Configure Duo Security for Cisco Umbrella SAML
Duo Security for SAML configuration can be authenticated in one of the following ways:
- Upload the identity provider's (IdP) metadata file
- Manually configure IdP fields
Table of Contents
- Prerequisites
- Configure Cisco Duo Single Sign On (SSO) Application
- Configure Cisco Umbrella for SAML with Metadata Upload
Prerequisites
- Cisco Duo Single Sign On (SSO) must be enabled and configured. For more information, see Duo Single Sign-On.
- id.swg.umbrella.com must be sent to the Umbrella secure web gateway (SWG) and not sent directly to the internet.
- SAML metadata must have a signing key.
- Ensure that your IDP Endpoint—the URL used to communicate with your identity provider—bypasses the Umbrella proxy to avoid an authentication loop.
- Configure SAML with your identity provider (IdP) that supports SAML 2.0 POST profiles.
- Download your IdP's metadata file in XML format.
- Enable cookies for your browser.
- Enable SAML and HTTPS inspection on a Ruleset that includes the Network and Tunnel identities from which the user traffic arrives.
Configure Cisco Duo Single Sign On (SSO) Application
To configure Cisco Duo SSO, follow the steps for Duo Single Sign-On for Cisco Umbrella.
Configure Cisco Umbrella for SAML with Metadata Upload
- Navigate to Deployments > Configuration > SAML Configuration and click Add.

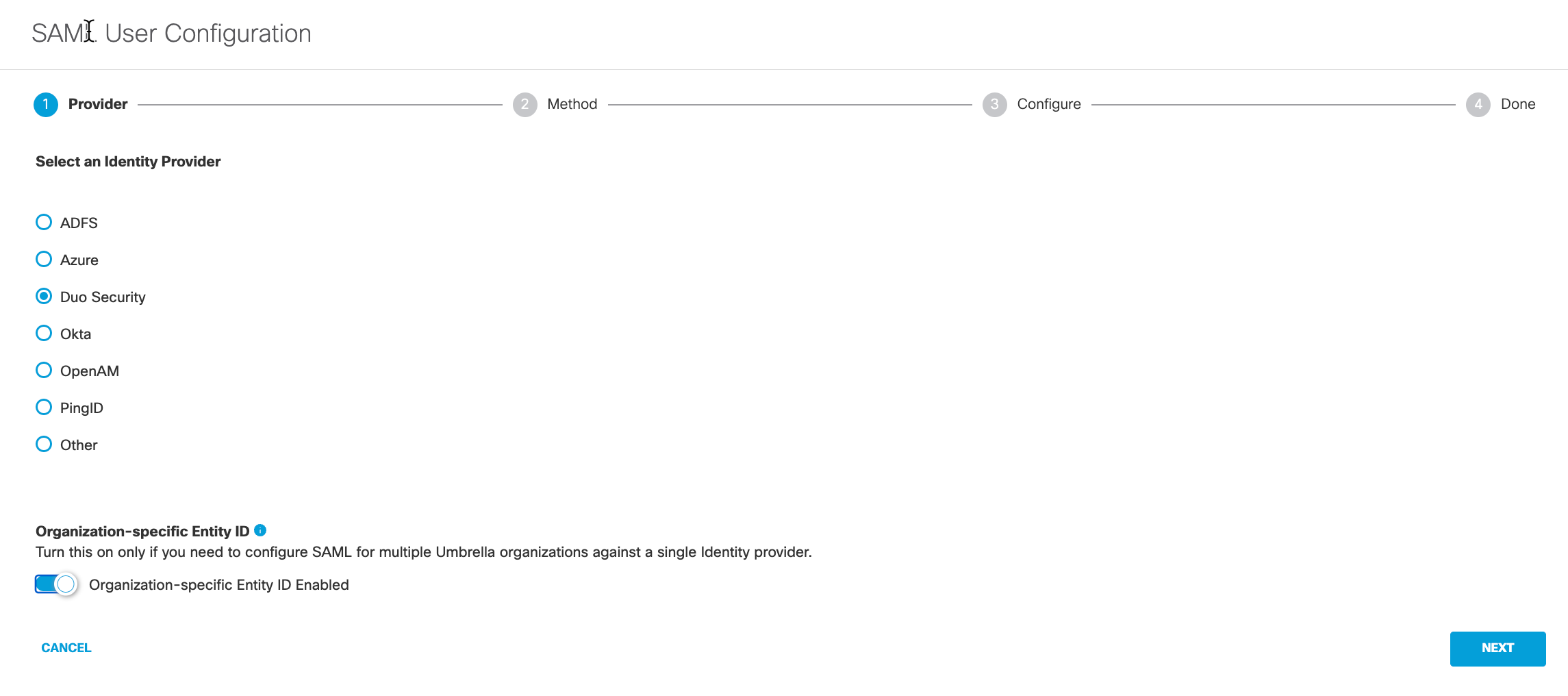
- Click the Duo Security radio button, toggle the Organization-specific Entity ID Enabled button to enable the entity ID, then click Next.
