Configure IKEv2 IPsec Tunnel with Umbrella
This document provides information to configure an IKEv2 IPsec tunnel to Cisco Umbrella in IOS-XE.
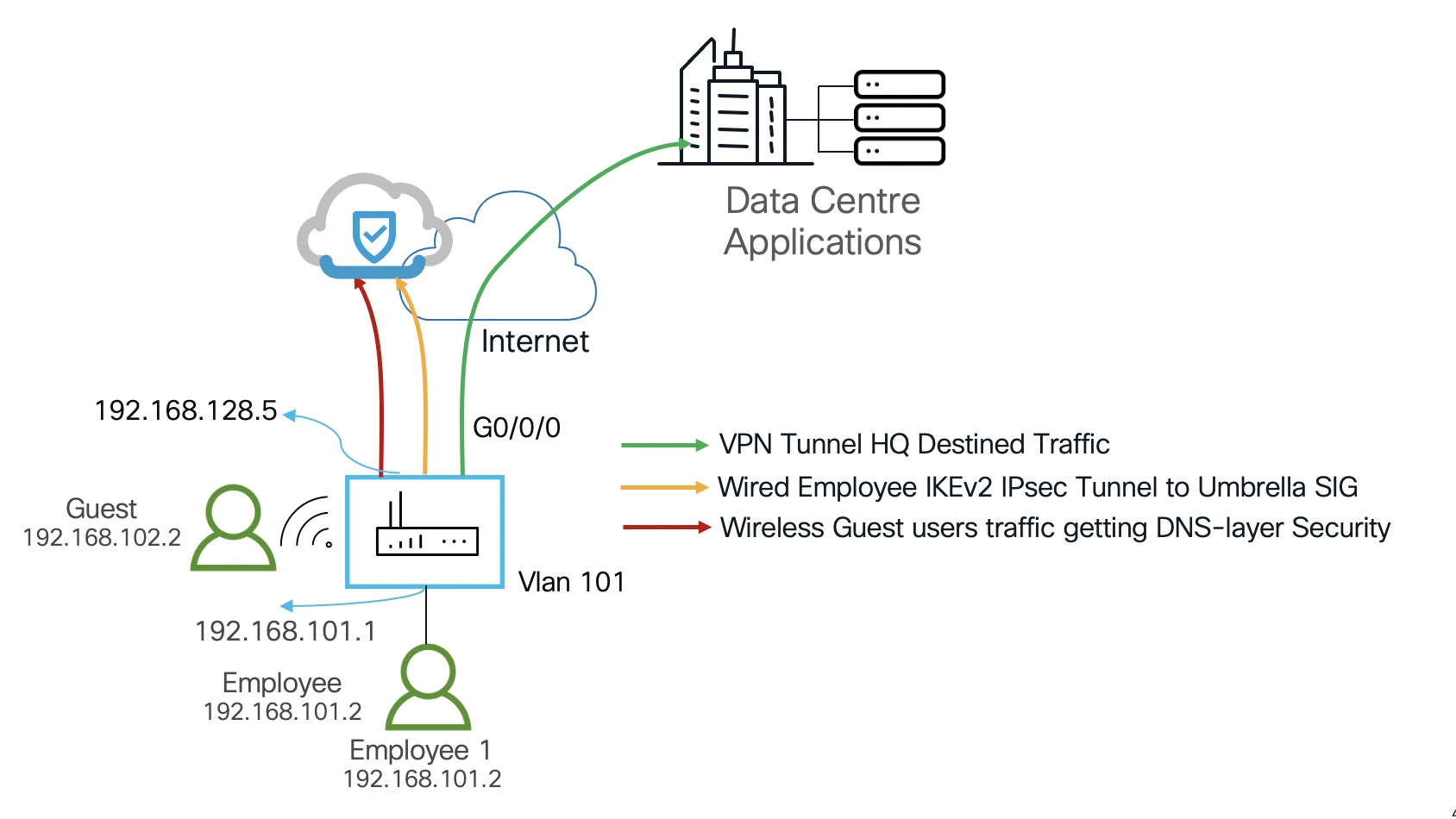
Table of Contents
- Prerequisites
- Image Download Links
- Supported Platforms
- Configuration
- Configure Tunnels in Umbrella
- Configure IKEv2 Proposal
- Configure IKEv2 Policy
- Configure IKEv2 Keyring
- Configure IKEv2 Profile
- Configure IPsec Transform Set
- Configure IPsec Profile
- Configure the Tunnel Interface
- Send Traffic to the Tunnel
- Verification
- Show IKEv2 session
- Show IPsec sa
- Create Umbrella Web Policy
- Test from a Host behind Vlan 101
- Other Resources
Prerequisites
- Umbrella SIG subscription.
