Manage Global Settings
The Web policy's Global Settings affect all rules and rulesets. Global settings can be enabled and disabled for certificate error handling, Microsoft 365 Compatibility and for Protected File Bypass.
Certificate Error Handling allows you to configure how Umbrella responds to detected certificate errors, either by ignoring errors from specified destinations or blocking access. Microsoft 365 Compatibility exempts Microsoft 365-related domains, marked as Optimize and Allow in Microsoft's endpoint categories, to bypass inspection and policy enforcement. Protected File Bypass overrides Umbrella's default setting that blocks the downloading of encrypted files.
Table of Contents
Certificate Error Handling
Enable this option to configure how responses are handled when a request to access a specified destination detects a certificate error. Umbrella can be set to ignore errors from specified destinations or block access if an error is detected. For more information, see Enable Certificate Error Handling.
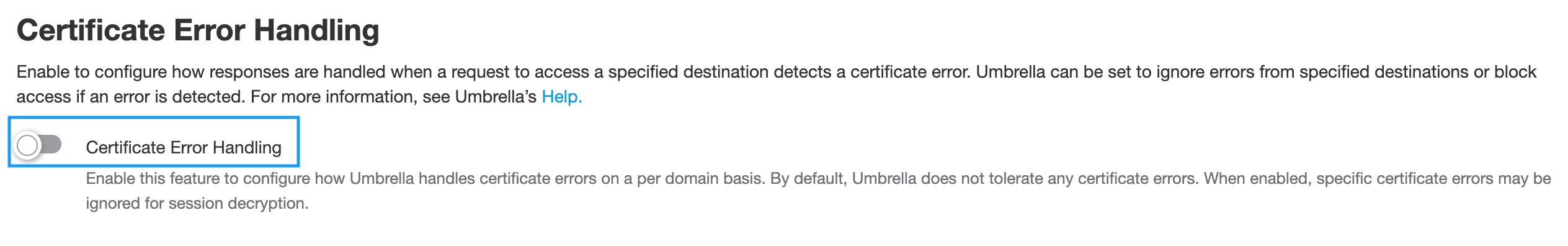
Microsoft 365 Compatibility
The Microsoft 365 Compatibility feature exempts Microsoft 365-related domains, marked as Optimize and Allow in Microsoft's endpoint categories, to bypass inspection and policy enforcement, allowing those domains to pass through the Umbrella infrastructure unaltered. The domains are excluded from HTTPS decryption and content filtering. The Microsoft 365 traffic appears in Umbrella reporting, however, because HTTPS inspection is disabled, traffic is logged only at the host/domain level and will not show the full URL.
Tenant Controls
Microsoft 365 Compatibility is compatible with Tenant Controls. However, when Tenant Controls are configured for Microsoft 365, Umbrella decrypts four Microsoft login domains (login.microsoftonline.com, login.live.com, login.microsoft.com, and login.windows.net) for the purpose of tenant enforcement. The domain is detected by analyzing the SNI (Server Name Indication) TLS extension. Some applications may not send SNI information in which case the exclusion does not apply.
Limitations
- Microsoft 365 traffic is still sent to Umbrella's web proxy service in all deployment methods (Tunnel, AnyConnect, PAC). To stop this traffic from hitting Umbrella entirely, add manual 'External Domain' entries or route the traffic direct to the internet from your connecting devices.
- File Inspection will no longer apply to this traffic.
- This will not change geo-location behavior for Microsoft 365
- This will not prevent the Microsoft 365 traffic egressing from an Umbrella IP address
- This does not apply to all Microsoft/Microsoft 365 domains. Only those categorized as important for performance by Microsoft.
- Allows a number of important Microsoft 365 domains so web policies and filtering do not apply to them and prevents these domains from triggering Umbrella SAML authentication.
Note: MS Intune sync requires "manage.microsoft.com" to be added to the Selective Decryption List even when the Microsoft 365 Compatibility feature is enabled.
For more information, see the official Microsoft documentation.
Procedure
- Navigate to Policies > Management > Web Policy and click Global Settings.

- Enable Microsoft 365 Compatibility.

