Umbrella Integration with Secure Web Appliance
About Secure Web Appliance
The Cisco Secure Web Appliance (SWA) intercepts and monitors Internet traffic and applies policies to help keep your internal network secure from malware, sensitive data loss, productivity loss, and other Internet-based threats. The integration of Cisco Umbrella SWG and SWA facilitates the deployment of common web policies between the two products. For more information, see Cisco Secure Web Appliance.
Table of contents
- Integrate Umbrella with SWA
- Prerequisites
- Known Limitations
- Known Behavior
- Add an API Key and Key Secret
- Register Secure Web Appliance with Umbrella
Integrate Umbrella with Secure Web Appliance (SWA)
- Ensure that the prerequisites are met on Umbrella.
- Generate an API key and Key secret on Umbrella.
- Complete the registration on Secure Web Appliance.
- Confirm the registration on Umbrella.
Prerequisites
- For a successful connection to Umbrella, update the Cert bundle to the latest version.
- To configure the translated policy from Umbrella, update the Content Categories to the latest version
- Manually enable the HTTPS Proxy in SWA, if HTTPS Inspection is enabled in Umbrella Ruleset.
- If an Active Directory (AD) is integrated with Umbrella, configure the same AD realm in SWA. Cisco recommends that you have a healthy AD Connector and Domain Controller.
- In SWA, enable Application Discovery and Control (ADC) under Security Services > Acceptable Use Controls for translation of the application settings selected in Umbrella rules.
- In Umbrella, ensure that a minimum of one internal network is associated with the public network or AD integrated with Umbrella.
Note: As per the prerequisites of internal networks, virtual appliances must be in use.
Known Limitations
- Policy translation is not triggered in the following scenarios:
- Ruleset name change.
- Name change in the Destination list selected in Rule.
- Name change in the application list selected in the Rule.
- Name change of selective decryption list selected in HTTPs inspection.
- Adding or removing categories in the selective decryption list used for HTTPs inspection.
- Selective decryption list consisting of only categories is selected in HTTPs inspection.
- Adding or removing AD Users or Groups in Ruleset and Rules.
- Integrating or removing AD in the Umbrella dashboard.
-
If Ruleset Identities are the same in multiple rulesets, then consistent HTTPs inspection settings translation is triggered only for the first Ruleset of the same identity.
-
Format for End-User Notification Pages → Notification Type: Redirect to Custom URL text box supports only well-formed hostname or IPv4 address. If you push other URL formats configured in the Block Page of Umbrella to SWA, the policy push fails with the error message: An http/https URL must consist of a well-formed hostname or IPv4 address, may optionally include a port, but may not contain a query string ('?...').'.", 'code': '400', 'explanation': '400 = Bad request syntax or unsupported method.
-
If AD Groups are selected in Rulesets and Rules do not match, the access policy is not created for that rule.
-
Categories and Domains selected in Selective Decryption List are set to Passthrough for decryption policies pushed from Umbrella to SWA. No access policy is applied to the pre-defined and custom URL categories in SWA. However, in Umbrella, Rules are applied to the same configuration.
-
If Microsoft 365 compatibility is enabled in Umbrella, it is set to Passthrough for Umbrella pushed decryption policies in SWA. So all categories of Microsoft 365 endpoints get passthrough.
-
If a Trusted AD is not configured in SWA and a group is selected for that AD in Umbrella, an error message to configure the AD is displayed in SWA.
-
If networks with different masks are selected in Ruleset and Rule, translation is not supported.
-
If a large number of applications are selected across Rules, Secure Web Appliance performance is affected.
-
To avoid redundant configuration, Cisco recommends using an application list rather than selecting individual applications in Rules.
Hybrid Reporting
- If the user is not included in Umbrella policies, mapping the AD User to Umbrella origin ID is not possible. Events of this type are identified by SWA origin ID.
- Filtering Support
- Only external IP addresses are supported by SWA-based filtering.
- SWAs from the same Org (different locations) having the same management IP address will result in combined reporting data.
- For LDAP/ISE/Guest-based identities, SWA does not support AD user-based identities.
- In some cases, the system may see duplicates or lost reporting entries.
Known Behavior
Hybrid Policy
- By default, the source interface in SWA Umbrella settings is set to Management. Changing the source interface to Data requires you to submit and commit the changes before enabling Hybrid Policy.
- Hybrid policies support translation for rule actions Allow, Block, and Warn.
- There is support for translation of Content Categories, Destination Lists, and Applications.
- Translation of AD Users, AD Groups, and internal networks that are associated with public networks is supported.
- In SWA, one Global Umbrella pushed identification profile will always be available.
- Policies that are configured by SWA administrator are prioritized following the policy push from Umbrella.