- Any router physically or virtually running IOS-XE 17.2 or later.
Image Download Links
Catalyst 8500L - https://software.cisco.com/download/home/286324574/type
Catalyst 8300 - https://software.cisco.com/download/home/286324476/type
Catalyst 8200 - https://software.cisco.com/download/home/286324472/type
Catalyst 8000V - https://software.cisco.com/download/home/286327102/type
ISR - https://software.cisco.com/download/home/284389362/type
CSR - https://software.cisco.com/download/home/284364978/type
ISRv - https://software.cisco.com/download/home/286308693/type
Supported Platforms
ISR 4461, 4451, 4431, 4351, 4331, 4321, 4221X, 4221, CSR, ISRv and ISR 1K, Catalyst 8500L, 8300, 8200, and 8000V.
Configuration
Configure Tunnels in Umbrella
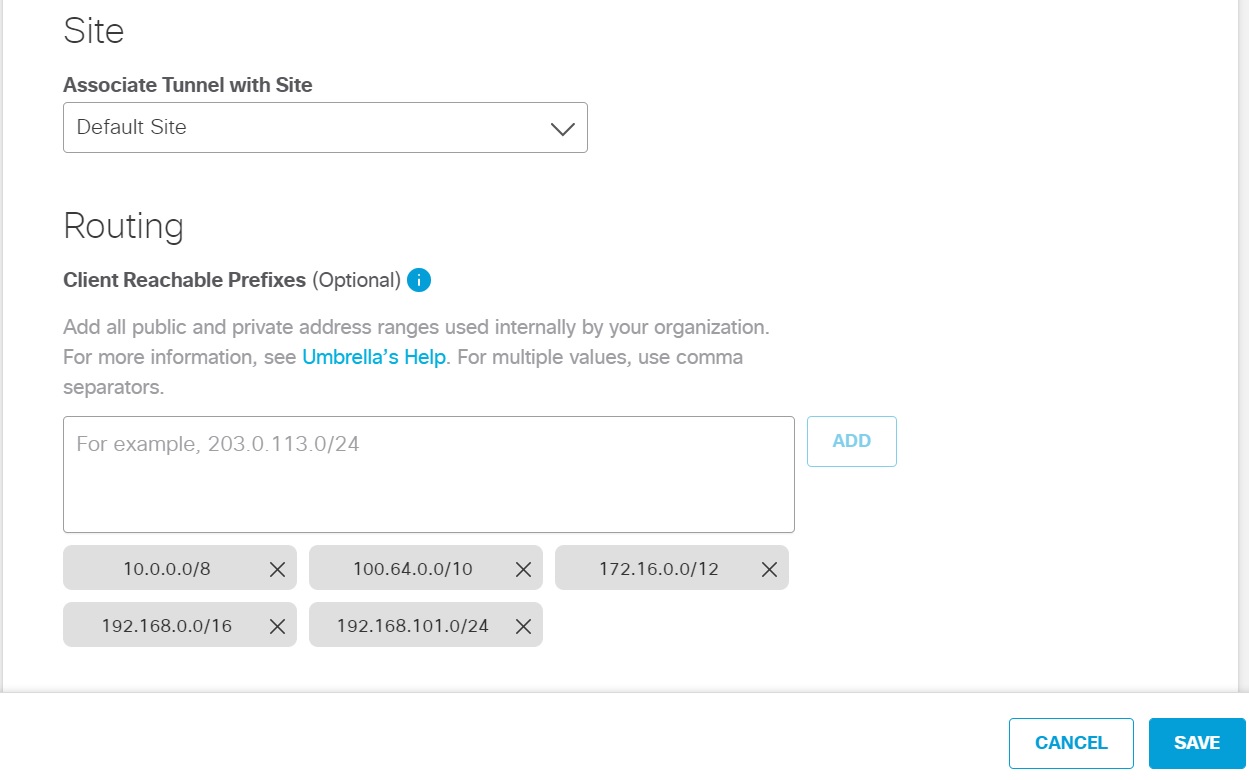
- Navigate to Deployments > Core Identities > Network Tunnels, and then click Add.
