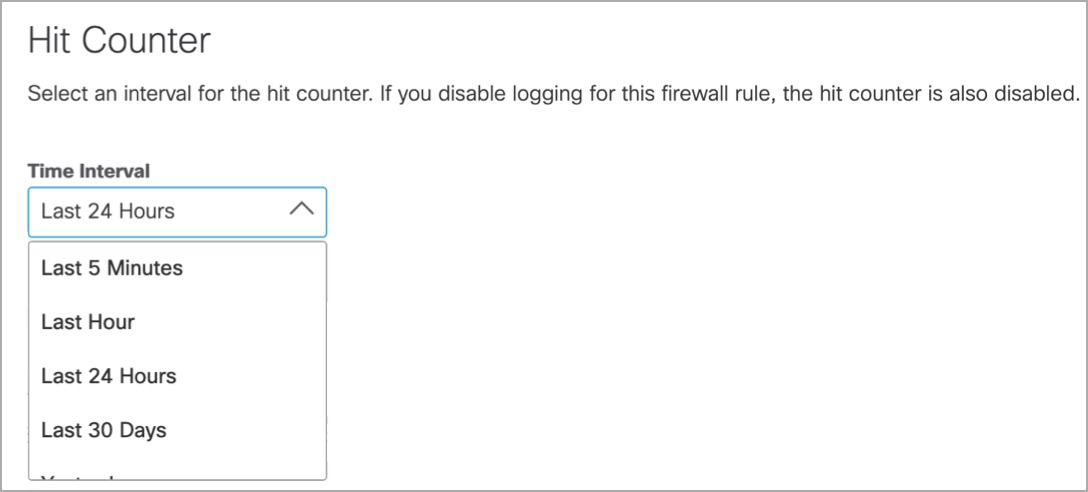
- Under Hit Counter, select an interval. Hit count is the number of times a firewall rule has been invoked, as well as the most recent invocation time. For more information, see Monitor Hit Count.
- To capture the firewall rule in Activity, enable the Logging toggle.
Note: If logging is disabled for a given policy, the hit count for that policy is also disabled. Logging is disabled by default.

- Click Save.
Add a Firewall Rule < Add an FQDN List to a Firewall Rule > Bypass SWG using FQDN
Updated about 1 year ago
