Enable Cloud Access Security Broker Features for Google Drive Tenants
Umbrella supports two Cloud Access Security Broker (CASB) features for Google Drive:
- Cloud Malware protection.
- Detection of third-party cloud applications that have been granted OAuth-based permission to access a user's protected resources on Google Drive. For more information, see Third-Party Apps Report.
Table of Contents
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
- The person performing the authentication must be a Google Super Admin and have an active Google user license.
- For third-party app support, your Google Drive tenant scopes for admin.report.audit.readonly and admin.reports.usage.readonly must be enabled.
- Chrome or Firefox is recommended with pop-up blockers/ad blockers disabled (only for the duration of authorization).
- Umbrella DLP Connector (also known as the SaaS API Connector) must be installed in the tenant by a Google Admin User. We recommend using a service account for the installation.
Limitation
- A tenant that fails to authenticate cannot be deleted.
Authorize a Tenant
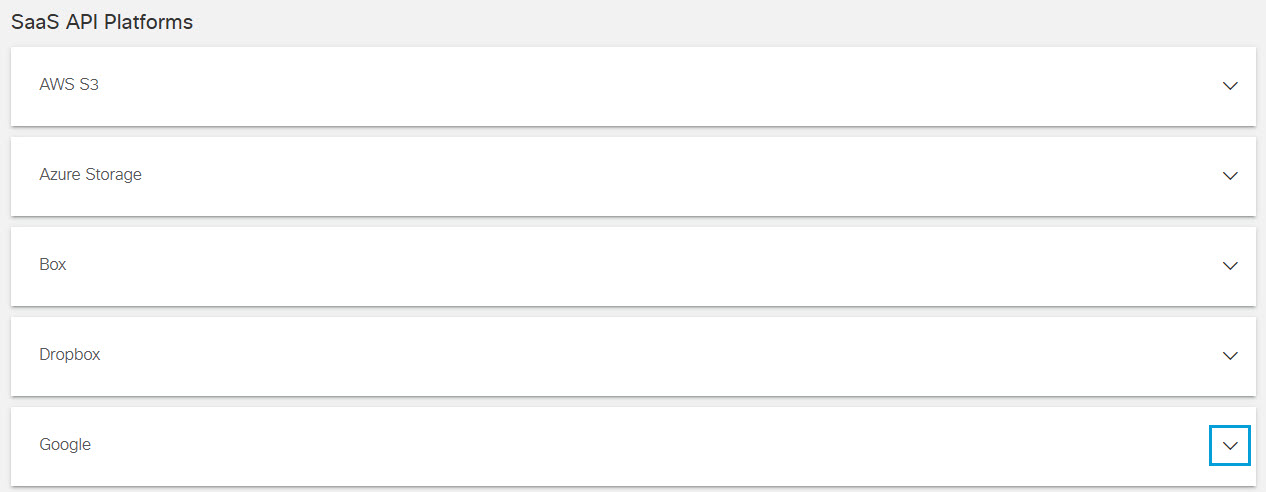
- In the Umbrella dashboard, navigate to Admin > Authentication.
- In the SaaS API Platforms section, click to expand Google.