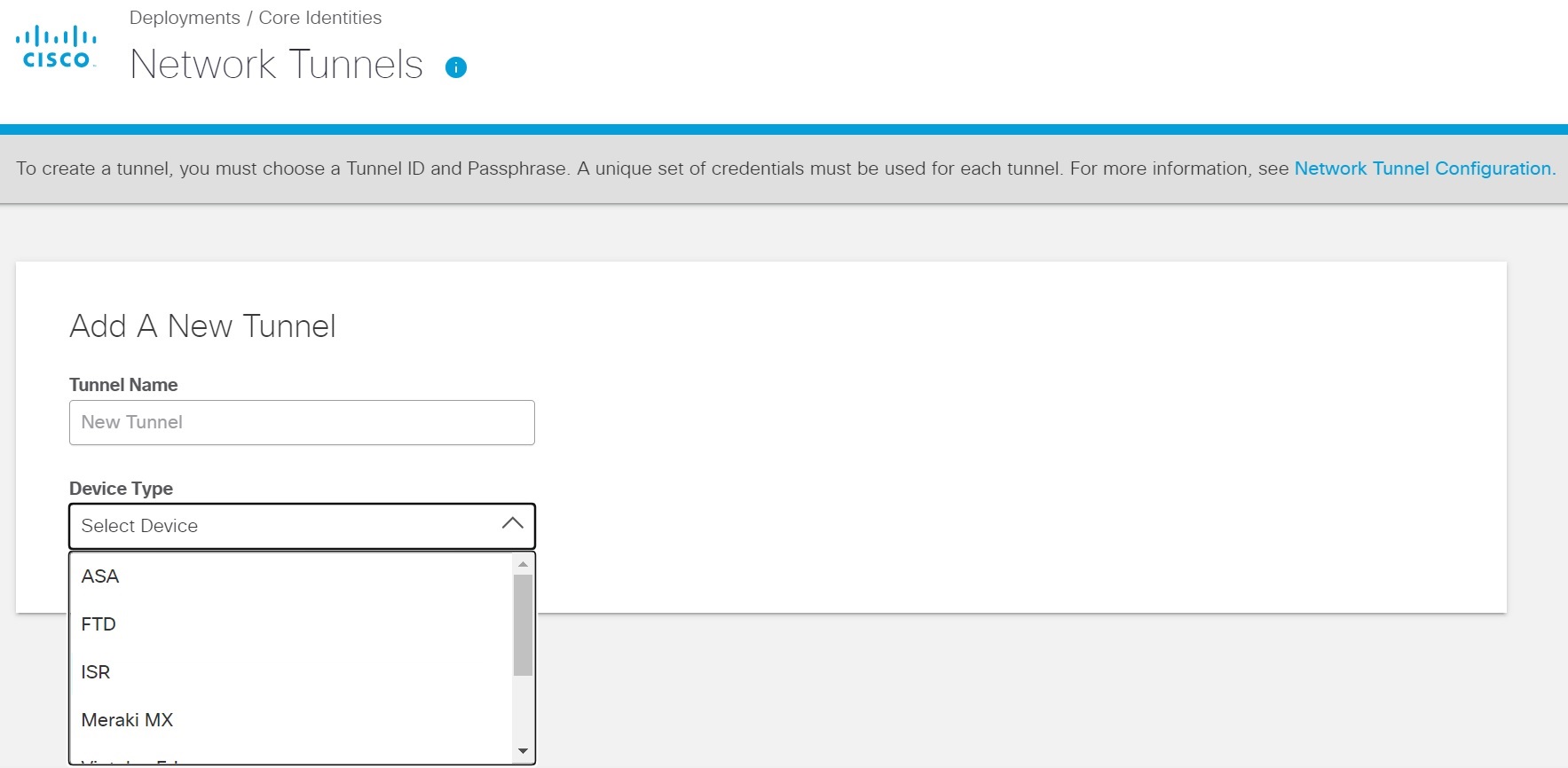
- Enter an appropriate name in the Tunnel Name field and choose an appropriate device from the Device Type drop-down list.
