Enable File Inspection for the Web Policy
For the Web policy, File Inspection is enabled through a ruleset. File Inspection uses Cisco's Advanced Malware Protection (AMP) as well as Umbrella's antivirus engines to scan for malicious files. Once inspections are complete, a file is either delivered or the connection is terminated and the user is served the IP of the block page.
Once you have enabled File Inspection, to monitor and review Umbrella's inspection activities, use the Security Activity and Activity Search reports.
Note: You must first enable File Inspection before you can Enable Threat Grid Malware Analysis.
Prerequisites
- A root certificate must be installed on all machines. For more information, see Manage Certificates.
- Full admin access to the Umbrella dashboard. See Manage User Roles.
Procedure
By default, File Inspection is enabled.
- Navigate to Policies > Management > Web Policy and click Add or expand an existing ruleset.

- Under Ruleset Settings, for File Analysis, click Edit.
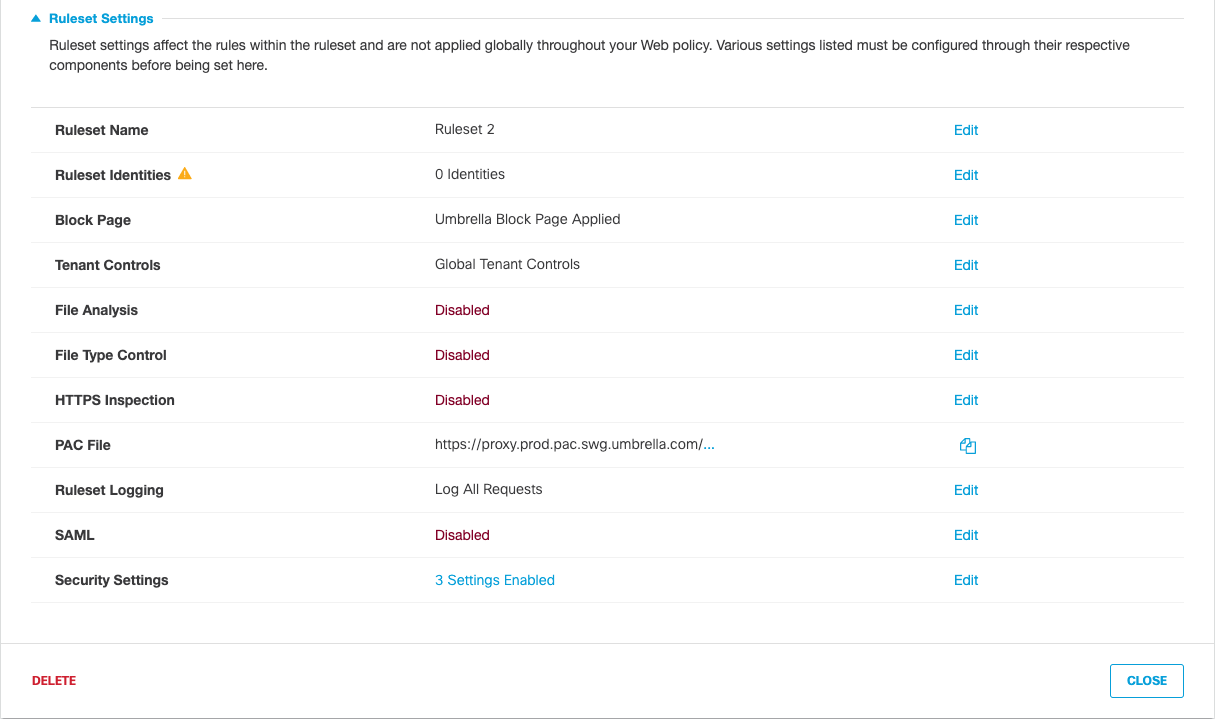
- Enable File Inspection and click Save.