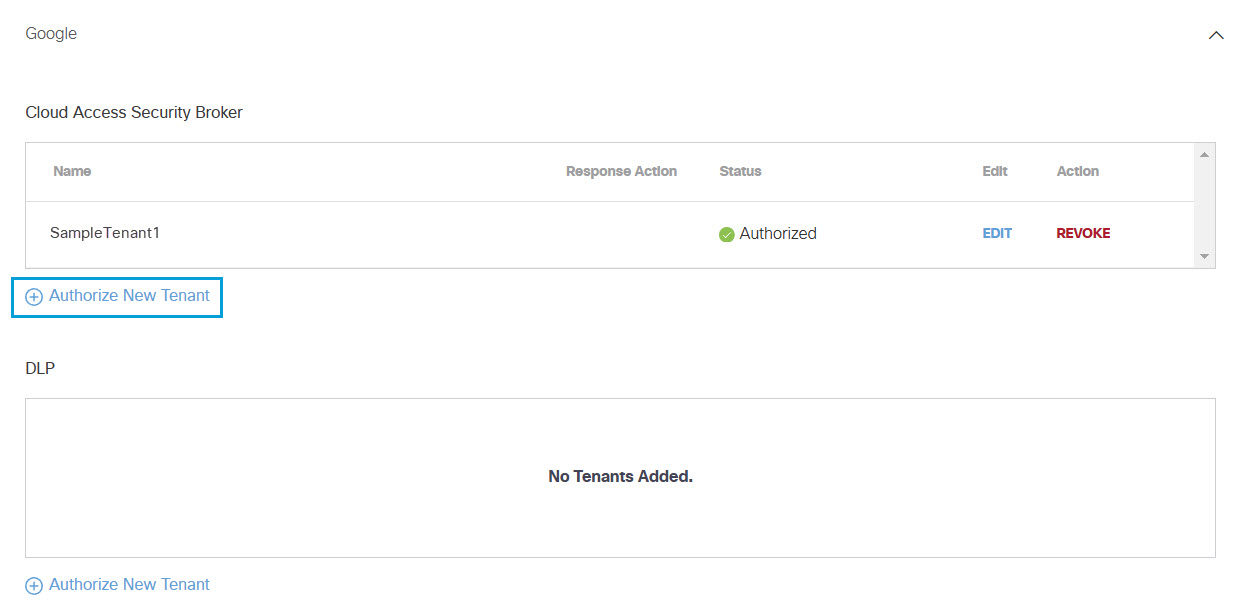
- In the Cloud Access Security Broker section, click Authorize New Tenant to add a Google tenant to your Umbrella environment.
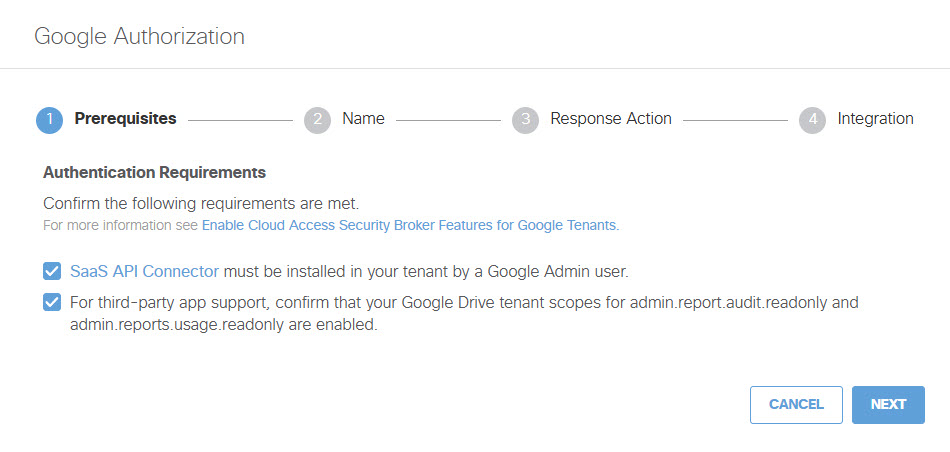
- In the Google Authorization dialog box, check the checkboxes to verify you meet the prerequisites, then click Next.
Note: The link to the SaaS API Connector brings you to the Umbrella DLP Connector site in the Google Workspace Marketplace. This is correct, despite the nomenclature difference.