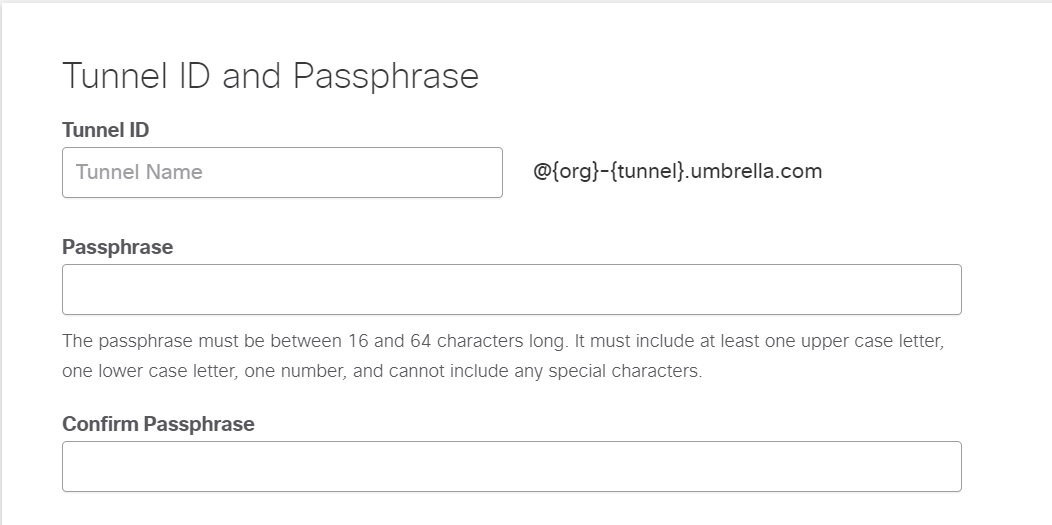
- Enter the Tunnel ID and the same Pre-Shared-Key (PSK) Passphrase in the Passphrase and the Confirm Passphrase fields.
Note: The Tunnel ID and Passphrase are required to configure the IKEv2 tunnel on the router.
- Choose an appropriate site from the Associate Tunnel with Site drop-down list and optionally, enter an IP address to the Client Reachable Prefixes field which you would like to send to Umbrella SIG and then click Save.
Note: Umbrella portal already pre populates the RFC 1918 addresses. You do not have to add any IP addresses.
The new tunnel appears in the Umbrella dashboard with a status of Not Established. The tunnel status is updated once it is fully configured and connected with appropriate device.
Configure IKEv2 Proposal
See Supported IPsec Parameters to choose encryption algorithm, integrity, and Diffie Hellman (DH) Group that should match with Umbrella support for appropriate proposal.
crypto ikev2 proposal umbrella-proposal
encryption aes-gcm-256
integrity sha256
group 19 20
Configure IKEv2 Policy
The match address local is only needed if you have multiple IKEv2 proposal configured with different encryption, group, and so on. If there is only one proposal, then you do not need the match address local command.
crypto ikev2 policy umbrella-pol
proposal umbrella-proposal
match address local 192.168.128.5 ==> WAN facing interface address
Configure IKEv2 Keyring
Choose the IP address of the Umbrella data center (DC) that is closest to you. See Connect to Cisco Umbrella Through Tunnel.
crypto ikev2 keyring umbrella-kr
peer umbrella
address 146.112.67.8 ===> Closest Umbrella DC
pre-shared-key XXXXXXXXXX ===> Fill in the pre-shared key from the Umbrella Portal
Configure IKEv2 Profile
This step requires the data that you gathered from the Umbrella portal.