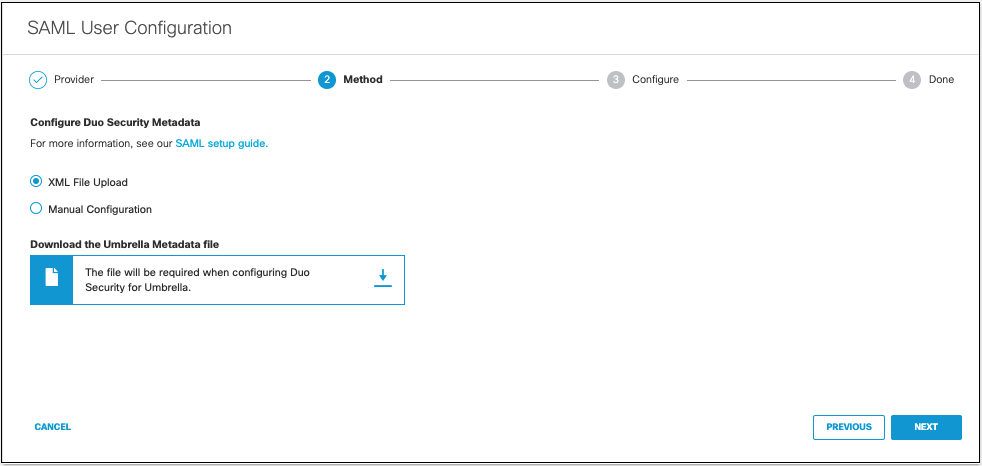
- Click the XML File Upload radio button, and then click Next.
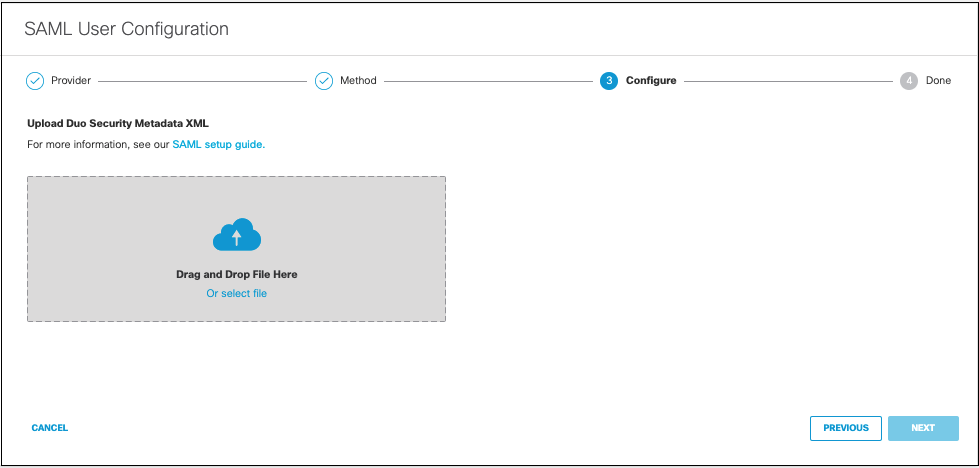
- Upload your Duo Security metadata file in XML format and click Next.
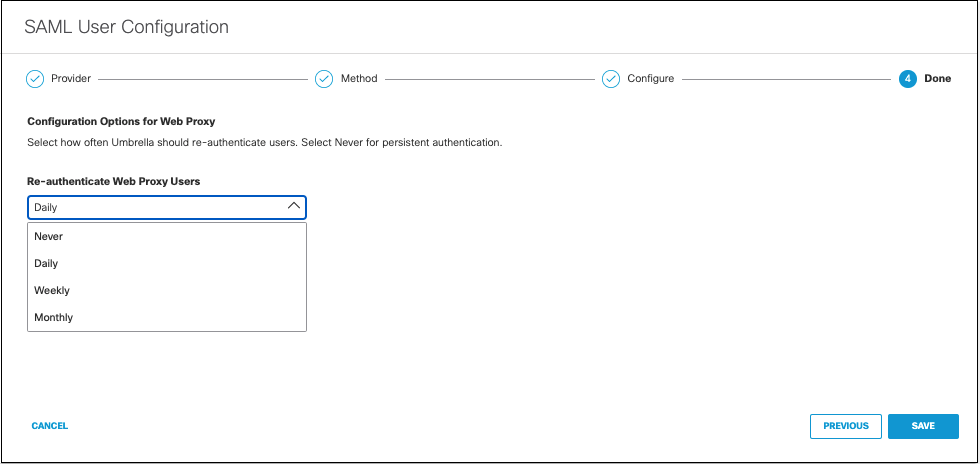
- Choose how often Umbrella re-authenticates the users from the Re-authenticate Web Proxy Users drop-down list. Make sure Daily is selected.
- Click Save. Your new configuration appears as SAML Web Proxy Configuration.
Configure AD FS for SAML < Configure Duo Security for Cisco Umbrella SAML > Configure PingID for SAML
Updated almost 2 years ago