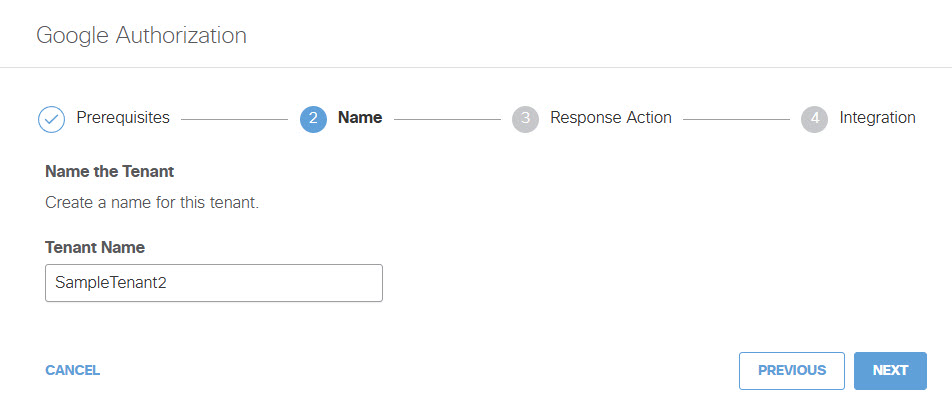
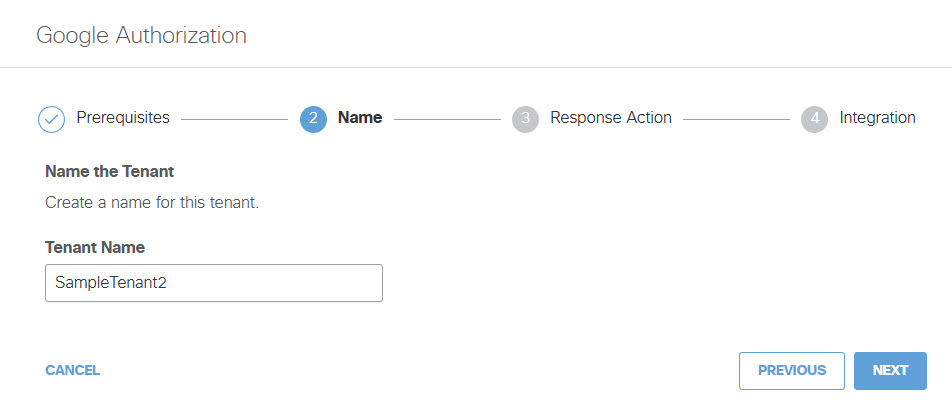
- Add a Tenant Name and then click Next.
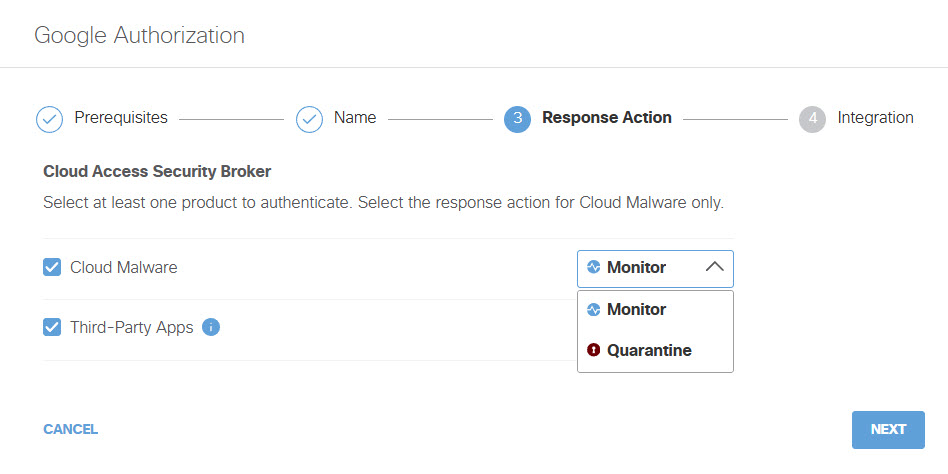
- Choose to authorize your Google Drive tenant for Cloud Malware Protection, or CASB detection for third-party applications, or both.
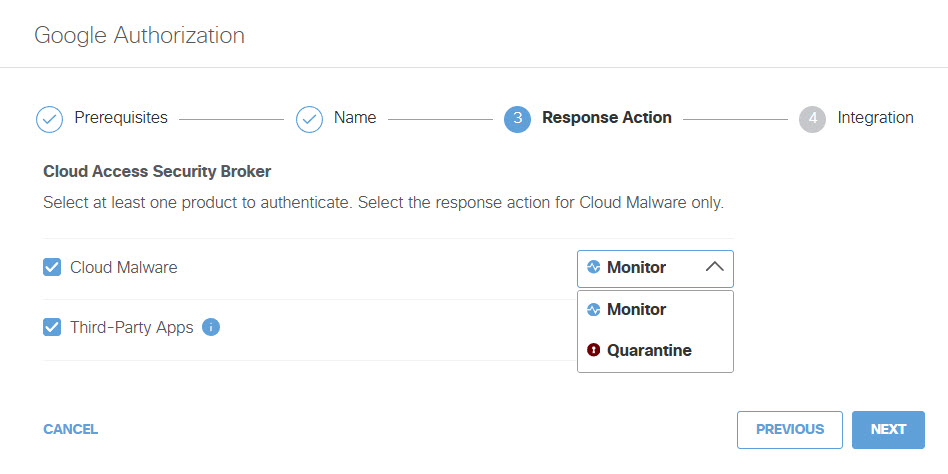
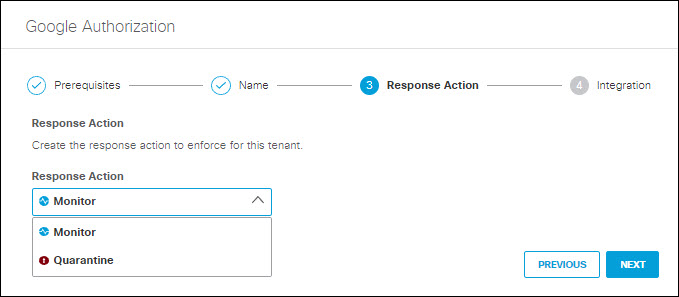
If you choose to authorize for Cloud Malware protection, you must also select a Response Action for Umbrella to apply to Google files found with malware.