Protected Files Bypass
Umbrella’s security protection is unable to scan protected files because these files are encrypted. Thus, Umbrella considers encrypted files to be a high risk security threat. Therefore, by default, Umbrella and by extension the Web policy, blocks identities from downloading encrypted files. Enabling the Web policy's Protected File Bypass global setting allows you to override Umbrella's default global setting and permits the downloading of protected files.

How Protected Files Bypass is Enabled and Disabled
- When enabled globally, Protected Files Bypass is enabled for all rules in all rulesets. Protected File Bypass is automatically enabled when adding new rules.
- When enabled globally, Protected Files Bypass cannot be disabled for individual rules. Protected Files Bypass is always enabled for all rules.
- When disabled globally, Protected Files Bypass can be enabled for individual rules. Protected Files Bypass can be either enabled or disabled for all rules.
- When disabled globally, Protected Files Bypass can be disabled for individual rules that had previously been set to enabled. Protected Files Bypass can be either enabled or disabled for all rules.
For more information and the procedure to manually enable or disable at the rule level, see Protected File Bypass.
Procedure
Note: Enable with caution as Umbrella will not scan protected files. Cisco recommends downloading and opening files from trusted sources only.
- Navigate to Policies > Management > Web Policy and click Global Settings.

- Enable Protected File Bypass.

PAC Files
To bypass internal or external domains, you can add these domains in Umbrella. Umbrella copies the domains that you configured in Umbrella to the default PAC file. Web traffic on the domains is not sent to the Umbrella proxy. For information about internal domains, see Manage Domains.
After you download the default PAC file from Umbrella, you can edit the default PAC file and add more domains. Then, upload the customized PAC file to Umbrella or host this PAC file in your environment. For more information, see Upload Custom PAC Files to Umbrella.
Umbrella does not update the Internal Domains in a customized PAC file. Umbrella only modifies the default PAC file with the Internal Domains that you add in Umbrella.
Note: Umbrella supports IP-based domains. You must enter the IP in the browser’s address bar as the domain portion of the URL. For example, https://1.2.3.4/URLpath/. The PAC file does not resolve a domain to IP before matching an IP-based domain for bypass.
Prerequisites
- Full admin access to the Umbrella dashboard. See Manage User Roles.
- To download the Umbrella PAC file or custom PAC files, connect to Umbrella on a fixed Network or Network Tunnel. Register your fixed networks or network tunnels with Umbrella. A roaming user device that has the Cisco Secure Client with the Umbrella Roaming security module deployed can also connect to Umbrella and download PAC files.
Procedure
Copy the url for the Umbrella PAC file or a custom PAC file that you uploaded to Umbrella. Then paste the PAC file URL in a browser search bar and edit the file.
Copy the Umbrella PAC File
-
Navigate to Policies > Management > Web Policy, and then click Global Settings.

-
For Umbrella PAC File, click Copy to get the URL for the default PAC file.

Download the Umbrella PAC File
- Paste the PAC file URL into the browser's address bar, and then press Enter / Return.
The browser downloads the PAC file.
Edit the PAC File
- Open the downloaded PAC file with a text editor, update it with domains to be bypassed, and then save the PAC file.
- Add the internal domains that the web proxy will bypass to the PAC file, and then save the file.
Note: Provide a comma-delimited list of domain names and surround each domain name in the list with quotation marks. The wildcard character asterisk * is supported and treated as any value of any length. Use caution when using wildcards as well as periods. For example, *.example.com bypasses www.example.com, mail.example.com, and c.23.example.com. *example.com bypasses www.example.com as well as phishingexample.com. - Save the PAC file.
//------------------------Customer Section------------------------
//Add your internal domains within quotations marks like "wwwin.acme.com"
//after the right parenthesis below. Please remove the two examples
//below and add your own internal domains.
var dont_proxy_customer_list = new Array(
"wwwin.example.org",
"*.example.org"
);
//Warning to Administrators: Touching any section after this point might
//affect your users browsing experience and lead to considerable number
//of issues and loading your customer support.
//---------------------End Customer Section-----------------------
Best Practices for the Web Policy and Rulesets < Manage Global Settings > Confirm SafeSearch for a Web Policy Ruleset
Updated 9 months ago