- When policy push is enabled in the registered appliance page, policies configured in the Umbrella are pushed to all SWAs registered under Umbrella.
- The WBRs are disabled for Decryption Policies pushed by Umbrella.
- The decryption policies pushed by Umbrella are set to Decrypt action by default.
- The End-User Notification page is always enabled in SWA as a global setting.
- In SWA, the End-User Notification page is configured only for the block page first selected in the ruleset of Umbrella.
- Changes in the selected block page appearance of the first ruleset is translated every three hours.
- In the case of identification profiles and customer categories pushed by Umbrella, policies configured by admin, are disabled from the SWA side if these profiles or categories are deleted from Umbrella.
- SWA registration with Umbrella ORG is limited to the number of seats assigned to a specific ORG, which can be seen in the following path of the Umbrella user interface: Admin > Licensing > Number of seats.
- SMA policies cannot be pushed to SWA when it is registered with Umbrella ORG.
- Umbrella cannot push profiles, policies, and custom URL categories to SWA, if there is no internal network and AD integrated in Umbrella.
- If API keys that were used for registration and enabling hybrid service are expired, the connection is not closed until you enable hybrid policy or registered SWA with Umbrella again.
- Rules Scheduling and Protected Bypass Umbrella rules configurations are not supported for hybrid policy push.
- The SMA policies pushed to SWA are not accepted if the SWA is managed by Umbrella.
- The Save and Load configuration feature does not work for Umbrella settings.
- Translation is not supported for the following Ruleset settings:
- Ruleset Identities - Chromebooks, G Suite OUs, G Suite Users, Tunnels, Roaming Computers, Internal Networks All Tunnels
- Tenant Controls
- File Analysis
- File Type Control
- HTTPS Inspection - only applications in Selective Decryption list
- PAC File
- SafeSearch
- Ruleset Logging
- SAML
- Security Settings
- The changes made to the HTTPS proxy or AD realm on the SWA do not affect the umbrella policy.
- Application Settings (CASI) Translation
- Application Settings selected in Rules are translated and pushed to SWA Access Policy only when ADC is enabled under Security Services > Acceptable Use Control in SWA.
- When the Application is selected in the Rule, a Custom URL category containing the domains of the selected application will be pushed to that Rule. This same category of Custom URLs is selected under the URL Filtering section of the Access Policy, with Monitor as the action.
- The application available in SWA but not in Umbrella inherits the global settings action. The application available in Umbrella but not in SWA is ignored.
- In SWA, applications that are not selected within Rules inherit the global settings.
- Selective Policy Push
- Umbrella web policies are pushed to registered SWAs only if the Hybrid Policy state is Active and Policy Push is enabled.
- Umbrella UI Error Message
- The error message for the last policy push failure can be seen on the Registered Appliance page, which has a maximum character limit of 1024.
- Cleanup of Policies Pushed by Umbrella
- After the policies pushed by Umbrella are cleaned up, all policies configured by admin are disabled.
Hybrid Reporting
- The hybrid reporting feature of SWA can be enabled only if a hybrid policy is enabled.
- The SWA sends the reporting data from policies configured by Umbrella, to the Umbrella dashboard.
- Approximately 25% of the local disk space used for reporting, is used to store hybrid reporting data, which is then pushed to Umbrella.
- When SWA does not push the reporting data to Umbrella, it locally stores only the reporting data that would be needed later for debugging.
- An SWA continues to send reporting data evaluated by Umbrella policies, even after selective policy push is disabled for that SWA. The Umbrella policy reporting dashboard may display deleted rules for those records if the rule has been deleted from the Umbrella policy.
Add an API Key and Key Secret
The Umbrella API enables you to manage and protect your networks, tunnels, network entities, and users. You can manage access to destinations, and view and update policies. You can create and manage various types of API keys in Umbrella. Use your API key credentials to authenticate requests to the Umbrella API, the legacy Umbrella API, the Umbrella KeyAdmin API, and the Umbrella Identity Provider API.
Note: While generating the API Key and Key Secret, ensure that you select Key Scope as Auth and Registered Appliances as Deployments.