- Choose Monitor to cause Umbrella to log files detected with malware. You will be able to manually quarantine these files from the Cloud Malware report.
- Choose Quarantine to:
- Move the file into a folder named Cisco_Quarantine_Malware in the root path of the admin who authorized the tenant, remove all collaborators, and change the file owner to the Google admin.
- Replace the file in its original location with a text file named filename.ppt_Cisco_Quarantined.txt explaining to the original file owner that the file is identified as malware and for more information to contact their organization administrator.
After making your selections, click Next.
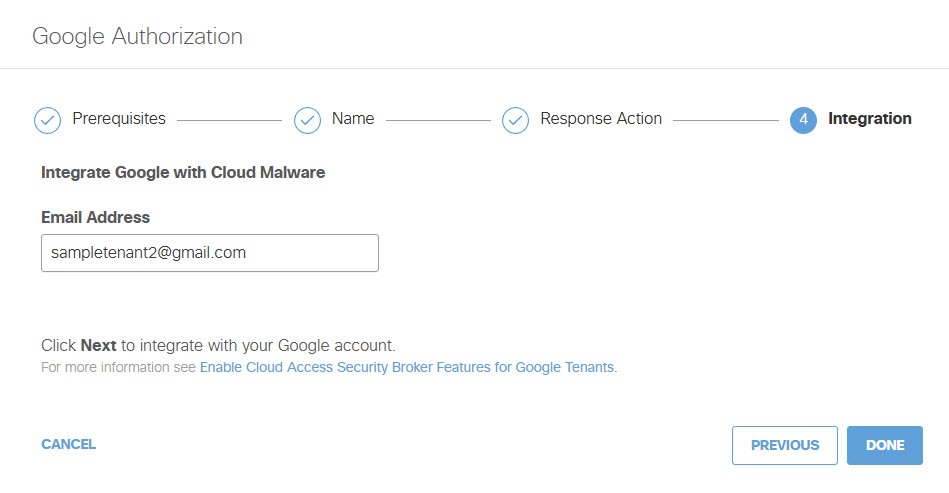
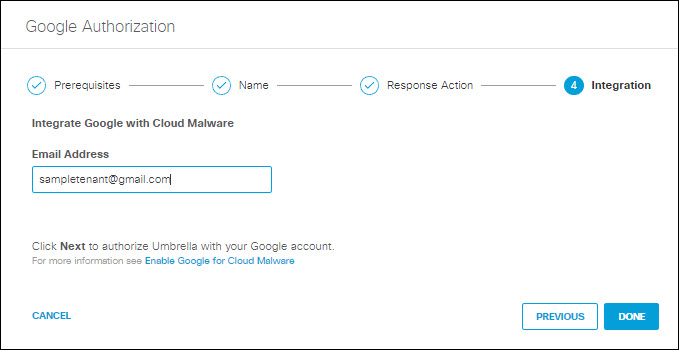
- Enter valid a gmail Email Address and then click Done.
The new tenant appears in the Cloud Access Security Broker section.