crypto ikev2 profile umbrella-ikev2-profile
match identity remote address 146.112.67.8 255.255.255.255
identity local email [email protected]
authentication remote pre-share
authentication local pre-share
keyring local umbrella-kr
dpd 10 2 periodic
Configure IPsec Transform Set
See Supported IPsec Parameters to choose the router's configuration that matches the parameters supported by Umbrella.
crypto ipsec transform-set umbrella-tset esp-aes 256 esp-sha256-hmac
mode tunnel
Configure IPsec Profile
crypto ipsec profile umbrella-ipsec-profile
set transform-set umbrella-tset
set ikev2-profile umbrella-ikev2-profile
Configure the Tunnel Interface
Tunnel destination is the Umbrella data center IP closest to you that you chose to configure Keyring.
interface Tunnel1
ip unnumbered GigabitEthernet0/0/0 ==> WAN Interface
tunnel source GigabitEthernet0/0/0 ==> WAN Interface
tunnel mode ipsec ipv4
tunnel destination 146.112.67.8 ===> Closest Umbrella DC
tunnel protection ipsec profile umbrella-ipsec-profile
Send Traffic to the Tunnel
You can add a default route on the router and set the next hop to the tunnel 1 interface or do the following:
Send guest user traffic (Vlan 102) directly in the clear to the internet by applying DNS-layer security for the wireless users. However, all employees traffic (Vlan 101) will be send in the IPsec tunnel to Umbrella SIG.
To configure an ACL, route-map to the tunnel 1 interface where next-hop is set. Make sure that this interface does not have NAT or FW configured. Umbrella will provide NAT and there is no need to apply FW for packets that will ride over the tunnel.
ip access-list ext To_Umbrella
permit ip 192.168.101.0 0.0.0.255 any
route-map umbrella-routemap permit 10
match ip address To_Umbrella
set interface Tunnel1
interface vlan101
ip policy route-map umbrella-routemap
The router configuration is complete and the tunnel is up.
Verification
Show IKEv2 session
Run the following command to shoe the IKEv2 session.
kusankar-1121X#show crypto ikev2 session
The output is similar to:
IPv4 Crypto IKEv2 Session
Session-id:43, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.128.5/4500 146.112.67.8/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:20, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/8084 sec
CE id: 0, Session-id: 43
Local spi: 2DB9D463EBD77607 Remote spi: 898DC0640ACA0422
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0x3CB167C1/0xC4FF1DDA
IPv6 Crypto IKEv2 Session
Show IPsec Sa
kusankar-1121X#sh crypto ipsec sa
The output is similar to:
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 192.168.128.5
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 146.112.67.8 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 37243, #pkts encrypt: 37243, #pkts digest: 37243
#pkts decaps: 44758, #pkts decrypt: 44758, #pkts verify: 44758
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.128.5, remote crypto endpt.: 146.112.67.8
plaintext mtu 1422, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0/0
current outbound spi: 0xC4FF1DDA(3305053658)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x3CB167C1(1018259393)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2067, flow_id: ESG:67, sibling_flags FFFFFFFF80000048, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4603810/1422)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC4FF1DDA(3305053658)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2068, flow_id: ESG:68, sibling_flags FFFFFFFF80000048, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4606818/1422)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Encaps and decaps are going up; it means that the traffic is being send and received.
Finally, configure some rules to block certain categories and test the traffic from a host behind Vlan 101.