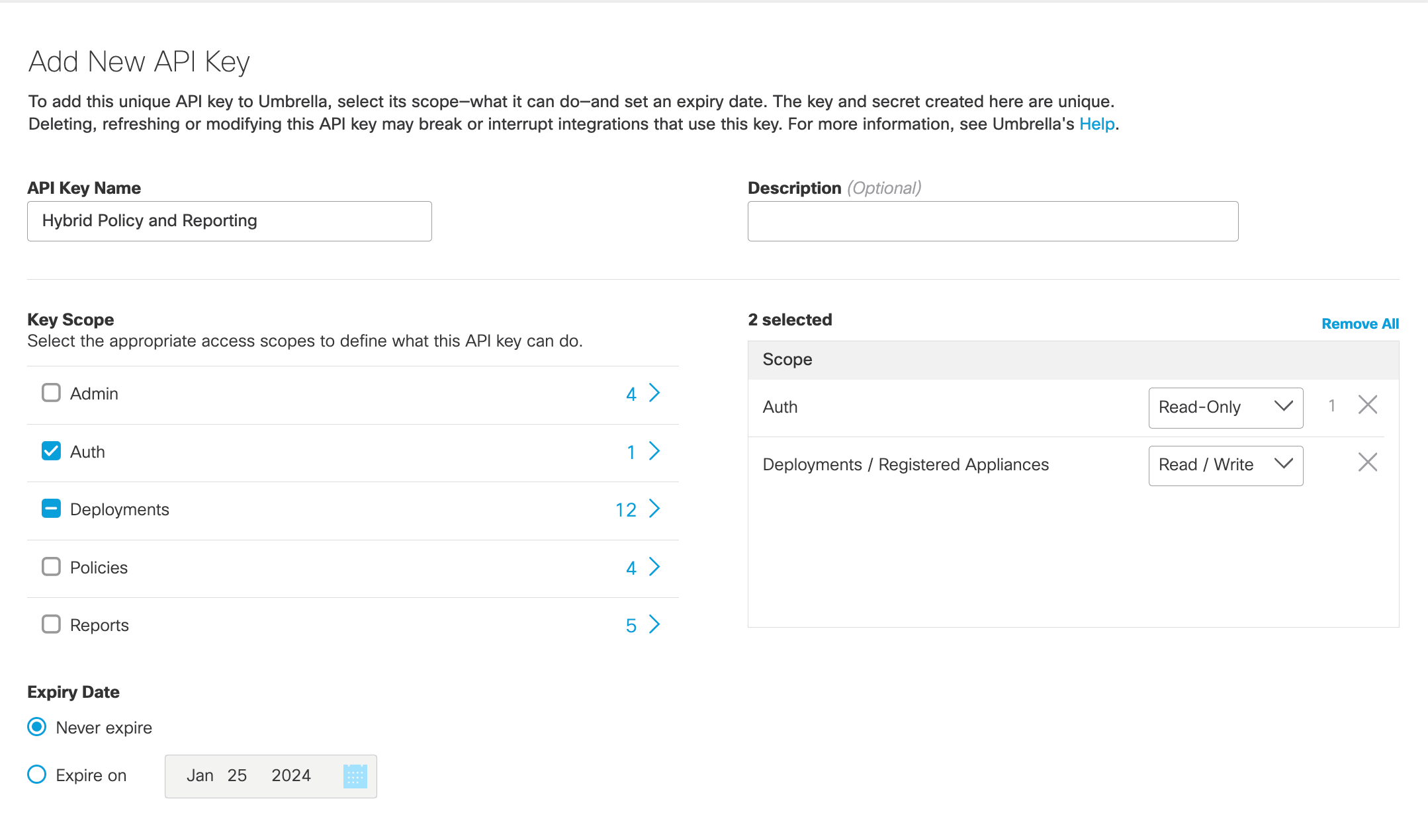
Register Secure Web Appliance with Umbrella
In Umbrella, registered devices are displayed at Deployments > Core Identities > Registered Appliances. You can configure SWA policies using Umbrella services.