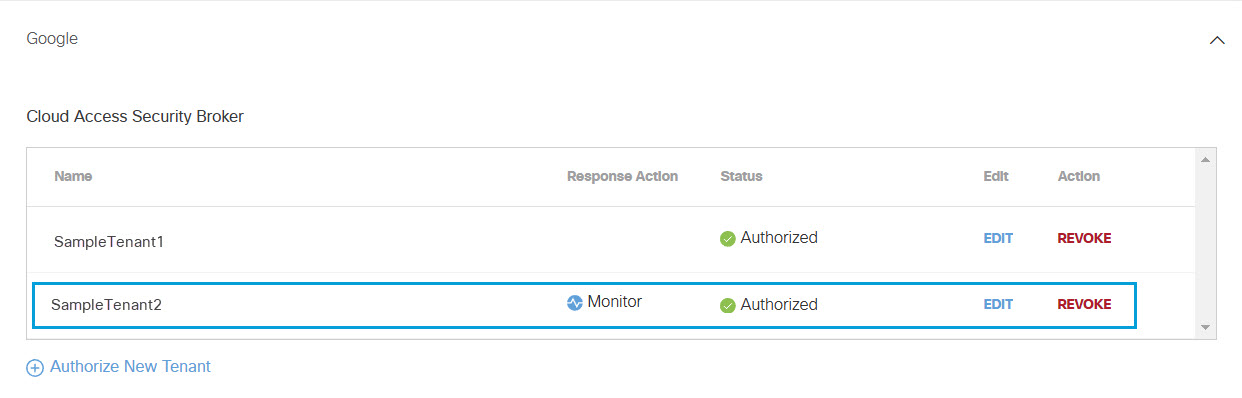
Edit a Tenant
You can change the Response Action you have selected for a tenant.
- Navigate to Admin > Authentication.
- In the SaaS API Platforms section, click Google.
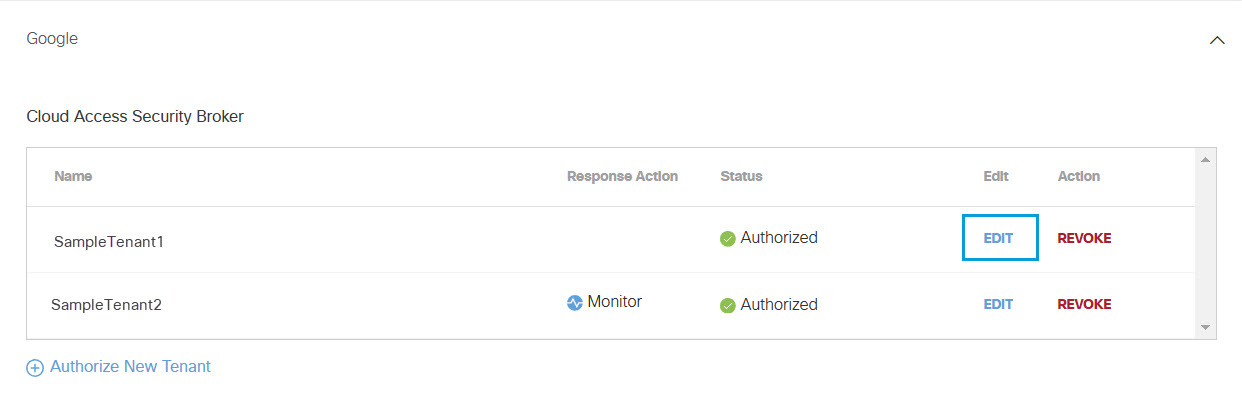
- In the Cloud Access Security Broker section, from the Edit column click Edit. You can edit any tenant.
- Choose to authorize your Google Drive tenant for Cloud Malware protection, or CASB detection for third-party cloud applications, or both.
If you choose to authorize for Cloud Malware protection, you must also select a Response Action for Umbrella to apply to Google files found with malware and then click Next.
- Choose Monitor to cause Umbrella to log files detected with malware. You will be able to manually quarantine these files from the Cloud Malware report.
- Choose Quarantine to:
- Move the file into a folder named Cisco_Quarantine_Malware in the root path of the admin who authorized the tenant, remove all collaborators, and change the file owner to the Google admin.
- Replace the file in its original location with a text file named filename.ppt_Cisco_Quarantined.txt explaining to the original file owner that the file is identified as malware and for more information to contact their organization administrator.
After making your selections, click Next.