Create Umbrella Web Policy
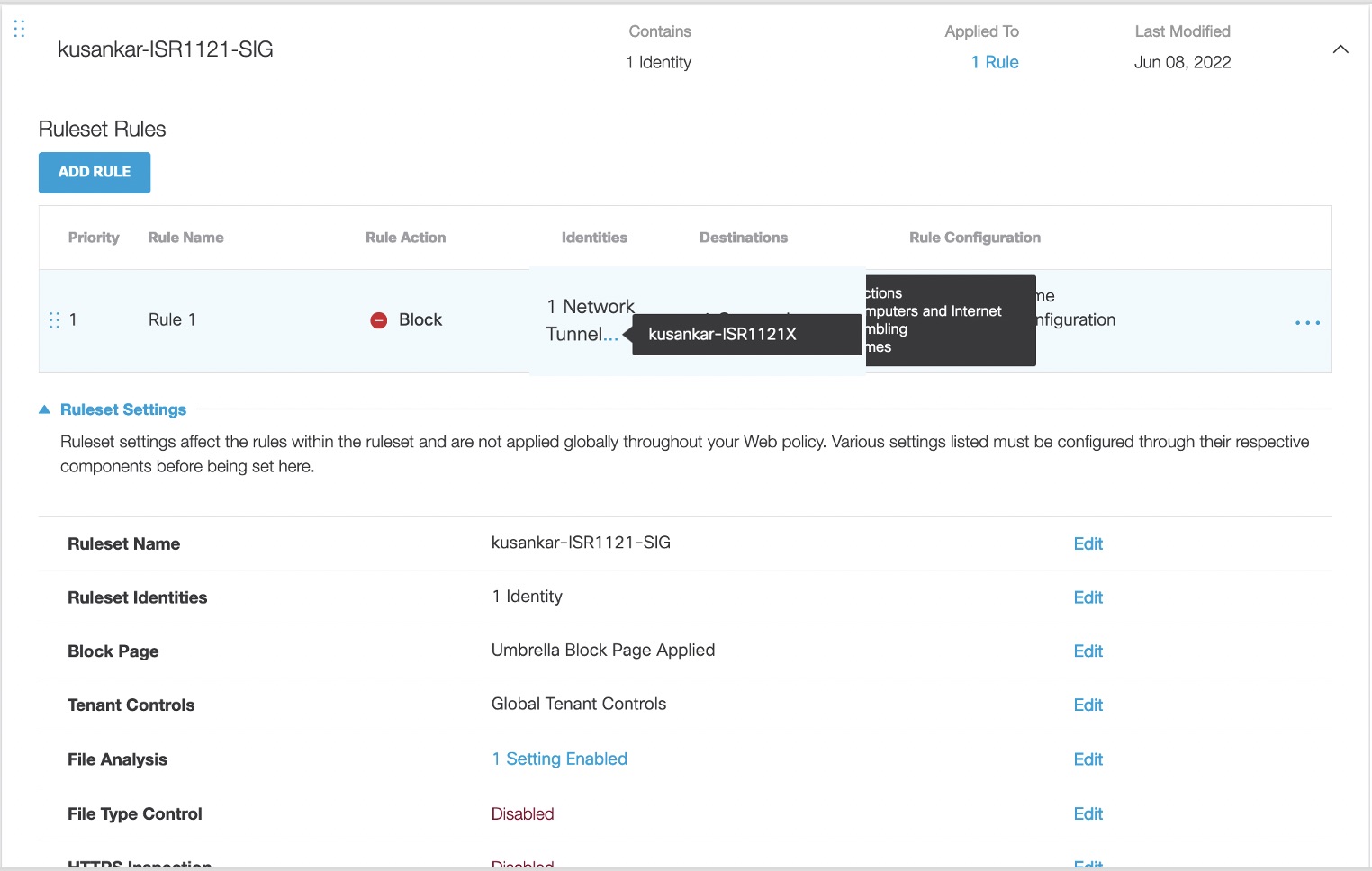
- Navigate to Policies > Management > Web Policy, and then click Add.

- Click Add Rule and enter a meaningful name for Rule Name, such as Rule 1.
For example, Rule 1 has been created and four categories are been blocked, such as Games, Gambling, Auctions, and Computers and Internet, and applied that to the Tunnel as shown in the following image.
Test from a Host behind Vlan 101
Browse 888.com, ebay.com, or other websites that belong to the four categories that you have blocked. Umbrella displays a block page. You can also use cs.co/checkumbrella on the host to see what OrgID you belong to.
Other Resources
Umbrella Cloud Firewall
Cisco 1000 Series Connected Grid Routers
Configure Tunnels with Cisco ISR < Configure IKEv2 IPsec Tunnel with Umbrella > Configure Tunnels Automatically with Cisco ASA and CDO
Updated almost 2 years ago