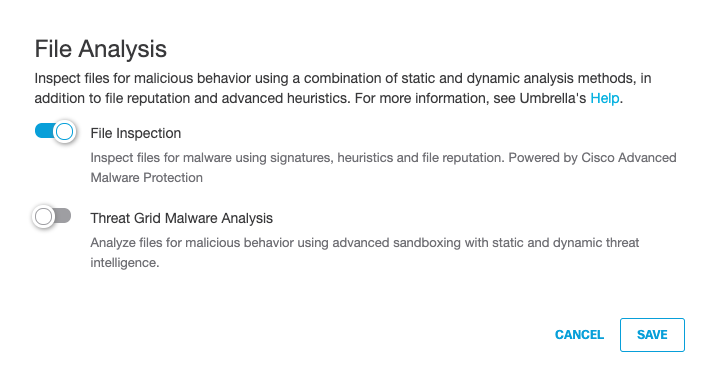
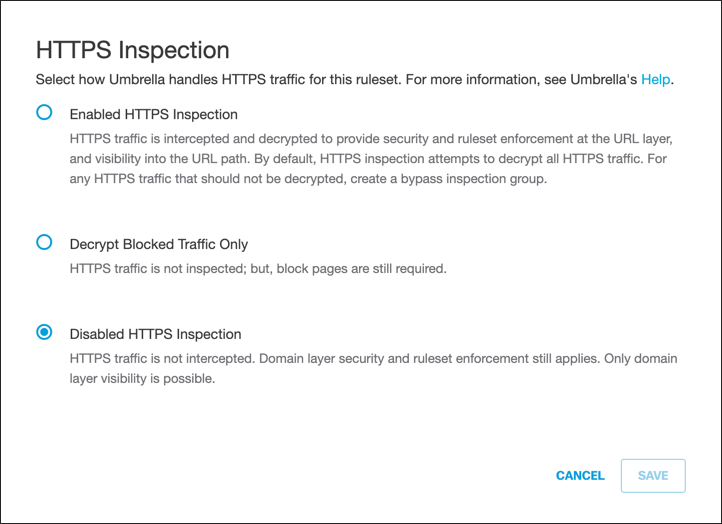
- For HTTPS Inspection, click Edit and select Enable HTTPS Inspection.
Note: Although not required, we recommend enabling HTTPS Inspection.
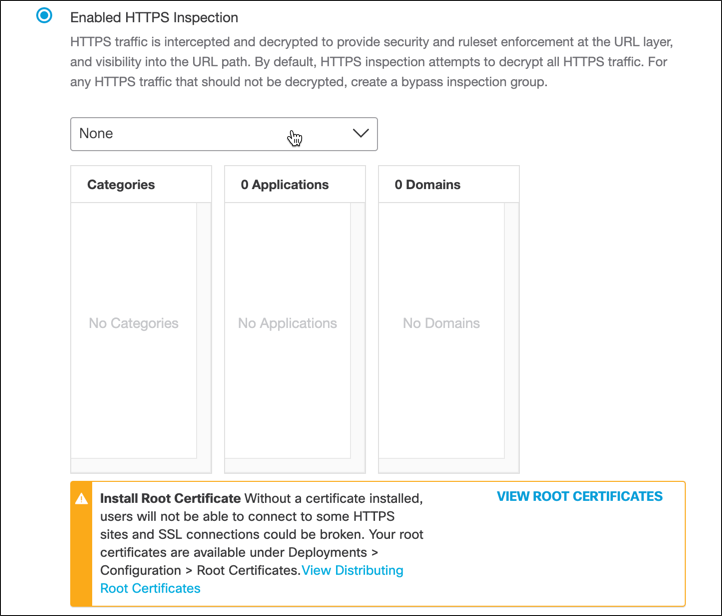
- From the pull-down menu, optionally select a preconfigured Selective Decryption List.
This preconfigured Selective Decryption List contains content categories and domains to be exempted from HTTPS inspection for the ruleset.
- Click Save.
Enable File Inspection for DNS Policies < Enable File Inspection for the Web Policy > Enable Threat Grid Malware Analysis
Updated almost 2 years ago