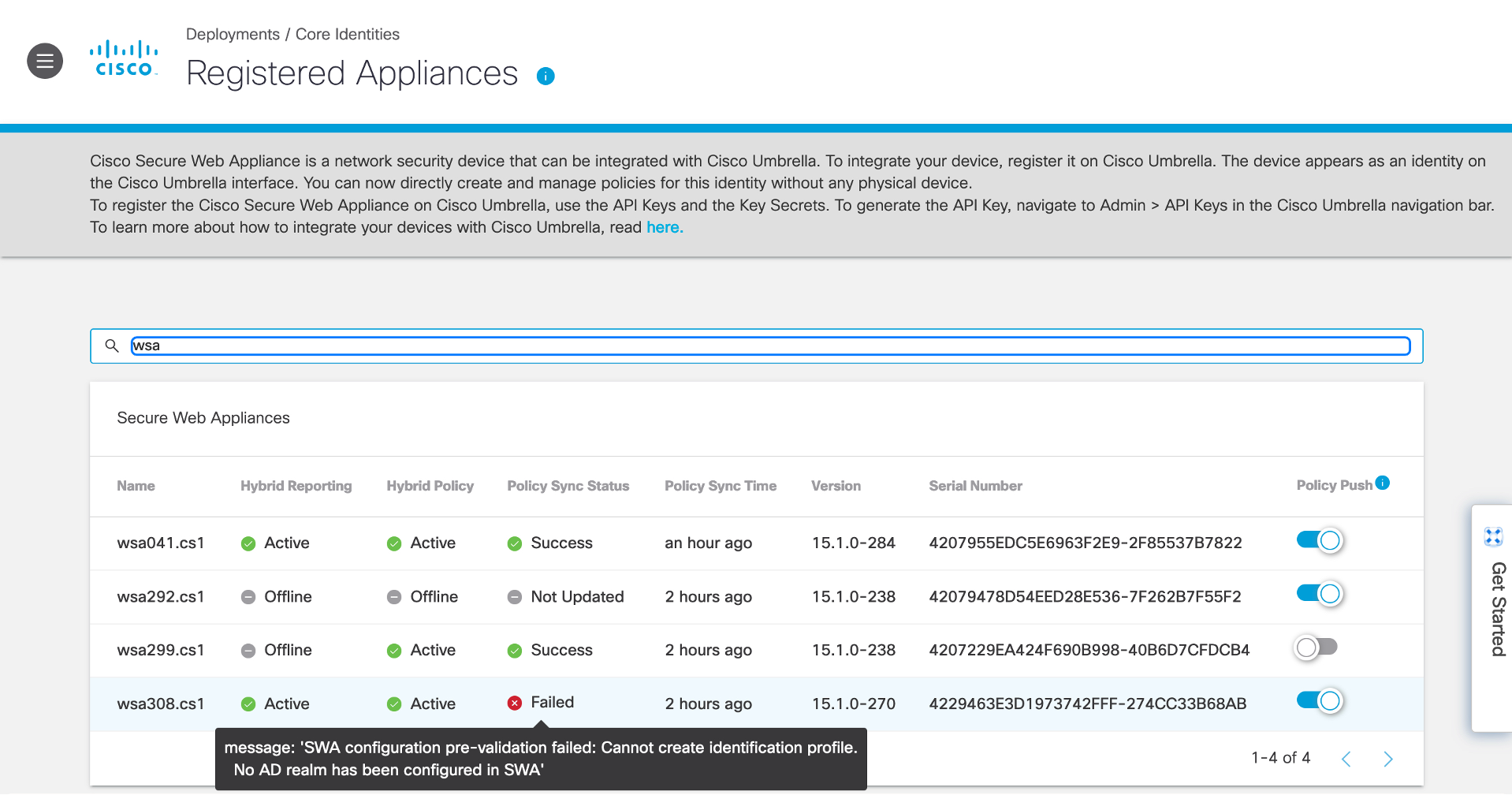
- Name: Name of the SWA.
- Hybrid Reporting:
- Active: Logs related to policies pushed by Umbrella to SWA are sent to Umbrella.
- Offline: Logs related to policies pushed by Umbrella to SWA are not sent to Umbrella.
- Hybrid Policy:
- Active: Supported Umbrella configurations are pushed to SWA.
- Offline: Web policies are not pushed to SWA.
- Policy Sync Status:
- Never Updated: Umbrella policies have never been pushed to SWA after registration.
- Success: Umbrella policies are pushed to SWA.
- Failed: Umbrella policies have not been pushed to SWA because of a failure.
Note
If the Policy Sync Status is Failed, you can view the error message in the UI by hovering your mouse over the Failed status.
- Policy Sync Time: The time at which the latest policy push sync was done.
- Version: The Build version of the SWA.
- Serial Number: Serial number of the SWA
- Policy Push:
- Enable: Web policies are pushed to the selected SWAs.
- Disable: Web policies are not pushed to the selected SWAs.
You can now configure SWA policies using Umbrella services.
For Hybrid Policy and Hybrid Reporting to be in the Active state enable Hybrid Policy and Hybrid Reporting from the SWA. When Umbrella establishes a connection with the appliance, Hybrid Policy and Hybrid Reporting move to the Active state. Once the Hybrid Policy is Active, changes made to a policy in Umbrella can be pushed to the appliance, in the case of policies for which translation is supported. Once Hybrid Reporting is Active, reporting logs from the SWA are pushed to the Umbrella Dashboard.
The Sync State indicates if the policy push to the appliance was a success or a failure. In cases where the sync failed, hover your mouse over the Failed icon to view the reason for the failure.
Policy Push allows you to enable or disable the pushing of policy changes made in Umbrella to the SWA.
Note
Even if Policy Push is enabled, policy changes get pushed to the SWA only if the appliance is registered with Umbrella and Hybrid Policy is Enabled and Active.
Restore the SecureX Ribbon < Umbrella Integration with Secure Web Appliance > Configure Web Policies and Destination Lists
Updated about 1 year ago