- Click Done.
The new Response Action is displayed.
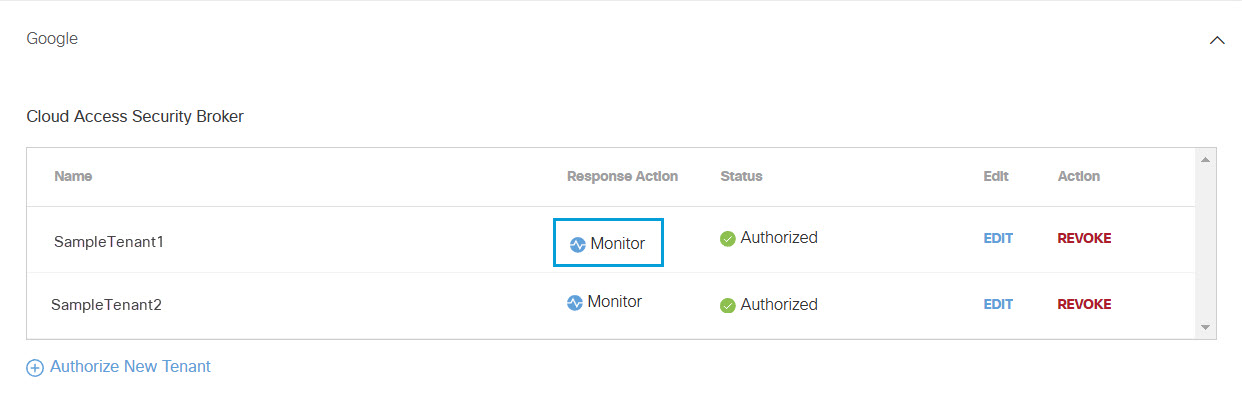
Revoke Authorization
You can revoke any authorized tenant.
- From the Action column, click Revoke. You can revoke any authorized tenant.
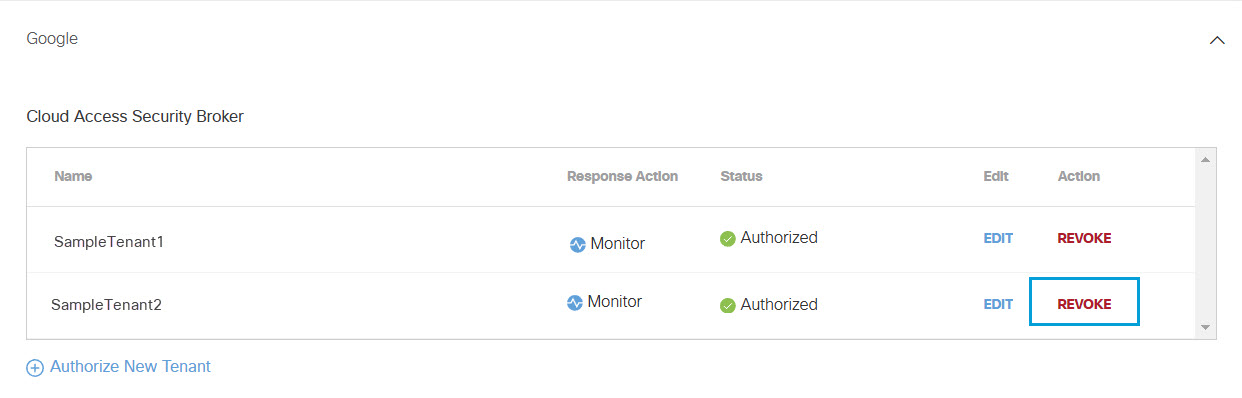
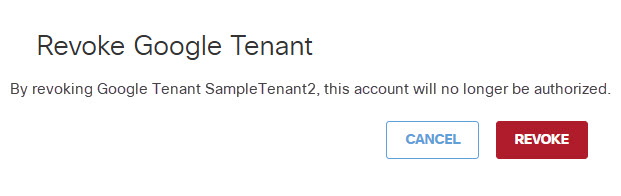
- Click Revoke. The selected tenant is no longer authorized.
Enable Cloud Malware Protection for Dropbox Tenants< Enable Cloud Malware Protection for Google Drive Tenants > Enable Cloud Access Security Broker Features for Microsoft 365 Tenants
Updated 8 months ago